Difference Between Block Cipher and Stream CipherBlock cipher and stream cipher are members of the family of symmetric key ciphers, essentially encryption techniques used for directly transforming the plaintext into ciphertext. In this article, we will discuss the characteristics of block ciphers and stream ciphers and how they differ from one another. What is Block Cipher?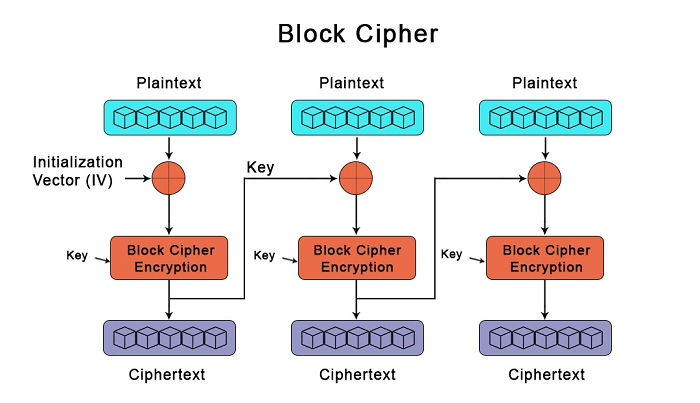
A block cipher is a symmetric cryptographic technique which we used to encrypt a fixed-size data block using a shared, secret key. During encryption, we used plaintext and ciphertext is the resultant encrypted text. It uses the same key to encrypt both the plaintext, and the ciphertext. A block cipher processes the data blocks of fixed size. Typically, a message's size exceeds a block's size. As a result, the lengthy message is broken up into a number of sequential message blocks, and the cipher operates on these blocks one at a time. With the help of the shared secret key, a block cipher encrypts and decrypts its input one block rather than one bit at a time. Since the block's size is fixed, padding is not necessary. It is a symmetric algorithm. During encryption, it converts text input into cyphertext using the shared key. It uses the same key during decryption to change the cyphertext back to the original plaintext. The length of the output and input are identical.
There are various modes of operation of a block cipher:
These modes serve as a block cipher's general procedures principles. 1. Electronic Codebook ModeElectronically code message in plaintext form is dine in ECB mode. It is the most straightforward block cipher operating mode. It does not introduce any randomness to the key stream, and it is the only mode we can use to encrypt a single-bit stream. Using the cipher's key and substitution alphabet, each plaintext symbol, such as a character from the plaintext alphabet, is transformed into a ciphertext symbol. Each block of plaintext is encrypted separately from every other block. Only 8 bytes of the key are used when the plaintext block is only 8 bytes long, and all 100 bytes of the key are utilised when the plaintext block is 100 bytes long. 2. Cipher Block Chaining Mode (CBC)When using CBC mode to encrypt data, each block of plaintext is combined with the ciphertext that came before it. A ciphertext generated by the symmetric algorithm depends on all plaintext block processed in the data stream before it. This is done to ensure that every block of the ciphertext depends on every other block that came before it. Before using the cipher algorithm to encrypt the data, each block of plaintext is XORed (exclusive OR) with the block of ciphertext that came before it. Numerous security applications used CBC mode. For example, Secure Sockets Layer/Transport Layer Security uses CBC mode in order to encrypt data which is transferred over the internet. 3. Ciphertext Feedback Mode (CFB)It is occasionally important to quickly encrypt and send plaintext values, one at a time, as opposed to CBC mode, which encrypts a predetermined number of bits of plaintext at a time. CFB also uses an IV, similar to CBC. A block cipher is a part of the random number generator used by CFB. In CFB mode, the previous ciphertext block is encrypted, and the output is XORed with the current plaintext block to create the current ciphertext block. 4. Output Feedback Mode (OFB)In certain ways, CBC and OFB modes are comparable and can be used with any block cipher. It uses a feedback mechanism; however, in OFB mode, the preceding block of ciphertext is XORed with the plaintext after encryption rather than prior to encryption. 5. Counter Mode (CTR)CTR mode uses a block chaining mode of encryption as a building block. The process of encrypting data is performed by XORing the plaintext with a series of pseudorandom values that are each created from the ciphertext using a feedback function; data is encrypted. A series of XORs between blocks of plaintext and corresponding blocks of ciphertext can be used to represent the CTR encryption process. Examples of Block CiphersThe majority of contemporary cipher suites are based on block ciphers. Several encryption standard protocols that utilise block ciphers are: 1. Data Encryption Standard (DES)Initially, sensitive, private information was protected using a 56-bit symmetric key algorithm. DES was later discontinued because of its short length and other security issues, although it is still regarded as a pioneer encryption standard. 2. Advanced Encryption Standard (AES)It is a popular block cipher which encrypts data in blocks of 128 bits using 128, 192, and 256-bit symmetric keys. The underlying block cipher uses substitution-permutation and transportation techniques to produce ciphertext by shuffling and replacing input data in a sequence of linked calculations. AES is a widely encryption standard since cryptanalysis efforts against its algorithms have been ineffective. 3. TwofishTwofish is an encryption standard that uses a Feistel network, a complex key schedule, and substitution techniques to separate the key and ciphertext. Using keys that can range in size from 128 to 256 bits, the standard encrypts plaintext data in blocks of 128 bits. Block ciphers are also used by other encryption schemes such as 3DES, Serpent, and Blowfish. What is Stream Cipher?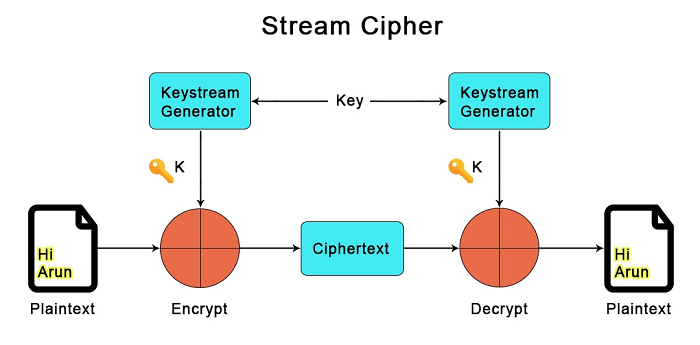
A stream cipher uses time-varying changes on plaintext data to encrypt a continuous string of binary numbers. As a result, this method of encryption works bit-by-bit, utilising keystreams to generate ciphertext for arbitrary lengths of plain text messages. The cipher combines a key (128/256 bits) and a nonce digit (64-128 bits) in order to generate the keystream - a pseudorandom number XORed with the plaintext to generate the ciphertext. The keystream must be different for each encryption iteration even though the key and nonce can be reused to maintain security. In order to build the keystream, stream encryption ciphers generate a unique nonce (a number used only once utilising feedback shift registers. Since a mistake in the translation of one bit often does not affect the entire plaintext block, stream cipher encryption algorithms are less likely to cause system-wide errors to spread. Additionally, stream encryption is linear and continuous, making it easier and quicker to deploy. However, stream ciphers do not have diffusion because each digit of the plaintext is mapped to one ciphertext output. Furthermore, they don't check for validity, which leaves them open to insertions. If hackers defeat the encryption algorithm, they are able to add to or change the encrypted message without being noticed. Stream ciphers are typically used to encrypt data in an application where the volume of plain text cannot be predicted and in low latency use-cases. In other words, a stream cipher is a type of encryption that uses plain text numbers and a stream of pseudorandom cipher digits. Each binary digit receives one bit at a time of this pseudorandom encryption digit stream. This encryption technique uses an infinite number of pseudorandom cipher digits for each key. State cipher is another name for a stream cipher. The term "state cipher" refers to a system where the encryption of each number is dependent on the cipher's current state. Types of Stream CiphersThere are two types of Stream Ciphers: 1. Synchronous Stream Ciphers In a synchronous stream cipher, the keystream block is created independently of the previous ciphertext and plaintext messages. The most popular stream cipher modes produce a string of bits using pseudorandom number generators and combine it with the key to create the keystream, which is then XORed with the plaintext to produce the ciphertext. 2. Self-Synchronizing/Asynchronous stream Ciphers The previous ciphertext block's fixed size (N-bits) and symmetric key are used to generate the keystream block via a self-synchronizing stream cipher, also known as ciphertext autokey. Asynchronous stream cipher can recognize active attacks by altering the ciphertext, which changes the information in the subsequent keystream. Due to the fact that a single-digit error can only affect a maximum of N bits, these ciphers also have restricted error propagation. Example of Stream CiphersThe following are examples of stream ciphers: 1. River Cipher (RC4)A quick and easy encryption algorithm called RC4/ARC4/ARCFOUR was created in 1987 to accomplish byte-by-byte encryption utilising 64- or 128-bit length keys. Transport Layer Security, secure Sockets Layer, and the IEEE 802.11 WLAN standard all use extensively RC4. The widely used encryption method is available in a number of variations, including SPRITZ, RC4A, and RC4A+. 2. Salsa20Salsa20 is a powerful, up-to-date encryption cipher that creates the encryption keystream using an expansion function. Salsa20 also relies on a core function which uses add-rotate-XOR (ARX) operations to map the key, a nonce digit, and constant vectors retrieved from the expansion function to the keystream. 3. Software-Optimized Encryption Algorithm (SEAL)An additive binary stream cipher called SEAL is designed for systems with 32-bit CPUs and enough RAM. The encryption standard depends on a pseudorandom family that maps a 32-bit string to any length string using a length-increasing function and a 160-bit key. PANAMA, Scream, Rabbit, HC-256, and Grain are a few other examples of stream ciphers. Difference Between Block Cipher and Stream Cipher
Advantages of Stream Cipher Over Block CipherThe following are the advantages of stream cipher over block cipher:
Key Differences Between Block Cipher and Stream Cipher
Next TopicDifference between
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










