Challenge Response Authentication Mechanism (CRAM)The most popular method for authenticating operations is the Challenge Response Authentication Mechanism (CRAM). They are a collection of protocols in which one side issues a challenge (to be addressed) and the other side is required to respond with the right response (to be verified/checked) in order to be authenticated. 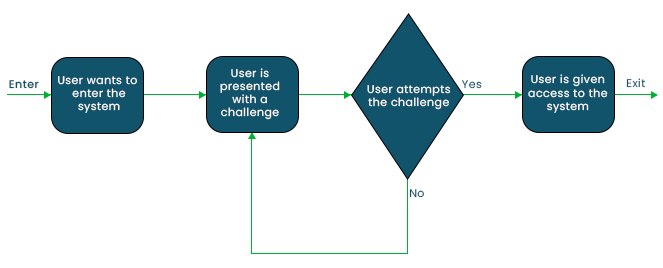
Challenge questions come in two flavours:
Methods of CRAM execution -1. CAPTCHA: The Fully Automated Public Turing Test to Distinguish Between Computers and People Spam and the automatic creation of new accounts on websites or for email are both stopped by CAPTCHA. 2. Secure Shell, or SSH SSH is a cryptographic network protocol that enables the secure operation of network services over insecure networks. 3. Password: The password is transmitted to the server, where it is checked by comparison with the right password. 4. A variation of CRAM called Salted Challenge Response Authentication Mechanism (SCRAM): To ensure that the password is only used once, the challenge is hashed and salted. Instead than matching the plain text password itself, the server compares the hash against the hash of the correct password. Because the password may only be used once, it cannot be divulged, preventing Man-in-the-Middle and replay attacks. 5. Biometrics: Every time a user wishes to verify himself, he must provide his unique biometric information (such as a retina scan or fingerprint scan) to the authenticating system for verification. How to Use Challenge-ResponseA challenge-response barrier is a security measure used to keep assets safe from unauthorised users, activities, programmes, and internet of things (IoT) devices. It requires cyber attackers to complete a series of challenges in order to bypass the security barrier and gain access to additional materials. A commercial bank, for example, creates a multifactor authentication (MFA) process using challenge-response authentication. Using multiple CRAMs, this process authenticates a user's identity. A two-factor authentication (2FA) process might entail entering a password and receiving a code via email. An MFA variant may also ask a personal question, such as "What is your mother's maiden name?" However, account logins aren't the only use of challenge-response authentication. CRAM Utilise cases
The user is shown an image, which is typically difficult to read at first look, and is then requested to input by deciphering the characters in the image. To stop bots from accessing the system, the input is then compared with the actual characters.
An image is cut up and confused before being submitted to the user for some form of human user-verifiable authentication. The input is used to validate user input. The user's response and the answer provided by the ML model are compared. The "task" is to choose the correct parts from the jumbled-up image. in Google CAPTCHA authentication frequently observed.
The proper password, which is already saved on the server you are attempting to access, is compared (directly or indirectly) with the one you entered to see if they match. Typical CRAM attacks include:
Limitations -One fundamental issue with passwords is that they are used repeatedly. When a password is received by the server, the server cannot determine whether or not the password is being entered by the real user. Newer CRAMs also use cryptography to match the hash of the passwords rather than the plain passwords. Some cryptographic CRAM examples -
Next TopicExtended Access List
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










