Computer Science Quiz - II: Part 1Topic 4 - Computer Networks1) One gigabit per second (Gbps) over a one-kilometre cable with no repeaters is the speed of a network using the MAC layer CSMA/CD protocol. The cable's capacity for signal transmission is 2 � 108 m/sec. This network's minimal frame size should be
Answer: (a) 10000 bits Explanation: Given that, Bandwidth, B = 1 Gbps = 109 bit per second Length, L = 1 Km = 103 meters Speed, S = 2 x 108 m/sec Frame Size, F = ? We know that Transmission Time (Tt) = 2 x Propagation Time (Tp) Where, Tt = F/B ______ (i) And Tp = L/S ________ (ii) From (i) and (ii), we get 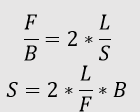
F = 2 * 103 * 109 / 2 * 108 F = 104 bits = 10000 bits Hence, (a) is the correct answer. 2) Consider a CSMA/CD network that uses a kilometer-long cable and 100 Mbps (108 bits per second) of data transmission to send information. How fast is the signal travelling through the cable, in kilometers per second, if the network's minimum frame size is 1250 bytes?
Answer: (c) 20000 Km/sec Explanation: Given that, Bandwidth, B = 1 Mbps = 108 bit per second Length, L = 1 Km = 103 meters Frame Size, F = 1250 bytes = 1250 * 8 bits Speed, S = ? We know that Transmission Time (Tt) = 2 x Propagation Time (Tp) Where, Tt = F/B ______ (i) And Tp = L/S ________ (ii) From (i) and (ii), we get 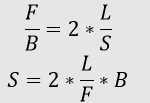
S = 2 * 103 * 108 / 8*1250 S = 2 * 1011 / 104 F = 2 * 107 = 20000 * 103 m/sec F = 20000 Km/sec Hence, (c) is the correct answer 3) Which of the following claims concerning CSMA/CD is TRUE?
Answer: (c) A network with a long propagation delay, such as a satellite network, cannot use CSMA/CD. Explanation: For the receiver to be able to identify any collisions, CSMA/CD mandates that the sender must continue transmitting at least until the first bit arrives at the destination. The minimum packet size required grows too large to be practical for networks with high prorogation delays because this time becomes too long. 4) The frame delimiter flag in a data communication protocol is indicated by 0111. The transmitter needs to broadcasts the data sequence 01110110. The data sequence obtained after bit-stuffing
Answer: (c) 011010110 Explanation: The sender will stuff '0' bit when it finds 011 sequence in data. So, the data sequence obtained will be 0110101100, marked bit are stuffed bit. Hence, (c) is the correct answer. 5) An 8-bit delimiter pattern of 01111110 is employed in a framing system that involves bit-stuffing. If 01111100101 is the output bit-string after stuffing, then the input bit-string is
Answer: (c) 0111110101 Explanation: The 8-bit delimiter is 01111110, so every '011111' sequence is data sequence is followed by a bit '0'. The output is 01111100101, where marked bit is the stuffed bit. Hence, the input bit-string is 0111110101. 6) Which of the following claims about an Ethernet local area network is TRUE?
Answer: (d) Explanation: The most common and commonly utilised LAN network for data transfer is Ethernet. It is a protocol for the data connection layer that describes how to prepare data for transmission and where to put it on the network. Now that we are thinking about the Ethernet protocol, we will go over each choice individually. (A) This choice is false since an Ethernet station is not required to pause before transmitting a frame in order to sense the channel. (B) A signal is jammed to block further data transmission by alerting all other stations or devices about the collision that has occurred. Therefore, this choice is likewise false. (C) Data transmission is halted after a collision occurs as a jam signal is sent. As a result, this choice is likewise false. (D) An exponential back-off method is utilized to lower the chance of collision on retransmissions. Therefore, only this choice is True. 7) Both protocols in one of the pairings listed below can employ numerous TCP connections between the same client and server. One of those is which?
Answer: (a) HTTP, FTP Explanation: If non-persistent connections are utilized, HTTP may employ various TCP connections for various webpage items. Two TCP connections are used by FTP, one for data and the other for control. Only ONE connection can be used simultaneously by TELNET and FTP. 8) which of the following employs UDP as the transport protocol?
Answer: (c) DNS Explanation: User Datagram Protocol (UDP) on port 53 is the primary protocol used by DNS to process requests. During a DNS query, the client sends a single UDP request, and the server responds with a single UDP response. 9) The following block of CIDR-based IP addresses is available to an Internet Service Provider (ISP): 245.248.128.0/20. The ISP wishes to keep half of this collection of addresses for itself, and give half to Organization A and half to Organization B. Which of the following assignments of addresses to A and B is legitimate?
Answer: (a) 245.248.136.0/21 and 245.248.128.0/22 Explanation: The ISP has 2(32-20) or 212 addresses because the routing prefix is 20. Half (or 211) of these 212 addresses must be given to organization A, and the remaining quarter (210) must be handed to organization B. Therefore, organization A's routing prefix will be 21. It will be 22 for B. Only alternatives (A) and (B) remain when we examine all the possibilities provided in the question since only them have the same number of routing prefixes. Currently, we must select between Option (A) and (B). ISP must take the first 20 bits of the address 245.248.128.0 and fix the 21st bit as 0 or 1 in order to allocate addresses to organization A. Similar to this, ISP must correct organization B's 21st and 22nd bits. The 21st and 22nd bits for organization B are treated as 0 in both choices (A) and (B), as can be seen if we look at the options (A) and (B) in more detail. Therefore, Organization A's 21st bit must be 1. The addresses for organization A are 245.248.136.0/21 if the first 20 bits of the address 245.248.128.0 are taken, and the 21st bit is set to 1. 10) Considering that the host has just been restarted, determine the proper order in which the upcoming packets are sent across the network by a host when a browser requests a webpage from a distant server
Answer: (c) DNS query, TCP SYN, HTTP GET request Explanation: When a client requests information, the server determines the DNS. To find the address of DNS, execute a DNS (domain name server) query. After then, a TCP connection must be created in order to continue speaking. Sending a TCP SYN message will create a TCP connection. Send an HTTP GET request to the server to retrieve the webpage it should show after the connection has been established. The TCP connection is terminated by the server when the response has been provided. 11) The hosts of a private network must be permitted to open TCP connections and send packets on open connections by means of a firewall that has been set up to support this. However, it won't permit external hosts to open TCP connections to hosts in the private network; instead, it will only permit them to deliver packets across open TCP connections that already exist or connections that are being opened (by internal hosts). The firewall should have the following minimal capabilities in order to achieve this:
Answer: (d) A pushdown automaton with two stacks Explanation: Option a) A combinational circuit is not the correct answer since the firewall requires memory, and combinational circuits have none. Option b) A finite automation is not the right answer because we require limitless memory, and there is no maximum number of TCP circuits. Option c) A pushdown automaton with a single stack - The stack is limitless; thus, this choice is invalid. If there are two connections and their details have been pushed onto a stack, the connection whose details were pushed first cannot be accessed without popping it off. Option d) Two stacks and a pushdown automaton - This is the Turing machine, so this choice is accurate. It can perform all operations that a regular computer can, Yes. Turing machines can be used to build firewalls. 12) Think about the Linux system's socket API, which supports connected UDP sockets. A connected UDP socket is one that has previously had its connect function invoked. Which one or ones of the following statements are TRUE? I. It is possible to communicate with numerous peers at once using a linked UDP socket. II. For a connected UDP socket, a process can successfully call the connect method once more
Answer: (b) Only II Explanation: I. False - It is not possible to communicate with numerous peers at once using a linked UDP socket. Despite the fact that UDP lacks connections, each UDP socket has a unique IP address and port number to connect to. As a result, we are unable to connect to numerous peers using the same socket at once. II. True - For a connected UDP socket, a process can successfully call the connect method once more. If the implementation permits, we can call connect again to connect to a new peer and disconnect the prior peer. 13) A TCP connection between a client process P and a server process S is required. Think about the following circumstance: The socket (), bind (), and listen () system calls are executed by the server process S in that order, after which it is preempted. The client process P then uses the socket () and connect () system calls to establish a connection with the server process S. There have been no accept () system calls made by the server process. Which of the following scenarios is possible?
Answer: (c) connect () system call returns an error Explanation: Because the accept () method is not run, connect () receives no response for a time stamp to wait, returns no response server error, and then no response is received 14) Which of the above socket API calls turns a disconnected active TCP socket into a passive socket?
Answer: (d) listen () Explanation: When a socket is marked as passive by the listen () function, it is indicated that it will be utilized to accept incoming connection requests made by accept (). 15) Take into account the following claims regarding the TCP timeout value. I. For the whole time that the connection is active, the timeout value is set to the RTT (Round Trip Time) that was recorded during TCP connection creation. II. The timeout value of a TCP connection is set using an appropriate RTT estimate algorithm. III. The timeout value has been configured to double the propagation time between the sender and the receiver. Which of the options below is correct?
Answer: (b) II is True but I and II are False Explanation: Time-out timer in TCP: Since data link layer (DLL) connections are hop-to-hop, it is impossible to tell how many hops are involved in getting data from sender to receiver since IP service is utilised, and the path may occasionally change. Therefore, TCP makes use of dynamic timers. To prevent unneeded congestion brought on by retransmissions, the time-out timer should be adjusted to grow or decrease as traffic dictates. For this, three algorithms are available:
Option I is False because we need a dynamic timer for the timeout since the timeout value cannot be fixed for the duration of the timeout because that would make the timer static. Option II is True because all three algorithms can be used to establish timeout values dynamically and are suitable for RTT estimates. Option III is False because the data link layer, where hop to hop distance is known, sets the timeout amount to double the propagation delay, not in the TCP layer. 16) Which of the subsequent assertions is FALSE?
Answer: (b) Compared to circuit switching, packet switching produces less fluctuation in delay is incorrect. Explanation: According to the destination address in each packet, data is transferred through packet-switched networks in discrete, tiny packets. The message is created by reassembling the packets in the correct order once they have been received. Dedicated point-to-point connections are necessary when using circuit-switched networks.
Hence, only b is false. 17) Time to Live (TTL) is a header field that is included in an IP datagram. The requirement for this field is best explained by which of the following statements?
Answer: (d) The use of it can stop packet looping. Explanation: An IP datagram's Time to Live can be viewed as a time limit on how long it can exist in a network. A situation where a datagram that cannot be delivered keeps circulating is prevented by the TTL field. 18) An IP datagram D is sent from host A (on TCP/IP v4 network A) to host B (on TCP/IP v4 network B). Assume that D was transmitted without any errors. Which IP header field(s) from the list below may not match the original datagram's when D reaches B?
Answer: (d) I, II and III Explanation:
Therefore, (d) is the correct answer. 19) Which of the following claims is accurate?
Answer: (c) A CRC field is present in an Ethernet frame, and a checksum field is present in an IP packet. Explanation: A 32bit CRC is present in Ethernet Frame shown in the figure. Image Here A 16bit Header checksum is present in an IP datagram shown in the figure. Image Here Hence, (c) is the correct answer. 20) Which of the following IP header fields does NOT undergo modification by a standard IP router?
Answer: (b) Source Address Explanation: When IP fragmentation occurs, length and checksum may be altered. Every router on the path to the destination decreases Time To Live. The source address does not change at any instant.
Next TopicComputer Science Quiz - II: Part 2
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










