Attacking a WebsiteIn this section, we are going to discuss attacking a website. For attacking websites, we have two approaches:
If both of the methods fail, we can try to test the web application, because it is just an application installed on that website. Therefore, our target might not be the web application, maybe our target is just a person using that website, but whose computer is inaccessible. Instead, we can go to the website, hack into the website, and from there go to our target person. All of the devices and applications are interconnected, and we can use one of them to our advantage and then make our way to another computer or to another place. In this section, instead of focusing on client side and server side attacks, we will be learning about testing the security of web application itself. We are going to use the Metasploitable machine as our target machine, and if we run ifconfig command, we will see that its IP is 10.0.2.4, as shown in the following screenshot: 
If we look inside the /var/www folder, we are able to see all the website files stored, as shown in the following screenshot: 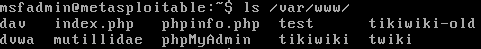
In the above screenshot, we can see that we have phpinfo.php page, and we have dvwa, mutillidae, and phpMyAdmin. Now, if we go to any machine on the same network, and try to open the browser and go to 10.0.2.4, we will see that we have a website made for Metasploitable, as shown in the given screenshot. A website is just an application installed on the web browser, and we can access any of the Metasploitable websites and use them to test their security: 
Now we are going to look at DVWA page. It requires Username as admin and Password as password to log in. Once we enter these credentials, we are able to log in into it, as shown in the following screenshot: 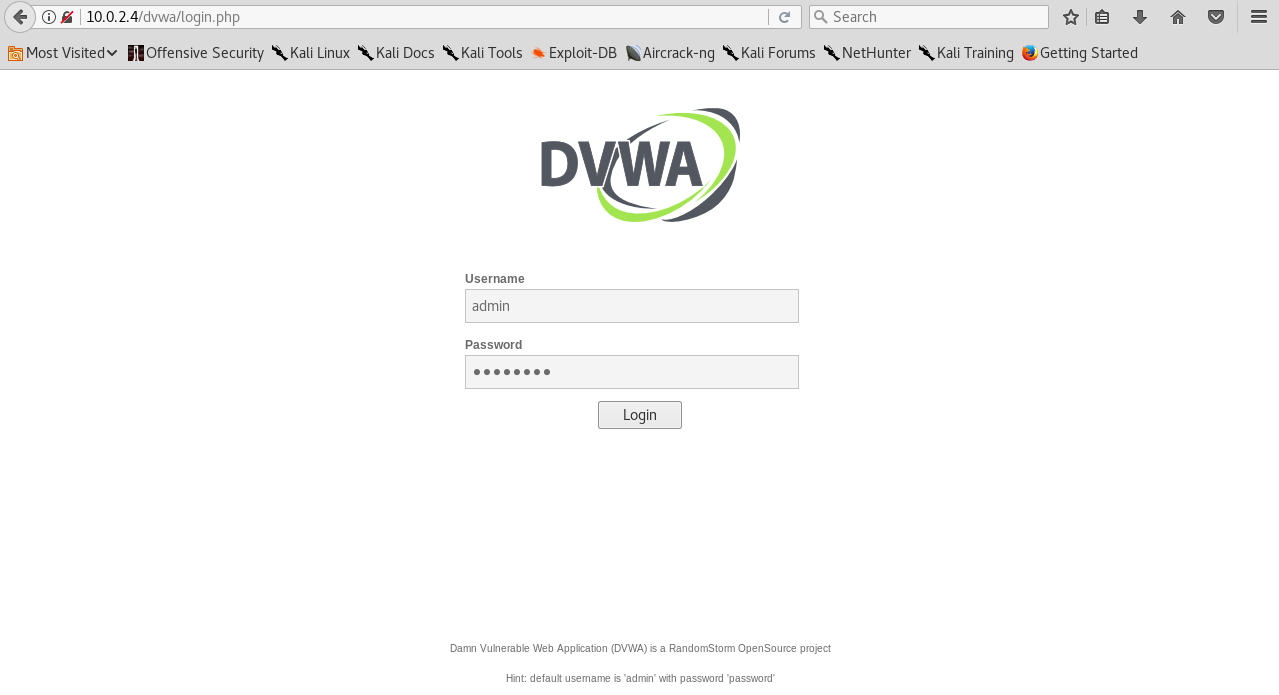
Once we logged in, we can modify the security settings by using the DVWA Security tab, as shown in the following screenshot: 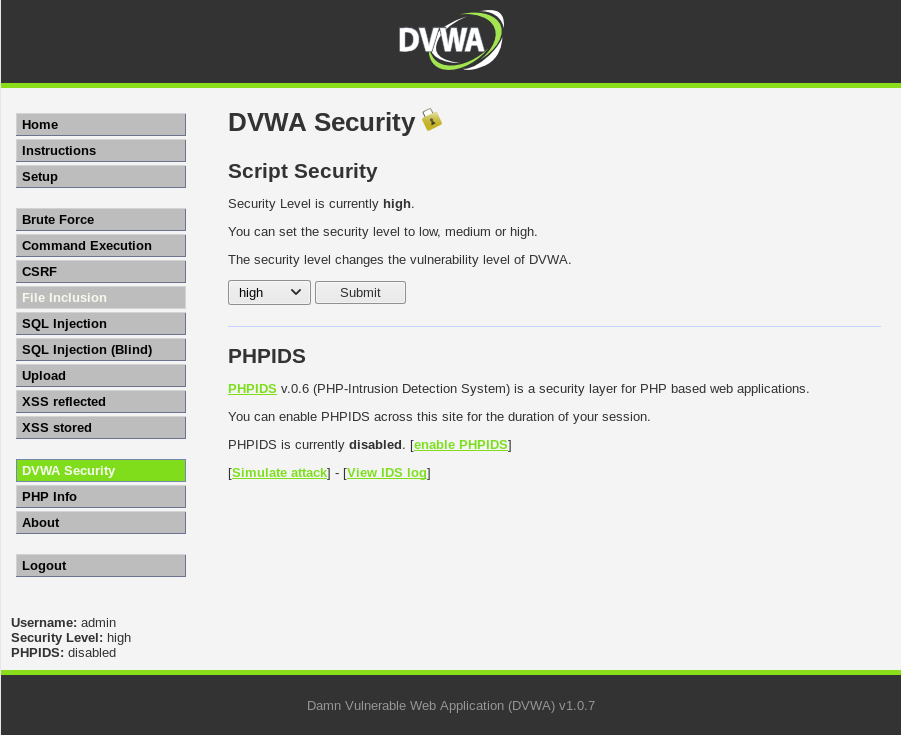
Under the DVWA Security tab, we will set Script Security to low and click on Submit: 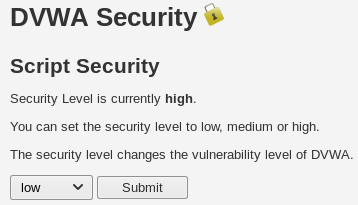
We will keep it set to low in the upcoming section. Because this is just an introductory course, we will only be talking about the basic way of discovering a web application vulnerabilities in both DVWA and the Mutilliidae web application. If we go to the Mutillidae web application in the same way that we accessed the DVWA web application, we should make sure that our Security Level is set to 0, as shown in the following screenshot: 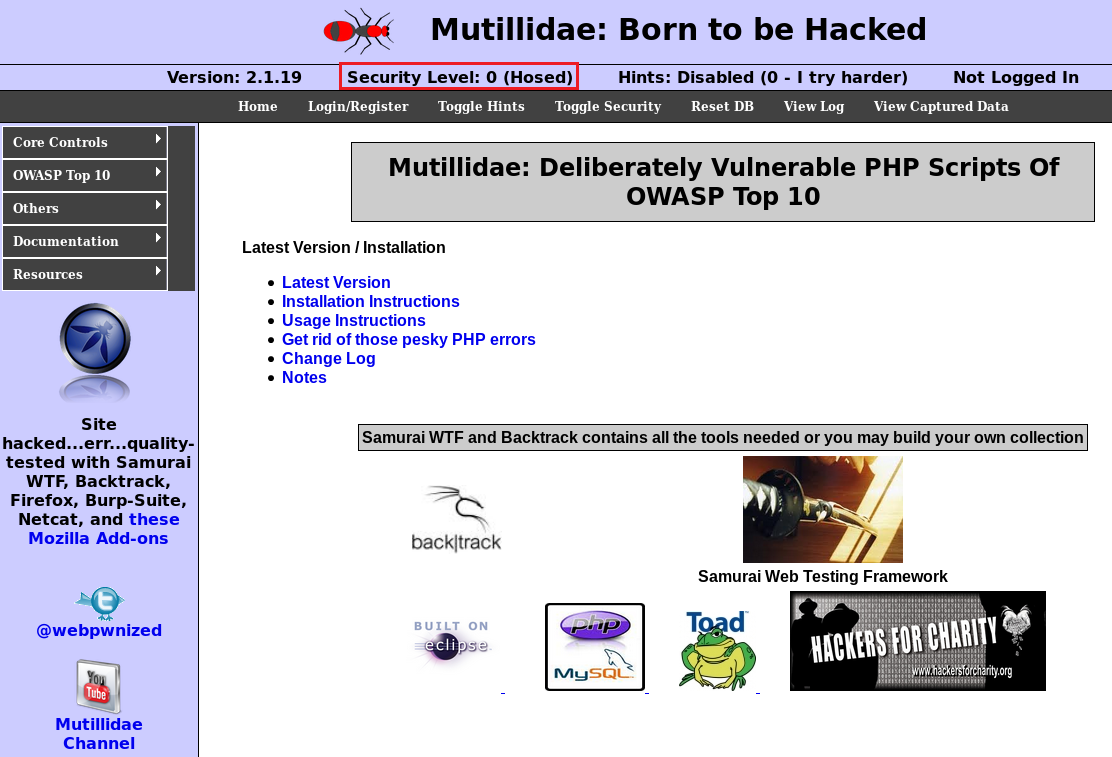
We can toggle Security Level by clicking the Toggle Security option on the page: 
Next TopicInformation Gathering
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










