Discovering SubdomainIn this section, we will study subdomain. We see subdomain everywhere, for example, subdomain.target.com. Now, if we have beta.facebook.com, we would have mobile.facebook.com, or we might have user.facebook.com. Suppose we google mail.google.com, which takes us to Gmail. Subdomain is used in lot of cases, websites have subdomain for their own users, for example, for certain customers or for employees, so they are not advertised unless it is some sort of VIP customer. We will not see subdomain on search engine and we will never see a link leading to them, so they might contain exploits or vulnerabilities that will help us to gain access to the whole website, but we never knew about that exploits or vulnerabilities because they are never advertised. Another thing is, when a lot of big websites trying to add a new feature or install a new update to the website, then install it in a subdomain, so we have beta.facebook.com, which contains a beta version of Facebook, which contains experimental features. Now experimental features are great for hackers because they are still under development, and there is a high chance of finding exploits in them. This is actually true because before some time ago, someone was able to brute-force the restore password key for any Facebook user and was able to gain access to any Facebook user's account. This was only possible through beta.Facebook.com because Facebook used to check for a number of attempts or failed attempts, and they didn't implement that security feature in beta version because they did not think anyone was going to go there. Beta usually has more problem than the normal website, so it is very useful to try and hack into it. In this section, we will see how we can find any subdomain that have not been advertised, or even advertised ones, so we will be able to get subdomain of our target. We are going to use a tool named as knock. This tool is very simple and we don't need to install it. We only have to download it using a git command. To do this we put the command git clone and then we put the URL of tool as shown below: 
Once it is downloaded, we will use cd command to navigate it. After navigation we will see that we have .py file, as shown below: 
Now, we will run this file using the python knockpy.py command, and then we will enter the website that we want to get the subdomain of, which is isecur1ty.org. The command is as follows: 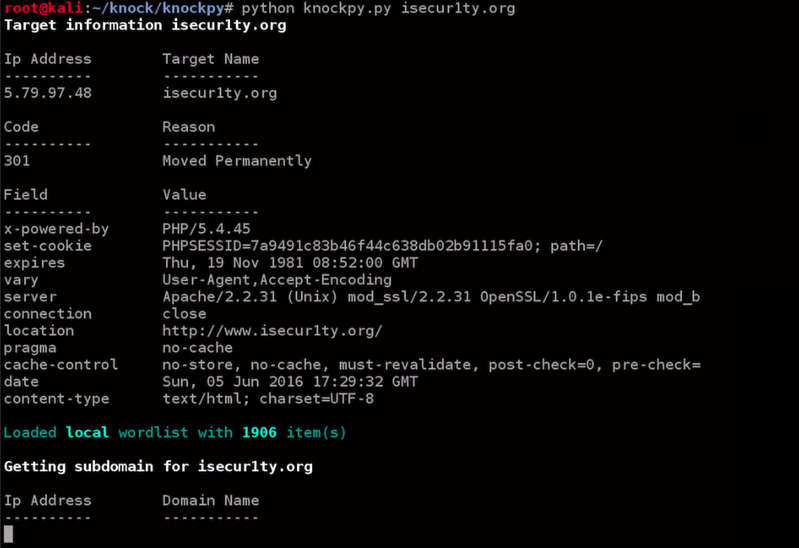
It will perform a brute-force and a Google-based subdomain search for isecur1ty, and it will show us any subdomain that isecur1ty might have that we could try and test security of and see what's installed on it. Maybe we will be able to gain access to the website through that subdomain. Once the scan is complete, as we can see in the following screenshot, we managed to find seven subdomain that were not advertised: 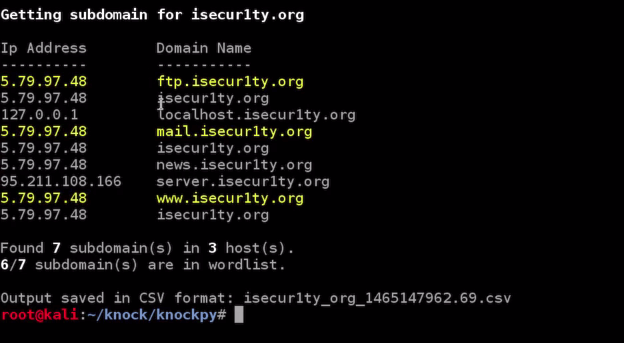
Now, one of them is ftp.isecur1ty.org. We already discussed about isecur1ty.org, and localhost.isecur1y.org is just a local subdomain. We can see that the mail.isecur1y.org has its own subdomain as well, and we can see a very interesting one, news.isecur1ty.org. It actually did contain a beta version of a script that has been worked on. Hence, if someone was trying to hack into our website, they would actually see that there is a script under development, and there is a high chance that they would have been able to find a vulnerability in it and gain access to the whole website. This shows us again how important information gathering is, which can be used to gain access to websites. If we don't do it, we will be missing a lot of things. For example, we might be missing a whole script with a whole number of vulnerabilities, or we could be missing an admin login page or an employee login page.
Next TopicAnalysing Discovering Files
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










