How to Check System Configuration in Ubuntu?Introduction to System ConfigurationIn system engineering, a system configuration defines the devices, processes, and computers that construct the system and its edge. The system configuration is more generally the particular definition of the components that define or/and prescribe what a system consists of. The term, i.e., "system configuration", can alternatively be used for relating to a model for a generalized abstract system. The configuration information usage is not tailored to a particular usage; it stands alone as any data set. A correctly configured system ignores resource-conflict issues and makes it easier for upgrading a system with newer equipment.
A computer system, specifically an operating system, commands a group of default configurations and settings when the system comes online first. These settings command the common features and functions that make the system execute in a stable manner. The operating systems have their configuration utilities to permit users or administrators to modify the system configuration. It is known as "msconfig" or "Microsoft System Configuration Utility" for Microsoft Windows. Sample ConfigurationBelow is a common SC XML System Configuration: It gives information about one "site" and defines that there is a single host with mysql-db and user-setup elements. The host should have any account with correct parameters for a user named mysql. The configuration schema needs no XML tags that are Unix- or Windows-specific. Simply, it illustrates data as standalone information. It is the indication of a positive model of system configuration. This model can be continued. For example, a user can have more attributes, such as "password" and "preferences". The elements can rely on other elements. Properties can be described that are passed into sub-components. The extensions could be endless and must be handled for preventing "breaking" the concept of the system configuration. Usage of System ConfigurationIn practical terms, the usage of the model falls into many categories, including operations, deployment, and documentation. 
OperationsIn the system, there may be used for configuration data by particular types of services during system operation. For instance, a Secnager may use the configuration to inherit the MD5 passwords for many user accounts that are permitted to remotely log into hosts. A service, i.e., a system monitor, may utilize the data for determining "how to monitor" and "what to monitor" the system components. The PresentationManager might utilize the data for accessing views and menu items based on the user access privileges. DeploymentIt involves describing a set of configuration data and operating on the data for realizing the system configuration accordingly. Simply, it may be a validation of what is there to ensure that the configuration is in the event. Some examples are available, including a Perl library opened from the command line for reading the configuration and start launching processes on the remote or local hosts to install elements. There may also be a service, i.e., SystemConfiguration, that offers an interface for other system software to use the configuration data and implement deployment-like tasks while the system is executing. DocumentationOne configuration use is to simply file what a system is. In turn, this documentation can become quite costly, thus convoluting the data model. It's important to differentiate between descriptive data and configuration data. The comments can be used at any level; however, the data bloating can decrease its usefulness. For instance, the system configuration isn't a place for recording historical changes or design descriptions and intent for the several components. The configuration data is to be "what we want it to be" or "what it is". Configuration ManagementConfiguration management is a system engineering process to establish and maintain consistency of the physical, functional, and performance attributes of a product with its operational information, design, and requirements during its life. Configuration management is a form of ITSM (IT Service Management) as described by ITIL that ensures the system configuration servers, computer systems, resources, and other assets are trusted, known, and good. It is sometimes called IT automation. Almost all configuration management involves a higher degree of automation for achieving these goals. It is why teams utilize different tools, such as Terraform, Ansible, Puppet, and other tools of configuration management. It is easier to build redundancies and in-checks, developing the potential for omissions because of the accuracy and human error to keep assets in the wanted state using automation. Without automation, one engineer can forget to update a software piece, and it can leave the system with an older software version that has a known vulnerability mentioned on CVE. This vulnerability can be accomplished by installing ransomware, spreading system worms, or other types of malware. Configuration management uses in several systems, but we will be concerned with the following:
What is the Importance of Configuration Management?When we open the settings menu in our software, we compromise with configuration management. We need to carefully handle it and keep track of configuration modifications to ensure traceability, or our business and end users can suffer from data leaks, data breaches, and system outages. To improve operations and decrease cybersecurity risk, several businesses use CMDB (Configuration Management Database), configuration management, and configuration management plan to ensure good configuration management. It helps with audit processes, asset management, and project management, as well as debugging and software development. Other advantages of configuration management are mentioned below:
What will Happen if We Don't Apply Configuration Management?We can ignore the costs related to configuration management by not using it at all. Although, we will pay in:
What are the Famous Configuration Management Tools?There are several famous tools of configuration management, which makes it complicated to find a stack of tools or a single tool that meets the requirements of the system configuration of our organization. The necessary tradeoffs and features we need to consider such as cybersecurity, enterprise support, ease of use, compatibility with older systems, always key to scale a data center, and performance. Tools such as Microsoft System Center Configuration Manager, Puppet, and Ansible have massive communities when it comes to market share. However, there are only some replacements in the configuration management space. Here are a few of the most famous tools we can consider: 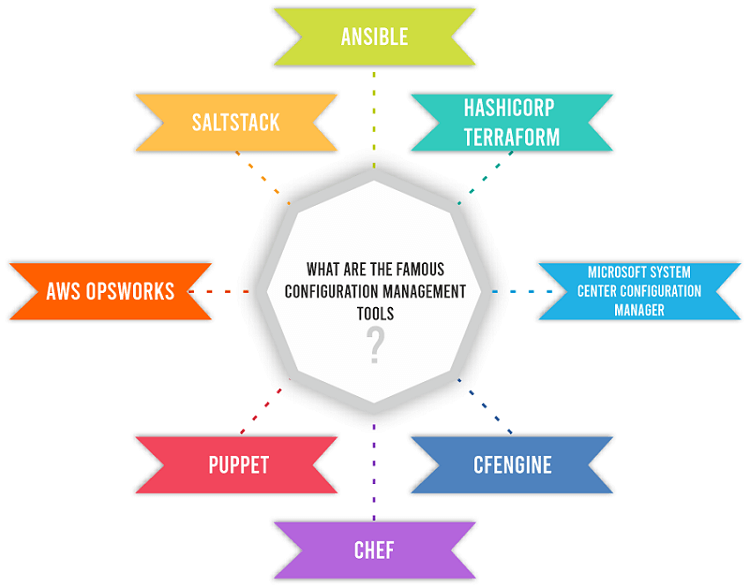
Checking System Configurations on UbuntuAll computers have many hardware elements. They are from distinct vendors and have various essential information related to them. If we face any issue with any of these hardware elements, this information is necessary to resolve them. For instance, if we wish to post on an online blog or forum about our issues, people can give us better explanations if they know about the hardware elements we have. Check CPU InformationWe can find several details about the CPU of our computer with the command, i.e., dmidecode, on Ubuntu. The command is as follows: 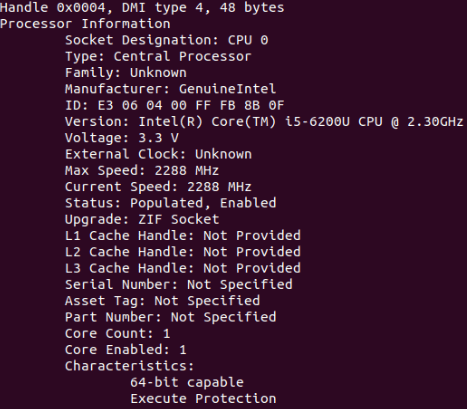
Note: If we are using any virtual machine, we will not get several details.Check RAM InformationWe can find details about the RAM or memory of our computer with the command, i.e., dmidecode. The command is as follows: 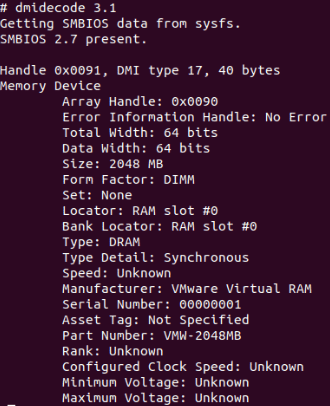
All details about our RAM should be shown. Check Motherboard InformationWe can find details about the motherboard with the command, i.e., dmidecode. The command is as follows: 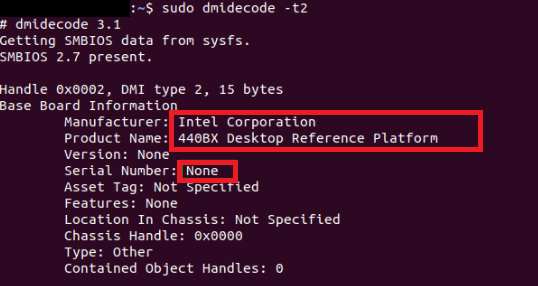
We should see the below details. The vendor or the manufacturer of your motherboard, the serial number, and the product name should be mentioned here, as we can see in the following screenshot: Check On Board Devices DetailsWe can check details about the built-in devices on our motherboard, like the sound card or graphic card with the command, i.e., dmidecode. The command is as follows: 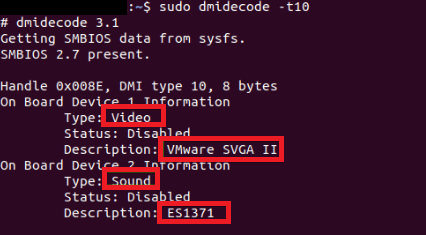
As we can see, we have two onboard devices on our virtual machine: a sound card and a video card: We can see the man page of the dmidecode command with the help of the following command for more details of it: Check Hardware Information using lshw CommandThe command, i.e., lshw, is very strong. We can use it to search hardware details of every available hardware of our computer. We can execute the below command for listing every hardware: 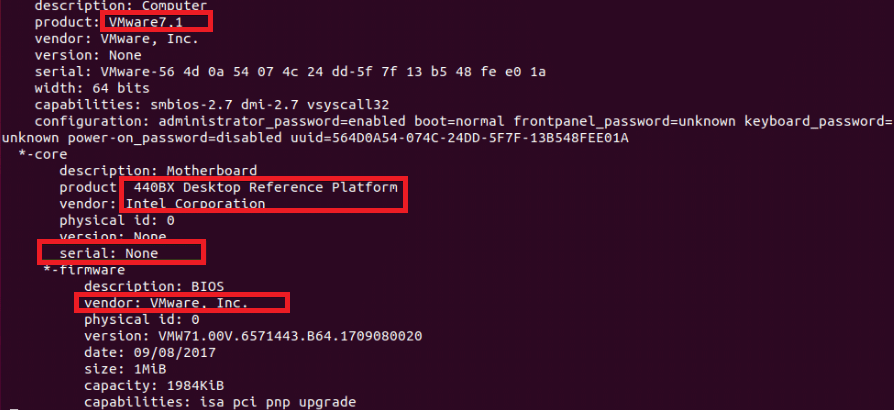
As we can see, every hardware detail is mentioned in the output. It is a very long list, so we pipped the result of the command to less. We can see the manufacturer or vendor of the hardware, their part number, name, serial number, and many more things here. Check Hardware Information using inix CommandAlso, we can check hardware details with the command, i.e., inix. By default, the inix command isn't available in Ubuntu. But we can easily get it from the official Ubuntu repository.
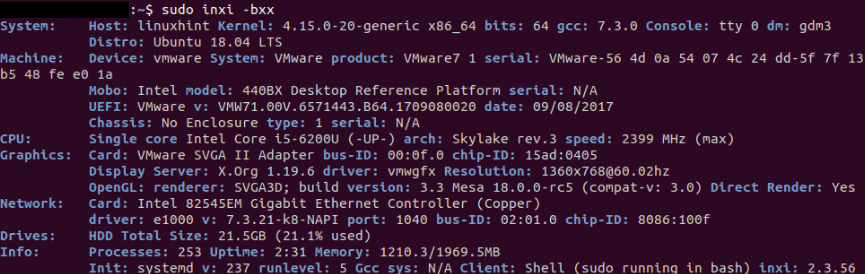
As we can see, every command hardware detail is printed in the above output.
Next TopicInstall httpd Ubuntu
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










