Linux sudoIntroductionThe Linux sudo command stands for Super User Do. Generally, it is applied as a prefix of a few commands that superuser is allowed to execute. If we prefix the command along with other commands, it would execute that command with high privileges. In other words, it will permit user along with proper authorization eating a command as other users like the superuser. It is equal to the option "run as administrator" in Windows. The sudo option allows us to have more than one administrator. The users who can apply the sudo command require to have the entry inside the file sudoers positioned at "/etc/sudoers/". Note: To view or edit the file we have to apply the sudo command. For editing the file, it is suggested to apply the "visudo" command.The sudo command by default needs that users verify themselves along with a password which is the password of the user, not a root password itself. Syntax of the sudo commandThe syntax of the sudo command is mentioned below: Option in sudo commandSome of the important options in sudo command are explained below: 1. -V: It stands for version. This option enables the sudo command for printing the number of the version and exit. The -V option would print out the defaults sudo list pause was observed if the requesting user is the root already. 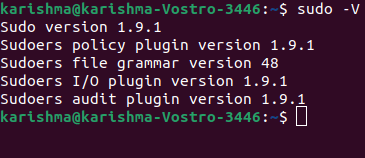
2. -l: It stands for list. This option will help to printout the various commands permitted the user over the current host. It shows that the current user could apply every command as sudo. 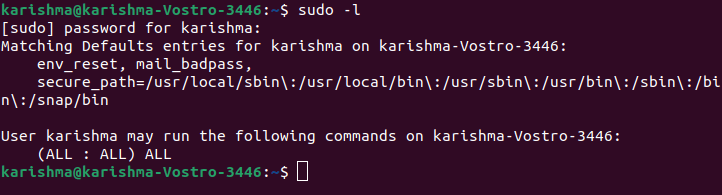
3. -h or -help: The h stands for help in this option. This option enables the sudo command for printing a message of the usage and exit. 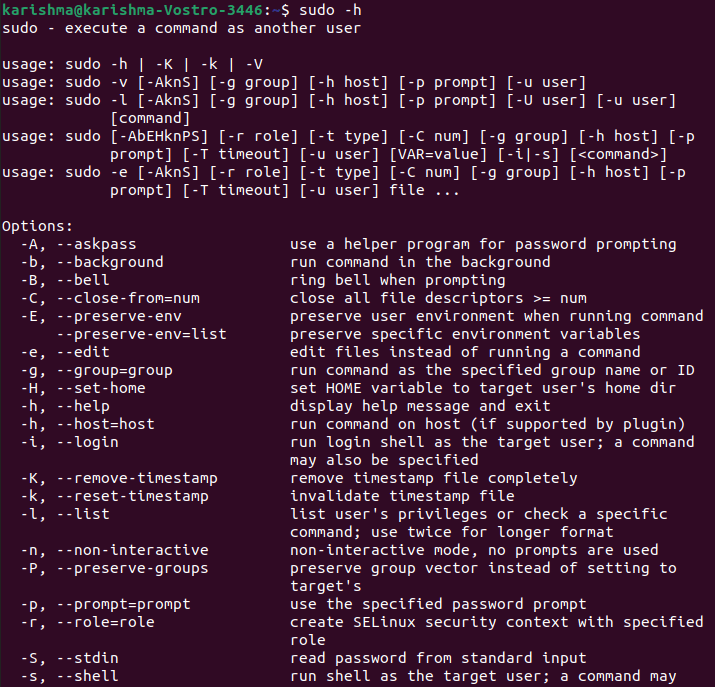
4. -v: It stands for validate. If the sudo command would update the timestamp of the user, the validate will prompt for the password of the user if necessary. It extends the sudo command timeout for the other 5 minutes but doesn't execute a command. It doesn't provide any result. 5. -k: It stands for kill. This option invalidates the timestamp of the user to sudo. Hence, the next time the sudo command is executed a password would be required. The -k option doesn't need any password and it was included for allowing the users to revoke the permissions of the sudo command through the .logout file. 6. -b: It stands for background. This option informs the sudo command to execute the provided commands inside the background. Note: If we apply this option we can't apply shell job control for manipulating the process.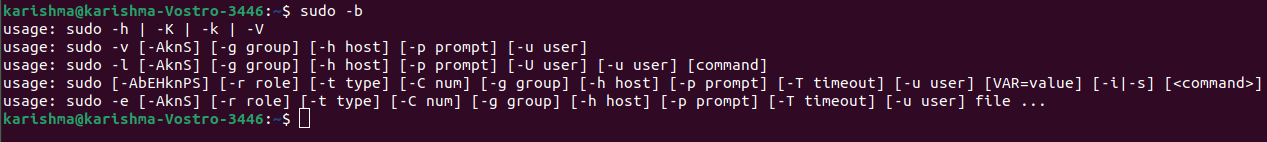
7. -K: This option is the same as the -k option. However, it stands for sure kill. This option is applied for removing the timestamp of the user entirely. It likewise doesn't need any password. 8. -p: It stands for prompt. This option permits us for overriding the password prompt (default) and apply a custom one. A few percent escapes are permitted which are as follows:
9. -n: This option will run the command without asking for the password. It is very useful if we wish to execute a few commands as background tasks (or inside the shell script), where we do not wish the sudo command for asking about the password. This option is short for non-interactive. 10. -u: It stands for user. This option enables the sudo command to execute the described commands other than the root as the user. For specifying a uid rather than the username, we can use the #uid. 11. -H: It stands for HOME. This option can set a HOME environment variable to our home directory of the root user as described inside the passwd file. The sudo command by default doesn't change HOME. 12. -s: It stands for the shell. This option executes the shell described through a SHELL environment variable when its set or this shell as described inside the passwd file. 13. -S: It stands for stdin. This option enables the sudo command for reading the password through standard input rather than the terminal device. 14. -: This option illustrates that the sudo command must stop processing the arguments of the command line. It is most helpful in conjunction with a -s flag. 15. -a: It stands for authentication type. This option enables the sudo command for using the described authentication type if validating a user, as permitted by the /etc/login/.config. The administrator of the system might describe the list of methods of the sudo-specific authentication by including the "auto-sudo" entry inside the /etc/login/.config. 
Environment Variables in sudo CommandThe following are some of the environment variables that are applied by the sudo command:
History of the sudo commandCliff Spencer and Robert Coggeshall wrote the actual subsystem in 1980 at SUNY/Buffalo at the Department of Computer Science. Robert Coggeshall carried sudo to the University of Colorado Boulder with him. Substantially, the features and code were changed by the IT members of the College of Engineering and the University Of Colorado Boulder Computer Science Department and applied science with Todd C. Miller between 1986-1993. Publicly, the latest version has been managed since 1994 by Todd .C Miller (OpenBSD developer) and has been shared since 1999 upon the ISC-style license. Thomas Claburn characterized such uncertainties as overblown in November 2009 in response to the thing that Microsoft had privilege sudo. Narrowly, the claims were framed to a specific GUI instead of the sudo approach. Design of the sudo commandUsers can supply their password to sudo when necessary instead of a superuser, unlike the su command. It permits accessible users for exercising qualified privileges without dealing secrecy of the password of the other account.
Configuration of the sudo commandThe /etc/sudoers file includes the user groups or list of users with permission to run a set of commands while containing the rights of a root user or other listed user. The program might be configured to need a password. Impact of the sudo commandIn a few system distributions, the sudo command has supplanted the use (default) of a different login of the superuser for various administrative operations, most importantly in a few Apple's macOS as well as Linux distributions. It prevents a few exploits and also permits for more protected logging of the admin commands. RBACThe sudo command could be used for transit between various types of roles within the role-based access control in collaboration with SELinux. Similar programs and toolsThe visudo is a utility of the command line that permits editing the configuration file of sudo inside a fail-safe way. It performs syntax and sanity checks and also prevents more than one simultaneous edits along with locks. The runas program facilitates the same performance in Microsoft Windows; however, it can't pass current long command lines to a child, environment variables, or directories. It doesn't support general elevation while it helps to execute the child as any other user. For windows, a true sudo and su that can transfer each of those state details and begin the child as another user or elevated are added with Hamilton C shell. The GUI is available for sudo (gksudo notably) but it is deprecated in Debian and also no longer in Ubuntu. Various other types of user interfaces aren't designed on sudo directly, but facilitate the same privilege elevation (temporary) for administrative goals like Authorization Sevices of Mac OS X, User Account Control inside Microsoft Windows, and pkexec inside the Unix-like operating systems. Since the 5.8 version of OpenBSD (October 2015), doas is available. It has been specified to substitute the sudo command inside the base system of OpenBSD. su vs. sudoIf we are accustomed to a more classical Linux setup, then we are used to applying the su command for gaining root privileges. We can issue the su command as well for effectively logging in as the root (the home of the root becomes our home). Using these kinds of distributions we can log in as a route user as well. But, it's not a good idea to login as a root user. If we are applying a distribution that depends on the su command and permits root user login, then login as our standard user and the su command to the root user. Most likely, we will notice that we can't log in as the root user using sudo-based distributions. In fact, in some distributions like Ubuntu, the account of the root user has been disabled. We can't log in as a root user and use the su command to become a root user. We could do is issue these commands using the sudo command for gaining administrative privileges. Usage of sudo commandThere are two different ways to execute administrative applications with Linux. Either we can change the superuser or root user using the su command or we can take benefit of the sudo command. When we utilize our time on the terminal, sudo is one of the important commands that we will quite frequently use. Using the sudo command rather than login in as the root user is more protected because we can grant only a few administrative privileges to a single user without his/her knowledge of the root password. How we implement it depends on which distro we use. A few distributions allow the root user (like OpenSUSE, Red Hat, or Fedora), while a few don't (like Debian and Ubuntu). Using the sudo command is simple in its very basic form. For example, we have to execute the dpkg for installing a software piece. If we just run the dpkg -i software.deb command as the standard user we will get an error message that the user doesn't have permissions to run the command. That's why by default standard users can't install various applications over a Linux machine. If we want to install any application on the Linux machine we need to have the privileges of a superuser. We will instead run the sudo dpkg -i software.deb command so that we can execute the installation successfully. Installing the sudo commandThe package of sudo command is pre-installed over most of the Linux distributions. To confirm that the package is installed on our system, the below steps must be followed:
Install Sudo on Fedora and CentOSInstall Sudo on Debian and Ubuntu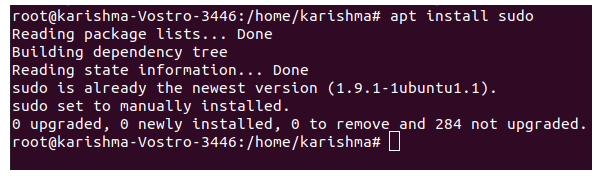
Command for Updating sudo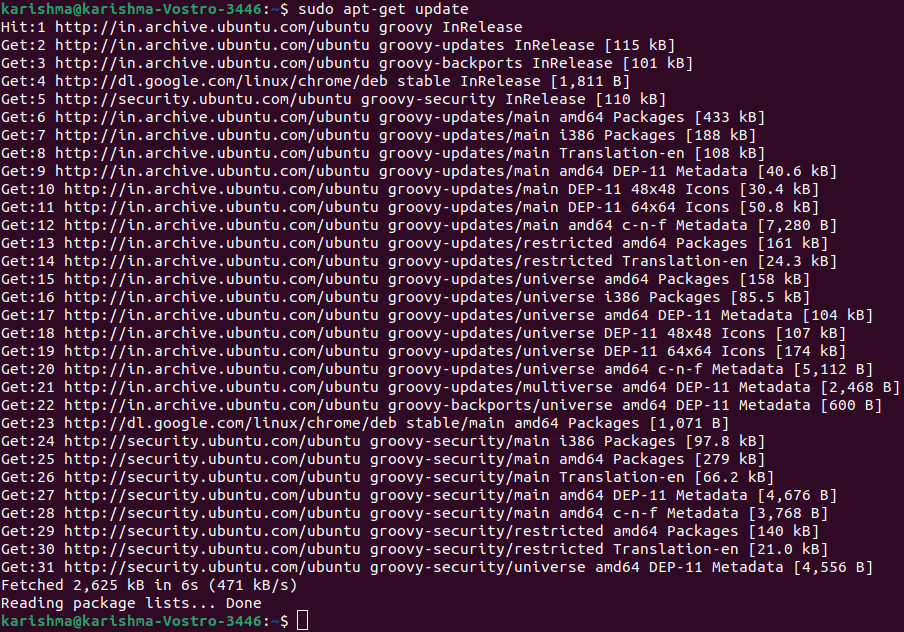
Next TopicBasic Linux Commands
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










