Important Questions on Mobile Computing1) What is Mobile Computing? Or What do you understand by Mobile Computing?Mobile computing is a technology that allows transmission of data, voice and video via a computer or any other wireless-enabled device /mobile device such as a handheld computer, laptop, smartphones, PDA etc. without having to be connected to a fixed physical wire. Mobile Computing is the process of computation on a mobile device. In this technology, a set of distributed computing systems or service providers and servers participate, connect, and synchronize through mobile communication protocols. 2) What are the basic building blocks for Mobile Computing?Mobile Computing requires portable computing devices such as laptops, smartphones, handheld computers etc. along with mobile communication technologies to enable users to access the Internet and mobile data on their home or work computers from around the world. 3) What do you understand by Mobility in Mobile Computing?Mobility is the ability to move freely. In Mobile Computing, users and devices both have to move on different geographical locations and different networks. Mobility is an essential aspect of Mobile computing. 4) What are the two different types of mobility in Mobile Computing?There are two types of mobility used in Mobile Computing: User Mobility: It is used to specify a user who has access to the same or similar telecommunication services at different places. In User Mobility, a user can move between:
Device Portability: It specifies the mobility of the device. There are many mechanisms in the network and inside the device that ensure that communication is still possible while the device is moving. In Device Portability, the device can move between:
5) What are the different types of applications in which Mobile Computing is used?Mobile Computing is used in the following types of applications:
6) What are the main obstacles that occurred in mobile communications?Following is a list of the biggest obstacles that occurred in mobile communications:
7) What is the full form of a SIM card?SIM is an acronym that stands for Subscriber Identity Module. It is a small plastic card that contains some unique information. 8) What information is stored on a SIM card?SIM has an ID number or IMSI, which stands for International Mobile Subscriber Identity. This number is used to identify the phone number to the network. SIM basically specifies our phone number but can also store contact information, telephone numbers, SMS messages, billing information and data usage etc. Along with these features, a SIM card contains the following information:
9) What does a SIM do? Or What is the working of a SIM card in Mobile communication?SIM or SIM card is a computer chip made of plastic that holds information and facilitates connecting to your network. It stores much technical information about network and communication. It facilitates you to make calls, send SMS, and connect to mobile internet services like 3G and 4G. It can store some data such as messages, contacts and emails, etc. You can transfer your contact to SIM in emergency conditions. It is also transferable. 10) What are the different advantages of Mobile Computing?Following is the list of advantages of Mobile Computing: Advantages of Mobile Computing Increased Productivity: Mobile Computing allows users to use mobile devices in various fields and companies. So, it has reduced the time and cost for clients and themselves also that's why productivity is increased. Portability: this is one of the biggest advantages of mobile computing. It allows you to move freely and not restricted to one location to complete your communication or do your jobs. You can even access your mails and do your online assignment while going anywhere. Entertainment: Due to the emerging of mobile devices and smartphones, the entertainment industry is enhanced quickly and bigger than ever. You can use it for entertainment purposes also. Cloud Computing: Mobile Computing provides the service of Cloud computing, which can be used for saving data, documents, audio, video files etc. on an online server and being able to access them anytime and anywhere by having only an internet connection. You can also access these files on several mobile devices or computers simultaneously. 11) What are the main disadvantages of Mobile Computing?Following is the list of main disadvantages of Mobile Computing: Disadvantages of Mobile Computing Quality of Connectivity: The quality of connectivity is one of the biggest disadvantages of Mobile Computing. Mobile devices require either Wi-Fi connectivity or mobile network connectivity such as GPRS, 3G or 4G connectivity. In this case, if you are not near any of these connections, your internet access will be slow, very limited or disconnected sometimes. Security Issues and Threats: Mobile connections are always vulnerable to security issues or threats. Mobile VPNs are not supposed to always be safe, and syncing devices might also lead to security concerns. If you are accessing a Wi-Fi network connection, it can also be risky because hackers may easily hack or bypass WPA and WEP security. Power Consumption and Battery Issues: Mobile devices use detachable and rechargeable batteries as a power source during communication. These batteries do not tend to last long. In emergencies, if you don't have a source of power for charging, then it will undoubtedly be a communication or data transmission failure. 12) What do you understand by guard space in Mobile Computing?The space between the channel interference ranges is known as guard space. Guard spaces are used to avoid frequency band overlapping or adjacent channel overlapping. 13) How is guard spaces arranged between users in CDMA systems?The guard spaces between users in CDMA systems are arranged orthogonally between the spreading codes. The lower the correlation is, the better is the user separation. 14) What do you understand by multiplexing in Mobile computing?FDM: The FDM technique separates signals by modulating the data onto different carrier frequencies. TDM: The TDM technique is used to separate signals by interleaving bits one after the other. 15) What are the three fundamental propagation behaviors depending on their frequency?Following are the three fundamental propagation behaviors depending on their frequency: Ground wave: When the frequency is less than 2 MHz. (<2 MHz) Sky wave: When the frequency is varied between 2-30 MHz. Line of sight: When the frequency is more than 30 MHz. (>30 MHz) 16) What is multipath propagation?/ What do you understand by multipath propagation?When the sender emits the radio waves, these radio waves can travel along a straight line, or they may be reflected at a large building, or scattered at smaller obstacles. Such transmission of data from sender to receiver is called multipath propagation. 17) What are the different basic schemes of analog modulations in mobile computing?The three basic schemes analog modulations in mobile computing are:
18) What are the Phase Lock Loop (PLL) in Mobile computing and its use?The Phase Lock Loop or phase-locked loop (PLL) is a control system that is used to generate an output signal whose phase is related to the input signal's phase. There are several different types of a phase-locked loop. The simplest PLL is an electronic circuit that contains a variable frequency oscillator and a phase detector in a feedback loop. The phase-locked loop is used to synchronize the frequency and phase of the receiver with the transmitter. 19) What is the hopping sequence in Mobile Communication?The hopping sequence is a pattern of channel usage used in Frequency Hopping Spread Spectrum (FHSS). 20) What do you understand by dwell time?The dwell time is the total amount of time spent on a channel with a specific frequency. 21) What are the advantages of a cellular system?The advantages of a cellular system are:
22) What is the difference between borrowing channel allocation (BCA) and fixed channel allocation (FCA)?In borrowing channel allocation (BCA), when the traffic load varies in adjacent cells, the cell with heavy load borrows frequencies from the neighboring cell. This scheme is called borrowing channel allocation or BCA. While in the fixed channel allocation, the frequencies assigned to cell clusters and cells respectively are fixed. This technique is called fixed channel allocation or FCA. 23) What is the responsibility of an authentication center?The responsibility of the Authentication center (AuC) is protecting user identity and data transmission. The AuC uses an algorithm for authentication as well as the keys for encryption. It also generates the values needed for user authentication in the HLR. 24) What do you understand by burst and normal burst?In mobile communication, the data is transmitted in small portions. These small portions are called bursts, and the portions used for data transmission inside a time slot is called normal bursts. 25) What is traffic multiframe and control multiframe?Traffic multiframe: The Traffic Channel frames are organized into multiframes that contain 26 bursts and takes 120 ms. 24 bursts are used in a traffic multiframe. Control multiframe: The combination of 51 TDMA frames which contains data for the other logical channels, is called control multiframe. 26) What do you understand by Mobile IP?Mobile IP or MIP is an IETF (Internet Engineering Task Force) standard communications protocol designed to allow mobile devices' (such as laptops, PDA, mobile phones, etc.) users to move from one network to another while maintaining their permanent IP (Internet Protocol) address. 27) Why Mobile IP is so important?Mobile IP is very important in Mobile communication because it facilitates mobile devices' users to move from one network to another without losing connectivity. 28) What are the different components of the Mobile IP?The Mobile IP has the following main components: Mobile Node: The mobile node is an end-user system or device with inbuilt software to provide network roaming capabilities. Examples of Mobile nodes are smartphones, cell phones, PDA (Personal Digital Assistant), laptop, Tablet etc. Home Agent: The home agents are used to provide several services for the mobile node and are located in the home network. It maintains the location registry and acts as a starting point to send packets towards the mobile nodes. Foreign Agent: The foreign agent acts as a default router for the mobile nodes. It provides several services to the mobile node during its visit to the foreign network. Care-of Address (COA): It defines the mobile node's current location from an IP point of view. The packet delivery toward the mobile node is done using a tunnel, and the COA denotes the endpoint of the tunnel. In other words, you can say that it specifies the address where packets exit the tunnel. Correspondent Node (CN): The correspondent node acts as a communication partner for the mobile node. It can be a fixed or mobile node. Home Network: The home network is the subset of the mobile node. No mobile IP support is needed within this network. Foreign network: A foreign network specifies a network in which a mobile node operates when away from its home network. 29) What is GSM in Mobile Computing?GSM is an acronym that stands for Global System for Mobile Communications (GSM). It is a standard developed by the European Telecommunications Standards Institute (ETSI) to describe the protocols for second-generation (2G) digital cellular networks used by mobile devices. 30) In which year and country GSM was first deployed?The GSM technology was first deployed in Finland in December 1991. By the mid-2010s, it became a global standard for mobile communications and covered over 90% market share. Now, it is operated in over 193 countries and territories. 31) Explain the GSM System Protocol Architecture.The GSM System protocol architecture can be defined as a layered model that allows communications between two different systems. The lower layers provide the services to the upper-layer protocols. Each layer passes suitable notifications to ensure the transmitted data has been formatted, transmitted, and received accurately. See the following diagram of the GSM System protocol architecture: 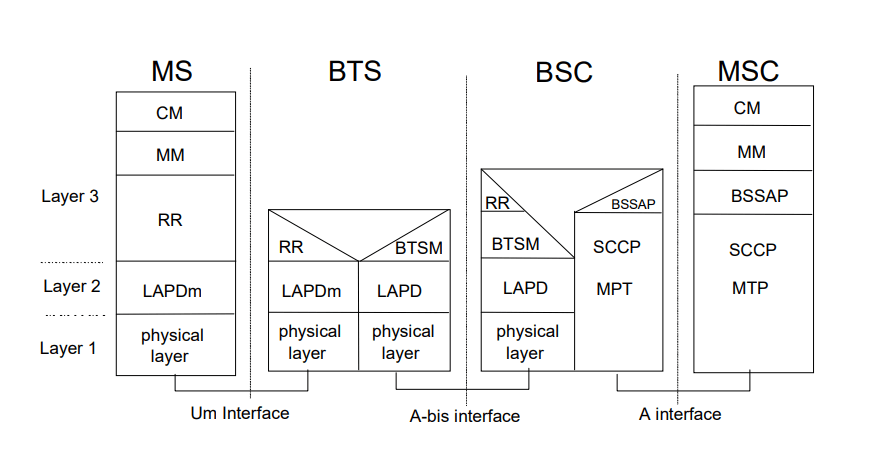
The GSM System protocol architecture consists of the following protocols: MS Protocols According to the architecture, the MS protocol is assembled into three general layers:
32) What do you understand by TCP?In Mobile computing, TCP stands for Transmission Control Protocol. It is a connection-oriented communication protocol that facilitates to exchange of messages between computing devices in a network. TCP is the most common protocol in networks. It uses the Internet Protocol (IP) to make the communication possible. That's why, together they are referred to as TCP/IP. 33) Explain the working of TCP in Mobile Computing.The working of TCP can be defined in the following steps:
34) What do you understand by OVSF?OVSF is an acronym that stands for Orthogonal Variable Spreading Factor. It is used to separate the different data streams of a sender in UMTS by using orthogonal codes. 35) What is polling in Mobile Communication?In Mobile communication, "polling" is a process of continuous checking of other programs or devices by one program or device to check their state. It usually sees whether they are still connected or want to communicate. In polling, there is one master station and several slave stations. 36) What do you understand by BSSGP in Mobile computing?BSSGP stands for Base Station Subsystem GPRS Protocol. It is used to convey routing and QoS-related information between the BSS and SGSN. BSSGP does not perform error correction and works on top of a frame relay (FR) network. 37) What do you understand by WLAN?WLAN is an acronym that stands for Wireless Local Area Network. It is a wireless distribution method for two or more devices that use high-frequency radio waves and often include an access point to the Internet. WLAN is the core concept of mobile communication. It facilitates users to move freely within the coverage area, such as a home or a small office while maintaining a network connection. Sometimes, WLAN is also called a local area wireless network (LAWN). 38) What are the advantages and disadvantages of WLAN?Following are the advantages and disadvantages of WLAN: Advantages of WLAN The wireless approach provides Flexibility: The most significant advantage of a WLAN is that it provides a facility that devices can be connected wirelessly. It doesn't require cables, so it provides flexibility because even small devices such as smartphones and tablets can be connected to the network without any wire. Reduce Cost: WLANs were very expensive in the early 1990s and were only used when wired connections were strategically impossible. But nowadays, the use of WLAN reduces the cost of the setup because it is cheap and allows homes and businesses to create local networks without wiring the building with Ethernet. The cost of cable and the wiring cost can be cut easily by using WLAN. If you want to extend the connection area, you can easily upgrade WLAN by replacing routers with new versions of devices with higher capacity. It is a more comfortable and cheaper solution than upgrading old Ethernet cables. Support Unlimited Devices: WLANs are not limited by the number of physical ports on the router so, you can connect dozens or even hundreds of devices. You can easily extend the range of a WLAN by adding one or more repeaters. Robustness: It is robust because there is no chance of connection failure due to loose wire. Disadvantages of WLAN Security: Wireless networks (WLAN) are naturally less secure than wired networks. It is very important to limit access to the network if security is a concern because any wireless device can attempt to connect to a WLAN. You can use wireless authentication such as WEP or WPA, which encrypts communication. Susceptible to Interference: WLAN is more susceptible to interference from other signals or physical barriers, such as concrete walls. That's why WLANs are not preferred over LANs. LANs offer the highest performance and security and are still used for many corporate and government networks. Quality of Service: The quality of service in WLAN is more inferior than LAN. Low Speed: WLAN doesn't provide as higher speed as LAN can provide. 39) What is the difference between infrastructure and ad-hoc networks?The Difference between Infrastructure and Ad-hoc Networks:
40) What are the main features of infrared transmission?Infrared transmission is used in the region of the electromagnetic radiation spectrum. Its wavelength is longer than the wavelength of visible light but shorter than the wavelength of radio waves. The Infrared frequencies are higher than the frequencies of microwaves but lower than the frequencies of visible light. 41) Where is infrared transmission used?The Infrared data transmission is generally used to connect laptops, smartphones, Personal Digital Assistants (PDAs) to peripheral devices such as printers or desktop computers for synchronizing work files. 42) In which applications the infrared waves are used in Mobile communication?The infrared waves are used in the following applications of mobile communication:
|
You may also like:
- Java Interview Questions
- SQL Interview Questions
- Python Interview Questions
- JavaScript Interview Questions
- Angular Interview Questions
- Selenium Interview Questions
- Spring Boot Interview Questions
- HR Interview Questions
- C Programming Interview Questions
- C++ Interview Questions
- Data Structure Interview Questions
- DBMS Interview Questions
- HTML Interview Questions
- IAS Interview Questions
- Manual Testing Interview Questions
- OOPs Interview Questions
- .Net Interview Questions
- C# Interview Questions
- ReactJS Interview Questions
- Networking Interview Questions
- PHP Interview Questions
- CSS Interview Questions
- Node.js Interview Questions
- Spring Interview Questions
- Hibernate Interview Questions
- AWS Interview Questions
- Accounting Interview Questions







