Multitenancy in Cloud computingMultitenancy is a type of software architecture where a single software instance can serve multiple distinct user groups. It means that multiple customers of cloud vendors are using the same computing resources. As they are sharing the same computing resources but the data of each Cloud customer is kept separate and secure. It is a very important concept of Cloud Computing. Multitenancy is also a shared host where the same resources are divided among different customers in cloud computing. 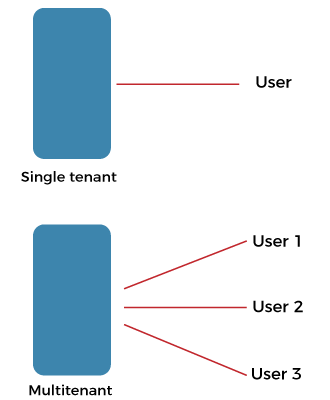
For Example :The example of multitenancy is the same as working of Bank. Multiple people can store money in the same Bank. But every customer asset is different. One customer cannot access the other customer's money and account, and different customers are not aware of each other's account balance and details, etc. Advantages of Multitenancy :
Disadvantages of Multitenancy :
Each tenant's data is not accessible to all other tenants within the cloud infrastructure and can only be accessed with the permission of the cloud provider. In a private cloud, customers, or tenants, can be different individuals or groups within the same company. In a public cloud, completely different organizations can securely share their server space. Most public cloud providers use a multi-tenancy model, which allows them to run servers with single instances, which is less expensive and helps streamline updates. 
Multitenant Cloud vs. Single-Tenant CloudIn a single-tenant cloud, only one client is hosted on the server and provided access to it. Due to the multi-tenancy architecture hosting multiple clients on the same server, it is important to understand the security and performance of the provider fully. Single-tenant clouds give customers greater control over managing data, storage, security, and performance. 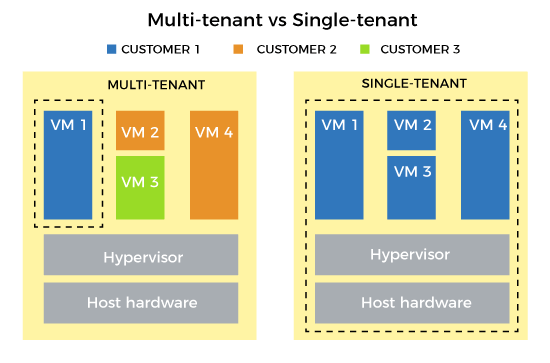
Benefits of multitenant architectureThere is a whole range of advantages to multitenancy, which are evident in the popularity of cloud computing. Multitenancy can save money. Computing is cheap to scale, and multi-tenancy allows resources to be allocated coherently and efficiently, ultimately saving on operating costs. For an individual user, paying for access to a cloud service or SaaS application is often more cost-effective than running single-tenant hardware and software. Enables multi-tenancy flexibility. If you have invested in your hardware and software, it can reach capacity during times of high demand or go idle during slow demand. On the other hand, a multitenant cloud can allocate a pool of resources to the users who need it as their needs go up and down. As a public cloud provider customer, you can access additional capacity when needed and not pay for it when you don't. Multi-tenancy can be more efficient. Multitenancy reduces the need for individual users to manage the infrastructure and handle updates and maintenance. Individual tenants can rely on a central cloud provider rather than their teams to handle those routine chores. Example Of Multi-TenancyMultitenant clouds can be compared to the structure of an apartment building. Each resident has access to their apartments within the entire building agreement, and only authorized persons may enter specific units. However, the entire building shares resources such as water, electricity, and common areas. It is similar to a multitenant cloud in that the provider sets broad quotas, rules, and performance expectations for customers, but each customer has private access to their information. Multitenancy can describe a hardware or software architecture in which multiple systems, applications, or data from different enterprises are hosted on the same physical hardware. It differs from single-tenancy, in which a server runs a single instance of the operating system and application. In the cloud world, a multitenant cloud architecture enables customers ("tenants") to share computing resources in a public or private cloud. Multitenancy is a common feature of purpose-built, cloud-delivered services, as it allows customers to efficiently share resources while safely scaling up to meet increasing demand. Even though they share resources, cloud customers are unaware of each other, and their data is kept separate. What does multitenant mean for the cloud?Cloud providers offer multi-tenancy as a means of sharing the use of computing resources. However, this shared use of resources should not be confused with virtualization, a closely related concept. In a multitenant environment, multiple clients share the same application, in the same operating environment, on the same hardware, with the same storage system. In virtualization, unlike multitenancy, each application runs on a separate virtual machine with its operating system. Each resident has authorized access to their apartment, yet all residents share water, electricity, and common areas. Similarly, in a multitenant cloud, the provider sets broad terms and performance expectations, but individual customers have private access to their information. The multitenant design of a cloud service can dramatically impact the delivery of applications and services. It enables unprecedented reliability, availability, and scalability while enabling cost savings, flexibility, and security for IT organizations. Multi-tenancy, Security, and ZscalerThe primary advantage of multitenant architectures is that organizations can easily onboard users. There's no difference between onboarding 10,000 users from one company or 10 users from a thousand companies with a multitenant cloud. This type of platform easily scales to handle increasing demand, whereas other architectures easily. From a security perspective, a multitenant architecture enables policies to be implemented globally across the cloud. That's why Zscaler users can walk around anywhere, knowing that their traffic will be routed to the nearest Zscaler data center-one in 150 worldwide-and their policies will follow. Because of this capability, an organization with a thousand users can now have the same security protections as a much larger organization with tens or hundreds of thousands of employees. Cloud-native SASE architectures will almost always be multitenant, with multiple customers sharing the underlying data plane. The future of network security is in the cloud.Corporate networks now move beyond the traditional "security perimeter" to the Internet. The only way to provide adequate security to users - regardless of where they connect - is by moving security and access control to the cloud. Zscaler leverages multi-tenancy to scale to increasing demands and spikes in traffic without impacting performance. Scalability lets us easily scan every byte of data coming and going over all ports and protocols - including SSL - without negatively impacting the user experience. Another advantage of multitenancy is that we can immediately protect all our customers from this threat as soon as a threat is detected on the Zscaler Cloud. Zscaler Cloud is always updated with the latest security updates to protect customers from rapidly evolving malware. With thousands of new phishing sites coming in every day, the equipment is not working. And Zscaler reduces costs and eliminates the complexity of patching, updating, and maintaining hardware and software. The multitenant environment in LinuxAnyone setting up a multitenant environment will be faced with the option of isolating environments using virtual machines (VMs) or containers. With VMs, a hypervisor spins up guest machines, each of which has its operating system and applications and dependencies. The hypervisor also ensures that users are isolated from each other. Compared to VMs, containers offer a more lightweight, flexible, and easy-to-scale model. Containers simplify multi-tenancy deployment by deploying multiple applications on a single host, using the kernel and container runtime to spin up each container. Unlike VMs, which contain their kernel, applications running in containers share a kernel, even across multiple tenants. In Linux, namespaces make it possible for multiple containers to use the same resource without conflict simultaneously. Securing a container is the same as securing any running process. When using Kubernetes for container orchestration, it is possible to set up a multitenant environment using a single Kubernetes cluster. It is possible to segregate tenants into their namespaces and create policies that enforce tenant segregation. Multitenant DatabaseWhen choosing a database for multitenant applications, developers have to balance customer needs or desire for data isolation and quick and economical solutions in response to growth or spikes in application traffic. To ensure complete isolation, the developer can allocate a separate database instance for each tenant; On the other hand, to ensure maximum scalability, the developer can make all tenants share the same database instance. But, most developers opt to use a data store such as PostgreSQL, which enables each tenant to have their schema within a single database instance (sometimes called 'soft isolation') and have the best of both worlds. Provides. What about "hybrid" security solutions?Organizations are increasingly using cloud-based apps, such as Salesforce, Box, and Office 365 when migrating to infrastructure services such as Microsoft Azure and Amazon Web Services (AWS). Therefore, many businesses realize that it makes more sense to secure the traffic in the cloud. In response, older vendors that relied heavily on periodic hardware equipment sales promoted so-called "hybrid solutions". In that data, center security controlled by devices and mobile or branch security is similar to those housed in a cloud environment. The stack handles security. This hybrid strategy complicates, rather than simplifies, enterprise security in that cloud users and administrators get none of the benefits of a real cloud service-speed, scale, global visibility, and threat intelligence-that is only a multitenant one. It can be provided through global architecture.
Next TopicGrid Computing
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










