Nuubi Tool in Kali LinuxThe data generated or collected during the Reconnaissance phase acts as a benchmark for other phases such as Scanning, Exploitation, etc. As a result, keeping important and sensitive data is always a difficult task for penetration testers. One tool used for penetration testing is NUUBI. NUUBI is a Python-based tool that conducts a large amount of recon. Nuubi Gathers Information Like:The following is the list of information that nubbi can generate:
Gathering this information can make exploitation easier and give the penetration tester a better framework for performing security research. Installation of Nuubi Tool in Kali LinuxStep 1: In order to install Nuubi, first, we have to open our Kali Linux terminal and then move to the Desktop with the help of the command below: 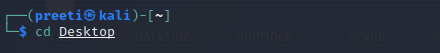
Step 2: Now that we are on the Dektop, use the following command to create a new directory called NUUBI. The installation of the NUUBI tool will be completed in this directory. 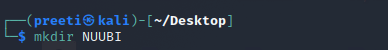
Step 3: Next, with the help of the following command, we have to switch to NUUBI 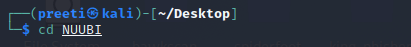
Step 4: Next, we have to install the tool. The tool must be cloned from Github. 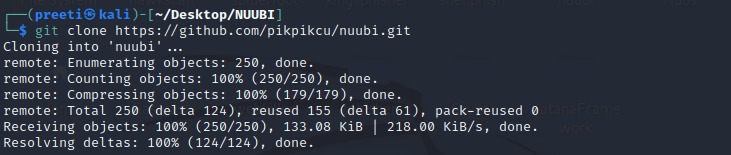
Step 5: The tool has been successfully downloaded to the NUUBI directory. Using the following command, list the content of the tool. 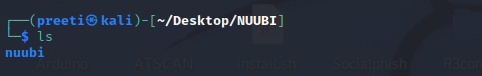
Step 6: We can see that a new directory for the nubbi tools was created while we were installing it. Now use the following command to get to that directory. 
Step 7: Use the command below to discover the contents of the tool once more. 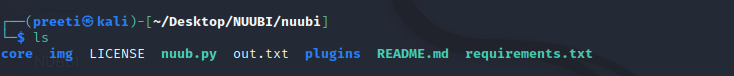
Step 8: Next, we have to download the required packages for running the tool. For this, we need to use the command below. 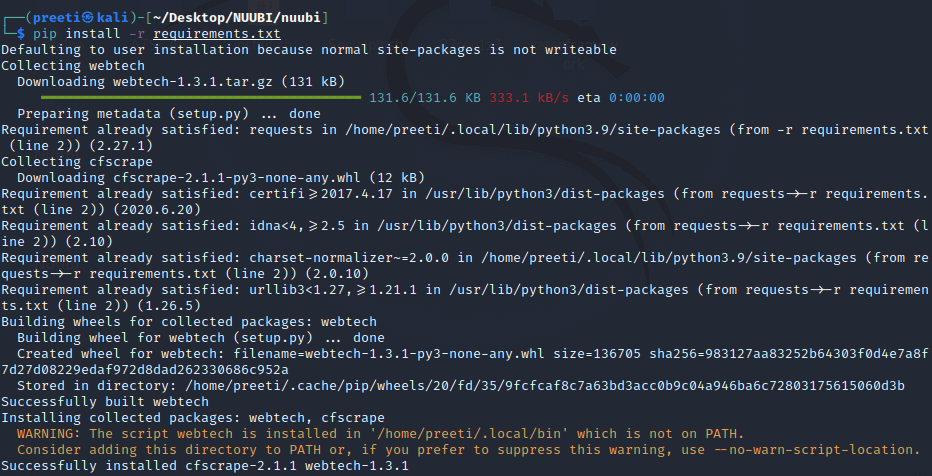
Step 9: Now that we've completed our installation, use the command below to view the help (which provides a better knowledge of the tool). 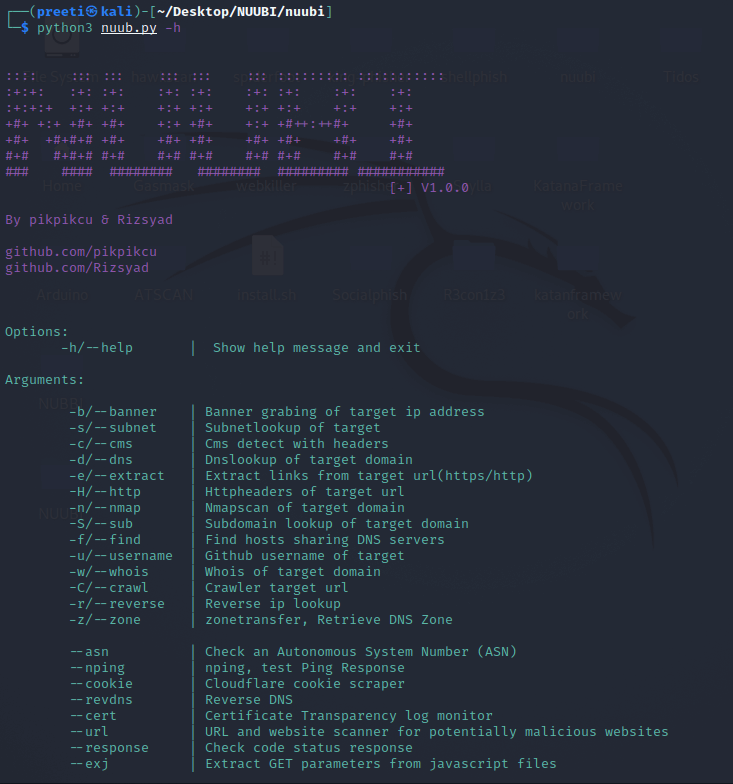
Example 1: Subnet Lookup of Target In this example, we'll collect information on the javatpoint.com subnet lookup. Subnet lookup yielded the following results: Address, Netmask, Network Range, Broadcast, etc. 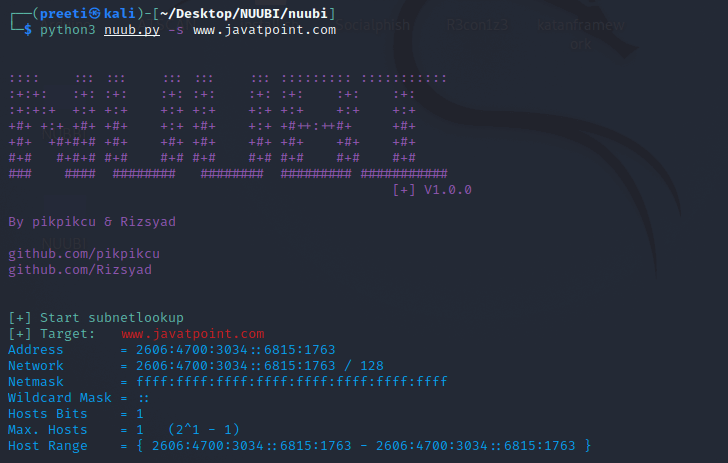
Example 2: Subdomain Lookup of the target domain In this case, we're gathering the target's subdomain. The -S tag, followed by the target URL (javatpoint.com) for this collection. 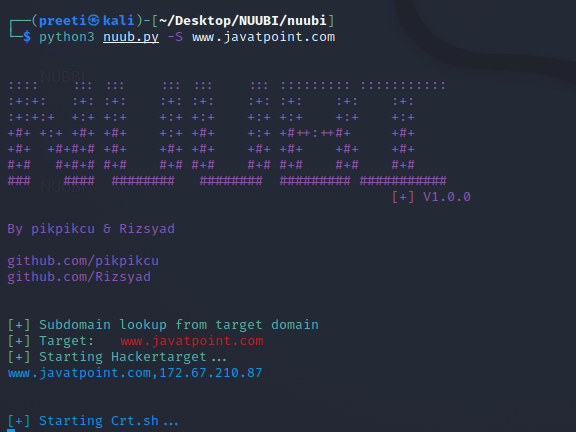
Example 3: HTTP Headers of target URL We'll be intercepting the HTTP Headers for our target in this example. We have a status code, a Server, a Location, and a Connection. 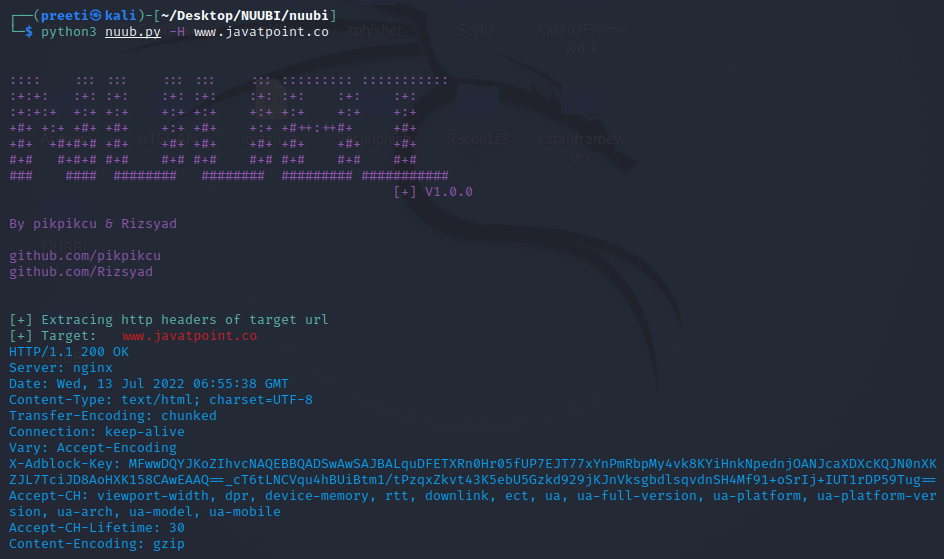
Example 4: Reverse DNS from the target IP address In this example, we'll use Reverse DNS to resolve an IP address. As we can see, we submitted our target's IP address and obtained the DNS Name for the related IP address. 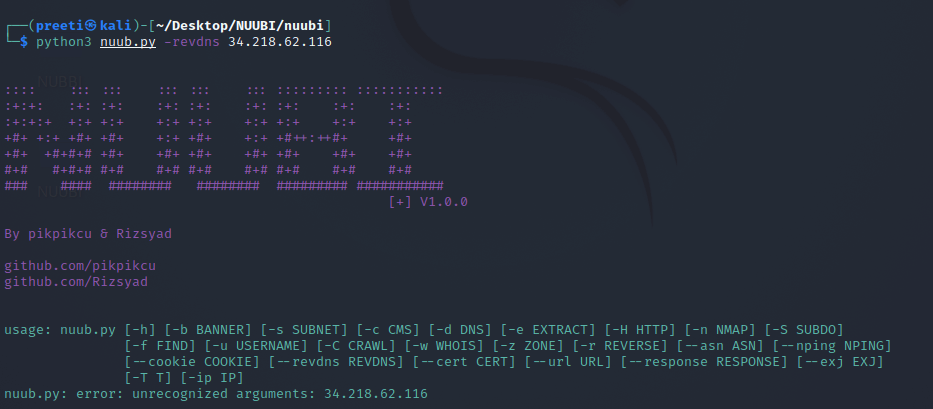
Example 5: CMS Detection of Target We'll be gathering CMS (Content Management System) information in this example. In the Results, we have got the server details and more information. 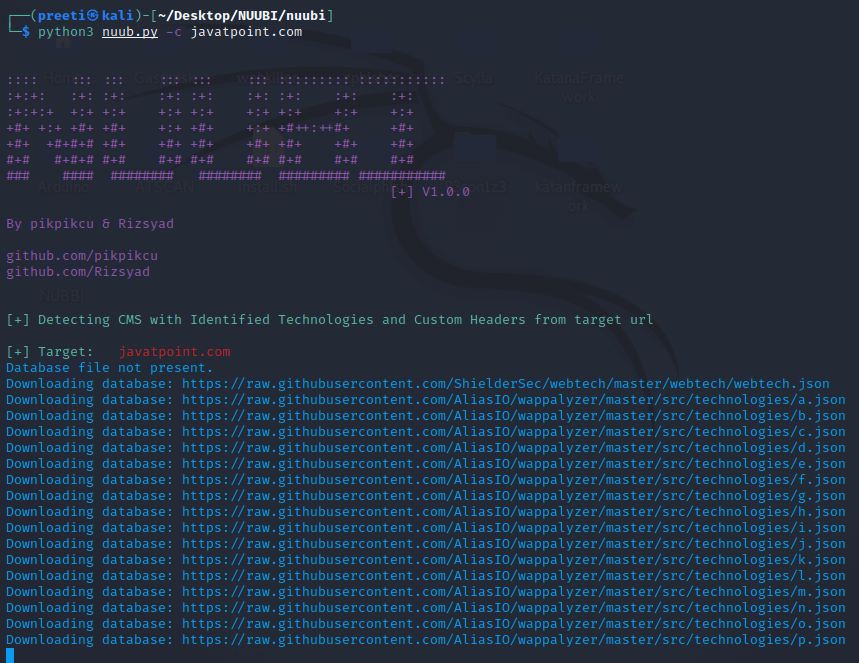
Example 6: Find hosts sharing DNS servers In this case, we will gather the host which is sharing the same DNS Server as javatpoint.com. As we can see, we have No DNS Server Record as a consequence, which suggests that javatpoint.com does not share its DNS Server with other hosts. 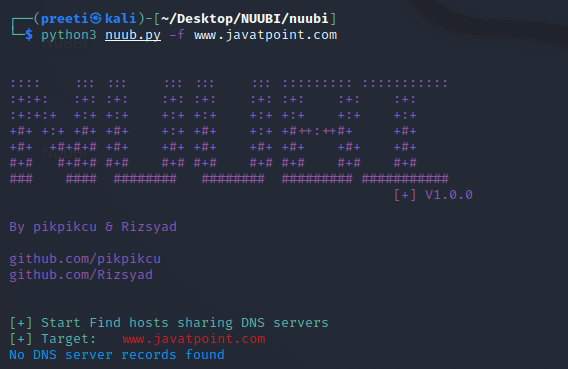
Example 7: Crawler target URL In this example, we'll crawl the target's metadata, which may contain important information. 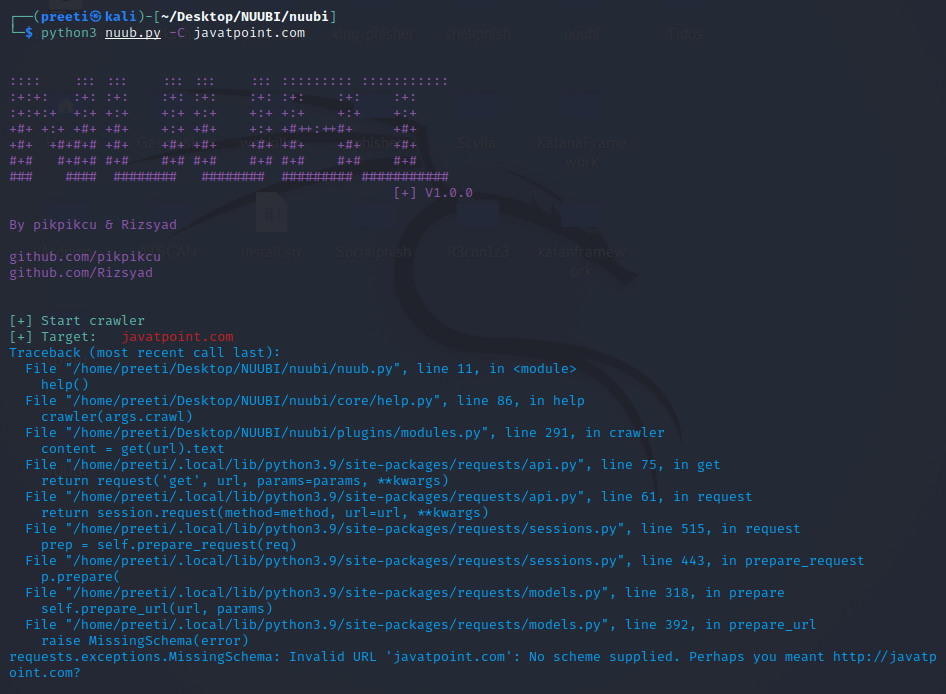
We've crawled some significant URLs from javatpoint.com in the screenshot below. Example 8: Certificate Transparency log Monitor In this gathering, we will be gathering Certificate Transparency logs from our target domain in this case. 
Next Topic#
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










