Phishing Tools for Kali LinuxPhishing is one of the best examples of an online scam; on a daily basis, everyone uses the internet for things like social media, email, online shopping, and banking transactions, all of which need the use of our login information or personal data. Phishing is when a website or application seems to be a trusted source, but it is not. It appears to be an original website or application, but it is not, and the fake one steals our data for improper use. In this article, we will discuss some phishing tools for Kali Linux. Here is the list of phishing tools in Kali Linux:
1. Socialphish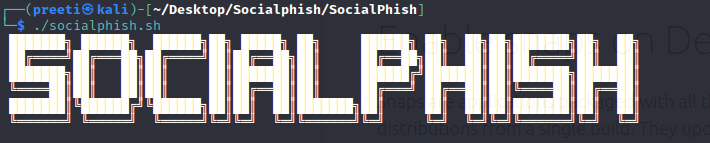
Socialphish is an open-source phishing tool with a lot of features. Socialphish which is used to conduct phishing attacks on targets, is growing increasingly popular. Socialphish is easier to use than Social Engineering Toolkit. Socialphish includes various templates created by another tool called Socialphish. Socailphish provides phishing templates for 33 famous websites, including Google, Facebook, Github, Yahoo, Snapchat, Spotify, Linkedin, origin Steam, Microsoft, Yahoo, Github, etc. Socialphish also allows users to utilize a custom template. This tool makes phishing attacks simple to carry out. They can use a lot of creativity to make the email appear as real as possible. Features of SocialphishThe following are the features of Socialphish:
Installation of SocialphishThe following steps are used to install Socialphish: Step 1: In order to install the Socialphish tool, first, we have to open our Kali Linux terminal and move to the Desktop. Here we need to create a directory named Socialphish. We will install the tool inside this directory. 
Step 2: We are now on the desktop. Here we need to create the directory named Socialphish. Use the following command to create the Socialphish directory. 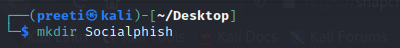
Step 3: The directory has been created. Now we have to use the following command in order to move into that directory. 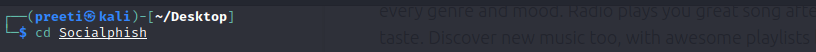
Step 4: Now, we are inside the Socialphish directory. We must download the tool to this directory, which implies we must clone the tool from GitHub. To clone the tool from GitHub, run the command below: 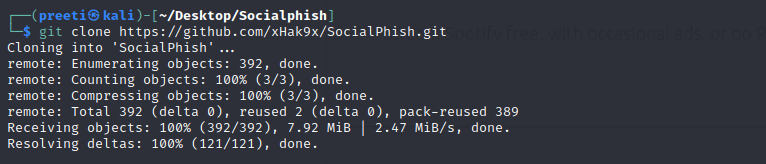
Step 5: The tool has been downloaded in the directory Socialphish. Use the following command to list the contents of the tool that has been downloaded. 
Step 6: When we list out the tool's content, we notice that it has created a new directory called SocialPhish. In order to see the contents of the tool, we need to move to this directory to view the tool's content. Use the following command to move to this directory. Step 7: Next, use the following command in order to list out the content of this directory. Step 8: Now, with the help of the following command, we need to give permission to the tool. Step 9: We may now use the following command to run the tool. This command will open the tool's help menu. 
The tool is running properly. Now we must provide the option number to the tool for which we need to create the phishing page. If we wish to make a phishing page for Instagram, we should go with option 1. Option 2 will take us to a Facebook phishing page. Similarly, we can select any of the tool's 33 websites. 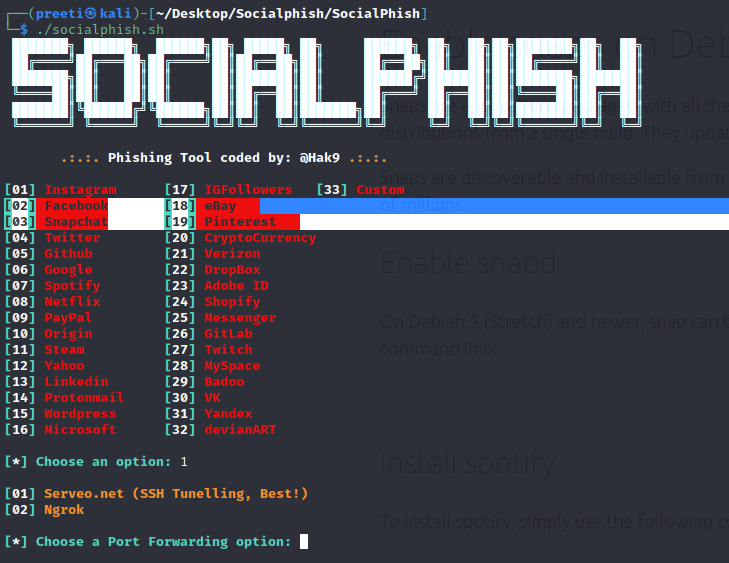
2. ShellPhish
ShellPhish is a tool that we can use to create phishing pages for the most prominent social networking sites, such as Facebook, Twitter, and Instagram. The application includes phishing templates for 18 well-known websites, the bulk of which are social media and email providers. This tool makes it simple to carry out a phishing attack. We can execute phishing in this tool (wide area network). We can use this tool to get ID and password credentials. Installation of ShellPhishThe following steps are used to install Shell Phish: Step 1: To install ShellPhish, we have to first open our Kali Linux terminal and then move to the Desktop. 
Step 2: Next, we have to create a new Directory called shellphish. 
Step 3: Using the following command on the terminal, we can download and install shellphish in the above directory. 
Step 4: Finally, type the following commands to execute the shellphish tool. 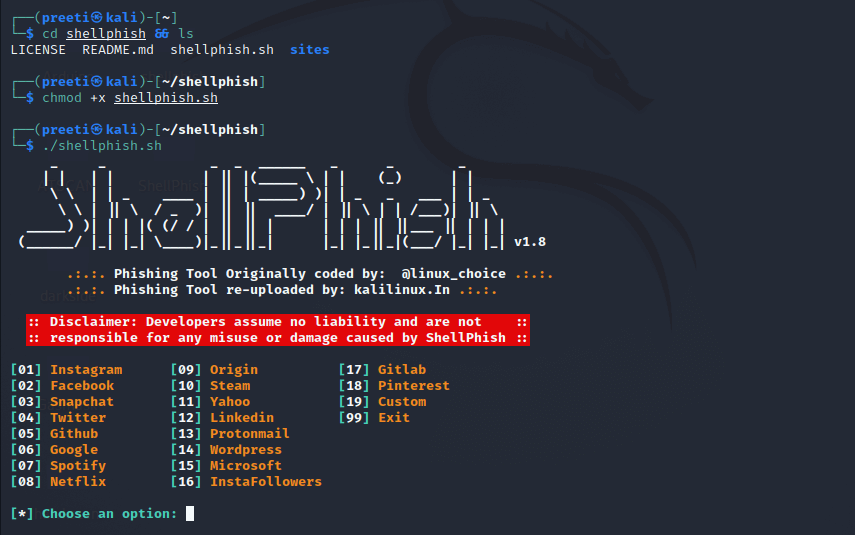
Now, we can see in the above screenshot that the tool is running successfully. This is how we can install ShellPhish tool on Kali Linux. 3. Zphisher
Zphisher is an open-source phishing tool with a lot of features. It has become increasingly popular in recent years for phishing attacks on Target. Zphisher is less difficult to use than the Social Engineering Toolkit. It includes various templates generated by a tool called Zphisher. It provides a phishing templates webpage for 18 well-known websites like Google, Snapchat, Facebook, Yahoo, Instagram, LinkedIn, Microsoft, Origin, GitHub, Microsoft, etc. it also offers the option of using a custom template if desired. This tool makes it simple to carry out a phishing attack. With the help of this tool, we can perform phishing in (a wide area network). We can also use this tool to retrieve credentials like id, passwords. Features of ZphisherThe following are the features of Zphisher:
Installation of ZphisherThe following steps are used to install Zphisher: Step 1: In order to install this tool, first we have to move to the desktop and then, install the tool with the help of the following commands. 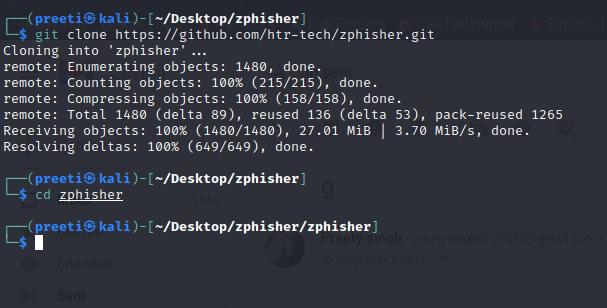
Step 2: Now, we are in the zphisher directory; use the below command to run the tool. 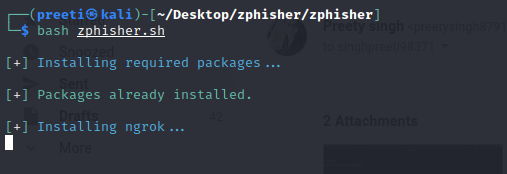
Step 3: The tool has been successfully run. Now we need to select the options from the tool used to create the phishing page. 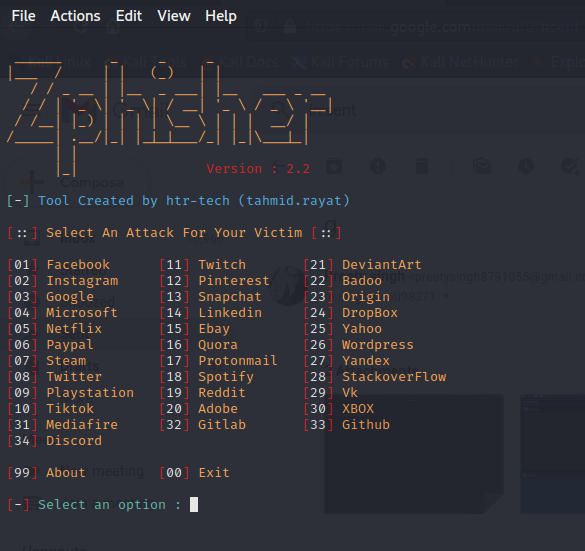
Step 4: We can select the option for which we need to create a phishing page from these options. Option 2 is appropriate if we want to create a phishing page for Instagram. 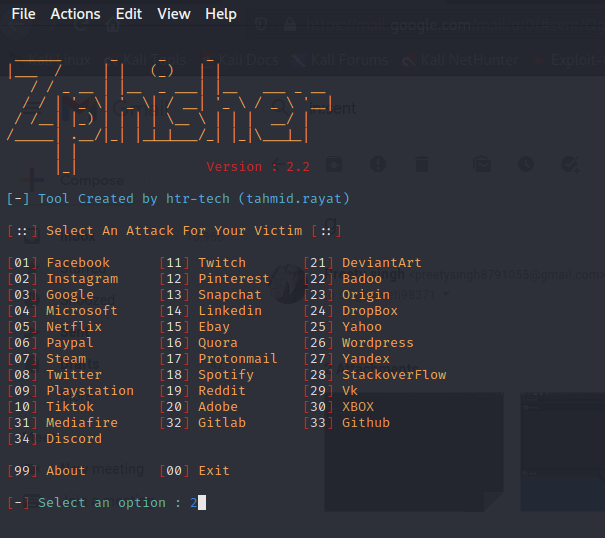
Step 5: As we can see, there are four alternatives for attracting the victim. We can select any option from the list, if we want to go with the first option, type 1. 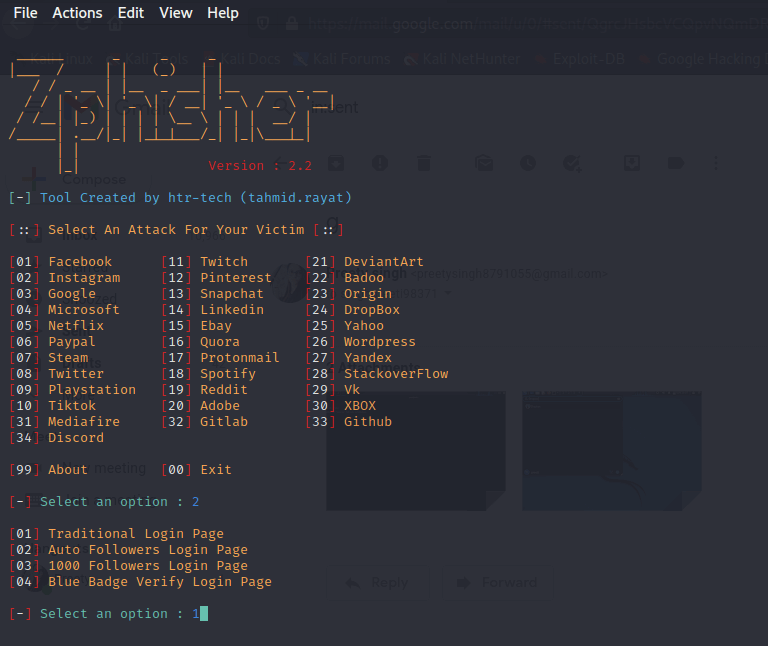
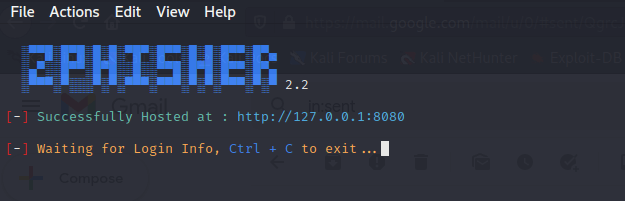
4. BlackeyeBlackeye is a powerful open-source phishing tool. Blackeye is becoming more famous these days that are used to carry out phishing attacks on the target. Blackeye is a handy social engineering toolkit. Blackeye is a collection of templates created by another tool called Blackeye. This tool makes it simple to perform phishing attacks. They can use a lot of creativity to make the email as legit as possible. Blackeye provides phishing templates for 33 famous websites, including Google, Instagram, Facebook, Netflix, Protonmail, Spotify, WordPress, Steam, Origin, Microsoft, and GitHub. Blackeye also allows users to utilize a custom template if desired. How to Install BlackeyeThe following steps are used to install Blackeye: Step 1: In order to install Blackeye, first, we have to open our Kali Linux operating system and then install the tool with the help of the following command. 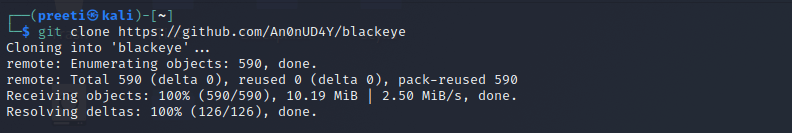
Step 2: Now, we have to use the command below in order to move into the tool's directory. 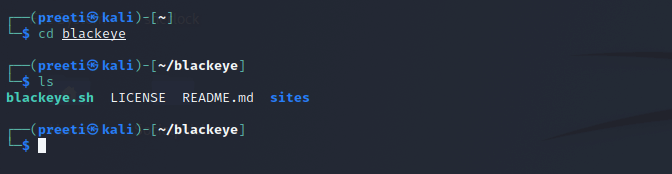
Step 3: Next, we will use the following command to run the tool. 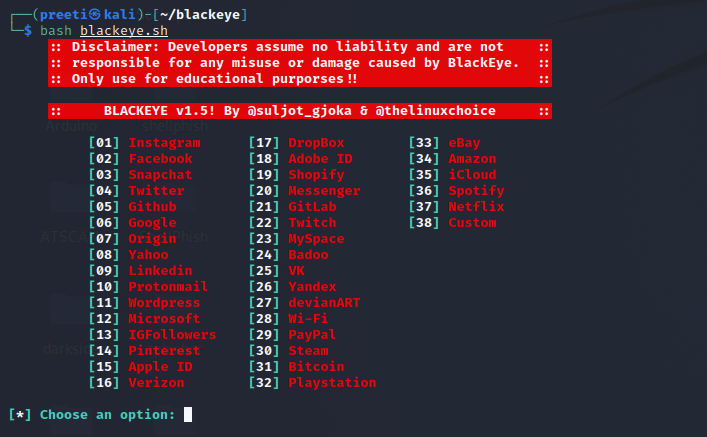
After the tool has been successfully installed, choose any option from the blackeye menu list to launch a phishing attack on our victims, and blackeye will generate a phishing link for the corresponding website, which we may email to our victims. Choose an option1 if we want to use Instagram. 5. King-PhisherKing Phisher is a tool that simulates real-world phishing attacks in order to test and promote. It is an open-source tool that can simulate real-world phishing attacks. This package includes a tool for testing and promoting user awareness by simulating real-world phishing attack. It is a user-friendly yet extremely flexible architecture that gives us complete control over email and server content. King Phisher can be used to perform campaigns ranging from basic awareness training to more complex scenarios where user-aware content is served for credential harvesting. Features of KingPhisherThe following are the features of King Phisher:
Installation of King-PhisherThe following commands are used to install King-Phisher: 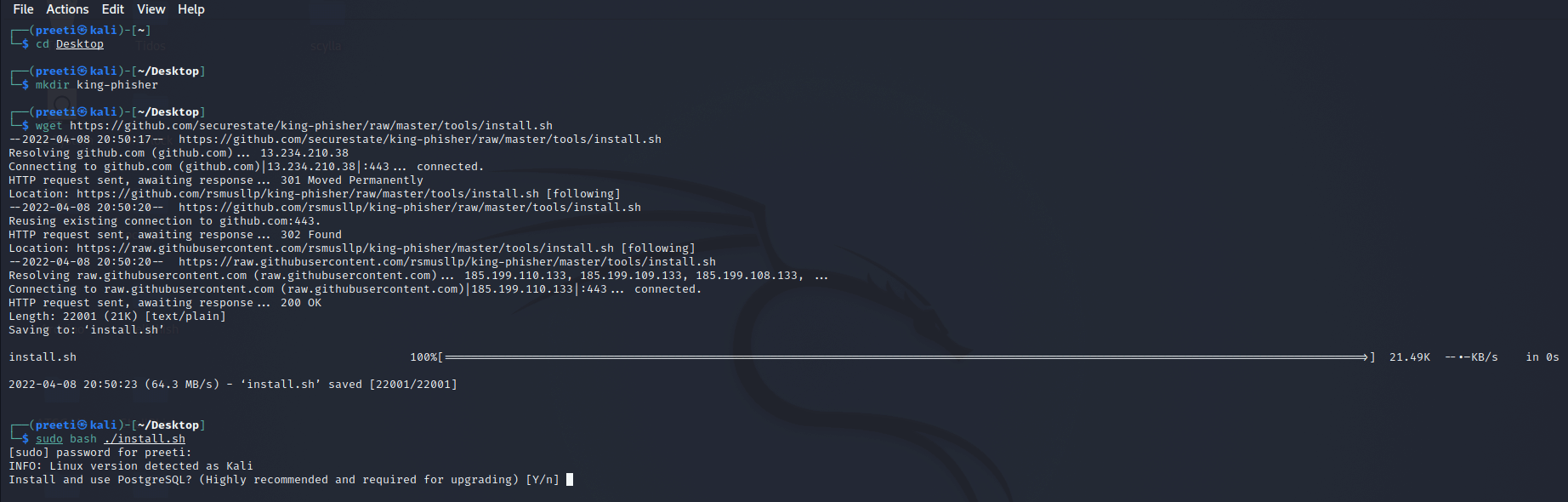
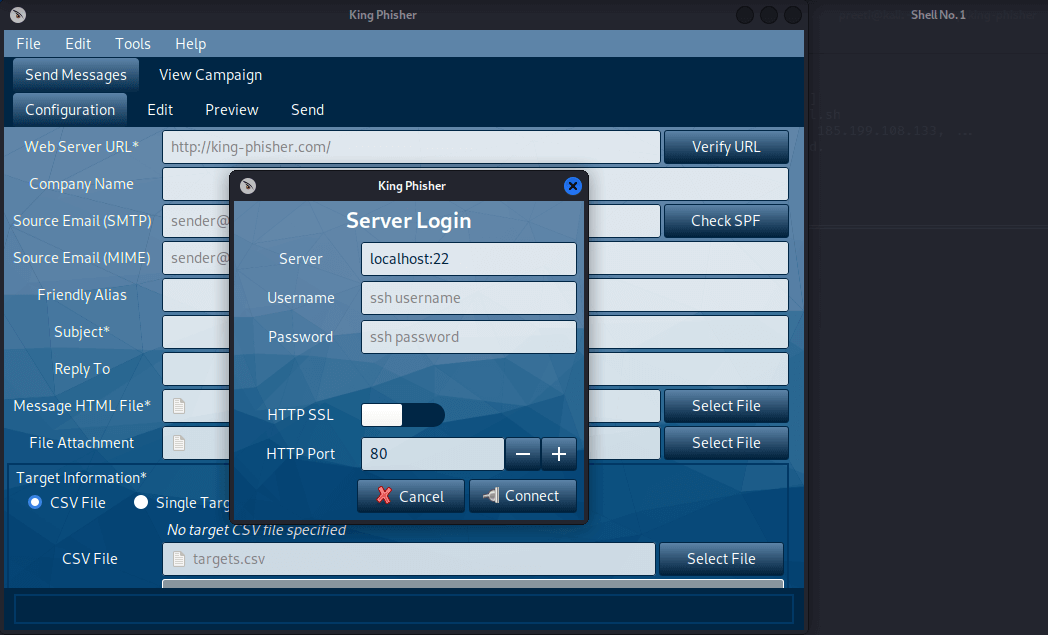
6. Blackphish
Blackphish is an open-source phishing tool with a lot of features. Blackphish, which is used to conduct phishing attacks on Target, is growing increasingly popular. Social Engineering Toolkit is more difficult than Blackphish. Blackphish includes certain templates which are generated by another tool called Blackphish. It provides phishing templates web pages for 5 well-known websites like Instagram, Google, Facebook, Snapchat, etc. When it comes to phishing tools, this tool is really useful. Installation of BlackphishThe following steps are used to install Blackphish: Step 1: In order to install Blackphish, first we have to move to the desktop and then start installing this tool with the help of the following commands: 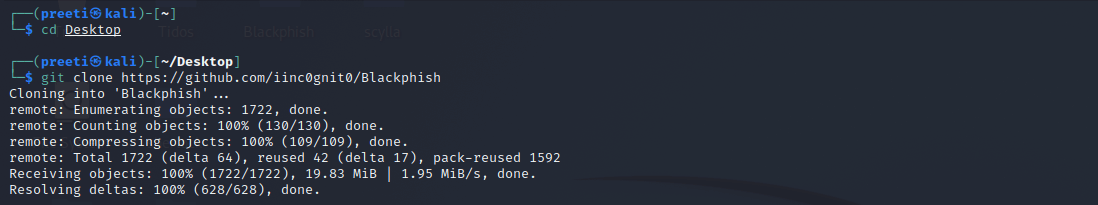
Step 2: Next, we have to move to the tool's directory with the help of the following command. Then install the tool with the help of the following command. 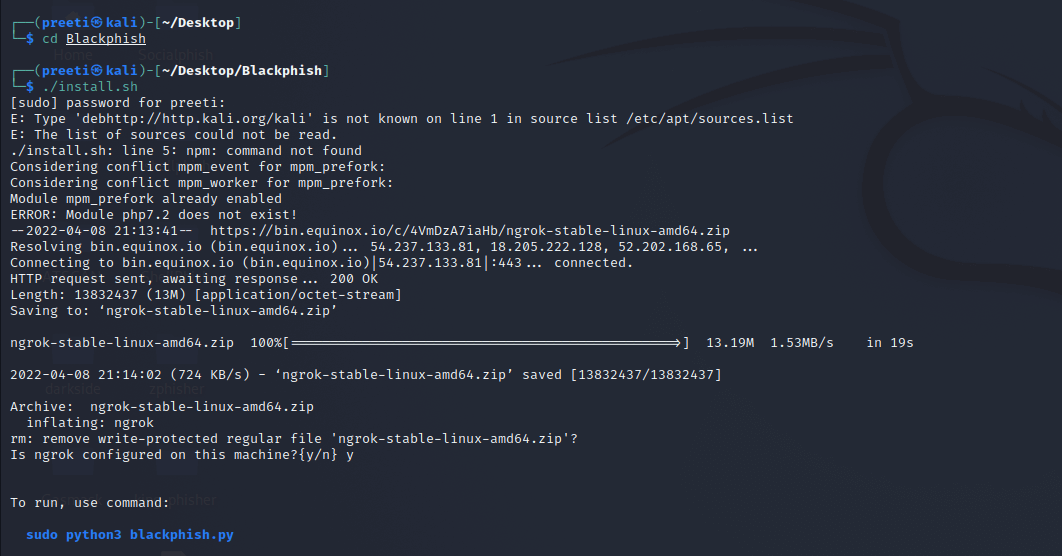
Step 3: The tool has been installed in our system. Use the following command to run the tool. 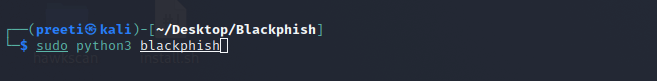
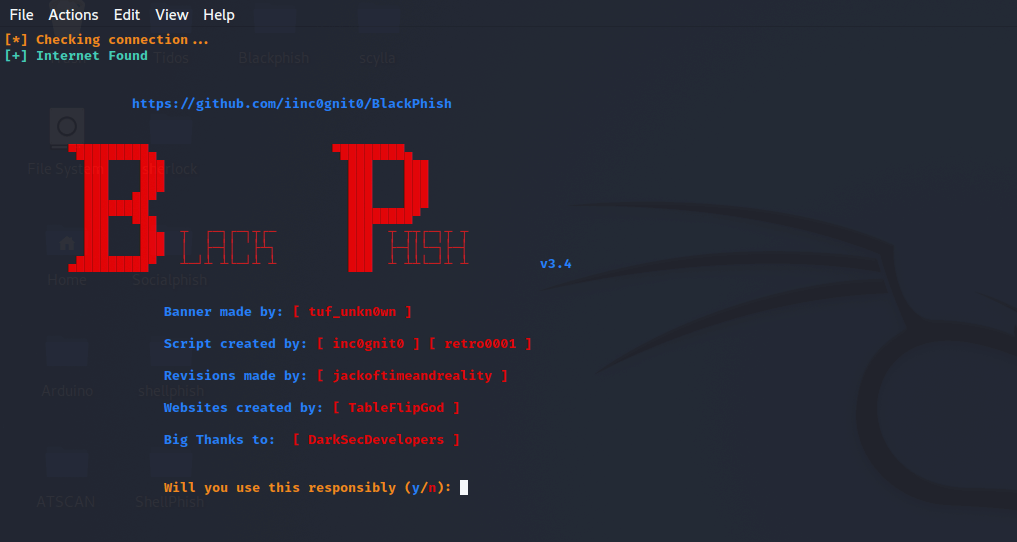
Step 4: We can now see a variety of options here. Suppose we want to create a phishing page for Instagram, type 1 and then 3 for localhost. We can select an option based on our needs. 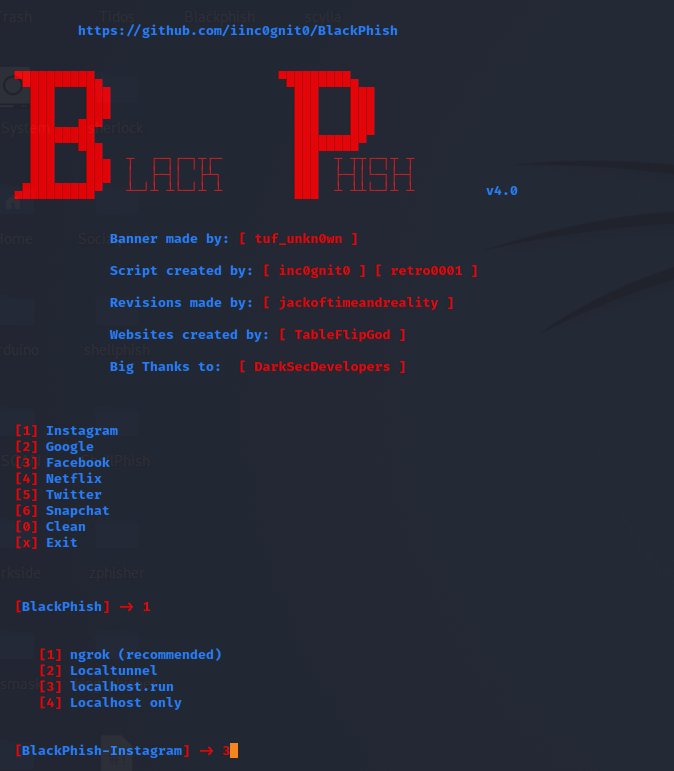
This is how we can easily install the BlackPhish tool on our Kali Linux terminal. 7. Hidden EyeHiddenEye is an advanced phishing tool with features such as keylogging and location tracking. The tool supports most social media, e-commerce, and business pages to be used as an attack vector against online targets. HiddenEye is a Python tool that requires Python3, PHP, and SUDO. This tool is supported by all major Linux distributions and Kali also. Features of Hidden EyeThe following are the features of Hidden Eye:
8. Ghost PhisherGhost Phisher is a wireless network audit and attack software that creates a fake access point and tricks a victim into connecting to it. It can be used to phish credentials and session hijacking. This tool is written in Python Programming Language and the Python Qt GUI library. Features of Ghost PhisherThe following are the features of Ghost Phisher:
Next TopicBest Chromebook for Kali Linux
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










