Difference between public key and private keyIn this article, we are going to discuss public key, private key and the difference between them. Private keys and public keys both terms are commonly used for encryption and decryption. So, it is very important to know about both keys and the difference between them. Public keyIt is an encryption technique that uses a pair of keys (public and private key) for secure data communication. In the pair of keys, the public key is for encrypting the plain text to convert it into ciphertext, and the private key is used for decrypting the ciphertext to read the message. The private key is given to the receiver while the public key is provided to the public. Public Key Cryptography is also known as asymmetric cryptography. 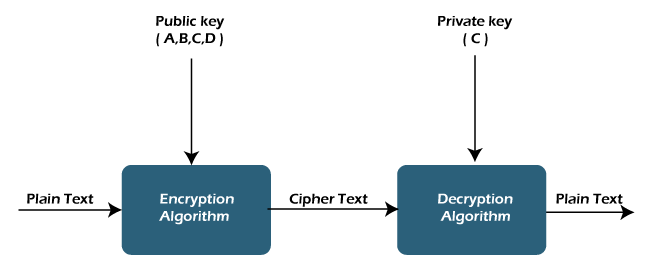
The public key can be shared without compromising the security of the private one. All asymmetric key pairs are unique, so a message encrypted with a public key can only be read by the person who has the corresponding private key. The keys in the pair have much longer than those used in symmetric cryptography. So, it is hard to decipher the private key from its public counterpart. Many of us, heard about RSA, which is the most common algorithm for asymmetric encryption in use today. Public-key encryption is slower than secret-key encryption. In secret key encryption, a single shared key is used to encrypt and decrypt the message, while in public-key encryption, different two keys are used, both related to each other by a complex mathematical process. Therefore, we can say that encryption and decryption take more time in public-key encryption. Applications of public keyThe applications of public key are -
Private KeyIn private key, the same key (or secret key) is used by both the parties, i.e., the sender and receiver, for Encryption/Decryption technique. The sender uses the secret key and encryption algorithm for encryption, whereas for decryption, the receiver uses this key and decryption algorithm. In Secret Key Encryption/Decryption technique, the algorithm used for encryption is the inverse of the algorithm used for decryption. It means that if the combination of addition and multiplication is used in the encryption algorithm, then the decryption algorithm will use the combination of subtraction and division. 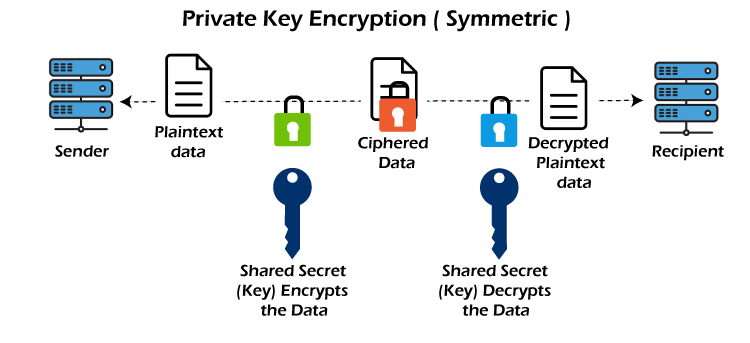
The secret key encryption algorithm is also known as symmetric encryption algorithm because the same secret key is used in bidirectional communication. The mechanism of private key is faster than the mechanism of public-key cryptography. The reason for this is that the size of the key is small. Public key v/s Private key
That's about the description of both public and private keys. Now, let's see the comparison chart between both keys. We are comparing both keys based on some characteristics.
Next TopicDifference between
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










