Splunk Basic SearchesIn this section, we are going to learn about the Basic Searches in the Splunk. We will also learn about the matching string, matches searches, how to retrieve events form the index, understanding search result, timeline of the event and pattern visualization and statistics. We build searches in this section that retrieve events from the index. The data for this tutorial is taken from titaniac.csv file, which we have uploaded earlier while the data ingestion. The file contains the information of the peoples who were present on the titanic. Matching SearchesThe Search manager also returns matching searches, which are based on your recent searches. The list of matching searches is useful if you want to run the same search from yesterday or from a week ago. When you log out, your search history will be retained. After you start learning the search language, the search assistant becomes more useful. The search wizard shows command information when you type search commands. Retrieve events from the indexLet's seek to figure out how many events are there in our titanic.csv file. You type the keywords in your search field to retrieve events that list errors or failures. If you're using several keywords, you need to define Boolean operators like AND, OR, and NOT. The AND logical operator is implied when you type in multiple keywords. For example, typing class is the same as typing titanic AND class. I am setting the time zone for effective searching.
For better understanding, take a look at the image below. 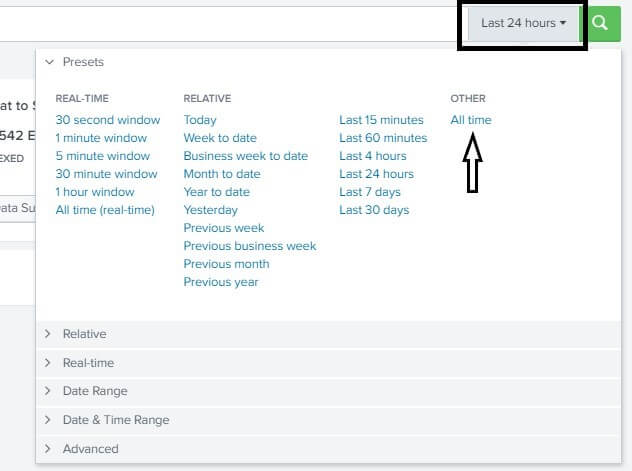
Remember that Boolean operators must be capitalized on. The symbol asterisk (*) is used as a wildcard symbol to match loss, loss, failure, failure, etc. Words within parentheses are given priority when evaluating Boolean expressions. NOT clauses shall be determined before the OR clauses. The lowest precedence is given to clauses AND. Understanding search results
Change the display of the Events viewer.
Timeline of eventsThe Event Timeline is a visual representation of the number of events occurring at each point in time. There are clusters of bar patterns, as the timeline changes with the search results. The height of each bar shows the number of occurrences. Timeline peaks or valleys can signify activity spikes or server downtime. The timeline shows incident trends or peaks and lows of event activity. The choices for the timetable are above the timeline. You can zoom in, zoom out, and adjust the timeline chart's size. Fields sidebar
You can hide the field's sidebar to maximize the results area. Patterns, Visualizations, and StatisticsThe Patterns tab represents a list of the most common patterns in the collection of events that your search returns. Each of these patterns represents incidents having a common structure. When you run a quest, the Statistics tab populates with transforming commands such as stats, top, map, etc. The Visualization tab also fills in searches with transforming commands. The Visualizations tab results region contains a diagram and the statistics table used to create the diagram. You'll learn how to convert commands, and use the tabs Statistics and Visualizations, later in the tutorial. How to search in SplunkSplunk has a new and fast searching functionality. It helps us to search the whole data set that is ingested in Splunk. We can use this feature just by clicking on the Search & Reporting option present on the left side of your Splunk platform. Click on it. 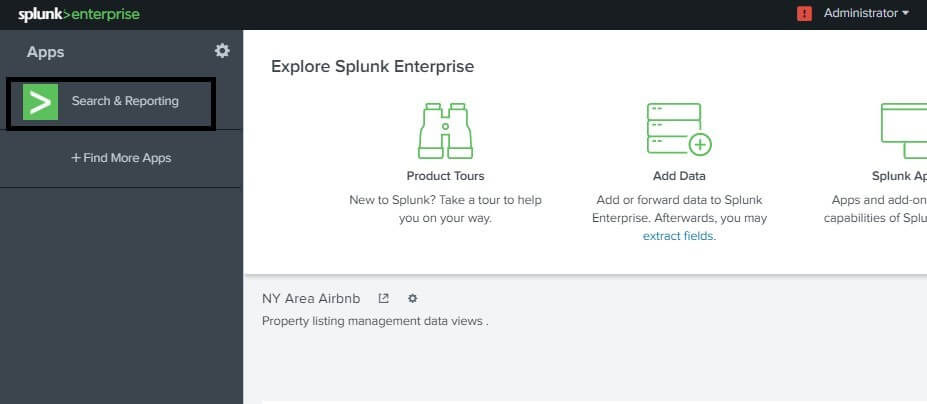
After you click on this option, a new page will appear on the screen stating New Search on the top of the window. Here we are given a search bar on the top where we can search anything we want from our uploaded database. We will write the index and the name, as shown in the image below, that we provided in our index name while we uploaded the data in the Data Ingestion tutorial. We can press the enter button from our keyboard, or we can also click on the search icon that is present on the right end of the search bar. Note
As we click on the Search button after setting up the right time zone, we will get the result. The result will consist of all the data that is associated with the index named as titanic, as we can see on our screen. 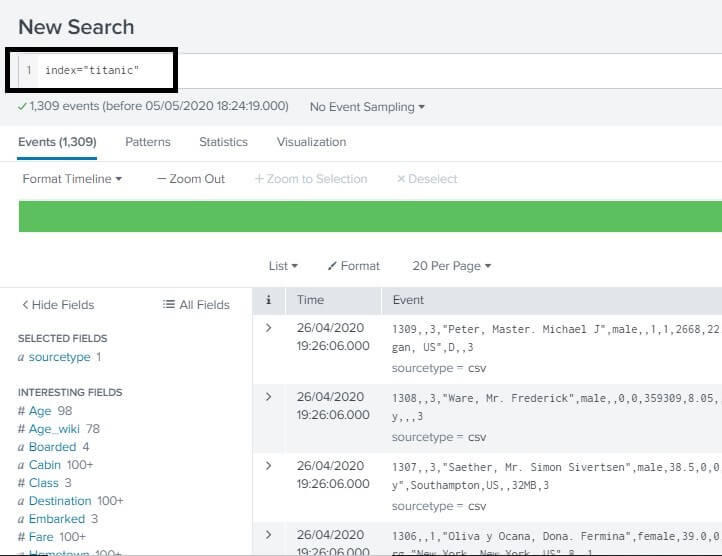
Combining Searching TermsWe can also search on our search bar by combining the different search perimeter's in it. But we have to make sure that the searching term must be in the same format as it is in the file or the Fields because Splunk searching is case sensitive. Sometimes writing the string may not return the value, so we must take care that for combining the different search perimeter, we must write the search string under the double-quotes. 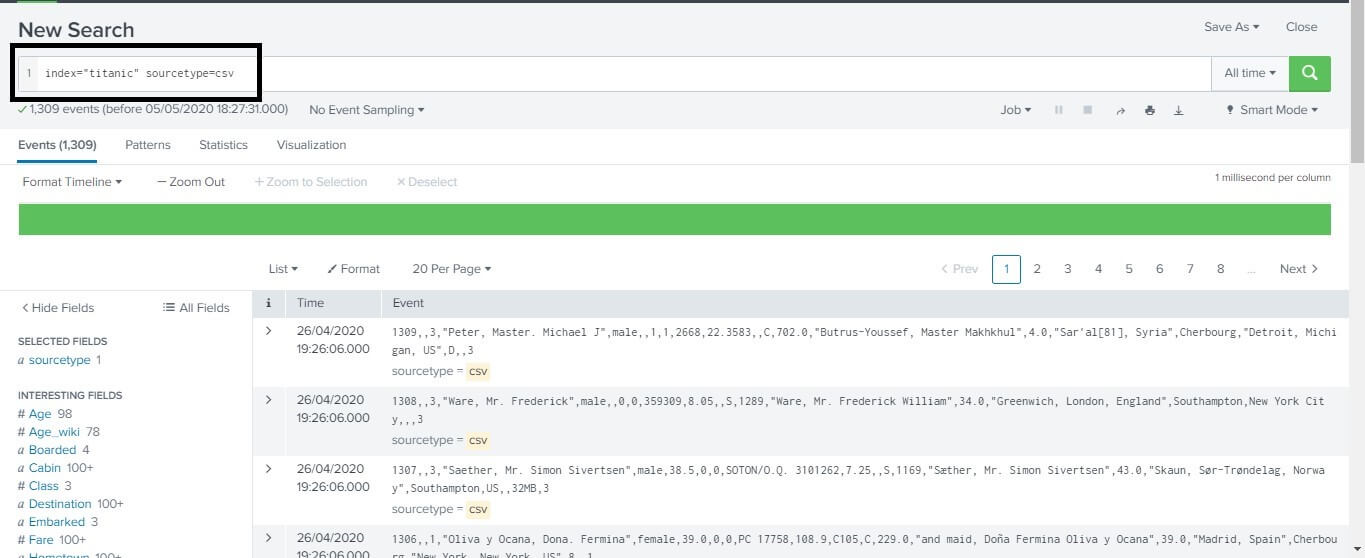
Using the wildcardWe can also use the wild card for effective searching in our data set. We can also combine our wild card with other logical operators like AND, OR. In the search below, we are searching for all the hometowns in our data set that starts with letter P in the data set. After pressing the enter button, we get the following result of all the events on our screen. This is a list of all the peoples that are having their hometown name starting with the letter P. 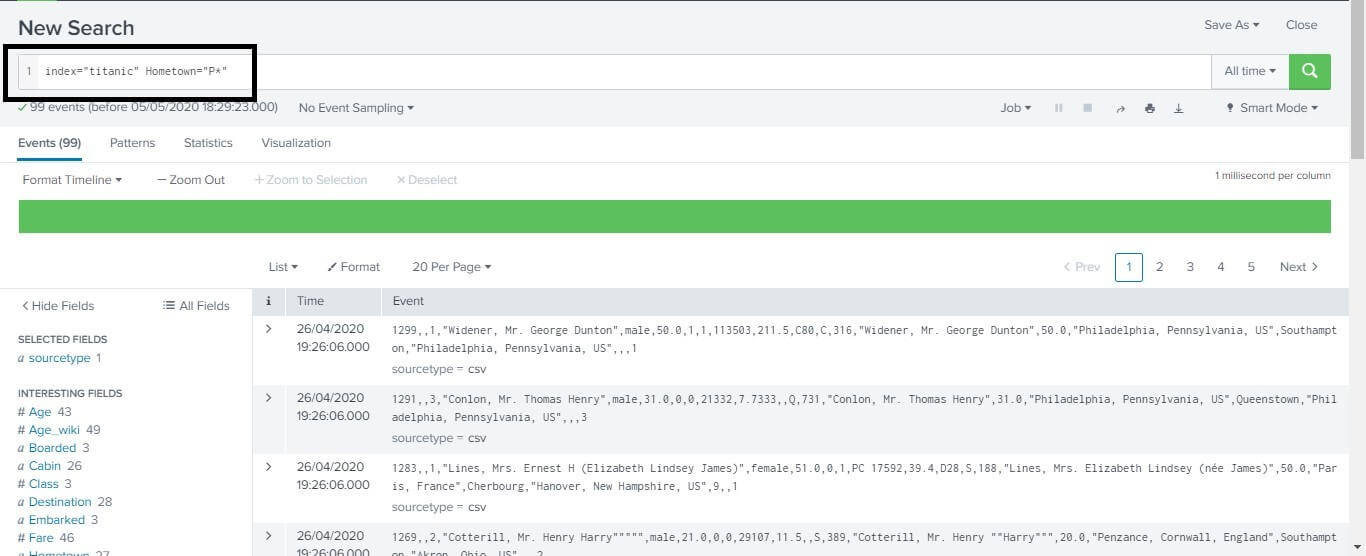
Refinement of Search ResultWe can also refine our search results to get the optimum output from our data. We can further improve it also by just adding a string to our search space. We just need to write the string into our search bar and click on the search button to search it. In the example below, we just want to search for the word Line in our dataset, so we just wrote Line in our search bar. Then the events returned contain the string that we searched for. For reference, you can have a look at the image below. 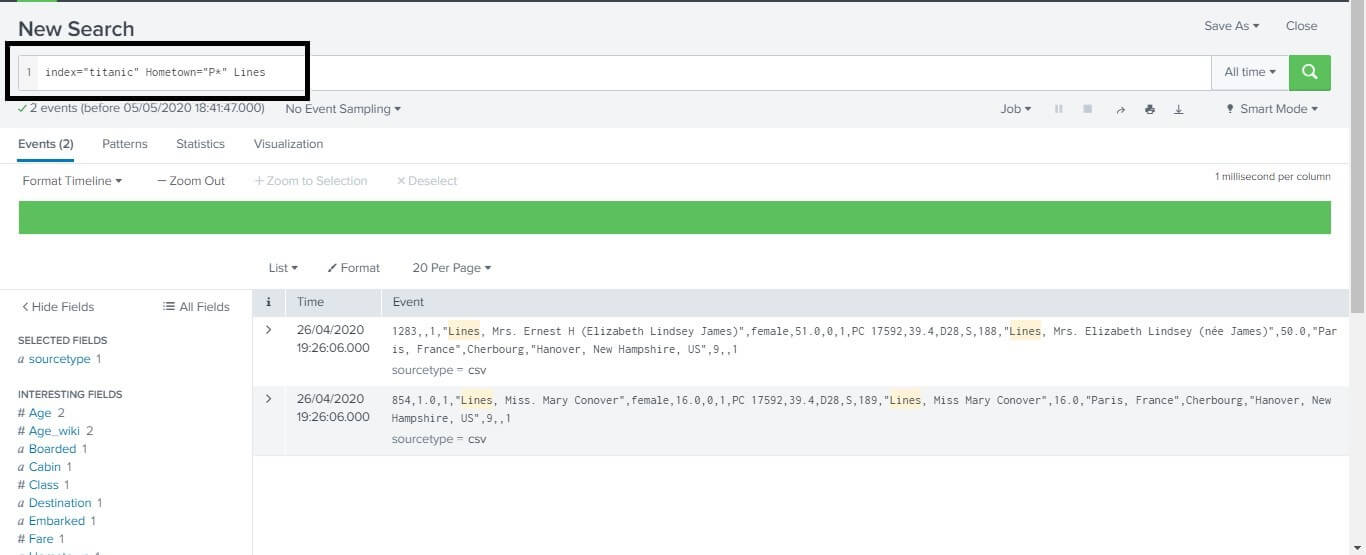
Boom! You just learned how to search in the Splunk platform. Now go on hitting the platform and explore.
Next TopicSplunk Field Searching
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










