Subdomain scanner toolsIn order to discover subdomains, the best subdomain scanner tools based on the terminal are as follows: AMASSAccording to Jeff Foley, when we want to discover a subdomain, we will Amass because it is one of our favorite tools. If we want to gather and accumulate the data of the subdomain in a large amount, we will use one of the most powerful commands, which are based on the terminal. We can get the subdomain's full list by the various types of subdomain mapping techniques, including reverse NDS sweeping, recursive brute force, machine learning, and scrapping, which is used by Amass. It can provide faster passive reconnaissance of subdomain by including the full integration along with SecurityTarils API. If we are trying to install Amass, it will become easy by using snap on Kali Linux operating system, or by precompiled packages, and other Linux distros. To do this, we can type the following command: We can start playing with amass when the above command gets running. Now we are going to see the use of amass to easily determine the subdomains. 
We can run the basic subdomain scanning by using the following command: The output of the above command is as follows: Using the single command, we can also scan the multiple domains, which are shown as follows: If we run amass -h command, we can find the other advanced scans. SubBruteOne of the fastest tools for subdomain discovery based on the brute force, which we have ever tested, is SubBrute. It is used to conceal the subdomain scanning's origin, and this feature is the coolest feature of it. Using the SubBrute, the enumerated DNS records can be recursively crawled by working as a DNS spider. By this, a complete terminal-based DNS toolkit is made. The syntax of SubBrute is described as follows, and it is very simple. The output of the above command is shown in the following screenshot: 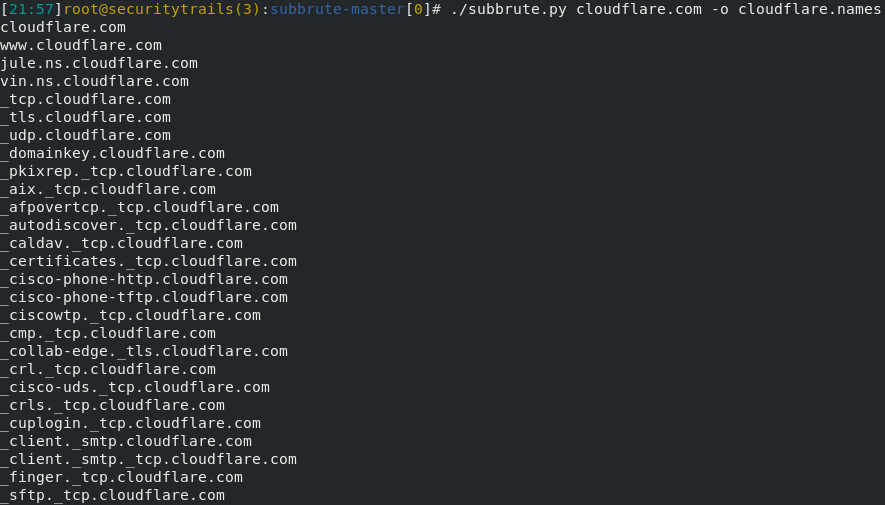
Filtering DNS records are supported by SubBrute. We will use the option --type if we are using any given domain name and want to get only TXT records. Using the function subbrute.run(), we can integrate our python script with the SubBrute, and this is another interesting fact about SubBrute. For example, If we want to use its advanced option, we will simply run the following command: KnockThe intel-gathering process is performed by the infosec researchers with the help of another tool of python subdomain scanning, which is known as Knock. When a full DNS zone transfer is performed, it will work. In the VirusTotal subdomain database, a query will be run by knock if DNS zone transfer fails. This program is very simple, and when we want to discover subdomains, it will perform a great job. The python-dnspython package is required by knock, and all major Linux distributions have this package. This task will become very simple when we have that sorted out. This file contains the VirusTotal API key, and we configure this key for this test as follows: After that, we will run the following setup like this: Lastly, against the target, we will run the scan like this: The above command will generate the expected output, which is shown in the following screenshot: 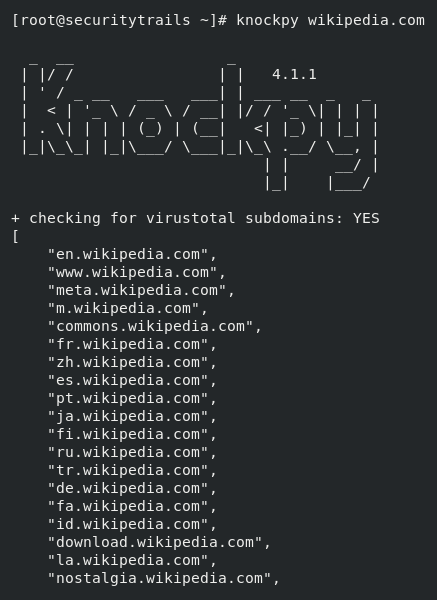
The other useful details like response status, remote detected server hostname, IP address and domain name are also provided by the same scan. 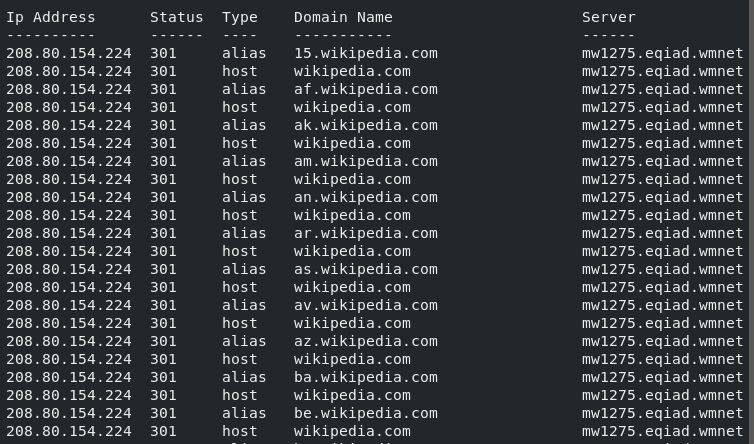
The scan can also be launched by the -w option followed by the external wordlist like this: When we run the knockpy -h command, we can get the other options and advanced scans options. DNSReconDNSRecon is known as one of the most known domain reconnaissance scripts. DNSRecon is written in Python, just like every other one described in this list. For AXFR zone transfer, when we checked all NS records, it will work. In order to perform DNS enumeration for any record type like SPF, TXT, SOA, SRV, MX, and NS, DNSRecon will be very useful. Wildcard resolution checking is supported by DNSRecon. It also supports discovery based on brute force for AAAA and A type records. The power of DNSRecon does not stop there. The indexed subdomains can also be fetched by GoogleBot by querying Google dorks. When we download the package of DNSRecon, a few required packages are necessary to install with pip. After this, we can test it like this: After executing this command, the following output will be generated: 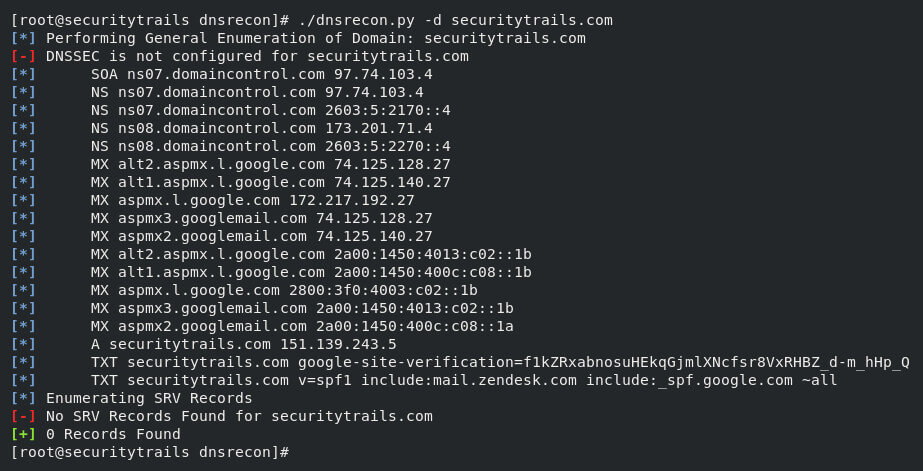
In the above screenshot, we can see that all types of DNS records are fetched by the DNSRecon scanning against securitytrails.com like TXT, MX, SOA, A, NS, and SRV records are also tried to enumerated by them. Our dns discovery can also be helped by the simple -d option. A directory file followed by option -D is used to also find the subdomains. Sublist3rIt can be described as a massive subdomain scanner, and it is based on Python. In order to collect the subdomain data, blue and red terms and bug bounty hunters also widely used it. If we need to determine subdomains, this tool will be fastest and most effective for us because it has the ability to query search engines like Baidu, Google, Bing, Yahoo and other third-party sources such as Netcraft. It may be surprising for us that it is also supported wordlists along with brute force attacks. Python 2 or Python 3 versions are the minimum requirement for Sublist3r. Version 2.7.x is recommended by Python 2. Version 3.4.x is recommended by Python 3. If we want to start, the Git repo needs to be a clone. After that, for some dependencies with a pip, we will run the installation like this: Now, the installation is completed. So, the subdomain scanning tasks can be performed like this: The above command will generate the expected output, which is shown in the following screenshot: 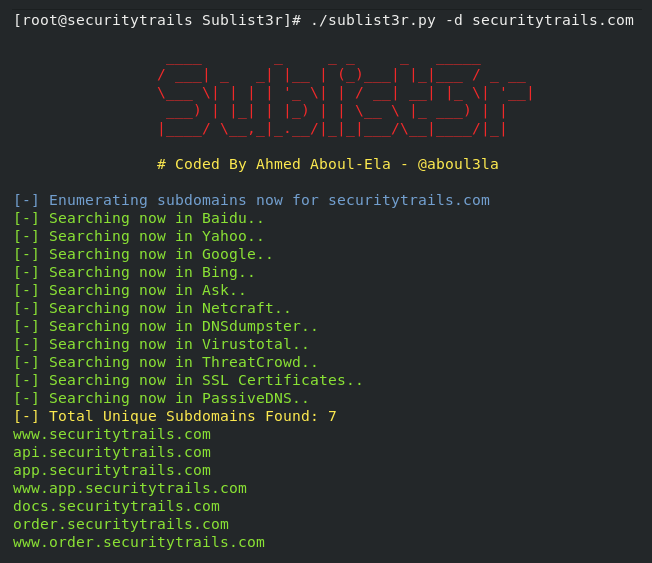
The certain open ports of subdomains are only scanned by this subdomain scanner, and this is the very cool feature of Sublist3r. For example: Subdomain enumeration is performed by the above request, and it will filter the hosts, which contain open ports as 80 and 443. AltDNSOn the basis of working with permutation and alteration, this subdomain discovery tool depends. The domain name may contain the muted or altered results, and the script can be run to generate both by using the list of confirmed subdomains and setting our default wordlist or our own wordlist of possible sensitive areas like server, test, dev, staging, etc. 200 + subdomains dataset is included by this AltDNS, and when we required that subdomains can churn out valid subdomains. When the git project is cloned, we can use pip to quickly resolve the dependency like this: After this, we can AltDNS is ready, and we can use it like this: Note: The list of the existing actual subdomain is described by subdomain.txt, and the wordlist of AltDNS is described by the words.txt.After executing the above command, the expected output will be generated, which is shown in the following screenshot: 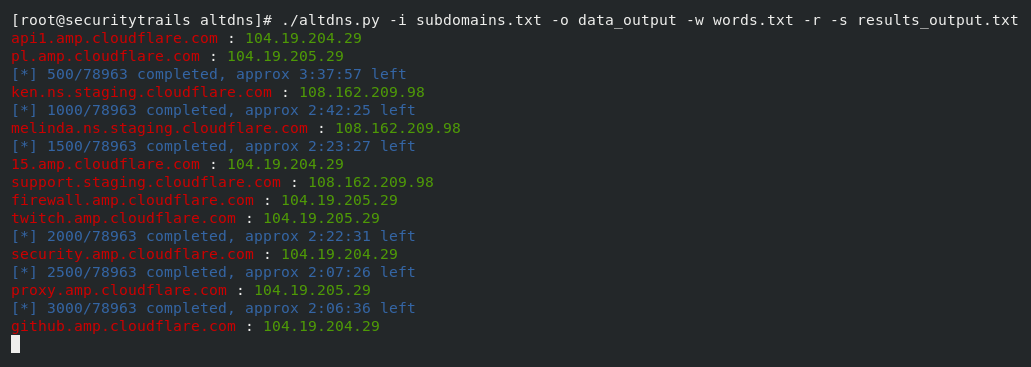
SummaryThe live subdomain databases are still generated by the tools based on the old terminal, but we can use passive OSINT sources to find the subdomains, and it is the more effective and fastest way to determine subdomains. When it comes to tasks of subdomain scanning and subdomain mapping, then the domain, passive DNS and IP intelligence database like the one we have built at SecurityTrails is now the #1 source of data.
Next TopicHandshaking Lemma
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










