Top 5 Tools for Sniffing and SpoofingSniffing and SpoofingThe network can be a valuable source of information and offers a variety of potential attack vectors for a penetration tester. Sniffing network traffic can offer access to valuable intelligence, and spoofing traffic can enable a penetration tester to identify and exploit potential attack vectors. Kali Linux is an operating system that is built for penetration testers that comes with a vast set of built-in tools. One of the tool categories within the Kali Linux operating system is focused on sniffing and spoofing network traffic. Sniffing is the process in which all the data packets passing in the network are monitored. Network administrators typically use sniffers to monitor and troubleshoot network traffic. Attackers use sniffers to monitor and collect data packets in order to acquire sensitive data such as passwords and user accounts. Sniffers can be installed as hardware or software on the system. Spoofing is the process in which an intruder creates fake traffic and pretends to be someone else (legitimate entity or legal source). Spoofing is accomplished by transmitting packers over the network with an erroneous source address. Using a digital signature is a great technique to deal with and tackle spoofing. Kali Linux Top 5 Tools for Sniffing and SpoofingKali Linux has several tools for sniffing and spoofing network traffic. The following are the top 5 tools for sniffing and spoofing: 1. WiresharkOne of the best and widely used tools for sniffing and spoofing is Wireshark. Wireshark is a network traffic analysis tool with a plethora of capabilities. Wireshark's extensive library of protocol dissectors is one of its most distinguishing features. These allow the tool to analyze a wide range of protocols, break out the several fields in every packet and display them within an accessible graphical user interface (GUI). Users with even basic network understanding will be able to understand what they are looking for. In addition, Wireshark has a number of traffic analysis tools, such as statistical analysis and the capability to follow network sessions or decrypt SSL/TLS traffic. 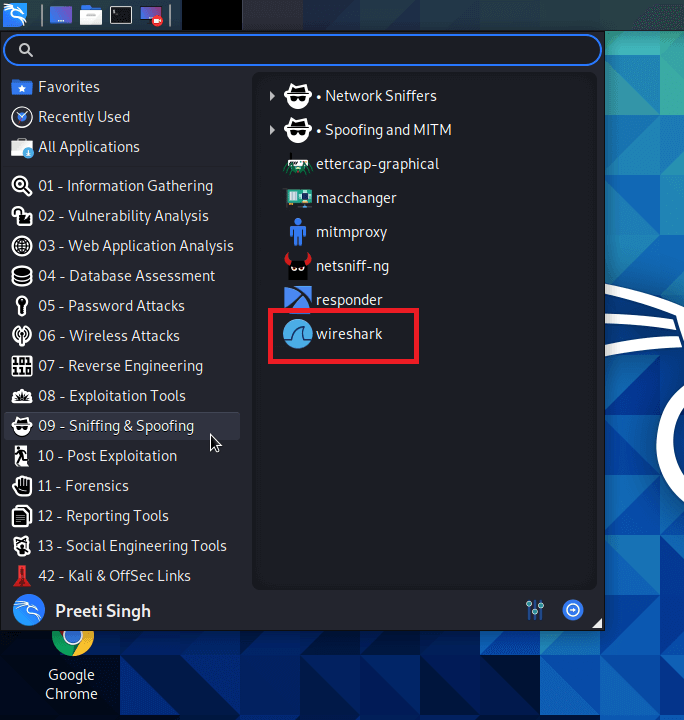
Wireshark is a useful sniffing tool since it gives us a lot of information about network traffic, either from a capture file or a live capture. This can help with understanding the network layout, capturing leaked credentials, and another task. 2. MitmproxyThe attacker interjects oneself into communication between a client and a server in a man-in-the-middle (MitM) attack. All traffic passing across that connection is intercepted by the attacker, giving them the ability to listen in on traffic and change data passing through the network. 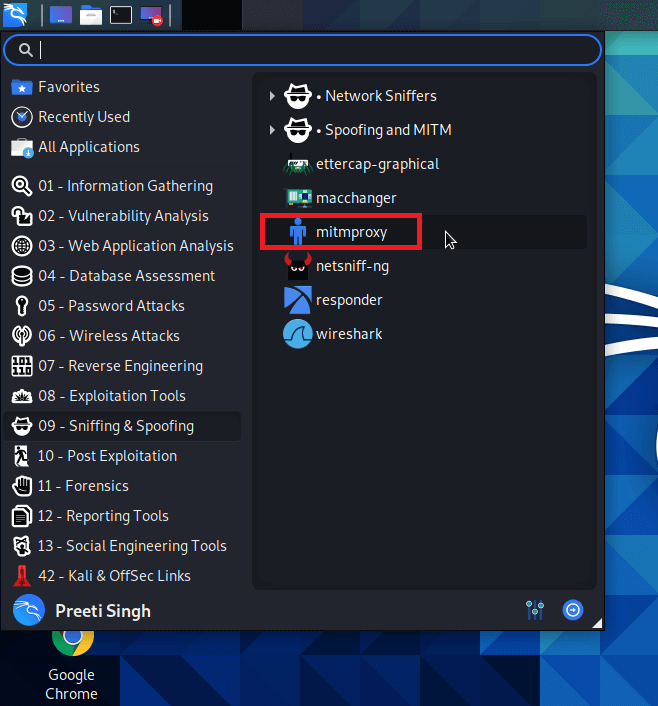
With the help of the mitmproxy in Kali Linux, we can easily perform the MitM attacks on web traffic. It enables the on-the-fly capture and modification of HTTP traffic, supports client and server traffic replay, and comprises the capability to automate attacks using Python. Mitmproxy may also support the interception of HTTPs traffic with SSL certificates generated on-the-fly. 3. Burp SuiteBurp Suite is a collection of various penetration tools. Its main focus is on web application security analysis. Burp Proxy is the main tool in Burp Suite which is helpful in Sniffing and Spoofing. Burp Proxy permits us to intercept and modify HTTP connections, as well as provides supports for intercept HTTPs connection. 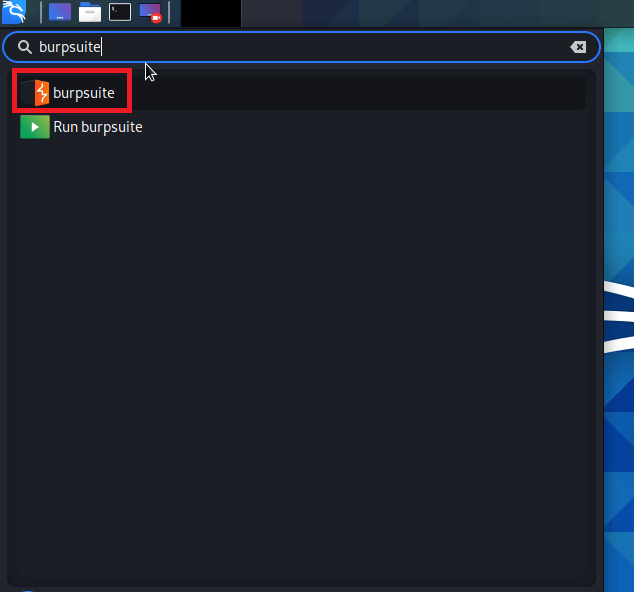
It works on a freemium model. Although the basic tools are free, attacks must be carried out manually without the ability to save work. Paying for a license grants us access to a larger tool (including a web vulnerability scanner) as well as automation support. 4. dnschefThe dnschef tool is a DNS proxy that may be used to analyze malware and penetration testing. A highly configurable DNS proxy, dnschef, is used for analyzing network traffic. This DNS proxy can generate fake requests and utilize these requests to be sent to a local machine rather than a real server. This tool works on multiple platforms and can generate phony requests and responses depending on domain lists. Different DNS record types are also supported by the dnschef tool. 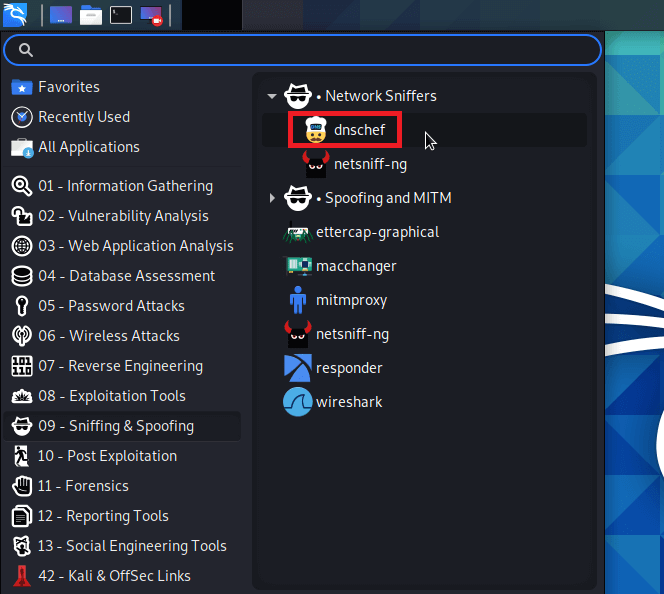
When it is impossible to force an application to use another proxy server, a DNS proxy must be used instead. If a mobile application disregards the HTTP proxy setting, dnschef can deceive it by faking requests and answers to a specified target. 5. ZaproxyOn Kali Linux, the executable named Zaproxy is OWASP's Zed Attack Proxy (ZAP). Like Burp Suite, ZAP is a penetration testing tool that aids in detecting and exploiting vulnerabilities within web applications. Because of its ability to intercept and modify HTTP(S) traffic, ZAP is a handy tool for sniffing and spoofing. ZAP has a lot of functionality and is a completely free tool for carrying out these attacks. 
Next TopicInstall LibreOffice in Kali Linux
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










