WEP IntroductionIn this section, we will discuss WEP (Wired Equivalent Privacy). It is the oldest one, and it can be easily broken. WEP uses the algorithm called RC4 encryption. In this algorithm, each packet is encrypted at the router or access point and then send out into the air. Once the client receives this packet, the client will be able to transform it back to its original form because it has the key. In other words, we can say that the router encrypts the packet and send it, and the client receives and decrypts it. The Same happens if the client sends something to the router. It will first encrypt the packet using a key, send it to the router, and the router will be able to decrypt it, because it has the key. In this process, if a hacker captures the packet in the middle, then they will get the packet, but they wouldn't be able to see the contents of the packet because they do not have the key. 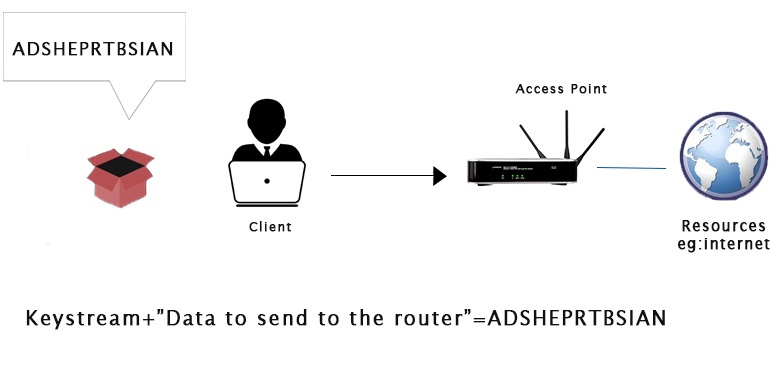
Each packet that is sent into the air has a unique keystream. The unique keystream is generated using a 24- bit IV (Initialization Vector). An initialization vector is a random number that is sent into each packet in plain text form, which is not encrypted. If someone captures the packet, they will not be able to read the packet content because it is encrypted, but they can read the IV in plain text form. The weakness with the IV is that it is sent in the pain text and it is very short(only 24- bit). In a busy network, there will be a large number of packets sent in the air. At this time 24-bit number is not big enough. The IV will start repeating on a busy network. The repeated IVs can be used to determine the key stream. This makes WEP vulnerable to statistical attacks. To determine the key stream we can use a tool called as aircrack-ng. This tool is used to determine the key stream. Once we have enough repeated IV, then it will also be able to crack WEP and give us the key to the network.
Next TopicWEP Cracking
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










