What is sshd in Linux?
sshd is a server process of the OpenSSH. It receives the incoming connections with the help of SSH protocol and operates as a server for this protocol. It manages encryption, file transfers, tunnelling, terminal connections, and user authentication.
Roles and start-up of distinct sshd processes
The process of sshd is begun when the system restarts. Usually, the program is located at the file, i.e., /usr/sbin/sshd. It executes as the root. The starting process operates as a master server that receives incoming connections.
This process is generally the one along with the process ID (lowest) or the one that is executing the longest. Also, it is a parent process of every other process of sshd. The below command could be used for displaying the process tree over Linux. It's easy to find which one is a parent process:
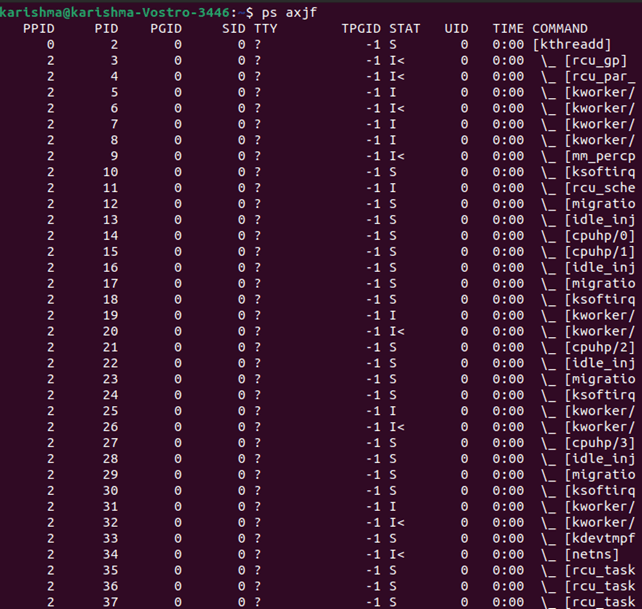
Various other processes of sshd are the child processes that represent an individual connection. A newer process is established for all the new sessions of SSH.
- When the SSH server is restarted or upgraded, the only master server is restarted.
- The server is developed hence that the processes of the server providing existing connections proceed to operate.
- It minimizes the interruption to users, for example, when the Sambar server configuration is modified.
- Usually, one of the easiest methods for restarting the SSH server is to apply the service sshd restart command.
- We should be careful when upgrading several configurations remotely because errors can prevent connecting to a server again.
Also, it's possible to kill a single process by killing the process of the server for a specific command, terminal, or user. It can be done, e.g., with the help of the kill -9 command.
It's also possible to execute more than one master sshd process over a similar system. It is very unusual, however, we have found organizational customers with multiple servers executing simultaneously along with distinct configurations.
All the servers will have to listen to a distinct port and will usually have a distinct configuration file.
sshd Configuration file
The SSH server contains a configuration file which is usually the /etc/sshd/sshd_config. This configuration file defines logging, file locations, authentication options, encryption options, and several other parameters.
Logging
The SSH server applies the syslog subsystem to log in. There are several ways for configuring syslog and various syslog servers. Several enterprises collect syslog information into the centralized SIEM system (short for Security Incident and Event Management system).
The syslog subsystem can be configured for logging SSH-related data into files under the /var/log/auth file by default on most of the systems. The /var/log/auth file is usually the default log file on most of the Debian-derived systems. The /var/log/secure file is usually the default log file on most of the Red Hat-derived systems.
Both the logging level and syslog facility could be configured inside the server configuration file. It is highly recommended for setting the login level to VERBOSE. Hence the fingerprints for the access of SSH get logged properly.
The newest versions of OpenSSH might automatically log it. However, several distributions of Linux come with various versions that do not log fingerprints without this type of setting.
Log files
Seeing at various log files could often acknowledge insights into the reason for the issues. Intentionally, the messages transferred to the client are created for revealing a bit about that user who has logged in as. It is for security causes.
For example, we do not wish the attacker to test the user accounts available over the target system. In other words, more data about authentication failures could often be detected inside the log file.
Debug Mode
Manually, the system administrator can execute the server along with the option, i.e., -d for getting other verbose results by the server. Often, it is the end resort when identifying connection problems.
The reason for authentication failures is usually clearly transparent in the output. It might be desirable to execute the newer server in a distinct port as compared to a normal server.
It is because of not preventing new connections to a server. The server will be run along with sshd -d -p 2222 and after that, the client will connect with the ssh -p 2222 [[email protected]]host.
sshd Options in Command Line
Manually, it is very rare to have to facilitate command options for an SSH server. Only users repackaging SSH or making new embedded platforms or new Linux distributions will do it.
The below options have existed in OpenSSH:
- -4: It uses IPv4 addresses only. It may be applied inside the environments in which DNS provides IPv4 addresses; however, routing doesn't work for these types of options.
- -6: It uses IPv6 addresses only. It may be applied to test to ensure that the connectivity of IPv6 works properly.
- -C connection_spec: This option is used to test the specific Match blocks inside the configuration file or inside the combination with the option, i.e., -T. The connection_spec can be defined as a comma-separated of = pairs list, in which could be one of: addr, lport, laddr, host, or user. One than one option of -C is combined and permitted.
- -c host_certificate_file: This option defines the path of the file including the certificate of the host for a host. This certificate is in the proprietary format of OpenSSH.
- -D: It doesn't become a daemon and detach. Often, it is applied when sshd is executed with systemd. It permits the process of easier monitoring in such platforms.
Without using such option, the SSH server detaches and forks from the terminal, enabling itself a process of the background daemon.
Until recently, the latter is the traditional form to execute the SSH server. Several embedded systems will still make use of the latter.
- -d: It enables the mode of debugging. The server doesn't fork and it will exit later processing an individual connection. It could be used to diagnose user authentication and other types of issues.
Usually, it provides more details about the issue, and then it will be set to a client.
- -E log_file: It appends the logs to a particular file rather than transferring them to the syslog.
- -e: Ut writes the logs of the debug to various standard errors. It can be used to debug.
- -f config_fileIt defines the path of a server configuration file. The /etc/ssh/sshd_config file is by default used.
- -g login_grace: It defines how quickly the users should authenticate themselves later opening the connection to an SSH server. 120 seconds is the default but it could be modified inside the server configuration file. Permanently, the timeout restricts reserving resources over a server by starting the unauthenticated connection to it.
- -i: It will be used when the server was executed by using the inetd. But, nobody does it these days.
- -h host_key_file: It defines a file through which for reading a host key. We can use the file, i.e., /etc/ssh/ssh_host_ as the default. Only a single host key could be defined for all the algorithms.
- -k timeout: It is an obsolete option. This option was applied with the 1 version of SSH. Its application is discouraged strongly.
- -o options: It overrides the configuration option described inside a configuration file. It can be helpful to test and run more than one server on distinct ports.
- -p port: It defines the port that a server receives. 22 is the default port. The port could also be described inside a server configuration file.
- -q: It doesn't transfer anything to a system log. It is not suggested. One of the actual uses of this type of option will be for various attackers for hiding the logins with the backdoor. Really, this option should not be there.
- -T:
It reads a server configuration file, inspects the syntax, and exits. It is helpful to check that a configuration file is fine before rebooting the server.
Especially, inspecting the configuration file is essential when remotely updating the configuration. In these types of cases, it's better to test a new configuration by executing the second server over a new port and only reboot the main server after login with the help of the test server successfully.
It could be combined with the options -C for testing a single Match block inside the configuration file.
- -t: It checks the configuration file and referenced key's validity. Check -T option for advice on extra resting before remotely rebooting the server.
- -u len: This option contains only one helpful aim: describing -u0 reasons dotted IP addresses to be saved inside the utmp file.
It also disables the lookups of DNS by an SSH server when the from=patterns or authentication techniques over the authorized keys don't need them.
|

 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










