What is Authorization in Information Security?IntroductionAuthorization is the process of granting someone permission to carry out a task. It explains how to find out if a user is authorised to use a resource or not. It may represent data and information to which a user has access. Another name for it is AuthZ. In general, authorization works in conjunction with authentication to allow the system to determine who is accessing the information. A security framework called authorization is used to determine the level of access that a user or client has to certain system resources, like software, files, services, data, and application features. Authentication is typically required before authorization in order to verify the identity of the customer. Generally, system administrators (SA) give access rights to certain customers and system resources. 
A system verifies an authenticated user's access rules during authorization and decides whether to grant or deny them access to resources. In order to facilitate the deployment and management of applications, modern, multiuser operating systems rely on well-designed authorization processes. Verification is necessary for important elements including user type, quantity, and credentials, as well as associated roles and actions. Role-based authorization, for example, can be assigned to user groups that require specific user resource tracking rights. Moreover, authorization can be based on an enterprise authentication structure such as Active Directory (AD) for seamless integration with security policies. For instance, by connecting with Microsoft Windows and the Internet Information Server (IIS), ASP.NET provides authorization and authentication services for web-based.NET applications. For certain resources, Windows supports Access Control Lists (ACL) via the New Technology File System (NTFS). The final authority on resource access is held by the ACL. For authorization support, the.NET Framework provides an alternative role-based security mechanism. Similar to code access security checks, role-based security is a dynamic method that works well with server applications. Authorized application users are determined based on their responsibilities. 
What the identity is permitted to perform is specified by an authorization policy. For example, while any bank customer can create and use an identity (such as a user name) to log into the bank's online service, the bank should ensure that after the identity has been authenticated, only the bank is permitted to access the specific account online. There are several levels of authorization, so it's not only restricted to a website or company intranet. A collection of identities with a shared authorization policy may contain an individual identity. Handling Authorization in a Computer SystemAuthorization rules in computer systems are part of an IT discipline known as Identity and Access Management (IAM). System administrators can regulate who is granted access to system resources and set client rights with the use of authorization and authentication under IAM. IT systems handle authorization services in a manner that is strikingly comparable to an actual access control procedure. Authorization Use CaseConsider using a collaborative platform such as Google Docs. Using the software, you may make and share documents. The ability to edit, remove, and comment on a document are examples of additional permissions. You can set up one or more access policies and share a document with other people if you are its owner. For instance, you can allow someone to simply add comments to your work after sharing it with them. In this instance,
The authorization to access resources is shown in the diagram below: 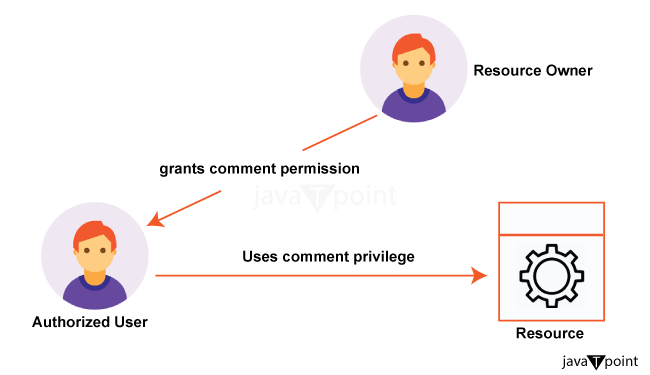
Definition of Authorization Using Authorization StrategiesComputer systems employ a variety of permission techniques for distributing applications. The two most popular ones are role-based access control (RBAC) and attribute-based access control (ABAC). Relationship Based Access Control (ReBAC) has been the focus of Auth0's recent investigations and solutions. There are also other options, such as Discretionary Access Control (DAC) and Graph-Based Access Control (GBAC). Application developers can handle various authorization services and requirements with the aid of each of these solutions. Attribute-Based Access Control (ABAC) and AuthorizationWhen utilizing ABAC, a computer system determines, in accordance with a trait (attribute or claim) linked to that user, whether or not that person has the necessary access privileges to carry out an action. An online retailer selling alcoholic beverages is one use case for this authorization procedure. The online store requires users to register and submit identification as evidence of age. This situation can be explained in the authorization context as follows:
In order for the business to handle access requests to purchase alcohol, the age claim must be presented. Thus, in this case, access to the resource is granted or denied based on the user attribute. Role-Based Access Control (RBAC) and AuthorizationAlternatively, authorization is handled by RBAC as permissions linked to roles rather than users. All that a role is a group of permissions. Consider the scenario where an organization employs you as a department manager. It would help if you had the authority appropriate to your position in this case, such as the capacity to assign duties, grant requests for time off and reimbursement, and so forth. A system manager would initially create a position named "Manager" (or something similar) before granting these permissions. They would then link you to the "Manager" position and grant this role these permissions. Of course, that position can also be assigned to other users who require the same set of rights. Managing authorization privileges is made easier when RBAC is used, as system managers may handle users and permissions in bulk rather than having to handle each one individually. Relationship-Based Access Control (ReBAC) and AuthorizationIn terms of permission, Relationship-Based Access Control considers the following question: "Does this user have a sufficient relationship to this object or action such that they can access it?" The relationship may be established directly, as through sharing a document, or it may arise from a user attribute, like belonging to a role group associated with the object. Establishing a connection between a user and their intended task sometimes requires looking at numerous nodes within a network consisting of groups, roles, organizations, and items. The person implementing the ReBAC system decides which relationships are essential for access and what kind of permissions those relationships grant.
Next TopicApplication Whitelisting
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










