What is the difference between Encryption and Hashing?To understand the key differences between encryption and hashing, we first need to understand what both these terms actually mean. 
What is Encryption?Encryption is basically a mathematical technique that employs one or more cryptographic techniques in order to protect digital data. Because an algorithm converts the plaintext (original text) into ciphertext (which is an unreadable form of the text) during encryption, the data entered is rendered unreadable. When the data has to be read, an authorized person can decrypt it with the help of a binary key or password. The user will be able to obtain the original data after converting ciphertext back to plaintext. Sensitive information should always be encrypted to prevent hackers from accessing it. For instance, websites that send bank account and credit card details encrypt sensitive data to guard against fraud and identity theft. Key points
Why is Encryption useful?The length of the encryption security key affects the encryption's strength. Web developers utilized either 40-bit encryption, which has a key with 240 potential permutations, or 56-bit encryption in the late 20th century. 
A 128-bit scheme was adopted as the Advanced Encryption Standard (AES) encryption length for web browsers by the end of the 20th century after hackers were successful in cracking those keys. The U.S. National Institute of Standards and Technology developed key lengths of 128, 192, and 256 bits in 2001. The majority of governments, banks, and militaries employ 256-bit encryption. The security and usability of decentralized cryptocurrencies like Bitcoin are based on encryption. Encryption MethodsAsymmetric Cryptography When speed is not as important as security and identity verification are needed, asymmetric cryptography is utilized. This kind of encryption is utilized in blockchain to approve bitcoin transactions as well as digital signatures when signing documents online. Asymmetric-key techniques tend to use different keys for encryption and decryption. Techniques for asymmetric encryption include RSA and PKI. Data is encrypted using a public key and decrypted using a private key in the RSA technique, which is frequently used for secure data transport. Via the issuing and administration of digital certificates, public key infrastructure (PKI) regulates encryption keys. Synchronous EncryptionWhen speed is more important than greater security, symmetric encryption is utilized, and it employs a single, secret symmetric key to both encrypt and decrypt the plaintext. Credit card transactions frequently use this encryption. Data Encryption Standards (DES), a low-level encryption block cipher algorithm, and Advanced Encryption Standard (AES), the gold standard for data encryption and the U.S. government standard, are examples of symmetric encryption types. DES performs its job by converting plain text into blocks of 64 bits and then converting them to ciphertext with the help of keys of 48 bits. Benefits from EncryptionDigital data saved on computer systems or communicated over the internet is secret when it is encrypted. Public cloud security and safeguarding data across complicated settings are an issue as enterprises increasingly rely on hybrid and multi-cloud environments. One should always keep in mind that the security of the cloud is the responsibility of cloud service providers, but the security of any data that is to be stored therein is the responsibility of the customer. The sensitive information of an organization must be safeguarded while enabling authorized users to carry out their duties. A strong encryption key management system, access control, and audit logging capabilities should all be included in this protection, in addition to data encryption. Both organizations and consumers benefit from encryption and security for on-premises and cloud data at the file, database, and application levels. Customers' payment card information must be encrypted by merchants when it is both kept and sent over open networks, according to the Payment Card Industry Data Security Standard (PCI DSS). Frequently asked questionsWhat are the differences between an Encryption's Public and Private keys? Asymmetric encryption cryptography encrypts and decrypts data using a public key and a private key. The private key can only be seen by the owner; however, the public key is allowed to be disclosed to the general public. This method encrypts messages using the recipient's public key, but it is only the recipient's private key, with the help of which the message can be decoded. How does cryptographic failure occur? A cryptographic failure is a security flaw that allows sensitive data, including passwords, medical records for patients, trade secrets, credit card numbers, email addresses, and other private user information, to be exposed. In a hacking attack on Target Corporation in 2013, up to 40 million credit card numbers were compromised. Despite the fact that the credit card data was encrypted, the hackers' sophistication allowed them to bypass it, leading to one of the biggest breaches of this kind in American history and triggering a Justice Department and U.S. Secret Service investigation. Encryption in a nutshellTo keep private data, messages, and financial transactions secure and secret in the digital world, encryption is necessary. It safeguards the privacy of digital data that is kept on computers or sent over the internet. There are numerous encryption methods available, including the Advanced Encryption Standard (AES), which is the U.S. government standard and also the gold standard for data encryption. What is Hashing?Every length of input can be converted into a certain length of encrypted output using a mathematical technique called a hash. Because of this, regardless of the actual data or size of the file involved, its unique hash remains the same regardless of size. Hash functions cannot be used to "reverse-engineer" the input from the hashed output since they are "one-way" (like a meat grinder; you cannot transform the minced beef back into a steak). However, if we are to use the same function on the very same data, the hash will remain the same as before, allowing us to confirm that the data is the same and, therefore, undamaged, given we previously knew the hash. 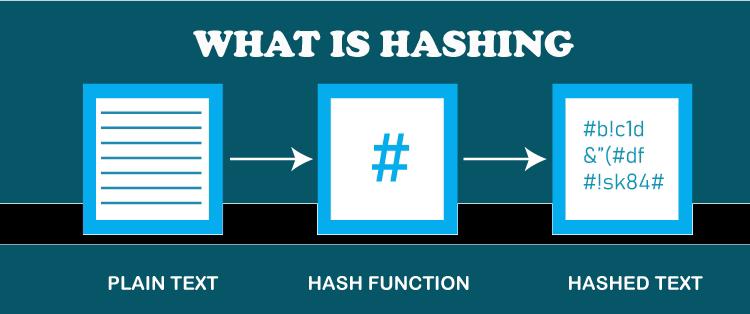
Hashing also had a major contribution to the field of bitcoin blockchain administration. Major lessons
What is cryptography's hashing process?Cybersecurity and some cryptocurrency protocols, including Bitcoin, depend on hashing operations. Any type of data can be turned into a distinctive text string by hashing. It is a straightforward mathematical procedure that is challenging to undo. The typical user comes into contact with hashing every day when it comes to passwords. The email provider does not save the password when an email address and password are formed; instead, they save the password's hash after it has been processed by a hashing algorithm. The email provider hashes the password entered each time a sign-in occurs and contrasts this hash with a previously saved hash. Access to email is permitted when the two hashes match. How does Hash function?Typical hash functions accept inputs of variable length and outputs of constant length. In cryptographic hash functions, the message-passing properties of hash functions are supplemented with security features. Hash functions are algorithms that control the encryption process. As an illustration, the Secure Hashing Algorithm 256 (SHA-256) encrypts the input it receives by:
The function that creates the hash is deterministic, which means that it always yields the same output when the same input is utilized. With extremely little computational power, SHA 256 can create a hashed output in milliseconds, but it also makes it challenging to decipher the input. As a result, hashing is perfect for protecting cryptocurrencies because it would take centuries for modern technology to figure out how to undo the encryption and get the original input. Adding security features to a message or piece of information, cryptographic hash functions make it more challenging to decipher its contents. Namely, these three characteristics are present in cryptographic hash functions:
Cryptocurrency and HashingThe blockchain, which refers to a globally distributed record created by hashing separate blocks of transaction data, is said to be the foundation of a cryptocurrency. In order to avoid fraudulent transactions and double expenditure of cash, the blockchain only stores validated transactions. Working with this hash entails mining and validating cryptocurrency. The first step in solving a cryptocurrency hash is to create a hash using the block header from the previous block as input. Each block header includes a version number, a date, the hash from the previous block, the Merkle root's hash, the nonce, and the target hash. Encryption and hashingWhat's the difference? When compared to encryption, is hashing more secure? It's usual to practice in the realm of data security to compare encryption and hashing, but why? Data is passed in as plaintext and output as ciphertext, which cannot be read, in a two-way function called encryption. Data can be decrypted to make it readable once more because encryption is two-way. Instead, one-way hashing scrambles the plaintext into a singular digest using a salt that cannot be reversed. Although it is technically possible to undo hashing, doing so would require an enormous amount of computing power. 
A hashing algorithm is used to do hashing work. The best performance of this method comes from collision resistance. Collision resistance refers to the fact that each digest is distinct from the others and does not overlap. This means that the hashing technique must be complicated enough to prevent overlapping hashes while still being manageable in terms of computation time. There are two main types of encryption, and there are several common types of algorithms used in both encryption and hashing. Popular Hashing and Encryption AlgorithmsThere are two varieties of encryption: symmetric and asymmetric. A public key and a private key are used separately for encryption and decryption in asymmetric encryption. Data is encrypted using a private key, which is kept a secret from everyone save the person doing the encryption. Anyone can access the public key, which is required for decryption. Since the data could not be re-encrypted using the private key if it were altered in transit, asymmetric encryption allows for the authentication of data. The same key is used for encryption and decryption in symmetric encryption. Due to the usage of a single key, this method of encryption is less secure but faster and needs fewer computing resources. Difference between Hashing and EncryptionDespite their similarities, encryption, and hashing serve different functions. Hashing is used, among other things, to compare huge amounts of data. Since hash values are substantially shorter than big pieces of data, they are much simpler to compare. As identifying values using hashes is quick and effective, hashes don't overlap, and hashing is also utilized for data mapping. Hashes are also used to generate random texts and digital signatures to prevent data duplication in databases. Hashing techniques are applied to passwords because they are virtually impossible to reverse. This shortens the password and prevents hackers from discovering it. 
On the other hand, encryption is typically used to encrypt data while it is in transit. As the data being transferred must only be viewed by the intended receiver, it must be sent in a way that prevents xx access. Data is encrypted so that it cannot be read by anybody other than the owner of the decryption key while it is in transit. Authentication procedures, database storage and retrieval, and other situations requiring data to be hidden at rest but later recovered all call for the usage of encryption rather than hashing. Hashing vs. Encryption: What's the Difference?Encryption:-
Hashing-
ConclusionBoth encryption and hashing are processes that are formed in an attempt to safeguard the valuable information so that it can be prevented from falling into the wrong hands. There are a number of differences between these two process such as one being a two way and other a one way process but nonetheless, both encryption and hashing are very important in today's world to safeguard data.
Next TopicDifference between
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










