Advantages and Disadvantages of Email
We have all used email at some point for a variety of purposes since the internet has become the norm. It could be for sending updated reports to a company, connecting with customers, or merely sending and receiving mail.
What is Email?
- Electronic mail is regarded as email.
- An email is a form of confidential communication between two individuals who have online accounts. It is electronic communication between computers.
- Another definition of email is the electronic transmission of messages from one computer user to a second recipient through a network.
- Email services can be web-based, like Gmail and Yahoo Mail, or they can need you to download an email software on your desktop, like Post-Box Express, etc.
Parts of an Email
The email normally consists of two fundamental parts:
- Header
- The header includes the receiver's name and the address.
- To field: The recipient's email address can be found here.
- The Cc field, which stands for carbon copy, contains a list of recipients of the message. The recipient has access to this list.
- Bcc stands for blind carbon copy, which refers to the list of recipients of a message. The receiver cannot see this list.
- The subject line for the email is usually a short title.
- Body: The message is contained in the body.
- It contains the actual text of the underlying message being conveyed.
- Additional images, a document, or any other attachment can be included in your email.
A from field is visible to the mail recipient. This contains the email address of the sender. The display name is displayed with the address.
Email address
- One needs to possess an email address to exchange and receive emails. An email address has two components:
- User name: This is the name associated with an individual's account, which may or may not be their real name.
- Domain name: A period (.) is used to denote the end of the location of the user's online account and the type of organization indicated.
Example: Username@domian_name, with the '@' sign separating the two components.
Email formats
- The two primary formats for emails are:
- Anyone can read plain text (.txt) messages, regardless of their email client. It doesn't provide any options for text formatting.
- Rich text format (.rtf) enables the insertion of images, graphics, and text formatting possibilities. It is readable by all email clients.
Email Protocols
Email communications are transmitted via email servers and use a variety of TCP/IP protocols.Several common email protocols are in use, including:
- IMAP (Internet Message Access Protocol) is a widely used client-server procedure that allows users to access emails hosted on local servers. It performs effectively in situations with low data transmission rates and sluggish connections.
- POP3 (Post office protocol) offers users a straightforward, standardized method of using their emails. It downloads messages to their PCs all at once to reduce internet costs.
- Only email messages can be transferred between email servers using the SMTP (Simple Mail Transfer Protocol) protocol.
- Although HTTP is not the protocol specifically designed for email, it can be used to access the inbox.
How does Email work?
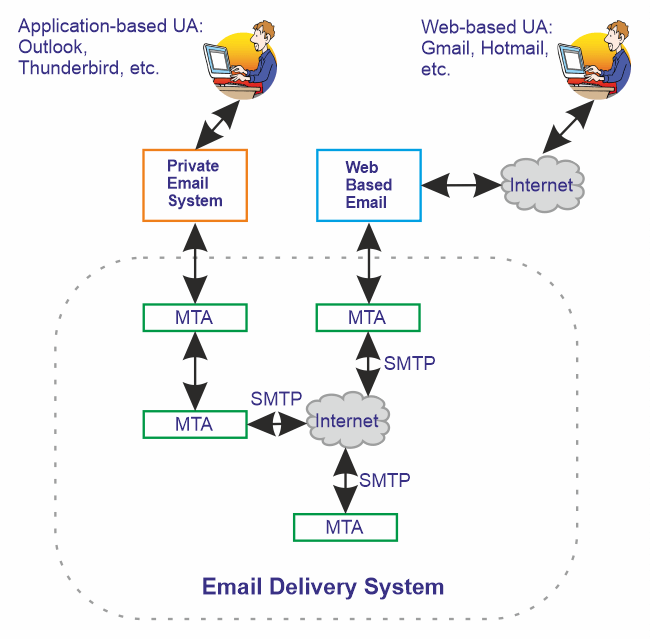
- First, in the graphic below, let's examine the list of essential elements for an email system.
- This segment will look at an example that clarifies how computers send, store, and receive emails.
- Let's pretend the email is scrolling right to the left.That is coming from the sender to the recipient at the left position.
- Let user 1 on the left and 2 on the right be two users.
- User 1 will begin by composing and addressing the email using a tool known as a mail user agent.
- The mail user agent for user 1 is an email application that operates on his personal computer. Microsoft Outlook and the open and free Thunderbird email client are two examples of such programs.
- These programs work with personal email servers like the one user 1 employs.
- A private email system: What is it exactly? Most individuals no longer use the private email system for their emails. Thus, you may be unfamiliar with the private email system.
- Web-based user agents connected to web-based email systems are likely familiar to most of us.
- The web-based user agents Gmail, Hotmail, and Yahoo mail are examples.
- However, some users want exclusive private user-agent applications that provide access to private email providers.
- Numerous establishments and workplaces will employ private systems.
- To utilize a private email system, users must have an email program like Thunderbird or Outlook downloaded on their computer.
- Emails from user 1 are likewise kept on his private network because he uses a private email system. He might even need to keep them on his computer.
- User 2 has a web-based user agent, as you can see.
- The user's two emails are saved online using a web-based user agent.
- User 2 can now send and receive email from any computer with an internet connection.
- Only computers connected to User 1's private network, which has a small number of computers, can send and receive email.
- User 1 may have just one desktop linked to the network if it is a residential network.
- User 1 then creates and sends an email via the internet.
- Email sent by user 1 from his private system must pass through several servers known as message transfer agents, or MTAs, before it can be delivered to user 2.
- When User 1 presses the send button, his user agent sends the email to the first message transfer agent after User 1 has finished writing it.
- The message is sent from that message transfer agent to another MTA, who then sends it to a third MTA through the internet.
- The final message transfer agent will keep the message until the user 2 web-based user agent asks for access to new incoming emails.
- This user agent connects to user 2's email. However, because the user agent is web-based, the data between the user agent and the user 2 computers must transit over an entirely another internet path.
- The entire process would be reversed if user 2 wanted to reply to user 1's message.
- In her user agent, shown in her web browser, User 2 would type a message.
- The email will reach her web-based email client when she clicks to send it over the internet.
- The message would pass via several MTAs as it traveled over the internet.
- The last MTA would retain and preserve the email until user 1 agent requested access to a fresh incoming email.
- The connection between the two MTAs is identified in the graphic as SMTP, as you can see.
- The communication mechanism that messages transferring agents use to communicate with one another is called SMTP, or simple mail transfer protocol.
- Similar to how internet protocol is the language of the internet, you may think of SMTP as the language of email servers.
- Additionally, it's important to remember that the name of the individual transfer agent can be found online anywhere after the @ sign-in email address.
- Therefore, an email system will ask user 1 which MTA you want to send this email to, to put it in a non-technical way.
- The one used by user 2 will elicit a response from user 1.
- The next question is, which user in this domain do you want me to deliver the message to?
- User 1 then replies by sending it to User 2.
- The computer is instructed to send this email to the user via the email address 2.
Advantages of Email
- Comparing sending email to sending postal mail, sending an email is significantly more affordable and quicker.
- By its very nature, email leaves a thorough written record of the interaction, unlike a phone conversation or face-to-face communication.
- It enables independent work according to each participant's schedule.
- The received message can be read, printed, forwarded, replied to, or deleted.
Disadvantages of Email
- Email responses require more time to respond than other messaging apps like WhatsApp.
- Emails are less intimate than other types of communication.
- For instance, it is more suitable to communicate with someone in person or over the phone rather than by email.
- Overloading information can result in decreased productivity.
- Unwanted bulk mail, or spam, is presented to the users.
- When a user becomes email tired, they stop reading and responding to a significant portion of their inboxes.
- When the email message header is created to make the message appear to be from a reputable or well-known source, email spoofing takes place.
- Email bombing is intended to cause a mail server crash when big messages are sent to a target address.
- When someone sends several messages that are hostile or enraged, this is known as flaming.
- Email scams come in many forms, such as email worms,advance-fee schemes, phishing,etc.
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now











