SQL Interview Questions and Answers
The following are the most popular and useful SQL interview questions and answers for fresher and experienced candidates. These questions are created specifically to familiarise you with the types of questions you might encounter during your SQL interview. According to our experiences, good interviewers rarely plan to ask any specific topic during the interview. Instead, questioning usually begins with a basic understanding of the subject, and based on your responses, further discussion happened. 1) What is SQL?SQL stands for the Structured Query Language. It is the standard language used to maintain the relational database and perform many different data manipulation operations on the data. SQL was initially invented in 1970. It is a database language used for database creation, deletion, fetching and modifying rows, etc. sometimes, it is pronounced as 'sequel.' We can also use it to handle organized data comprised of entities (variables) and relations between different entities of the data. 2) When SQL appeared?SQL first appeared in 1974. It is one of the most used languages for maintaining the relational database. In 1986, SQL became the standard of the American National Standards Institute (ANSI) and ISO (International Organization for Standardization) in 1987. 3) What are the usages of SQL?SQL is responsible for maintaining the relational data and the data structures present in the database. Some of the common usages are given below:
4) Does SQL support programming language features?SQL refers to the Standard Query Language. Therefore, it is true that SQL is a language but does not actually support the programming language. It is a common language that doesn't have a loop, conditional statements, and logical operations. It cannot be used for anything other than data manipulation. It is a command language to perform database operations. The primary purpose of SQL is to retrieve, manipulate, update, delete, and perform complex operations like joins on the data present in the database. 5) What are the subsets of SQL?The following are the four significant subsets of the SQL:
6) What is the purpose of DDL Language?DDL stands for Data definition language. It is the subset of a database that defines the data structure of the database when the database is created. For example, we can use the DDL commands to add, remove, or modify tables. It consists of the following commands: CREATE, ALTER and DELETE database objects such as schema, tables, indexes, view, sequence, etc. Example 7) What is the purpose of DML Language?Data manipulation language makes the user able to retrieve and manipulate data in a relational database. The DML commands can only perform read-only operations on data. We can perform the following operations using DDL language:
Example 8) What is the purpose of DCL Language?Data control language allows users to control access and permission management to the database. It is the subset of a database, which decides that what part of the database should be accessed by which user at what point of time. It includes two commands, GRANT and REVOKE. GRANT: It enables system administrators to assign privileges and roles to the specific user accounts to perform specific tasks on the database. REVOKE: It enables system administrators to revoke privileges and roles from the user accounts so that they cannot use the previously assigned permission on the database. Example 9) What are tables and fields in the database?A table is a set of organized data in the form of rows and columns. It enables users to store and display records in the structure format. It is similar to worksheets in the spreadsheet application. Here rows refer to the tuples, representing the simple data item, and columns are the attribute of the data items present in a particular row. Columns can categorize as vertical, and Rows are horizontal. Fields are the components to provide the structure for the table. It stores the same category of data in the same data type. A table contains a fixed number of columns but can have any number of rows known as the record. It is also called a column in the table of the database. It represents the attribute or characteristics of the entity in the record. Example Table: Student Field: Stud_rollno, Stud_name, Date of Birth, Branch, etc. 10) What is a primary key?A primary key is a field or the combination of fields that uniquely identify each record in the table. It is one of a special kind of unique key. If the column contains a primary key, it cannot be null or empty. A table can have duplicate columns, but it cannot have more than one primary key. It always stores unique values into a column. For example, the ROLL Number can be treated as the primary key for a student in the university or college. 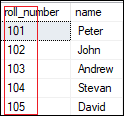
We can define a primary key into a student table as follows: To read more information, click here. 11) What is a foreign key?The foreign key is used to link one or more tables together. It is also known as the referencing key. A foreign key is specified as a key that is related to the primary key of another table. It means a foreign key field in one table refers to the primary key field of the other table. It identifies each row of another table uniquely that maintains the referential integrity. The primary key-foreign key relationship is a very crucial relationship as it maintains the ACID properties of the database sometimes. It also prevents actions that would destroy links between the child and parent tables. We can define a foreign key into a table as follows: To read more information, click here. 12) What is a unique key?A unique key is a single or combination of fields that ensure all values stores in the column will be unique. It means a column cannot stores duplicate values. This key provides uniqueness for the column or set of columns. For example, the email addresses and roll numbers of student's tables should be unique. It can accept a null value but only one null value per column. It ensures the integrity of the column or group of columns to store different values into a table. We can define a foreign key into a table as follows: To read more information, click here. 13) What is the difference between a primary key and a unique key?The primary key and unique key both are essential constraints of the SQL. The main difference among them is that the primary key identifies each record in the table. In contrast, the unique key prevents duplicate entries in a column except for a NULL value. The following comparison chart explains it more clearly:
To read more information, click here. 14) What is a Database?A database is an organized collection of data that is structured into tables, rows, columns, and indexes. It helps the user to find the relevant information frequently. It is an electronic system that makes data access, data manipulation, data retrieval, data storing, and data management very easy. Almost every organization uses the database for storing the data due to its easily accessible and high operational ease. The database provides perfect access to data and lets us perform required tasks. The following are the common features of a database:
15) What is meant by DBMS?DBMS stands for Database Management System. It is a software program that primarily functions as an interface between the database and the end-user. It provides us the power such as managing the data, the database engine, and the database schema to facilitate the organization and manipulation of data using a simple query in almost no time. It is like a File Manager that manages data in a database rather than saving it in file systems. Without the database management system, it would be far more difficult for the user to access the database's data. The following are the components of a DBMS:
16) What are the different types of database management systems?The database management systems can be categorized into several types. Some of the important lists are given below:
17) What is RDBMS?RDBMS stands for Relational Database Management System. It is a database management system based on a relational model. It facilitates you to manipulate the data stored in the tables by using relational operators. RDBMS stores the data into the collection of tables and links those tables using the relational operators easily whenever required. Examples of relational database management systems are Microsoft Access, MySQL, SQL Server, Oracle database, etc. 18) What is Normalization in a Database?Normalization is used to minimize redundancy and dependency by organizing fields and table of a database. There are some rules of database normalization, which is commonly known as Normal From, and they are:
Using these steps, the redundancy, anomalies, inconsistency of the data in the database can be removed. 19) What is the primary use of Normalization?Normalization is mainly used to add, delete or modify a field that can be made in a single table. The primary use of Normalization is to remove redundancy and remove the insert, delete and update distractions. Normalization breaks the table into small partitions and then links them using different relationships to avoid the chances of redundancy. 20) What are the disadvantages of not performing database Normalization?The major disadvantages are: The occurrence of redundant terms in the database causes the waste of space in the disk. Due to redundant terms, inconsistency may also occur. If any change is made in the data of one table but not made in the same data of another table, then inconsistency will occur. This inconsistency will lead to the maintenance problem and effects the ACID properties as well. 21) What is an inconsistent dependency?An Inconsistent dependency refers to the difficulty of getting relevant data due to a missing or broken path to the data. It leads users to search the data in the wrong table, resulting in an error as an output. 22) What is Denormalization in a Database?Denormalization is a technique used by database administrators to optimize the efficiency of their database infrastructure. The denormalization concept is based on Normalization, which is defined as arranging a database into tables correctly for a particular purpose. This method allows us to add redundant data into a normalized database to alleviate issues with database queries that merge data from several tables into a single table. It adds redundant terms into the tables to avoid complex joins and many other complex operations. Denormalization doesn't mean that normalization will not be done. It is an optimization strategy that takes place after the normalization process. 23) What are the different types of SQL operators?Operators are the special keywords or special characters reserved for performing particular operations. They are also used in SQL queries. We can primarily use these operators within the WHERE clause of SQL commands. It's a part of the command to filters data based on the specified condition. The SQL operators can be categorized into the following types:
24) What is a view in SQL?A view is a database object that has no values. It is a virtual table that contains a subset of data within a table. It looks like an actual table containing rows and columns, but it takes less space because it is not present physically. It is operated similarly to the base table but does not contain any data of its own. Its name is always unique. A view can have data from one or more tables. If any changes occur in the underlying table, the same changes reflected in the views also. 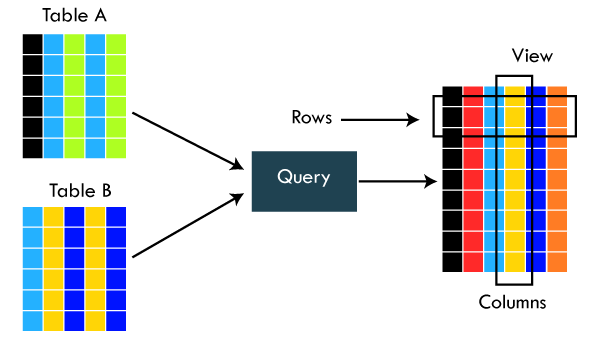
The primary use of a view is to implement the security mechanism. It is the searchable object where we can use a query to search the view as we use for the table. It only shows the data returned by the query that was declared when the view was created. We can create a view by using the following syntax: 25) What is an Index in SQL?An index is a disc structure associated with a table or view that speeds up row retrieval. It reduces the cost of the query because the query's high cost will lead to a fall in its performance. It is used to increase the performance and allow faster retrieval of records from the table. Indexing reduces the number of data pages we need to visit to find a particular data page. It also has a unique value meaning that the index cannot be duplicated. An index creates an entry for each value which makes it faster to retrieve data. For example: Suppose we have a book which carries the details of the countries. If you want to find out information about India, why will you go through every page of that book? You could directly go to the index. Then from the index, you can go to that particular page where all the information about India is given. 26) What are the different types of indexes in SQL?SQL indexes are nothing more than a technique of minimizing the query's cost. The higher the query's cost, the worse the query's performance. The following are the different types of Indexes supported in SQL:
27) What is the unique index?UNIQUE INDEX is used to enforce the uniqueness of values in single or multiple columns. We can create more than one unique index in a single table. For creating a unique index, the user has to check the data in the column because the unique indexes are used when any column of the table has unique values. This indexing does not allow the field to have duplicate values if the column is unique indexed. A unique index can be applied automatically when a primary key is defined. We can create it by using the following syntax: Example Suppose we want to make a Phone column as a unique index. We can do this like below: To read more information, click here. 28) What is clustered index in SQL?A clustered index is actually a table where the data for the rows are stored. It determines the order of the table data based on the key values that can sort in only one direction. Each table can have only one clustered index. It is the only index, which has been automatically created when the primary key is generated. If many data modifications needed to be done in the table, then clustered indexes are preferred. To read more information, click here. 29) What is the non-clustered index in SQL?The indexes other than PRIMARY indexes (clustered indexes) are called non-clustered indexes. We know that clustered indexes are created automatically when primary keys are generated, and non-clustered indexes are created when multiple joins conditions and various filters are used in the query. The non-clustered index and table data are both stored in different places. It cannot be able to alter the physical order of the table and maintains the logical order of data. The purpose of creating a non-clustered index is for searching the data. Its best example is a book where the content is written in one place, and the index is at a different place. We can create 0 to 249 non-clustered indexes in each table. The non-clustered indexing improves the performance of the queries which use keys without assigning the primary key. 30) What are the differences between SQL, MySQL, and SQL Server?The following comparison chart explains their main differences:
31) What is the difference between SQL and PL/SQL?The following comparison chart explains their main differences:
32) Is it possible to sort a column using a column alias?Yes. We can use the alias method in the ORDER BY instead of the WHERE clause for sorting a column. 33) What is the difference between clustered and non-clustered indexes in SQL?Indexing is a method to get the requested data very fast. There are mainly two types of indexes in SQL, clustered index and non-clustered index. The differences between these two indexes are very important from an SQL performance perspective. The following comparison chart explains their main differences:
To read more information, click here. 34) What is the SQL query to display the current date?There is a built-in function in SQL called GetDate(), which is used to return the current timestamp. 35) Which are joins in SQL? Name the most commonly used SQL joins?SQL joins are used to retrieve data from multiple tables into a meaningful result set. It is performed whenever you need to fetch records from two or more tables. They are used with SELECT statement and join conditions. The following are the most commonly used joins in SQL:
36) What are the different types of joins in SQL?Joins are used to merge two tables or retrieve data from tables. It depends on the relationship between tables. According to the ANSI standard, the following are the different types of joins used in SQL:
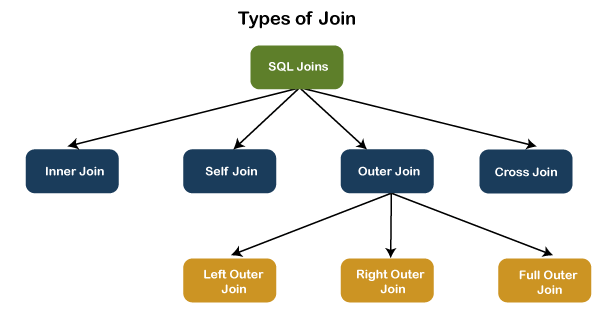
To read more information, click here. 37) What is INNER JOIN in SQL?Inner join returns only those records from the tables that match the specified condition and hides other rows and columns. In simple words, it fetches rows when there is at least one match of rows between the tables is found. INNER JOIN keyword joins the matching records from two tables. It is assumed as a default join, so it is optional to use the INNER keyword with the query. The below visual representation explain this join more clearly: 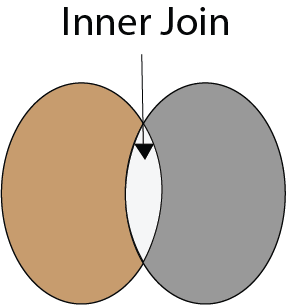
The following syntax illustrates the INNER JOIN: To read more information, click here. 38) What is the Right JOIN in SQL?The Right join is used to retrieve all rows from the right-hand table and only those rows from the other table that fulfilled the join condition. It returns all the rows from the right-hand side table even though there are no matches in the left-hand side table. If it finds unmatched records from the left side table, it returns a Null value. This join is also known as Right Outer Join. The below visual representation explain this join more clearly: 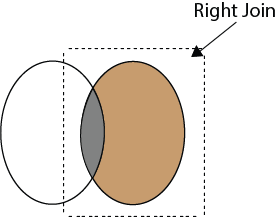
The following syntax illustrates the RIGHT JOIN: To read more information, click here. 39) What is Left Join in SQL?The Left Join is used to fetch all rows from the left-hand table and common records between the specified tables. It returns all the rows from the left-hand side table even though there are no matches on the right-hand side table. If it will not find any matching record from the right side table, then it returns null. This join can also be called a Left Outer Join. The following visual representation explains it more clearly: 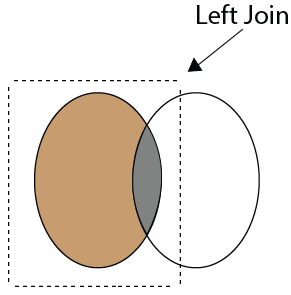
The following syntax illustrates the RIGHT JOIN: To read more information, click here. 40) What is Full Join in SQL?The Full Join results from a combination of both left and right join that contains all the records from both tables. It fetches rows when there are matching rows in any one of the tables. This means it returns all the rows from the left-hand side table and all the rows from the right-hand side tables. If a match is not found, it puts NULL value. It is also known as FULL OUTER JOIN. The following visual representation explains it more clearly: 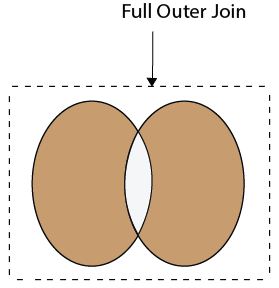
The following syntax illustrates the FULL JOIN: To read more information, click here. 41) What is a "TRIGGER" in SQL?A trigger is a set of SQL statements that reside in a system catalog. It is a special type of stored procedure that is invoked automatically in response to an event. It allows us to execute a batch of code when an insert, update or delete command is run against a specific table because the trigger is the set of activated actions whenever DML commands are given to the system. SQL triggers have two main components one is action, and another is an event. When certain actions are taken, an event occurs as a result of those actions. We use the CREATE TRIGGER statement for creating a trigger in SQL. Here is the syntax: To read more information, click here. 42) What is self-join and what is the requirement of self-join?A SELF JOIN is used to join a table with itself. This join can be performed using table aliases, which allow us to avoid repeating the same table name in a single sentence. It will throw an error if we use the same table name more than once in a single query without using table aliases. A SELF JOIN is required when we want to combine data with other data in the same table itself. It is often very useful to convert a hierarchical structure to a flat structure. The following syntax illustrates the SELF JOIN: Example Suppose we have a table 'Student' having the following data: 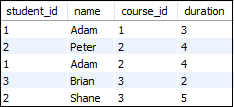
If we want to get retrieve the student_id and name from the table where student_id is equal, and course_id is not equal, it can be done by using the self-join: Here is the result: 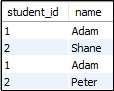
To read more information, click here. 43) What are the set operators in SQL?We use the set operators to merge data from one or more tables of the same kind. Although the set operators are like SQL joins, there is a significant distinction. SQL joins combine columns from separate tables, whereas SQL set operators combine rows from different queries. SQL queries that contain set operations are called compound queries. The set operators in SQL are categories into four different types: 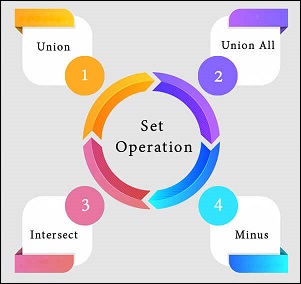
A. UNION: It combines two or more results from multiple SELECT queries into a single result set. It has a default feature to remove the duplicate rows from the tables. The following syntax illustrates the Union operator: B. UNION ALL: This operator is similar to the Union operator, but it does not remove the duplicate rows from the output of the SELECT statements. The following syntax illustrates the UNION ALL operator: C. INTERSECT: This operator returns the common records from two or more SELECT statements. It always retrieves unique records and arranges them in ascending order by default. Here, the number of columns and data types should be the same. The following syntax illustrates the INTERSECT operator: D. MINUS: This operator returns the records from the first query, which is not found in the second query. It does not return duplicate values. The following syntax illustrates the MINUS operator: To read more information, click here. 44) What is the difference between IN and BETWEEN operators?The following comparison chart explains their main differences:
45) What is a constraint? Tell me about its various levels.The constraint is used to specify the rule and regulations that allows or restricts what values/data will be stored in the table. It ensures data accuracy and integrity inside the table. It enforces us to store valid data and prevents us from storing irrelevant data. If any interruption occurs between the constraint and data action, the action is failed. Some of the most commonly used constraints are NOT NULL, PRIMARY KEY, FOREIGN KEY, AUTO_INCREMENT, UNIQUE KEY, etc. The following syntax illustrates us to create a constraint for a table: SQL categories the constraints into two levels: Column Level Constraints: These constraints are only applied to a single column and limit the type of data that can be stored in that column. Table Level Constraints: These constraints are applied to the entire table and limit the type of data that can be entered. To read more information, click here. 46) How to write an SQL query to find students' names start with 'A'?We can write the following query to get the student details whose name starts with A: Here is the demo example where we have a table named student that contains two names starting with the 'A' character. 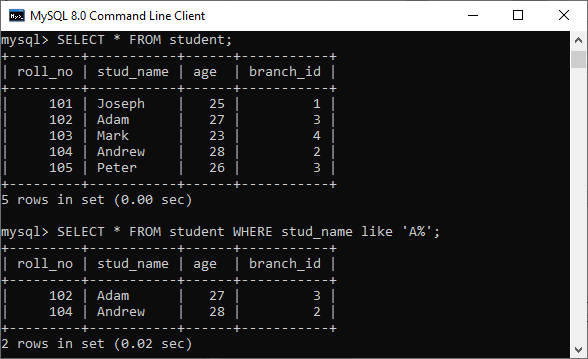
47) Write the SQL query to get the third maximum salary of an employee from a table named employees.The following query is the simplest way to get the third maximum salary of an employee: Here is the demo example that shows how to get the third maximum salary of an employee. 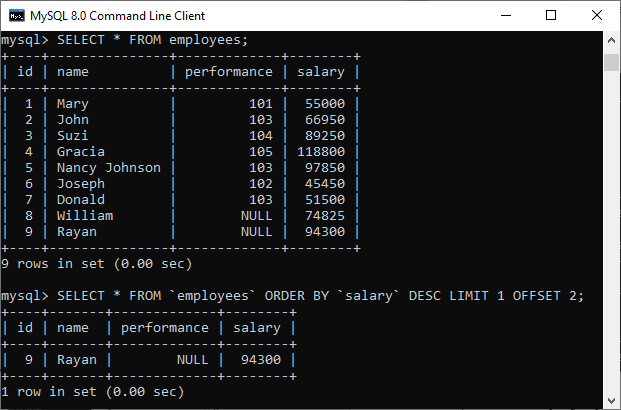
The following are the alternative way to get the third-highest salary of an employee: A. Using LIMIT Keyword B. Using Subquery C. Using TOP Keyword 48) What is the difference between DELETE and TRUNCATE statements in SQL?The main difference between them is that the delete statement deletes data without resetting a table's identity, whereas the truncate command resets a particular table's identity. The following comparison chart explains it more clearly:
To read more information, click here. 49) What is the ACID property in a database?The ACID properties are meant for the transaction that goes through a different group of tasks. A transaction is a single logical order of data. It provides properties to maintain consistency before and after the transaction in a database. It also ensures that the data transactions are processed reliably in a database system. The ACID property is an acronym for Atomicity, Consistency, Isolation, and Durability. Atomicity: It ensures that all statements or operations within the transaction unit must be executed successfully. If one part of the transaction fails, the entire transaction fails, and the database state is left unchanged. Its main features are COMMIT, ROLLBACK, and AUTO-COMMIT. Consistency: This property ensures that the data must meet all validation rules. In simple words, we can say that the database changes state only when a transaction will be committed successfully. It also protects data from crashes. Isolation: This property guarantees that the concurrent property of execution in the transaction unit must be operated independently. It also ensures that statements are transparent to each other. The main goal of providing isolation is to control concurrency in a database. Durability: This property guarantees that once a transaction has been committed, it persists permanently even if the system crashes, power loss, or failed. To read more information, click here. 50) Is a blank space or zero the same as a NULL value?No. The NULL value is not the same as zero or a blank space. The following points explain their main differences:
51) What are functions and their usage in SQL?SQL functions are simple code snippets that are frequently used and re-used in database systems for data processing and manipulation. Functions are the measured values. It always performs a specific task. The following rules should be remembered while creating functions:
SQL categories the functions into two types:
SQL functions are used for the following purposes:
52) What is meant by case manipulation functions? Explains its different types in SQL.Case manipulation functions are part of the character functions. It converts the data from the state in which it is already stored in the table to upper, lower, or mixed case. The conversion performed by this function can be used to format the output. We can use it in almost every part of the SQL statement. Case manipulation functions are mostly used when you need to search for data, and you don't have any idea that the data you are looking for is in lower case or upper case. There are three case manipulation functions in SQL: LOWER: This function is used to converts a given character into lowercase. The following example will return the 'STEPHEN' as 'stephen': NOTE: Here, 'dual' is a dummy table.UPPER: This function is used to converts a given character into uppercase. The following example will return the 'stephen' as 'STEPHEN': INITCAP: This function is used to converts given character values to uppercase for the initials of each word. It means every first letter of the word is converted into uppercase, and the rest is in lower case. The following example will return the 'hello stephen' as 'Hello Stephen': 53) Explain character-manipulation functions? Explains its different types in SQL.Character-manipulation functions are used to change, extract, and alter the character string. When one or more characters and words are passed into the function, the function will perform its operation on those input strings and return the result. The following are the character manipulation functions in SQL: A) CONCAT: This function is used to join two or more values together. It always appends the second string into the end of the first string. For example: Input: SELECT CONCAT ('Information-', 'technology') FROM DUAL; Output: Information-technology B) SUBSTR: It is used to return the portion of the string from a specified start point to an endpoint. For example: Input: SELECT SUBSTR ('Database Management System', 9, 11) FROM DUAL; Output: Management C) LENGTH: This function returns the string's length in numerical value, including the blank spaces. For example: Input: SELECT LENGTH ('Hello Javatpoint') FROM DUAL; Output: 16 D) INSTR: This function finds the exact numeric position of a specified character or word in a given string. For example: Input: SELECT INSTR ('Hello Javatpoint', 'Javatpoint'); Output: 7 E) LPAD: It returns the padding of the left-side character value for right-justified value. For example: Input: SELECT LPAD ('200', 6,'*'); Output: ***200 F) RPAD: It returns the padding of the right-side character value for left-justified value. For example: Input: SELECT RPAD ('200', 6,'*'); Output: 200*** G) TRIM: This function is used to remove all the defined characters from the beginning, end, or both. It also trimmed extra spaces. For example: Input: SELECT TRIM ('A' FROM 'ABCDCBA'); Output: BCDCB H) REPLACE: This function is used to replace all occurrences of a word or portion of the string (substring) with the other specified string value. For example: Input: SELECT REPLACE ( 'It is the best coffee at the famous coffee shop.', 'coffee', 'tea'); Output: It is the best tea at the famous tea shop. 54) What is the usage of the NVL() function?The NVL() function is used to convert the NULL value to the other value. The function returns the value of the second parameter if the first parameter is NULL. If the first parameter is anything other than NULL, it is left unchanged. This function is used in Oracle, not in SQL and MySQL. Instead of NVL() function, MySQL have IFNULL() and SQL Server have ISNULL() function. 55) Which function is used to return remainder in a division operator in SQL?The MOD function returns the remainder in a division operation. 56) What are the syntax and use of the COALESCE function?The COALESCE() function evaluates the arguments in sequence and returns the first NON-NULL value in a specified number of expressions. If it evaluates arguments as NULL or not found any NON-NULL value, it returns the NULL result. The syntax of COALESCE function is given below: Example: This statement will return the following output: 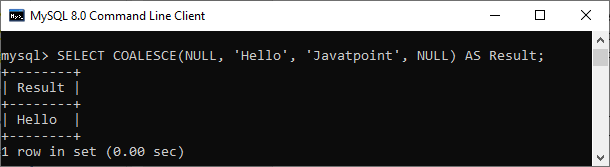
57) How do we use the DISTINCT statement? What is its use?The DISTINCT keyword is used to ensure that the fetched value always has unique values. It does not allow to have duplicate values. The DISTINCT keyword is used with the SELECT statement and retrieves different values from the table's column. We can use it with the help of the following syntax: Suppose we have a table 'customer' containing eight records in which the name column has some duplicate values. 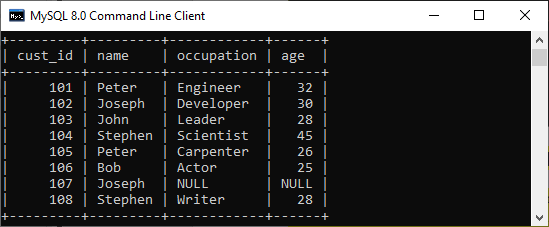
If we want to get the name column without any duplicate values, the DISTINCT keyword is required. Executing the below command will return a name column with unique values. 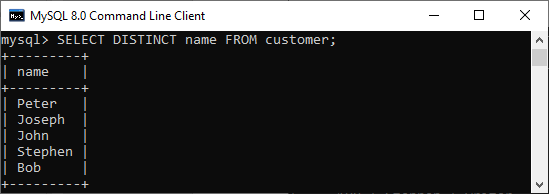
58) What is the default ordering of data using the ORDER BY clause? How could it be changed?The ORDER BY clause is used to sort the table data either in ascending or descending order. By default, it will sort the table in ascending order. If we want to change its default behavior, we need to use the DESC keyword after the column name in the ORDER BY clause. The syntax to do this is given below: We have taken a customer table in the previous example. Now, we will demonstrate the ORDER BY clause on them as well. In the below output, we can see that the first query will sort the table data in ascending order based on the name column. However, if we run the second query by specifying the DESC keyword, the table's order is changed in descending order. 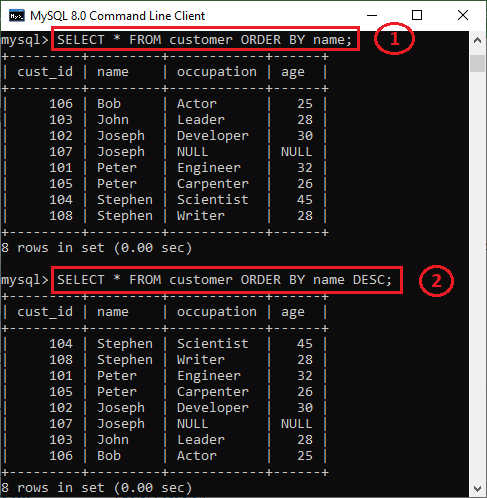
59) Is the following query returns the output?Answer: No. The above query does not return the output because we cannot use the WHERE clause to restrict the groups. We need to use the HAVING clause instead of the WHERE clause to get the correct output. 60) What is the difference between the WHERE and HAVING clauses?The main difference is that the WHERE clause is used to filter records before any groupings are established, whereas the HAVING clause is used to filter values from a group. The below comparison chart explains the most common differences:
To know more differences, click here. 61) How many Aggregate functions are available in SQL?The aggregate function is used to determine and calculate several values in a table and return the result as a single number. For example, the average of all values, the sum of all values, and the maximum and minimum value among particular groupings of values. The following syntax illustrates how to use aggregate functions: SQL provides seven (7) aggregate functions, which are given below:
62) What is SQL Injection?SQL injection is a type of vulnerability in website and web app code that allows attackers to control back-end operations and access, retrieve, and destroy sensitive data from databases. In this technique, malicious SQL statements are inserted into a database entry field, and once they are performed, the database becomes vulnerable to an attacker. This technique is commonly used to access sensitive data and perform administrative activities on databases by exploiting data-driven applications. It is also known as SQLi attack. Some common examples of SQL injection are:
63) What is the difference between the RANK() and DENSE_RANK() functions?The RANK function determines the rank for each row within your ordered partition in the result set. If the two rows are assigned the same rank, then the next number in the ranking will be its previous rank plus a number of duplicate numbers. For example, if we have three records at rank 4, the next rank listed would be ranked 7. The DENSE_RANK function assigns a unique rank for each row within a partition as per the specified column value without any gaps. It always specifies ranking in consecutive order. If the two rows are assigned the same rank, this function will assign it with the same rank, and the next rank being the next sequential number. For example, if we have 3 records at rank 4, the next rank listed would be ranked 5. 64) Is it possible to implicitly insert a row for the identity column?Yes. We can implicitly insert a row for the identity column. Here is an example of doing this: 65) What are SQL comments?Comments are explanations or annotations in SQL queries that are readable by programmers. It's used to make SQL statements easier to understand for humans. During the parsing of SQL code, it will be ignored. Comments can be written on a single line or across several lines.
Advanced SQL MCQ Questions and AnswersThis section provides multiple-choice questions and answers based on advanced query optimization. 1) What type of join do you need when you want to include rows with values that don't match?
Answer: b Explanation: Outer Join returns all rows that match the specified condition, including unmatched rows from one or both tables. Hence, option (B) is the right answer because the outer join is the only join that can display unmatched records. 2) Which of the following option matched a CASE SQL statement?
Answer: a Explanation: The CASE expression is a control flow function that evaluates a set of conditions and displays the output when the first condition is met. It is primarily used to handle conditional statements, same as IF-THEN-ELSE statements in other programming languages. Hence, option (A) is the right answer. 3) Which of the following is an illegal data type in SQL?
Answer: d Explanation: NUMBER data type is used for defining exact or approximate numeric values. CLOB stands for Character Large Object used for storing a large amount of textual data. BLOB stands for Binary Large Object that acts as a reference or pointer to an object such as a file, image, video, etc. LINT is a SQL dialect linter. It highlights mistakes, explains what's wrong with them, why they might be wrong, and what you can do as developers to fix them. Hence option (D) is the right answer. 4) The view is updated immediately if the actual relations used in the view definition change. These views are referred to as _________.
Answer: c Explanation: A materialized view is a table stored on the disk containing the data from the result set of a query. It helps to keep the database up-to-date. Views are called Materialized views when the actual relations used in the view definition change, and the view is updated immediately. 5) The part of SQL that deals with the SQL support constructs are called _______.
Answer: d Explanation: Persistent Storage Module (SQL/PSM) is a feature that allows users to extend the basic SQL functionality with their own additions. 6) Which of the following is true regarding a correlated subquery?
Answer: a Explanation: Correlated subqueries are used for row-by-row processing. It referenced a column in the outer query and evaluated once for each row processed by the outer query (parent statement) such as SELECT, UPDATE, or DELETE statement. On the other hand, uncorrelated subqueries evaluate the subquery first and then determine the processing of the outer query. 7) Whenever a database is modified, the system executes a statement called _________.
Answer: b Explanation: A trigger is a set of SQL queries that reside in a system catalog. It is a special type of stored procedure that is invoked automatically in response to an event. Hence, option (B) is correct because the trigger is a statement that the system executes whenever a database is modified. 8) A transaction starts when
Answer: d Explanation: A transaction has a statement to begin and end both. It starts when one of the following events takes place CREATE, COMMIT, ROLLBACK, etc. Hence option (D) is correct. 9) Which of the below sequential statements cannot be used in a function?
Answer: b Explanation: A function can use any type of sequential statements, such as an IF, CASE, LOOP, NEXT, EXIT, or NULL statement. However, it has one exception: it does not allow to work with WAIT statement because it cannot be used inside a function. The WAIT statement is used to schedule system work. 10) In the data type TIME(p), what does p stands for?
Answer: c Explanation: The SQL TIME data type represents a day's time using a 24-hour clock. The p indicates the number of digits for the fractional part of the seconds. Its value ranges from 0 to 7. If we do not specify the p, it will be 7 by default. Hence option (C) is the correct answer. 11) Which of the following is a privilege in SQL standard?
Answer: d Explanation: A privilege allows users to perform a set of activities on a particular database object. Privileges are divided into two categories:
12) Which of the following indicates another name for referential integrity constraints?
Answer: b Explanation: Referential integrity specify a relation between two tables. Each table must have a primary key. It is also called subset dependencies because the set of foreign key values in table1 of table2 must be a subset of the set of primary key values in table2. 13) Triggers are stored blocks of code that have to be called in order to operate.
Answer: b Explanation: Option (B) is correct because the trigger is a set of SQL statements that resides in system memory with unique names and is executed automatically when a database server event occurs. 14) Outer join is the same as equi-join, except one of the duplicate columns in the result table is removed.
Answer: b Explanation: An equijoin is a join in which the equal comparison operator is used to match the keys of both tables. In contrast, outer join is a join where rows in one table that do not have a matching row in another table are selected with NULL values for the unknown columns. 15) A transaction is a collection of closely related update commands that must all be completed, or none at all, for the database to be valid.
Answer: a Explanation: A transaction is a group of statements to perform single or multiple tasks in a database. Each transaction must happen two things in SQL:
Next Topic#
|
You may also like:
- Java Interview Questions
- SQL Interview Questions
- Python Interview Questions
- JavaScript Interview Questions
- Angular Interview Questions
- Selenium Interview Questions
- Spring Boot Interview Questions
- HR Interview Questions
- C Programming Interview Questions
- C++ Interview Questions
- Data Structure Interview Questions
- DBMS Interview Questions
- HTML Interview Questions
- IAS Interview Questions
- Manual Testing Interview Questions
- OOPs Interview Questions
- .Net Interview Questions
- C# Interview Questions
- ReactJS Interview Questions
- Networking Interview Questions
- PHP Interview Questions
- CSS Interview Questions
- Node.js Interview Questions
- Spring Interview Questions
- Hibernate Interview Questions
- AWS Interview Questions
- Accounting Interview Questions






