Network SegmentationA network infringement is an unavoidable risk when shopping online. Threats are unavoidable, and every system must be capable of withstanding a break-in. One cyber-security method stepped out as particularly effective in mitigating the effects of a network violation. Network segmentation is an information security methodology. During effective data breaches, network segmentation can protect crucial parts of the network. If the structure is breached, this coping mechanism restricts the level of destruction that attackers can induce. This article discusses all of the safety advantages of network segmentation. You'll discover how multi-layer security can withstand assaults and why differentiation is more dependable than plain network architectures. What is Network segmentation?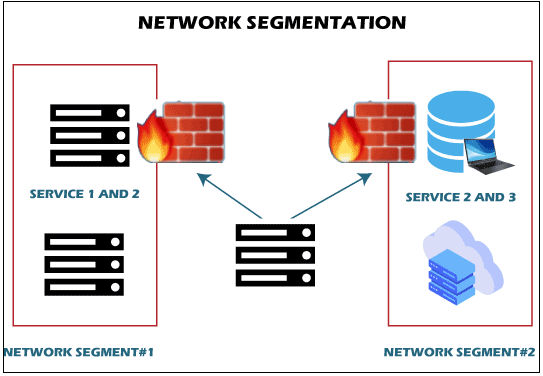
A computer network is segmented when it is divided into smaller components. The goal is to boost system reliability and functionality. Network segregation, network clustering, and network separation are all concepts that often amount to a similar thing. The step is to divide a system into multiple segments is known as network segmentation. These segments are formed by erecting barriers among system components that do not require communication. For example, a corporation may designate a router for its photocopiers or a portion for data storage. When you portion an infrastructure, each router acts as an independent structure with its own set of safety and security regulations. You can direct the supply of network traffic among segments using this network architecture. You can prevent all congestion in one portion from achieving another. Network engineers also utilize network segmentation for scanning information flows depending on the traffic type, origin, or intent. Alienating components of a network decreases the incentive of a risk to move via the structure freely. Many sections of the system are not corrupted if a portion of the channel is violated. Instance of segmentationConsider a large bank with multiple branch locations. The bank's security plan prevents division staff members from having access to its financial reporting process. By mitigating all division's traffic from reaching the banking sector, network segmentation can help implement security procedures. Furthermore, by significantly reducing data traffic, the monetary system can function effectively for the financial experts who utilize it. Types of Network segmentation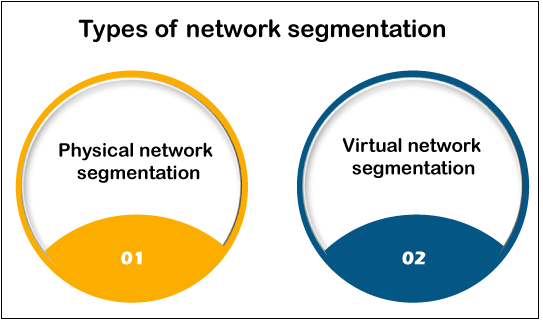
A network can be physically or virtually segmented by network administrators. Let's consider two techniques of segmentation:
Physical segmentation entails dividing a wide network into numerous smaller physical elements. It usually entails purchasing additional equipment, including switching devices, adapters, and routers. While physical network segmentation may appear to be the simplest way to break down a network, it is frequently very expensive and can result in unforeseen effects.
Virtual network segmentation is the most prevalent and cost-effective practice of distributing a network. The same firewall rules are provided by various sections, while switches maintain the VLAN (virtual local area network). Both differentiation techniques have advantages and disadvantages, but the result is the same. You restrict communication channels and make it difficult for a hazard to assault more than one segment. Working of Network segmentationSegmentation appears to work by directing how traffic seeps between the sections. You could select to prevent all traffic in one section from achieving another, or you could restrict the stream depending on the traffic form, origin, location, and a variety of other factors. A differentiation procedure outlines how you determine to section your infrastructure. Segmenting a network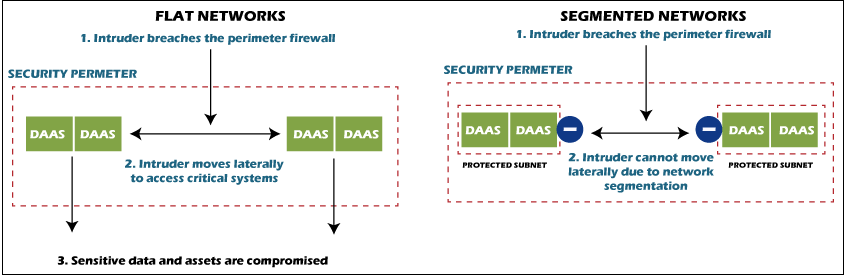
Standard flat networks are easy to maintain, but they do not provide existing surveillance. In a plain network infrastructure, proxy servers evaluate all traffic coming to prevent assaults outside the structure. Hardly anything protects hackers from getting to database systems and crucial systems once they have breached the network's security fence. Flat networks' errors are eliminated by segmentation because there is less heavy traffic on a segmented network, efficiency increases. A differentiated network mitigates regional traffic and decreases the "noise" in-network congestion by having fewer servers per router. Another advantage of network segmentation legislation is that it simplifies regulatory requirements. A system can be divided into areas that contain information that follows the same correct procedures. Different locations limit the requirement of conformance while also simplifying security measures. Prevalent network segmentation use casesIt is all well and nice in theory, but where and how would your subgroup your customer's networks in practice? Here are some typical example situations discussed below.
A customer's guest network could conceivably be both wireless and wired, but nine times out of ten, the host network is solely cordless. By introducing a new visitor SSID and making sure that it is optimized to offer wireless seclusion, you are essentially making a "mini-segment" for each customer of the visitor's Wi-Fi, enabling them to see only the web.
In contrast to visitor networks, which are usually cordless, a voice network is usually wired. Load balancing and attenuation are essential for high voice-over-IP (VoIP), and combining it with conventional internet traffic can degrade call efficiency. Voice networks are typically divided into different voice VLANs with their IP subnet scope.
Is it necessary for every customer and department to have full rights to the test environment? Should your customer's supervisor be capable of pulling updates from the financial statements? On both charges, the answer is most likely 'no.' You can generate a set of related services and clients by dividing customer segments and facilities into their own Layer three network sections or edge routers. What is the legislation that implements segmentation?Internal security systems, and Access Control List (ACL) and Virtual Local Area Network (VLAN) setups on network infrastructure, are examples of cultural classification innovations. These strategies, however, are expensive and difficult. Nowadays, software-defined issues affect enhances network activity segmentation by categorizing and tracking it. It then employs traffic labels to directly enforce differentiation strategy on network devices without the conventional methods' intricacy. Micro-segmentationIn segmentation initiatives, micro-segmentation makes use of a lot more detail, such as user information. It facilitates more granulated and adaptable laws to satisfy the organization's extremely specialized requirements or corporate website. Advantages of Network segmentationAmong all information security methods, segmentation offers the most comprehensive and efficient security. The following are some of the security advantages of network segmentation discussed below: 1. Strong Data SecurityThe more you regulate internet traffic, the simpler it is to prevent critical data. By restricting the range of previously covered that can obtain your information caches, segmentation creates a wall all over them. Lesser segments with network connectivity means fewer crossing points for hackers stealing anything valuable. 2. Threat ReductionIf hackers break into a structural constraint, they are confined to a single router. It takes some time to gain links to the full of structure. While hackers attempt to break into other subnet masks, administrators have time to improve other sections' safety. Once the issue has been contained, administrators can direct their eyes to the violated segment. 3. Control of Limited AccessBy restricting user access to every single part of a larger group, differentiation helps protect against insider threats. The Legislation of Squares Privilege is a safety mechanism. By limiting access to different critical networks to a select small number of people, you restrict the way attackers can gain access to systems. People are the biggest liability in the information security string, so Squares Privileges' Legislation is critical. As per Verizon's 2020 Security Breach Report, malevolent email addresses cause more than two-thirds of malicious software network violations. If a customer's qualifications are taken away or mistreated, a differentiated network will keep trespassers away from sensitive funds. A differentiated network will keep trespassers away from sensitive resources if a user's qualifications are stolen or mistreated. 4. Enhanced Threat Detection and TrackingWith segmentation, you can add more remote monitoring statements. Increasing the number of checks makes it easier to detect suspicious behavior. Sophisticated monitoring also aids in determining the source and context of a problem. Administrators can search for signs of illicit behavior by tracking event logs and electronic conductivity. Realizing how intruders act allows administrators to take a proactive security strategy and protect the main character. 5. Rapid Response TimesAdministrators can react to remote operations more quickly because of different routers. When a threat or error occurs, it is simple to determine which sections are impacted - These perspectives aid in narrowing the scope of debugging. Timely response to remote operations can also enhance the user experience. Clients will not be affected by a structural constraint problem unless a subnet devoted to customers is violated. 6. Damage ManagementNetwork segmentation reduces the impact of a comprehensive security assault. Segmentation keeps the infringement in one router and the rest of the system secured by restricting how far a threat can be stretched. Errors in the network are also stored in a single router. The consequences of a problem are not noticed in other areas, attempting to make the fault easier to manipulate and correct. 7. Safeguard Endpoint DevicesSegmentation maintains unwanted activity away from unsecured edge devices due to repeated load balancing. This advantage of network segmentation is becoming increasingly important as IOT (Internet of things) systems have become more prevalent. Endpoint devices are both a common target and a common primary source for cyber threats. A differentiated network alienates these systems, reducing the overall system's level of harm. Don't Underestimate the Value of Network SegmentationWhile network segmentation is not new, it is also not out of the deadline. Between reducing threat landscape and traffic control, differentiation is one of the most effective ways of detecting crucial infringements. Presently, network segmentation is more of a recommended practice framework than a prerequisite. After all, patterns in companies prone to cybercrime, particularly the Electronic Payment Business, indicate that segmentation may become a required safety mechanism. Whether or not that occurs, the intense competition for nodes for some of the most competitive sectors raises questions about network segmentation's welfare programs.
Next TopicWhat is Bare Metal Server
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









