Vulnerability AssessmentVulnerability Assessment is a process of evaluating security risks in software systems to reduce the probability of threats. The purpose of vulnerability testing is to reduce intruders or hackers' possibility of getting unauthorized access to systems. The vulnerability is any mistake or weakness in the system's security procedures, design, implementation, or internal control that may violate the system's security policy. A vulnerability assessment process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage. Using a risk-based approach, vulnerability assessments may target different technology layers, the most common being host, network, and application-layer assessments. Vulnerability assessments provide security teams and other stakeholders with the information they need to analyze and prioritize potential remediation risks in the proper context. Vulnerability assessments are a critical component of the vulnerability management and IT risk management lifecycles, helping protect systems and data from unauthorized access and data breaches. Organizations of any size, or even individuals who face an increased risk of cyberattacks, can benefit from some form of vulnerability assessment. Still, large enterprises and other organizations subject to ongoing attacks will benefit most from vulnerability analysis. Because security vulnerabilities can enable hackers to access IT systems and applications, enterprises need to identify and remediate weaknesses before being exploited. A comprehensive vulnerability assessment, along with a management program, can help companies improve the security of their systems. Types of Vulnerability AssessmentsVulnerability assessment applies various methods, tools, and scanners to determine grey areas, threats, and risks. Everything depends on how well the given systems' weakness is discovered to attend to that specific need. Below are the different types of vulnerability assessment, such as: 1. Network-based scans It helps identify possible network security attacks. The scan helps zero-in the vulnerable systems on wired or wireless networks. 2. Host-based scans Host-based scans are used to locate and identify vulnerabilities in servers, workstations or other network hosts. This type of scan usually examines ports and services that may also be visible to network-based scans. It also provides excellent visibility into the configuration settings and patch history of scanned systems. 3. Wireless network scans Wireless network infrastructure is scanned to identify vulnerabilities. It helps in validating a company's network. 4. Application Scans It is used to test websites to discover all known software vulnerabilities. It also identifies security vulnerabilities in web applications and their source code by automated scans on the front-end or static or dynamic source code analysis. 5. Database Scans Database Scans aid in identifying grey areas in a database to prevent vicious attacks by cybercriminals. It is identifying rogue databases or insecure environments and classifying sensitive data across an organization's infrastructure. Vulnerability Assessments BenefitsVulnerability assessments allow security teams to apply a consistent, comprehensive, and clear approach to identifying and resolving security threats and risks. This has several benefits to an organization, such as:
Vulnerability Assessment ProcessBelow is the step by step vulnerability assessment process to identify the system vulnerability. 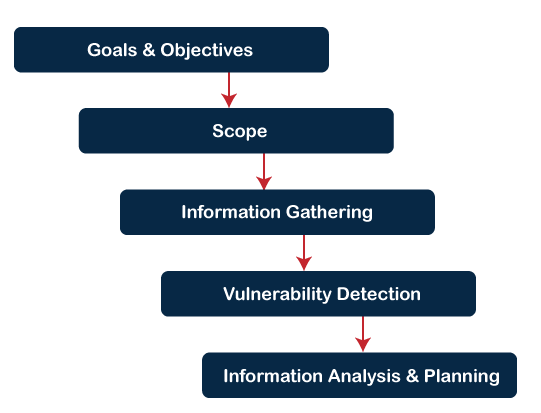
How to do Vulnerability AssessmentFollowing is the steps to do a Vulnerability Assessment, such as: 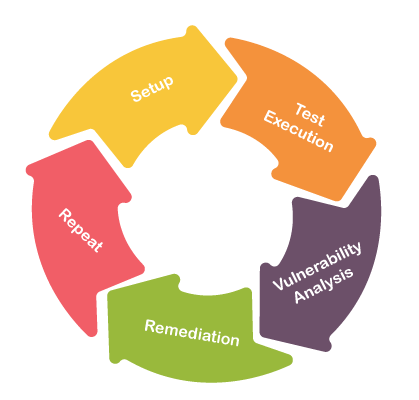
Step 1) Setup: We need to start by determining which systems and networks will be assessed, identifying where any sensitive data resides, and which data and systems are most critical. Configure and update the tools. Step 2) Test Execution: A packet is the data routed unit between an origin and the destination. When any file, such as an e-mail message, HTML file, Uniform Resource Locator (URL) request is sent from one place to another on the internet, the TCP layer of TCP/IP divides the file into several "chunks" for efficient routing. Each of these chunks will be uniquely numbered and will include the Internet address of the destination. These chunks are called packets.
Step 3) Vulnerability Analysis: Now define and classify network or System resources and assign priority to the resources (low, medium, high). Identify potential threats to each resource and develop a strategy to deal with the most prioritized problems. Define and implement ways to minimize the consequences if an attack occurs. Step 4) Remediation: The vulnerability assessment results to patch key flaws or problems, whether simply via a product update or through something more involved, from installing new security tools to an enhancement of security procedures. In step 3, we prioritized the problems that ensure the most urgent flaws are handled first. It's also worth noting that some problems may have so little impact that they may not be worth the cost and downtime required for remediation. Step 5) Repeat: Vulnerability assessments need to be conducted regularly, monthly or weekly, as any single assessment is only a report of that moment in time. These reports give a strong sense of how security posture has developed. Vulnerability Testing MethodsHere are the following vulnerability testing methods, such as:
Next TopicWhat is Phishing
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









