What is Encryption?Encryption helps us to secure data that we send, receive, and store. It can consist text messages saved on our cell-phone, logs stored on our fitness watch, and details of banking sent by your online account. It is the way that can climb readable words so that the individual who has the secret access code, or decryption key can easily read it. For diplomatic information to help in providing data security. A large volume of personal information is handled electronically and maintained in the cloud or on servers connected to the web on an ongoing basis. Without our distinctive data bending up in the networked systematic system of a company, it's almost not possible to go on with the business of any, which is why it is crucial to know how to help in keeping the information private. 
How does it work?It is the procedure of taking ordinary text, such as a text or email, and climbing it into an unreadable type of format known as "cipher text." It helps to protect the digital information either saved on or spread through a network such as the internet on computer systems. The cipher text is converted back to the real form when the calculated recipient accesses the message which is known as decryption. "Secret" encryption key, a lining up of algorithms that climbed and unscramble info. back to a readable type, must be worked by both the sender and the receiver to get the code. 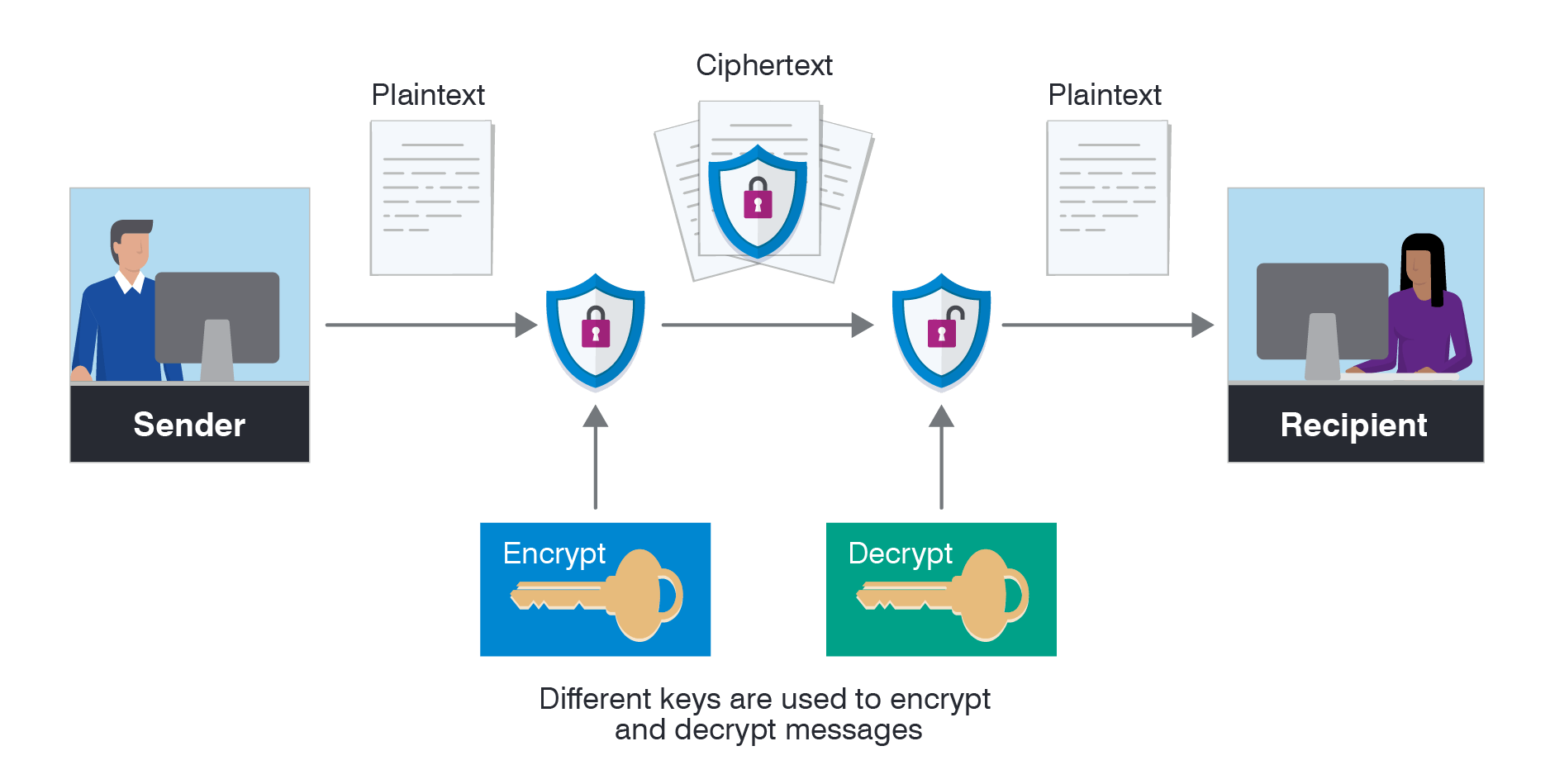
Symmetric and Asymmetric EncryptionThe sequence of numbers used to encrypt and decrypt data is an encryption key. Algorithms are used to construct encryption keys. It's random and special to each key. Symmetric encryption and asymmetric encryption are two kinds of encryption schemes. Here's how distinct they are.
Types of EncryptionThere are various types of encryption, and every encryption type is created as per the needs of the professionals and keeping the security specifications in mind. The most common encryption types are as follows. Data Encryption Standard (DES)The Data Encryption Standard is example of a low-level encryption. In 1977, the U.S. government set up the standard. DES is largely redundant for securing confidential data due to advancements in technology and reductions in hardware costs. Triple DESThe Triple DES works 3* times the encryption of DES. It means, it first encrypts the data, decrypts the data, and again encrypt the data. It improves the original DES standard, which for sensitive data has been considered too poor a form of encryption. RSAThe RSA holds its name from three computer scientists' ancestral initials. For encryption, it utilises a powerful and common algorithm. Because of its main length, RSA is common and thus commonly used for safe data transmission. Advanced Encryption Standard (AES)The U.S. government norm as of 2002 is the Advanced Encryption Standard. Worldwide, AES is used. Two-FishThe Two-fish is exampled as one of the quick encryption algorithms and is of no-cost for anyone to use. It is usable in hardware and software. Using encryption via SSLMost legally sites use very known as "secure sockets layer" (SSL), which, when sent to and from a website, is a procedure of encrypting data. It prevents attackers from accessing the information when it is in transit. To confirm that we practice safe the encrypted online transactions, search the padlock icon in URL bar and the "s" in the "https". Accessing sites using SSL is a good idea if:
Why encryption matters?There are following reasons to use the encryption in our day-to-day life. That are: 1. Internet privacy concerns are realEncryption helps protect our privacy online by translating sensitive information into messages "only for your eyes" intended only for the parties who need them, and no one else. We should make sure our emails sent over an encrypted network, or either message must be in an encrypted format. In their Settings menu, most email clients come with the encryption option and if we check our email with a web browser, take a moment to ensure that SSL encryption is available. 2. Hacking is big businessCybercrime, mostly managed by international corporations, is a global sector. Many of the large-scale thefts of data we might have read about in the news show that cybercriminals are indeed out for financial gain to steal personal information. 3. Regulations demand itThe Portability and Transparency Act for Health Insurance (HIPAA) allows healthcare providers to incorporate safety features that help secure online confidential health information for patients. The Fair Credit Practices Act (FCPA) and related regulations that help protect customers must be enforced by retailers. Encryption allows companies to remain consistent with regulatory guidelines and specifications. It also helps secure their clients' valuable data. How ransomware uses encryption to commit cybercrimes? Encryption is intended to secure our data, but it is also possible to use encryption against us. Targeted ransomware, for example, is a cybercrime that can impact organisations, including government agencies, of all sizes. Also, ransomware can attack individual users of computers. How do attacks involving ransomware occur? In order to attempt to encrypted different devices, including computers and servers, attackers deploy ransomware. Until they give a key to decrypt the encrypted data, the attackers also demand a ransom. Ransomware attacks on government departments can shut down facilities, making it impossible, for example, to obtain a permit, obtain a marriage licence, or pay a tax bill. Targeted attacks mostly target large organisations, but we can also experience ransomware attacks. Some ways we must always keep in our mind to be safe from such attacks.
Consider making use of cloud resources. It can help to prevent a ransomware infection, since previous versions of files are maintained by several cloud providers, enabling us to 'roll back' to the unencrypted type. Don't pay any ransom. In the hope of getting our files back, we might pay a ransom, but we might not get them back. There's no assurance that our data will be released by cybercriminals. To help protect our confidential personal details, encryption is important. But it can be used against us in the event of ransomware attacks. Taking steps to help us reap the benefits and prevent the damage is wise. How is encrypted data deciphered?With the support of a key, an algorithm, a decoder or something similar, the intended recipient of the encrypted data will decrypt it. If the data and the encryption process are in the digital domain, the intended user may use the necessary decryption tool to access the information they need. For decryption purposes, the item used can be referred to as the key, cipher or algorithm. We will find specific details about each of them below. Cipher: The word cipher refers to an algorithm primarily used for the purposes of encryption. A cipher consists of a series of successive steps at the end of which it decrypts the encrypted information. Two major types of ciphers exist: stream ciphers and block ciphers. Algorithm: The processes that are followed by the encryption processes are algorithms. There are various types of algorithms that are explicitly used to decrypt encrypted files and data: some of these types include blowfish, triple DES and RSA. In addition to algorithms and ciphers, it is possible to use brute force to decode an encoded text.
Next TopicWhat is Project Management
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









