What is Security Operation Center?A Security Operation Center (SOC) is a team of expert individuals who dedicate themselves to high-quality IT security operations. A SOC seeks to prevent cybersecurity threats, detects and responds to any incident on the computers, servers and networks it oversees. SOC has a unique ability to monitor all systems on an ongoing basis, as employees work in shifts, rotating and logging activity around the clock. As opposed to a traditional IT department, a SOC staff includes highly experienced cybersecurity analysts and trained engineers. These individuals use various computer programs and specialized security processes to point weaknesses in the company's virtual infrastructure and prevent these vulnerabilities from leading to theft. The technologies SOCs employ include an arsenal of firewalls, probes, security information, event management systems and monitor data as it moves across the various platforms. The SOC team stays ahead of potential threats by analyzing active feeds, establishing rules, identifying exceptions, enhancing responses and vulnerabilities in the defenses they have already set up. With various tasks to perform, SOCs can look different depending on many factors using various tech and methods. Some companies have an in-house SOC, while others pick to outsource these services. However, they all have the primary goal of preventing breaches and minimizing losses due to online criminal activity. Functions of SOCHere are the following main functions performed by the security operation center, such as: 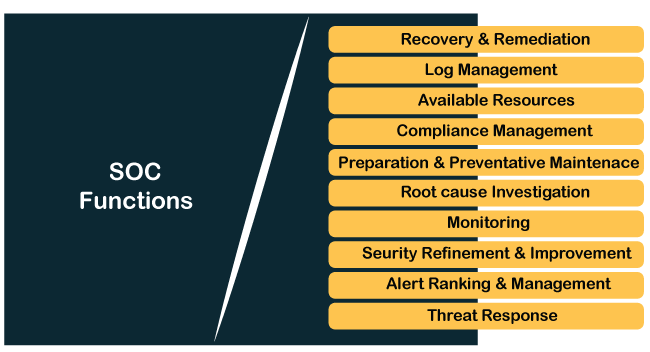
1. Take Stock of Available Resources The SOC is responsible for two types of assets, the various devices, processes and applications. They are charged with safeguarding and the defensive tools at their disposal to help ensure this protection.
2. Preparation and Preventative Maintenance Even the most well-equipped and agile response processes are no match for preventing problems from occurring in the first place. To help keep attackers at bay, the SOC implements preventative measures, this can be divided into two main categories:
3. Continuous Proactive Monitoring Tools used by the SOC scan the network to flag any abnormalities or suspicious activities. Monitoring the network around the clock allows the SOC to be notified immediately of emerging threats, giving them the best chance to prevent or mitigate harm. Monitoring tools can include a SIEM or an EDR, the most advanced of which can use behavioral analysis to "teach" systems the difference between regular day-to-day operations and actual threat behavior, minimizing the amount of triage and analysis be done by humans. 4. Alert Ranking and Management When monitoring tools issue alerts, it is the responsibility of the SOC to look closely at each one, discard any false positives, and determine how aggressive any actual threats are and what they could be targeting. This allows them to triage emerging threats appropriately, handling the most urgent issues first. 5. Threat Response An incident is confirmed. The SOC acts as a first responder, performing actions such as shutting down or isolating endpoints, terminating harmful processes or preventing them from executing, deleting files, and more. The goal is to respond to the extent necessary while having as small an impact on business continuity as possible. 6. Recovery and Remediation In the outcome of an incident, the SOC will work to restore systems and recover any lost or compromised data. This may include wiping and restarting endpoints, reconfiguring systems. When successful, this step will return the network to the state before the incident. 7. Log Management The SOC is responsible for collecting, maintaining, and regularly reviewing the log of all network activity and communications for the entire organization. This data helps define a baseline for "normal" network activity, can reveal the existence of threats, and can be used for remediation and forensics in the aftermath of an incident. Many SOCs use a SIEM to aggregate and correlate the data feeds from applications, firewalls, operating systems and endpoints, producing their internal logs. 8. Root Cause Investigation In the outcome of an incident, the SOC is responsible for figuring out exactly what happened when, how and why. During this investigation, the SOC uses log data and other information to trace the problem to its source, which will prevent similar problems from occurring in the future. 9. Security Refinement and Improvement Cybercriminals are constantly refining their tools, tactics, and to stay ahead of them, the SOC needs to implement improvements continuously. The plans outlined in the Security Road Map come to life during this step, but this refinement can also include hands-on practices such as red-teaming and purple-teaming. 10. Compliance Management Many of the SOC's processes are guided by established best practices, but compliance requirements govern some. The SOC is responsible for regularly auditing their systems to ensure compliance with such regulations, which may be issued by their organization, by their industry, or by governing bodies. These regulations include HIPAA, PCI DSS and GDPR. Acting under these regulations not only helps safeguard the sensitive data that the company has been entrusted with. It can also shield the organization from reputational damage and legal challenges resulting from a breach. How to build a SOCThe following steps help to build a great Security Operation center, such as: Step 1: Develop the strategy Start by assessing the organization's existing SOC capabilities in terms of people, processes, and technologies. Stick to SOC's four major operations, such as monitoring, detection, response, and recovery. To effectively discharge the duties, the team should create a strategy that considers business objectives. For example, identifying which systems and data are vital for sustaining operations to keep the business afloat will help determine the SOC team's priorities. Step 2: Design a solution Instead of relying on a broad-function SOC solution, limiting the scope to the organization's situation is a best practice. When designing your SOC, be on the lookout for scope creep to keep it scalable to meet future needs. A focused solution reduces the amount of time invested in implementation and achieves quick results. The design should include:
Step 3: Create procedures, processes and training The SOC solution must follow the six phases of the Threat Lifecycle Management (TLM) framework: forensic data collection, the discovery of potential threats, and the qualification of discovered threats to assess the potential impact on the business, investigation, threat neutralization, and recovery. In the case of a hybrid or outsourced SOC model, coordinate with the service provider. Step 4: Prepare the environment Check whether all the required elements are in place before deploying the solution. Key elements include remote access mechanisms, strong authentication for remote access, and SOC staff equipment protection. Step 5: Implement the solution To execute the solution, you must
Once done, check the alignment of systems with the workflow. Step 6: Deploy end to end-use cases Next, deploy use cases that focus on end-to-end threat detection and response realization. It should be implemented across the analytics tier, security automation, and orchestration tier. Test all forms of the automation solution rigorously. Furthermore, verify the readability and security of the remotely accessed solution. Step 7: Maintain and evolve the solution The solution will require continuous maintenance and updating at regular intervals. Updating based on how the SOC functions in the organization's environment will increase the SOC solution's efficiency and threat detection rate. How a SOC Works
Types of Soc ModelsWe have been focused on an external SOC processor model where the company is paying for an outside SOC provider to manage their cybersecurity needs. However, there are several other SOC architecture models. 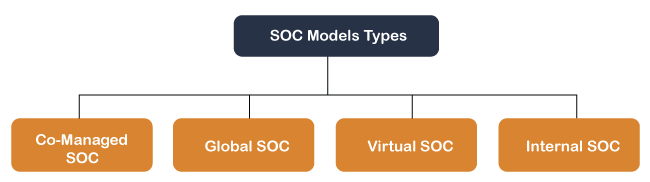
SOC OperationsIndividual SOC cybersecurity providers offer different suites of products and services. However, a core set of operational functions that a SOC must perform to add value for an organization. We have termed these as the seven competencies and will outline them here. 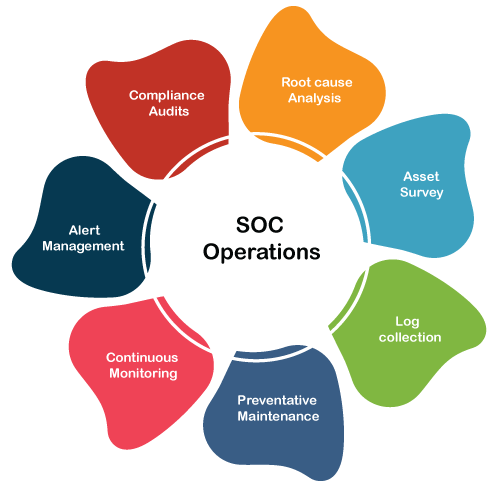
1. Asset Survey: For a SOC to help a company stay secure, they must have a complete understanding of what resources they need to protect. Otherwise, they may not be able to protect the full scope of the network. An asset survey should identify every server, router, firewall under enterprise control, and any other cybersecurity tools actively in use. 2. Log Collection: Data is the most important thing for a SOC to function properly, and logs serve as the key source of information regarding network activity. The SOC should set up direct feeds from enterprise systems so that data is collected in real-time. Humans cannot digest such large amounts of information, which is why log scanning tools powered by artificial intelligence algorithms are so valuable for SOCs. However, they do pose some interesting side effects that humanity is still trying to iron out. 3. Preventative Maintenance: The SOC can prevent cyberattacks from occurring by being proactive with their processes. This includes installing security patches and adjusting firewall policies regularly. Since some cyberattacks begin as insider threats, a SOC must also look within the organization for risks. 4. Continuous Monitoring: To be ready to respond to a cybersecurity incident, the SOC must be vigilant in its monitoring practices. A few minutes can be the difference between blocking an attack and letting it take down an entire system or website. SOC tools run scans across the company's network to identify potential threats and other suspicious activity. 5. Alert Management: Automated systems are great at finding patterns and following scripts. But the human element of a SOC proves it's worth when it comes to analyzing automated alerts and ranking them based on their severity and priority. SOC staff must know what responses to take and how to verify that an alert is legitimate. 6. Root Cause Analysis: After an incident occurs and is resolved, the SOC's job is just beginning. Cybersecurity experts will analyze the root cause of the problem and diagnose why it occurred in the first place. This feeds into continuous improvement, with security tools and rules modified to prevent future occurrences of the same incident. 7. Compliance Audits: Companies want to know that their data and systems are safe and managed in a lawful manner. SOC providers must perform regular audits to confirm their compliance in the regions where they operate. SOC RolesSOC provider is a perfect place to build a career. Let's run through some of the primary positions involved in running a SOC. 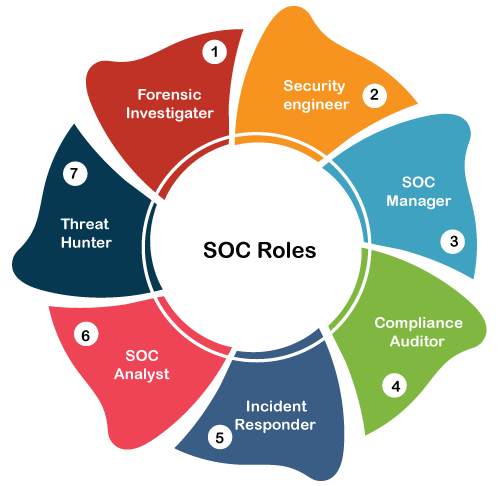
1. SOC Manager SOC Managers are the leaders of their organization. The means top-level responsibilities fall to them, including hiring or firing, budgeting, and setting priorities. They typically report directly to the executive level, especially the chief information security officer (CISO). 2. Compliance Auditor The compliance auditor plays a key role in the standardization of processes within a SOC. They essentially function as the quality control department, ensuring that SOC members. 3. Incident Responder Incident Responders are the people who are paid to react to alerts as soon as possible. They use a wide range of monitoring services to rank the severity of alerts, and once one has been deemed a full-scale issue, they engage with the affected enterprise to begin recovery efforts. 4. SOC Analyst The SOC analysts are responsible for reviewing past incidents and determining the root cause behind them. They typically have many years of experience in the cybersecurity profession. 5. Threat Hunter These are the team's proactive members who run tests across a network to identify areas of weaknesses. The goal is to find vulnerabilities before a hacker can exploit them with an attack. 6. Forensic Investigator The forensic investigator is in charge of identifying the root cause, locating all attacks' sources, and collecting supporting evidence. 7. Security Engineer A security engineer develops and designs systems or tools necessary to carry out effective intrusion detection and vulnerability management capabilities. Benefits of Security Operations CenterWhen implemented correctly, a security operations center can provide an organization with several benefits, such as:
Next TopicWhat is Smallpox
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









