What is SIEM Tool?SIEM stands for Security information and event management. SIEM is an approach to security management that combines security information management (SIM), and security event management (SEM) functions into one security management system. The acronym SIEM is pronounced SIM with a silent e. SIEM is a software solution that aggregates and analyzes activity from many different resources across the entire IT infrastructure. SIEM collects security data from network devices, servers, domain controllers, and more. It stores, normalizes, aggregates, and applies analytics to that data to discover trends, detect threats, and enable organizations to investigate any alerts.
The underlying principles of every SIEM system are to aggregate relevant data from multiple sources, identify deviations from the norm and take appropriate action. For example, when a potential issue is detected, a SIEM system might log additional information, generate an alert and instruct other security controls to stop an activity's progress. A SIEM system can be a rules-based statistical correlation engine to establish relationships between event log entries. Advanced SIEM systems have evolved to include user and entity behavior analytics (UEBA) and security orchestration, automation and response (SOAR). SIEM systems work by hierarchically deploying multiple collection agents to gather security-related events from end-user devices, servers and network equipment, and specialized security equipment, such as firewalls, antivirus or intrusion prevention systems (IPS). The collectors forward events to a centralized management console, where security analysts sift through the noise, connecting the dots and prioritizing security incidents. The security information and event management process can be broken down as follows:
How Does SIEM Work?SIEM software collects and aggregates log data generated throughout the organization's technology infrastructure, from host systems and applications to network and security devices such as firewalls and antivirus filters. The software then identifies and categorizes incidents and events, as well as analyzes them. SIEM provides two primary capabilities, such as:
At its core, SIEM is a data aggregator, search, and reporting system. SIEM gathers immense amounts of data from the entire networked environment, consolidates and makes that data human accessible. Benefits of SIEMHere are some benefits of using SIEM, such as:
SIEM ToolsThere is several security information and event management tools in the IT market which have been around for more than a decade. SIEM tools are the most effective way for organizations to protect sensitive data. Larger enterprises are the primary customers for SIEM tools since they are the most likely to require IT oversight. However, small and mid-sized businesses (SMBs) can still enjoy the benefits of SIEM capabilities, often through a partnership with a managed service provider (MSP). The best SIEM tools are adept at using past trends to differentiate between actual threats and legitimate use, enabling you to avoid false alarms while ensuring optimal protection. 1. SplunkSplunk Enterprise Security is a popular option that has been around for over a decade. As the name implies, this is an enterprise-level option, which means the licensing costs are not particularly competitive. This tool may be too pricey. We can get this tool as on-premises software or as a SaaS solution. The dashboard has useful visualizations, such as graphs and charts. 
It provides real-time threat monitoring, rapid investigations using visual correlations and investigative analysis to trace the dynamic activities associated with advanced security threats. The Splunk SIEM is available as locally installed software or as a cloud service. It supports threat intelligence feed integration from third-party apps. 2. IBM QRadarIBM QRadar collects log data from sources in an enterprise's information system, including network devices, operating systems, applications and user activities. The QRadar SIEM analyzes log data in real-time, enabling users to quickly identify and stop attacks. 
QRadar can also collect log events and network flow data from cloud-based applications. This SIEM also supports threat intelligence feeds. QRadar is another popular SIEM tool that can deploy as a hardware appliance, a virtual appliance, or a software appliance, depending on the organization's needs and capacity. QRadar can integrate with Varonis to add Advanced Threat Detection capabilities. Businesses looking to integrate a wide range of logs across their critical systems will likely find QRadar reliable. This IBM product has smart features that catch a diversity of ever-changing threats. It is not necessarily the most intuitive product, as it has a complex architecture to match its capabilities. 3. ArcSightArcSight has an open architecture, which gives it a few standout capabilities. This tool can consume data from a wider range of sources than many SIEM products, and its structured data can be used outside of ArcSight, which may be useful for more expert IT teams. It collects and analyzes log data from an enterprise's security technologies, operating systems and applications. Once a malicious threat is detected, the system alerts security personnel. 
ArcSight can also start an automatic reaction to stop malicious activity. Another feature is the ability to integrate third-party threat intelligence feeds for more accurate threat detection. 4. SolarWinds Security Event ManagerSolarWinds Security Event Manager provides all the log management features, such as security event-time correlation, compliance reporting, and advanced analytics features. 
It is built for businesses that are specifically looking for robust log monitoring and better prioritization and response for incident management. We can also use the tool's file integrity checker to track access and other changes made to files and folders. This tool customizes and improves security with data encryption, SSO/smart card integration, and the ability to block IPs, applications, and USBs as needed. 5. SolarWinds Threat MonitorSolarWinds Threat Monitor is a powerful security-focused SIEM solution that analyzes security log info across various sources and cross-checks anomalies against a continuously updated global threat database. This tool gives automated, intelligent responses to security events with comprehensive alerts. 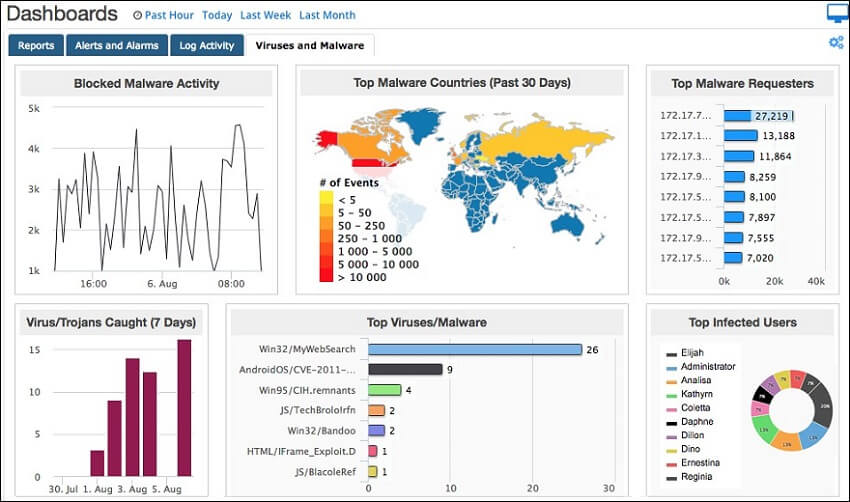
The tool is available for both on-premises or in the cloud. It comes with a year of archival log space and indexed log capabilities for easier normalization and search. It also comes with a 14 days free trial, with the cloud version being a very popular choice for MSPs. 6. LogRhythmLogRhythm NextGen SIEM is a solid, fast option for critical log management on Windows. The tool is easy to deploy for trained IT staff, and the dashboard helps simplify workflow. If we have specific compliance standards and know the queries, it is quick to configure the reports. 
This tool has rapidly-evolving AI and automation features. This platform does not scale, particularly for larger businesses, and there is limited support if we need to expand into cloud environments. 7. AlienVault Unified Security ManagementAlienVault unified security management tool is an option for SMBs looking for an entry-level SIEM product, and it can be implemented on both Mac and Windows. This tool doesn't offer the breadth of features of leading competitors. It recently added endpoint detection and new response capabilities. 
8. RSA NetWitness SuiteRSA NetWitness Suite is another option for log management and threat intelligence. This tool allows for robust threat analysis. 
It can recreate full sessions to see exactly what happened during an attack and get insight into hackers' strategy with automated behavioral analytics. This tool is on the upper end of the pricing spectrum to be more appropriate for enterprises. 9. Sumo LogicThis tool is a new cloud-based platform appropriate for both cost and features for SMBs. Since the product is new, there isn't much of a community base in place, but Sumo Logic claims its product fills gaps in IT security that other products have missed, especially when it comes to cloud deployments. 
NOTE: This tool seems to have more of a technical user in mind, so the design features aren't as appealing.10. McAfee Enterprise Security ManagerThis is a familiar tool, but be warned that other McAfee products have been discontinued in the past. The product's log sharing with tools from other vendors isn't straightforward. 
If you are already implementing other McAfee products like their famed antivirus software, it may make sense to choose a McAfee SIEM solution to streamline your operations. In any case, selecting this solution will get basic dashboard management and reporting capabilities. 11. SecuronixSecuronix is a rare SIEM tool that is easy to use for users and advanced security teams. The Securonix is a Full-featured tool with strong behavioral and data monitoring. 
Securonix ties up with LogRhythm and IBM to managed Value, Deployment, Ease of Use and Detection, with Response and Management right behind. The cloud-delivered service is priced based on the number of employees, making it one of the simpler pricing schemes in a market where data and incident volume predominate. 12. FortinetFortinet tool is a good choice for those who want strong security, particularly for existing Fortinet customers. 
Fortinet tool has undergone more third-party testing than any other vendor on this list. Its breach and intrusion prevention, gateways and EDR capabilities have all been tested by NSS Labs. Fortinet SIEM tool scored highest in Detection, Response and Management. Users are high on the SIEM product's real-time monitoring capabilities, with behavioral monitoring being one area, the product could improve. SIEM Tools MethodologyWe analyzed third-party test data, user reviews, product features, analyst reports, resellers, and vendor-supplied pricing. Here is an explanation of rating categories, such as:
Next TopicFile extensions
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









