What is Pen Test?Pen Testing or Penetration Testing is a type of security testing used to uncover vulnerabilities, threats, and risks that an attacker could exploit in web or network applications and software applications. In the context of web application security, penetration testing is commonly used to augment a web application (WAF). The purpose of penetration testing is to identify and test all possible security vulnerabilities present in the software application. Vulnerability is the risk that an attacker can gain authorized access to the system data. Vulnerabilities are usually introduced by accident during the software development and implementation phase. Common vulnerabilities include configuration errors, design errors, software bugs etc. Penetration Analysis depends upon two mechanisms, such as Vulnerability Assessment and Penetration Testing (VAPT). Penetration testers use the same tools, techniques, and processes as attackers to determine the business impacts of weaknesses in the systems. Penetration tests usually simulate a variety of different attacks that could threaten the business. A pen test might examine a system that is robust enough to resist attacks from authenticated and unauthenticated positions, as well as a range of system roles. Redscan is an award-winning provider of cybersecurity penetration testing services. Our range of CREST penetration testing engagements helps organizations to effectively manage cybersecurity risk by identifying, safely exploiting, and helping to remediate vulnerabilities that could otherwise lead to data and assets being compromised by malicious attackers. The main objective of penetration testing is to identify security weaknesses. Penetration testing can also be used to test an organization's security policy, employee's security awareness and the organization's ability to identify and respond to security incidents. The information about security weaknesses identified through pen testing is aggregated and provided to the organization's IT and network system managers, enabling them to make strategic decisions and prioritize remediation efforts. Types of Penetration TestingThe type of penetration test selected usually depends on the scope and whether the organization wants to simulate an attack by an employee, Network Admin (Internal Sources) or by External Sources. There are three types of Penetration testing, such as: 
1. White Box Testing: In a white-box penetration testing, the tester is usually provided with complete information about the network or systems to be tested, including the IP address schema, source code, OS details, etc. This can be considered as a simulation of an attack by any internal sources. 2. Black Box Testing: In black-box penetration testing, a tester does not know the systems tested. The tester is responsible for collecting information about the target network or system. 3. Grey Box Testing: In a grey box penetration testing, a tester is provided with partial knowledge of the system. It can be considered as an attack by an external hacker who had gained illegitimate access to an organization's network infrastructure documents. Areas of Penetration TestingPenetration testing is usually done in the following areas, such as:
Phases of Penetration TestingPen testers aim to simulate attacks carried out by motivated adversaries. To do so, they typically follow a plan that includes the following steps: 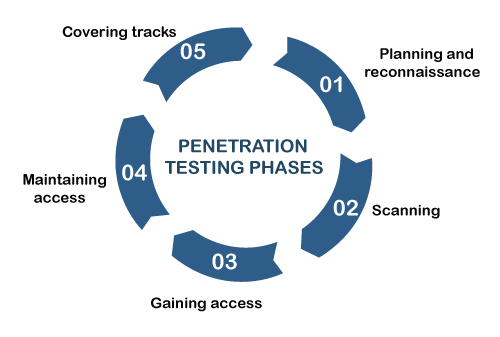
1. Planning and Reconnaissance: Gather as much information about the target as possible from public and private sources to inform the attack strategy. Sources include internet searches, domain registration information retrieval, social engineering, nonintrusive network scanning, and dumpster diving. This information helps the pen tester map out the target's attack surface and possible vulnerabilities. Reconnaissance can vary with the pen test's scope and objectives and might be as simple as making a phone call to walk through a system's functionality. 2. Scanning: The pen tester uses tools to examine the target website or system for weaknesses, including open services, application security issues, and open source vulnerabilities. Pen testers use a variety of tools based on what they find during reconnaissance and during the test. 3. Gaining access: Attacker motivations vary from stealing, changing, or deleting data to moving funds to simply damaging the reputation. To perform each test case, pen testers must decide on the best tools and techniques to gain access to the system, whether through a weakness, such as SQL injection, or malware, social engineering, or something else. 4. Maintaining access: Once pen testers gain access to the target, their simulated attack must stay connected long enough to accomplish their goals. It's about demonstrating the potential impact. 5. Covering Tracks: The attacker must clear any trace of compromising the victim system, any data gathered, log events to remain anonymous. Once an attacker has exploited one vulnerability, they may gain access to other machines, so the process repeats, i.e., looking for new vulnerabilities and exploiting them. This process is referred to as pivoting. Penetration Testing ToolsPen testers often use automated tools to uncover common application vulnerabilities. Penetration tools scan code to identify malicious code in applications that could result in a security breach. Pen testing tools examine data encryption techniques and can identify hard-coded values, such as usernames and passwords, to verify security vulnerabilities in the system. Penetration testing tools should:
Many of the most popular penetration testing tools are free or open-source software; this gives pen-testers the ability to modify or otherwise adapt the code for their own needs. Some of the most widely used free or open-source pen-testing tools include:
Penetration testers use the same tools that black hat hackers use because they are well-documented and widely available and help the pen testers better understand how they can be wielded against their organizations. Penetration Testing MethodsOne important aspect of any penetration testing program is defining the scope within which the pen testers must operate. The scope defines what systems, locations, techniques and tools can be used in a penetration test. Below are several of the main pen test strategies used by security professionals, such as: 
Pen Testing Vs. Automated TestingPen testing is mostly a manual effort. Pen testers do use automated scanning and testing tools in the process. But they also go beyond the tools and think their way through security barriers using their knowledge of the latest attack techniques to provide more in-depth testing than a vulnerability assessment, i.e., automated testing can provide. Here are a few comparative advantages of manual pen testing and automated testing: Manual Pen Testing Pen testing uncovers vulnerabilities and weaknesses not found in popular lists and tests business logic that automated testing can overlook, e.g., data validation, integrity checks. Also, a manual pen testing review can help identify false positives reported by automated testing. Manual pen testers are experts who "think" like adversaries and analyze data to target their attacks and test systems and websites in ways automated testing solutions following a scripted routine cannot. Automated Testing Automated testing generates results faster and needs fewer specialized professionals than a fully manual pen testing process. Automated testing tools track results automatically and can sometimes export them to a centralized reporting platform. Also, while the results of manual pen tests might vary from test to test, running automated testing repeatedly on the same system will produce the same results. Advantage and Disadvantage of Pen TestingWith the frequency and severity of security breaches increasing day by day, organizations have never had a greater need for visibility into how they can withstand attacks. Regulations such as PCI DSS and HIPAA mandate periodic pen testing to remain current with their requirements. Here are some advantages and disadvantages for this type of defect discovery technique, such as: Advantages
Disadvantages
Next TopicWhat is SIEM Tool
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









