Vulnerability Assessment and Scanning ToolsWhat is Vulnerability AssessmentIn information technology, a vulnerability evaluation is the systematic analysis of security vulnerabilities. It examines if the system is vulnerable to any security vulnerabilities, defines severity levels to such vulnerabilities, and, if and whenever appropriate, recommends abatement or mitigation. In any device that fixes possible vulnerabilities, vulnerability testing or vulnerability evaluation is a systematic method of discovering security loopholes. Here, we have some examples of threats that vulnerability assessment can eliminate are:
Purpose of Vulnerability AssessmentThe objective of vulnerability analysis is to prohibit unauthorized access to an information system from being possible. The confidentiality, credibility, and availability of the system are protected by vulnerability checking. The method extends to all machines, networks, network devices, apps, cloud computing, web applications, etc. 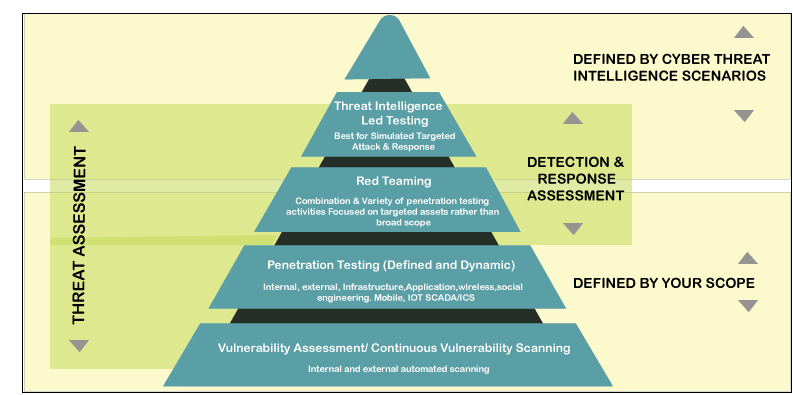
Categories of Vulnerability ScannerScanners of vulnerabilities contain their methods of working. Based on how they work, we can categorize the vulnerability scanners into three categories. They are defined below. 1. Vulnerability Scanner based on HostIt is used on a dedicated server or machine to identify vulnerabilities such as an individual computer or a local network such as a connection or core-router Analysis of sensitive systems which, if not adequately tested or not created from a validated device image, can be susceptible to the attacks. 2. Vulnerability Scanner based on CloudIt is used inside cloud-based frameworks such as enterprise applications, WordPress, and Joomla to identify vulnerabilities. Detection of privacy risks in web applications and their encryption keys by means of robotic front-end or static/dynamic system software reviews are scanned. 3. Vulnerability Scanner based on DatabaseThis type of vulnerability scanner used for identifying bugs in applications for database management. Databases are the foundation of every confidential information processing system. To avoid attacks like SQL Injection, vulnerability scanning is implemented on database management systems. Analysis of vulnerabilities and configuration issues of databases or big data systems, detection of unauthorized databases or vulnerable dev/test settings, and classification of sensitive data across the infrastructure of an enterprise is analyzed. 4. Vulnerability Scanner based on NetworkThis type of vulnerability scanner is used when you're searching for open ports to identify vulnerabilities in a local network. With the support of the method, services running on open ports decide whether or not vulnerabilities occur. Evaluation of policies and procedures aimed at preventing unauthorized access to private or public networks and services available by the network. Vulnerability Assessment ToolsVulnerability assessment tools lead to multiple methods of detecting vulnerabilities in application domains. Vulnerability tools for code analysis analyze coding glitches. Excellently-known rootkits, backdoors, and Trojan Horses can be discovered in audit vulnerability toolkits. In the industry, there are several vulnerability scanners obtainable. They can be freely accessible, charged, or open-source. On GitHub, many free and open-source tools have been developed. Choosing which tool to use depends on a variety of variables, such as the category of security vulnerabilities, the cost estimate, how often the tool is modified, etc. Here, we have discussed some of the best vulnerability scanning tools. They are- 1. OpenVASOpenVAS is a valuable tool for detecting vulnerabilities that endorses massive scale scans that are appropriate for companies. This tool can be used not only in web applications or application server, but also in databases, programming systems, networks, and virtualization software to diagnose vulnerabilities problems. OpenVAS provides frequent updates, which widens the exposure of vulnerability detection. It also assists in assessing the risk and demonstrates preventive measures for the identified vulnerabilities. 2. Nikto2Nikto2 is a screening program for open-source exploits that emphasizes on web application security. Nikto2 will discover about 6700 hazardous archives that cause web server problems and evaluate iterations based on inaccurate servers. In addition, Nikto2 can immediately notify you to server installation problems and improve virtual server audits in a minimal amount of time. Nikto2 might not offer any preventative measures for potential vulnerabilities that include risk management functionality. Nikto2, after all, is a constant accessed tool that allows vulnerabilities to be covered more broadly. 3. NetsparkerNetsparker is also a vulnerability assessment tool for web applications with an optimization feature provided for vulnerability seeking. This tool is also smart enough to find vulnerabilities within the next few hours in millions of web application domains. It has many additional features, but it is a charged enterprise-level vulnerability tool. It has slithering innovation that, through crawling into the system, discovers vulnerabilities. Netsparker will identify and recommend mitigation strategies for vulnerabilities reported. Also, security tools are available for comprehensive vulnerability evaluation. 4. AcunetixAcunetix is a commercial (open-source edition also obtainable) web application vulnerability scanner with several features offered. With the help of this tool, there is a mapping range of about 6500 vulnerabilities. It can also discover network vulnerabilities as well, in additament to web services. Acunetix offers the opportunity for your scan to be streamlined. It is suitable for large-scale organizations because several systems can be controlled by it. HSBC, NASA, USA air force are few industrial titans that use the Arachni scanning tool for vulnerability testing. 5. ArachniFor application development, Arachni is also a deeply committed vulnerability tool. A number of vulnerabilities are protected by this tool and are inspected periodically. Arachni offers risk management services and recommends suggestions and defensive measures for vulnerabilities that have been identified. Linux, Windows, and macOS are supported by Arachni, a freely used and open-source security vulnerabilities tool. With its capacity to adapt with recently discovered vulnerabilities, Arachni also aims to assist in penetration testing. 6. NmapAmong many cybersecurity experts, Nmap is one of the possibly the best-known, freely used and open-source testing tools for networks. To explore hosts in the domain and for software exploration, Nmap uses the penetrating technique. In two or more distinct networks, this function aims to detect exploits. If you really are a beginner or trying to learn to search for vulnerabilities, then the Nmap scanning tool is a great starting point. 7. W3AFW3AF is a platform also called Web Software Attack and Framework, open and free-source. This software is an open-source web application analysis for vulnerabilities. By identifying and evaluating the bugs, it provides a mechanism that is useful to protect the web application. This software is recognized for user-friendliness. W3AF also has infiltration services used for vulnerability assessment work, along with penetration testing options. W3AF contains a broad-scale set of vulnerabilities. This tool can be selected for networks that are attacked repeatedly, particularly with previously unrecognized vulnerabilities. 8. GoLismeroGoLismero is a tool used for intrusion prevention that is free and open-source. GoLismero aims to identify web application threats and vulnerabilities, but can also search for network vulnerabilities. GoLismero is an efficient tool that works with outcomes obtained by other vulnerability tools such as OpenVAS, then consolidates the findings and gives feedback. A broad variety of vulnerabilities, including storage and network vulnerabilities, are protected by GoLismero. GoLismero also supports preventative measures for discovered vulnerabilities. 9. IntruderThe Intruder is a paid vulnerability scanner explicitly designed for cloud-based storage scanning. Immediately after a vulnerability is released, intruder software begins to search. The scanning mechanism in Intruder is automated and constantly monitors for vulnerabilities. Since it can sustain many equipment, Intruder is appropriate for enterprise-level intrusion detection. In contrast to cloud-based testing, Intruder can help to identify network vulnerabilities and also provide feedback and recommendations on efficiency. 10. OpenSCAPOpenSCAP is an application of tools that help search for vulnerabilities, analyze vulnerabilities, calculate vulnerabilities, and build protection measures. OpenSCAP is a platform developed by groups that are free and open source. Only the Linux operating system supports OpenSCAP. The OpenSCAP platform supports web apps, web-based applications, databases, operating systems, networks, and virtualization software for vulnerability scanning. In addition, it provides a risk evaluation service and endorses to counterbalance the threats. 11. AircrackAircrack, also called Aircrack-NG, is a series of software used to test the security of the wireless network. These tools may be used to inspect networks and enable different operating systems, such as Linux, OS X, Solaris, NetBSD, Windows, and much more. The tool will concentrate on several areas of Wi-Fi privacy, such as traffic and data management, driver and card screening, hacking, attack response, etc. By collecting the data packets, this method helps you to recover the missing keys. 12. Comodo HackerProofYou are able to minimize network downtime with Comodo Hackerproof, conduct regular intrusion detection, and use the integrated PCI scanning tools. The drive-by detection and mitigation feature can also be used, and you can create valuable trust with your guests. Many organizations will turn more tourists into customers, thanks to the advantage of Comodo Hackerproof. When purchasing a product with the business, customers appear to feel better, and you should consider that this drives up your sales. You'll enjoy a new level of protection with the patent-pending tracking technology, SiteInspector. 13. MBSA (Microsoft Baseline Security Analyzer)It is a completely independent vulnerability analyzer developed by Microsoft used to search for vulnerabilities on the Windows server or Windows device. There are many exotic features in the Microsoft Baseline Security Analyzer, such as scanning of the core network frames, searching for security patches and other Windows updates, and much more. It is a helpful platform for Windows users. It's important in helping you find missed upgrades or fixes for protection. To install new security patches on the system, use the tool. Small to medium-sized organizations render the software most valuable, and with its capabilities, it may save the security of the organization's money. To fix the bugs which the tool detects, you would not need to consult a security specialist. 14. NexposeNexpose is an open-source platform that can be used without any cost. For security assessments, intelligence analysts frequently use this method. Credit goes to the Github network, all the latest vulnerabilities are included in the Nexpose repository. With the Metasploit System, people can use this tool and also can focus on it to provide a thorough scan of your web service. Different sections will be taken into consideration before producing the report. Vulnerabilities are graded as per their level of risk by the instrument and rated from minimum to maximum. It will scan new apps, so the entire network is secured. Every week, Nexpose is modified so you know it and can find the new threats. 15. Retina CS CommunityRetina CS Community is a web-based open-source dashboard that allows you to build a more structured and streamlined framework for risk mitigation. Retina CS Group has functions such as compliance monitoring, reconfiguring, and compliance with configuration, and you can do a multi-platform vulnerability evaluation just because of this. If it comes to maintaining network security, the tool is incredible for minimizing time, expense, and determination. For DBs, web apps, workspaces, and servers, it provides an automated vulnerability scanning. With items such as virtual app screening and vCenter implementation, companies and organizations can get full support for virtual worlds. 16. SolarWinds Network Configuration ManagerUsers have continuously received glowing ratings from SolarWinds configuration management. The vulnerability evaluation tool provides a particular form of insecurity that most other strategies do not fix, such as malfunctioning network infrastructure. It places it apart from the rest with this function. The predominant usefulness is the verification of network equipment implementations for inconsistencies as a vulnerability assessment tool. To exploit vulnerabilities in the cisco routers, it consolidates with the National Vulnerability Database and has access to the latest CVE's. Any Cisco program running ASA, IOS, or Nexus OS can operate with it. 17. Nessus ProfessionalNessus, developed by Tenable Network Security, is an emblazoned and copyrighted vulnerability scanner. Nessus can stop attacker attempts on the networks, and it check vulnerabilities that allow sensitive information to be hacked remotely. The tool provides a wide variety of cloud infrastructure, digital and physical networks, including OS, DBs, programs, and many other tools. Nessus is trusted by millions of customers for their vulnerability assessment and configuration problems. Network Security with Vulnerability AssessmentWhen an attack begins by altering the structure of the system network, the tools will be able to detect and prevent it. They facilitate you with environmental regulations with their ability to spot out-of-process shifts, compliance modifications, and even appropriate deficiencies. You must follow a predetermined method, like the one illustrated below, to execute a vulnerability assessment. There are four phases to the vulnerability scanning process: scanning, assessment, analysis and remediation. Each of these are discussed below. 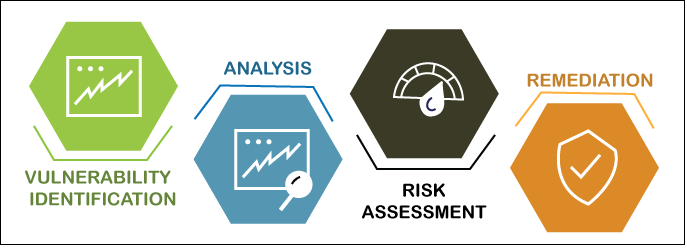
1. Vulnerability Identification (Scanning)The goal of this phase is to formulate a detailed list of the vulnerabilities of a program. Cybersecurity experts test and assess the security performance of databases, repositories or other structures by testing them with automated software. To determine safety vulnerabilities, analysts often depend on vulnerability databases, manufacturer vulnerability notifications, wealth management systems, and threat detection feeds. 2. AnalysisThe aim of this phase is to determine the cause and root cause of the established vulnerabilities in level one. It includes the description and the root cause of the insecurity of sensing devices essential for the vulnerabilities. For instance, a previous version of a free software repository might be the root cause of a vulnerability. This offers a straightforward direction for updating the library for remediation. 3. Risk AssessmentPrioritization of exploits is the purpose of this stage. It implies security analysts granting each vulnerability a rank or intensity ranking, predicated on such considerations as:
4. RemediationThe purpose of this move is to close security loopholes. It's usually a collaborative effort between security personnel, management and operations leaders, who decide the most appropriate route for abatement or containment of each vulnerability. Specific steps for remediation can include:
You can follow a predetermined method, as the one illustrated below, to execute a vulnerability assessment. Step 1: Start the process by recording, determining what resources to use, and obtaining the appropriate stakeholder approval. Step 2: Conduct vulnerability scanning using the required instruments. Make sure all the outputs of those vulnerability tools are saved. Step 3: Analyze the output and determine which vulnerabilities may be a possible threat. The risks can also be prioritized, and a plan to minimize them can be identified. Step 4: Ensure that you log all the findings and compile stakeholder reports. Advantages of Vulnerability AssessmentThe screening of vulnerabilities ensures devices safety from external threats. Some advantages of vulnerability scanning are given below:
Next TopicCapacitor
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










