What is Brute Force Attack?
A brute force attack uses trial-and-error to guess the password, login info, or encryption keys with the hope of eventually guessing a combination correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. A brute force attack accounted for 5% of confirmed security breaches to gain unauthorized access to a system. It is a simple attack method and has a high success rate.
Instead, the attacker can attempt to guess the key, which is created from the password using a key derivation function. This is known as an exhaustive key search.
This method is very fast when used to check all short passwords, but for longer passwords, other methods such as the dictionary attack are used because a brute-force search takes too long. Longer passwords, passphrases, and keys have more possible values and even more combinations, making them exponentially more difficult to crack than shorter ones.
Brute-force attacks can be made less effective by obfuscating the data to be encoded, making it more difficult for an attacker to recognize when the code has been cracked, or by making the attacker do more work to test each guess. One of an encryption system's strengths is how long it would theoretically take an attacker to mount a successful brute-force attack against it.
Brute-force attacks are an application of brute-force search, the general problem-solving technique of enumerating all candidates and checking each one.
Types of Brute Force Attacks
Each brute force attack can use different methods to uncover your sensitive data. You might be exposed to any of the following popular brute force methods:
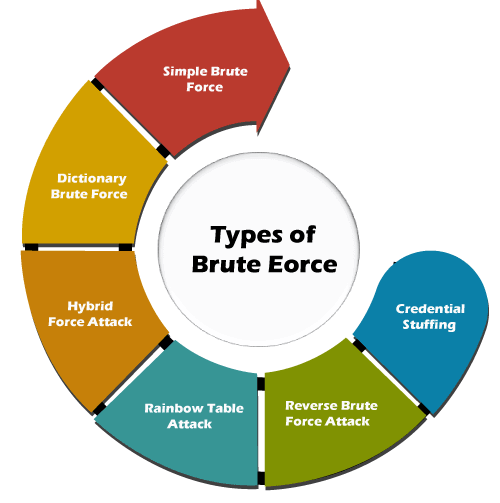
- Simple brute force attack: It uses a systematic approach to 'guess' that doesn't rely on outside logic. Hackers attempt to logically guess your credentials, which completely unassisted from software tools or other means. These can reveal extremely simple passwords and PINs.
- Dictionary attacks: It guesses usernames or passwords using a dictionary of possible strings or phrases. A hacker chooses a target and runs possible passwords against that username. Dictionary attacks are the most basic tool in brute force attacks. While not necessarily being brute force attacks in themselves, these are often used as an important component for password cracking.
- Hybrid brute force attacks: It starts from external logic to determine which password variation may be most likely to succeed and then continues with the simple approach to try many possible variations. A hybrid attack usually mixes dictionary and brute force attacks. These attacks are used to figure out combo passwords that mix common words with random characters.
- Rainbow table attacks: A rainbow table is a pre-computed table for reversing cryptographic hash functions. You can use it to guess a function up to a certain length consisting of a limited set of characters.
- Reverse brute force attack: A reverse brute force attack reverses the attack strategy by starting with a known password. It uses a common password or collection of passwords against many possible usernames. Then hackers search millions of usernames until they find a match. Targets a network of users for which the attackers have previously obtained data. Many of these criminals start with leaked passwords that are available online from existing data breaches.
- Credential stuffing: It uses previously-known password-username pairs, trying them against multiple websites. If a hacker has a username-password combo that works for one website, they'll try it in tons of others as well. Since users have been known to reuse login info across many websites, they are the exclusive targets of an attack. Exploits the fact that many users have the same username and password across different systems.
Brute Force Attack Tools
Guessing a password for a particular user or site can take a long time, so hackers have developed tools to do this task faster.
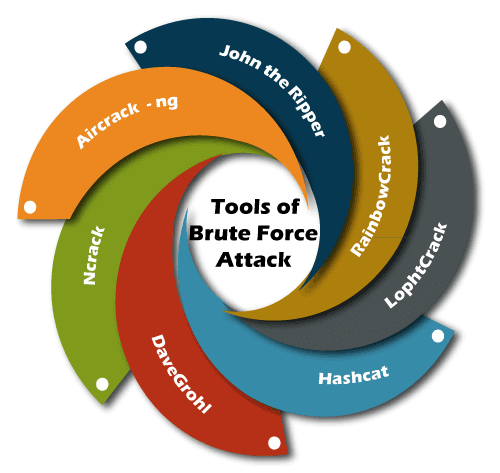
- Aircrack-ng: You can use this on Windows, Linux, iOS, and Android. It uses a dictionary of widely used passwords to breach wireless networks.
- John the Ripper: It runs on 15 different platforms, including UNIX, Windows, and OpenVMS. It tries all possible combinations using a dictionary of possible passwords.
- RainbowCrack: Some tools scan pre-compute rainbow tables for the inputs and outputs of known hash functions. These "hash functions" are the algorithm-based encryption methods used to translate passwords into long, fixed-length series of letters and numerals. The rainbow tables remove the hardest part of the brute force attacking to speed up the process.
- L0phtCrack: It is a tool for cracking Windows passwords. It uses rainbow tables, dictionaries, and multiprocessor algorithms.
- Hashcat: It works on Windows, Linux, and Mac OS. It can perform simple brute force, rule-based, and hybrid attacks.
- DaveGrohl: It is an open-source tool for cracking Mac OS. It can be distributed across multiple computers.
- Ncrack: It is a tool for cracking network authentication. It can be used on Windows, Linux, and BSD.
- CPU and GPU: Combination of CPU and GPUaccelerates computing power. By adding the thousands of computing cores in the GPU for processing enables the system to handle multiple tasks at once. Hackers using this method can crack passwords about 250 times faster than a CPU alone.
- Automated tools: These use rapid-fire guessing that is built to create every possible password and attempt to use them. Brute force hacking software can find a single dictionary word password within one second. These tools have workarounds programmed in them to:
- Work against many computer protocols, such as FTP, MySQL, SMPT, and Telnet.
- Allow hackers to crack wireless modems.
- Identify weak passwords.
- Decrypt passwords in encrypted storage.
- Translate words into leetspeak.
- Run all possible combinations of characters.
- Operate dictionary attacks.
How to Create Protect Passwords
As a user, you can do many things to support your protection in the digital world. The best defense against password attacks is ensuring that your passwords are as strong as they can be.
Brute force attacks rely on time to crack your password. So, your goal is to make sure your password slows down these attacks as much as possible because if it takes too long for the breach to be worthwhile, most hackers will give up and move on.
Here are a few ways you can create strong passwords against brute attacks, such as:
- Use an advanced username and password: Protect yourself with stronger credentials than adminand password to keep out these attackers. The stronger this combination is, the harder it will be for anyone to penetrate it.
- Use a password manager.Installing a password manager automates creating and keeping track of your online login info. These allow you to access all your accounts by first logging into the password manager. You can then create extremely long and complex passwords for all the sites you visit, store them safely, and you only have to remember the one primary password.
- Stay away from frequently used passwords.It's important to avoid the most common passwords and to change them frequently.
Passive Backend Protections for Passwords
Once you've got the basics protection, you'll want to boost your security and get users on board. Now, go to the backend protection.
- High encryption rates:System administrators should ensure that passwords for their systems are encrypted with the highest encryption rates possible, such as 256-bit encryption. The more bits in the encryption scheme, the harder the password is to crack.
- Salt the hash:Administrators should also randomize password hashes by adding a random string of letters and numbers (called salt) to the password itself. This string should be stored in a separate database and retrieved and added to the password before it's hashed. By salting the hash, users with the same password have different hashes.
- Two-factor authentication (2FA):Administrators can require two-step authentication and install an intrusion detection system that detects brute force attacks. It requires users to follow-up a login attempt with a second factor, like a physical USB key or biometrics scan.
- Limit number of login re-tries:Limiting the number of attempts also reduces susceptibility to brute-force attacks. For example, allow three attempts to enter the correct password before locking out the user for several minutes.
- Implement Captcha:Manual verification does stop robots from brute-forcing their way into your data. Captcha comes in many types, including retyping the text in an image, checking a checkbox, or identifying objects in pictures. Regardless of what you use, you can use this before the first login and after each failed attempt to protect further.
- Use an IP denylist:The IP denylist is used to block known attackers. Be sure this list is constantly updated by those who manage it.
Active IT Support Protections for Passwords
- Password education:User behavior is essential to password security. Educate users on safe practices and tools to help them keep track of their passwords. Services like Kaspersky Password Manager allow users to save their complex, hard-to-remember passwords in an encrypted "vault" instead of unsafely writing them down on sticky notes.
- Watch accounts in real-time: Work to find unusual activity trends and take measures to block any potential attackers in real-time. Look out for IP address blocks, account lockdown, and contact users to determine if account activity is legal.
|


 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










