Hash FunctionHash Function is used to index the original value or key and then used later each time the data associated with the value or key is to be retrieved. Thus, hashing is always a one-way operation. There is no need to "reverse engineer" the hash function by analyzing the hashed values. Characteristics of Good Hash Function:
Some Popular Hash Function is:1. Division Method:Choose a number m smaller than the number of n of keys in k (The number m is usually chosen to be a prime number or a number without small divisors, since this frequently a minimum number of collisions). The hash function is: 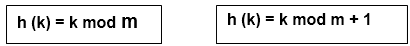
For Example: if the hash table has size m = 12 and the key is k = 100, then h (k) = 4. Since it requires only a single division operation, hashing by division is quite fast. 2. Multiplication Method:The multiplication method for creating hash functions operates in two steps. First, we multiply the key k by a constant A in the range 0 < A < 1 and extract the fractional part of kA. Then, we increase this value by m and take the floor of the result. The hash function is: 
Where "k A mod 1" means the fractional part of k A, that is, k A -⌊k A⌋. 3. Mid Square Method:The key k is squared. Then function H is defined by Where L is obtained by deleting digits from both ends of k2. We emphasize that the same position of k2 must be used for all of the keys. 4. Folding Method:The key k is partitioned into a number of parts k1, k2.... kn where each part except possibly the last, has the same number of digits as the required address. Then the parts are added together, ignoring the last carry. H (k) = k1+ k2+.....+kn Example: Company has 68 employees, and each is assigned a unique four- digit employee number. Suppose L consist of 2- digit addresses: 00, 01, and 02....99. We apply the above hash functions to each of the following employee numbers: (a) Division Method: Choose a Prime number m close to 99, such as m =97, Then That is dividing 3205 by 17 gives a remainder of 4, dividing 7148 by 97 gives a remainder of 67, dividing 2345 by 97 gives a remainder of 17. (b) Mid-Square Method: k = 3205 7148 2345 k2= 10272025 51093904 5499025 h (k) = 72 93 99 Observe that fourth & fifth digits, counting from right are chosen for hash address. (c) Folding Method: Divide the key k into 2 parts and adding yields the following hash address:
Next TopicBinary Search Trees
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










