Bitcoin Mitigating AttacksBitcoin is the most secure cryptocurrency, which provides security at multiple levels of the protocol. It is often rendering sustained sophisticated attacks. In this section, we are going to look at various types of probable attacks in the bitcoin system. The Sybil AttackThe Sybil attack happens in the peer-to-peer network. A malicious attacker wishes to carry out this attack on the bitcoin network. In this, a node in the network operates multiple identities at the same time and undermines the authority in the reputation system. Its main aim is to gain the majority of influence in the network to carry out illegal actions in the system. The Sybil attack is difficult to detect and prevent, but the following measures can be useful:
Race AttackThe Race Attack requires the recipients to accept unconfirmed transactions as payment. As an attacker, you can send the same coin to different vendors by using the two different machines. If the vendors deliver the things without waiting for block confirmation, they will soon realize that the transaction was rejected during the mining process. The solution to this is that the vendor must wait for at least one block confirmation before sending things. This attack is easier to pull off when the attacker has a direct connection to the victim's node. Therefore it is recommended to turn off incoming connections to nodes for receiving payments so that your node will identify their own peers. And it does not allow the payer to submit the payment to the payee directly. Finney AttackThe Finney attack is named after Hal Finney. The Finney attack is one of the types of double-spending problem. In this attack, the attacker is the miner who mines blocks normally. In the block, he includes a transaction which sends some of his coins back to himself without broadcasting the transaction. When he finds a pre-mined block, he sends the same coins in a second transaction. The second transaction would be rejected by other miners, but this will take some time. To prevent this attack, the seller should wait for at least six blocks confirmation before releasing the goods. Vector76 AttackThe Vector76 attack is a combination of the Race attack and the Finney attack such that a transaction that even has one confirmation can still be reversed. In this attack, a miner creates two nodes, one of which is connected to the exchange node, and the other is connected to well-connected peers in the blockchain network. Now, the miner creates two transactions, one high value, and one low value. Then, the attacker pre-mines a high-value transaction to an exchange service. When a block is announced, he quickly sends the pre-mined block directly to the exchange service. When exchange service confirms the high-value transaction, the corrupted attacker sends a low-value transaction to the blockchain network that finally rejects the high-value transaction. As a result, the corrupted attacker's account is deposited on the amount of the high-value transaction. This attack can be protected by disabling the incoming connections and only connecting to well-connected nodes. The 51% AttackThe 51% attack is a potential attack on the blockchain network. It refers to a single miner or group of miners who are trying to control more than 50% of a network's mining power, computing power or hash rate. In this attack, the attacker can block new transactions from taking place or being confirmed. They are also able to reverse the transactions that have already confirmed while they were in control of the network, leading to a double-spending problem. When a miner forms a valid block of transactions, the individual will broadcast the block to other miners on the network. It can only be accepted if all transactions in a block are valid according to the existing record on a blockchain. However, a corrupt minor with more than 50% of a network's hash rate does not broadcast solutions to the rest of the network. It results in the formation of two versions of the blockchain. One is the public version of the blockchain, which is being followed by legitimate miners. And second is used by the corrupt miners who are not broadcasting it to the rest of the network. 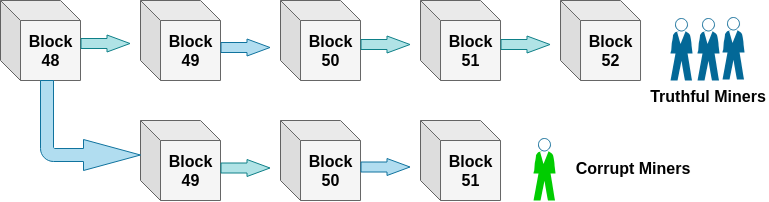
This type of attack is fictitious because it is costly to acquire computing power, which has more than 50% of the computing power of the entire network.
Next TopicWho sets the Bitcoin Price
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










