Blockchain and data privacy
What exactly is Blockchain?
The blockchain, as a secure ledger, organises the increasing number of transactions into a hierarchically growing chain of blocks , with each block guarded by cryptography techniques to ensure the robust integrity of its transaction data. New blocks can only be committed to the global chain of blocks if the decentralised consensus method is successfully completed.
In particular, a block retains the hash value of the whole block itself, which may be viewed as its encryption image, as well as the hash value of the preceding block, serving as a cryptographic connection to the before block in the the distributed ledger.
Introduction
Blockchain has become one amongst the most highly anticipated technological advances in recent years. However, blockchain technology as well as information security laws and regulations have advanced significantly.
Blockchain provides the benefits of decentralisation and distributed global ledger sharing, but it also carries a possibility of data privacy leaks. There is still a wide room for the development of different protection techniques to prevent harmful attackers from stealing the personal information of blockchain users. First, this article examines the chain block design, as well as the Bitcoin data privacy danger. Blockchain is a decentralised data processing technique in which all network participants are responsible for data distribution and storage. With the massive amounts expansion of the blockchain technology in recent years, many countries' energy departments have started using blockchain technologies for smart grids in areas such as trading in energy applications, electric car applications, energy security applications, and microgrid operations. Blockchain technology, when integrated with cryptography, can provide safe real-time metering & communication procedures for smart grids, significantly lowering the high costs of transmission generated by the previous approach. The use of the blockchain in the process of trading electric energy may successfully minimise energy loss while also improving the trading system's real-time performance and security. Without the use of third intermediaries, businesses and consumers can trade power and capital on a peer-to-peer and trustworthy basis.
Data privacy introduction
So far, the majority of public interest in blockchain has been on crypto-currencies, particularly Bitcoin, as well as associated financial services like first-time coin offerings (ICOs). Less overtly, but maybe more critically in the long run, significant investment is being made in the creation of a wide range of blockchain applications, ranging from asset registration (including property) to self-executing ('smart') contracts. Despite widespread misunderstanding about what blockchain is or could become, blockchain and other distributed ledger methods (DLTs) have attracted the attention of governments, companies, and individuals, and they have become a focus of interest for lawmakers and regulators around the world.
In most applications, transactions are globally disclosed and are not encrypted. If this data involves personal data, such as "medical or financial data," it causes regulatory and legal issues, particularly in Germany. One option is to exclusively store data that is encrypted in the distributed ledger, but this raises another issue: if a key needed to decode specific details is lost, the information may not be restored precisely. In addition, if a key has been taken or publicised, all data in the blockchain is forever decrypted because the data cannot be edited. Blockchain, on the other hand, can help to improve preventive security methods, particularly in terms of identification and access.
How blockchain supports data privacy
In the modern era, where all things are digital and data is king, privacy is now an unavoidable concern. Today's users having little to no influence over how online apps and websites use their data and private data. Whereas this data can be utilised to provide personalised searches and personalised product and service suggestions, it can also lead to fraud and security breaches. Blockchain technology offers a solution! Let us look at some of the ways Blockchain technology works to preserve the confidentiality and safety of users and their data.
- Decentralisation and Agreement : Decentralisation is a crucial component that contributes to the security of Blockchain. Whereas a standard database keeps data in a single location, Blockchain stores data by replicating it to multiple locations, resulting in a distributed ledger. As a result, in order to secure data privacy, Blockchain requires non-traditional procedures.Each exchange on the system is open and is stored on a collection of devices rather than just one computer. Every device connected to a blockchain gets an electronic copy of each transaction that occurs on the blockchain.
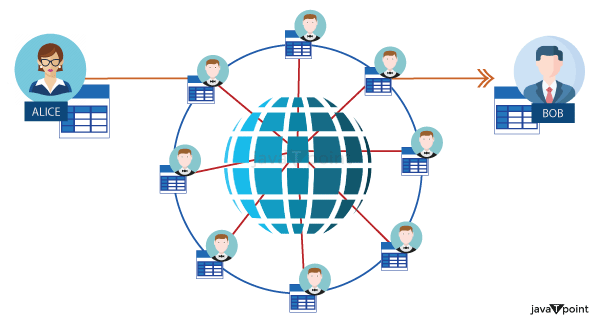
This implies that the blockchain is collaboratively run and governed by a community of individuals who depend on the system. Any new block added to the chain by a node in the network is first validated by the Blockchain network's other nodes. The modified blocks are discarded. Only when more than 51% of the computers in the blockchain agree on the new block will it be properly added to the chain. This is referred to as the Majority mechanism.
- Hashing and Blocks : As the name implies, blockchain is an ordered sequence or series of blocks. Each one of these blocks is made up of three distinct components, namely,
- The information or data
- The hash value of the block
- The prior block in the chain's hash
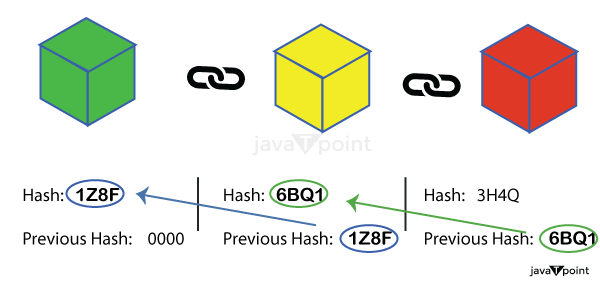
The information in a block is encrypted and has a unique identity (similar to a fingerprint). This identification is referred to as a Hash. Each block in the chain has responsibility for storing the encryption key of the previous block. This contributes to the Blockchain system's effectiveness and security.The Genesis Block is the initial block in a chain that is unconnected to any earlier block.
If anything inside the block changes, the hash of the blocks also changes. That means the following block is going to point to an additional hash rather than the one that came preceding it (it no more stores the preceding block's valid hash). As a result, all subsequent blocks in the sequence become invalid. Because of this property, hashes may be used as an effective method for detecting modifications and manipulation in Blockchain data. As a result, the information is protected and tamper-proof.
- Proof of work on Sample : Proof work is a process or approach used to slow down the generation of new blocks. As a consequence, if a person interferes with the contents in one block, he or she must recalculate the evidence of work for every other block in the chain. Individuals will find it difficult to tamper without a block as a result of this.
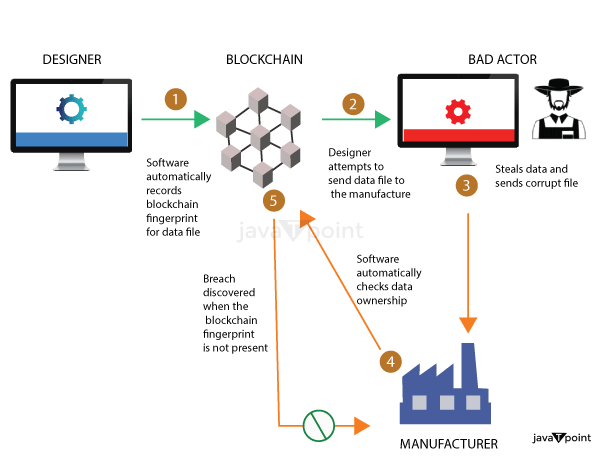
Proof of operation and hashing algorithms work together to reduce fraud and hence ensure the integrity and security of data in the network of Blockchain devices.
- Public Addresses : Every node in the distributed ledger (computer or other device) has a unique private key and public address. When a node participates in an exchange, it simply communicates its public address to the rest of the world, not the private key. This public name is a random string of digits and letters. When other Blockchain network users see the public location, all they can see is the transaction record and the general address. However, personal and financial data such as the user's name, age, and address remain anonymous. This mechanism ensures that the user's privacy is protected.
- Encryption and Private Key Control: Blockchain employs sophisticated encryption algorithms to secure data. Each participant in a blockchain network has a unique cryptographic key pair: a public key and a private key. Data is encrypted using the recipient's public key, ensuring that only the intended recipient can decrypt and access the information. This cryptographic encryption protects sensitive data during transmission and storage, reducing the risk of unauthorized access.
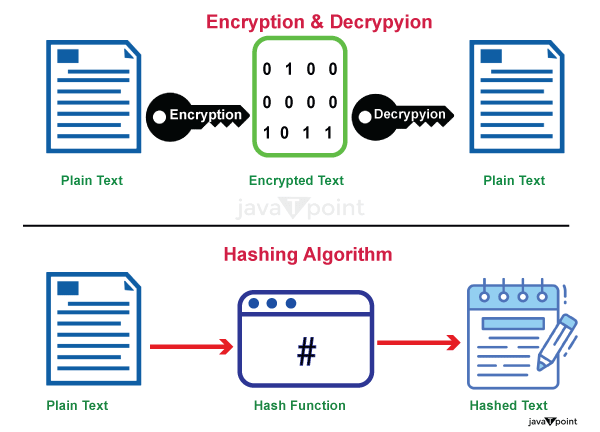
The private key, which is securely held by the data owner, grants access to the data stored on the blockchain. This ownership and control over the private key empower individuals and organizations to manage their own data, eliminating the need to trust centralized entities with sensitive information. Users can share selective access to their data by granting temporary or permanent cryptographic permissions, thereby enhancing data privacy and control.
- Proof of Zero-Knowledge : Zero Knowing Proof is an excellent method for safeguarding private information in the Blockchain system. This strategy allows a person to demonstrate to other people that a particular assertion is true without revealing any extra information. In an exchange, the prover must demonstrate to the verifier whether a certain value (also referred to to both the provide and the verifier) is accurate and reliable, while eliminating any extraneous information.
- It's like proving to somebody that you know the secret without actually telling them the secret.
- Smart Contracts and Permissioned Blockchains: Smart contracts, self-executing programs running on blockchain networks, provide an additional layer of privacy and control over data. Smart contracts enable predefined rules and conditions to be enforced automatically, eliminating the need for intermediaries. By embedding privacy features within smart contracts, sensitive information can be securely shared and processed without exposing it to unauthorized parties.
In permissioned blockchains, access to the network and data is restricted to trusted participants, enhancing privacy and confidentiality. These private blockchains are particularly useful in enterprise settings, where specific data privacy requirements need to be met. By carefully managing access control and permissions, organizations can ensure that only authorized entities can participate and access sensitive data.
Data privacy Threads in blockchain :
- Pseudonymity versus Anonymity: One of the fundamental characteristics of blockchain is the pseudonymous nature of transactions. While users are represented by cryptographic addresses rather than their real identities, the transparency of the blockchain can still enable the linkage of transactions to specific individuals or entities. With the increasing availability of external data sources and sophisticated analysis techniques, the pseudonymous nature of blockchain transactions may be compromised, jeopardizing the privacy of participants.
- Data Leakage through Off-Chain Activities: Although blockchain itself provides a secure environment for data storage, certain interactions and activities related to blockchain may occur off-chain. Off-chain data includes information shared through external platforms, communication channels, or smart contracts that interact with external systems. These off-chain activities can potentially expose sensitive data, such as personal details or transactional information, to vulnerabilities outside the blockchain environment. Consequently, the privacy of participants' data becomes dependent on the security measures implemented in these external components.
- Inadequate Implementation of Privacy Protocols: While blockchain offers potential solutions for privacy concerns, the implementation of privacy protocols and techniques is not standardized across all blockchain networks. Privacy features such as zero-knowledge proofs, ring signatures, or stealth addresses can enhance confidentiality, but their usage and effectiveness can vary depending on the specific blockchain implementation. Inadequate implementation or misconfiguration of privacy protocols can lead to unintended data exposure, rendering the blockchain susceptible to privacy breaches.
- Public versus Private Blockchains: Public blockchains, such as Bitcoin and Ethereum, maintain transparent transaction records visible to anyone in the network. While these blockchains provide strong security guarantees, they inherently sacrifice privacy to achieve decentralization and transparency. On the other hand, private or permissioned blockchains limit access to trusted participants, enabling greater privacy control. However, even in private blockchains, data privacy can be compromised if participants do not adhere to strict access controls or if malicious actors infiltrate the network.
- Storage of Immutable Data: The immutability of data recorded on the blockchain, a key feature ensuring data integrity, can also pose challenges to privacy. Once information is written on the blockchain, it cannot be altered or deleted. In cases where personal or sensitive data is inadvertently stored on the blockchain, eradicating that information becomes extremely challenging. This immutability feature conflicts with the "right to be forgotten" principle, which is a crucial aspect of data privacy regulations such as the General Data Protection Regulation (GDPR).
Conclusion
Blockchain technology presents a groundbreaking solution to the challenges of data privacy and security. Through its decentralized structure, immutability, encryption mechanisms, and smart contract capabilities, blockchain offers a robust framework for safeguarding personal and organizational data.
While blockchain technology offers promising solutions to data privacy concerns, it is essential to acknowledge and address the challenges it presents. Striking a balance between transparency and privacy, adopting robust privacy protocols, and ensuring proper implementation of security measures are crucial steps toward enhancing data privacy within blockchain systems. As blockchain evolves and matures, continuous efforts to address these challenges will be necessary to unleash its full potential while safeguarding the privacy rights of individuals and organizations alike.
|

 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now














