Emerging Cyber Security threatsA cyber and safety breach is a malicious act that seeks to hurt, steal, or disrupt surfing in general. Hacking, computer infectious agents An attack aiming at obtaining unauthorized access to, destroying, interrupting, or stealing a technical asset, a network of computers, confidential information, or any other sort of sensitive data is one example of a cyber risk. Cyber hazards might arise within an organization from trusted personnel or in remote locations from unknown sources. According to Cybersecurity Ventures, the number of open cybersecurity roles climbed to 3.5 million between 2013 and 2021. FireEye, another large IT data company, thinks that number will climb even further. When you realise that just about 30,000 new STEM graduates enter the job market every year, it's evident that senior IT workers face substantial challenges. a report from the US government, network attacks have reached their highest level in the past three years, and sponsored by the state cyber threats used in war have reached record levels. North Korea's recent hack is the first of many. Despite the "doom & gloom," there could be some good news on the way. What Are the Most Recent Cyber Threats?Remote labor became an alternative standard during the outbreak. Working from home allowed businesses to continue operating as usual, but it also opened the door to cybercriminal activity. Emerging cyber threats have increased theft by 600% since the worldwide crisis began. Hackers and fraudsters use a number of ways to steal your important data and hold your business's finances hostage, ranging from basic email phishing attempts to complicated cross-site scripting (XSS). With a year-over-year increase of 1,070 percent in attacks involving ransomware between July 2020 and the start of 2021, staying on top of security trends-such as malware and supply system threats-is more important than ever.1 To successfully recognize and guard against security dangers, we must work together and share our collective knowledge, research, insight, and understanding. Cyber threats remain amongst the top worldwide threats, according in the Global Business Forum's worldwide Hazards Report 2021. The pandemic or life-risking portion has raised technology adoption, but it additionally highlighted computer flaws and unpreparedness, worsening technological disparities within and among civilizations. Do Cyber Attacks a Genuine Threat?Unfortunately, no one considers information security to be vital until it is too late. In 2022, the number of information breach victims increased 210% over Q2 2022. Not only that, but the total amount of data breach notifications without an explanation increased from 19 by 2019 and 617 in 2022. 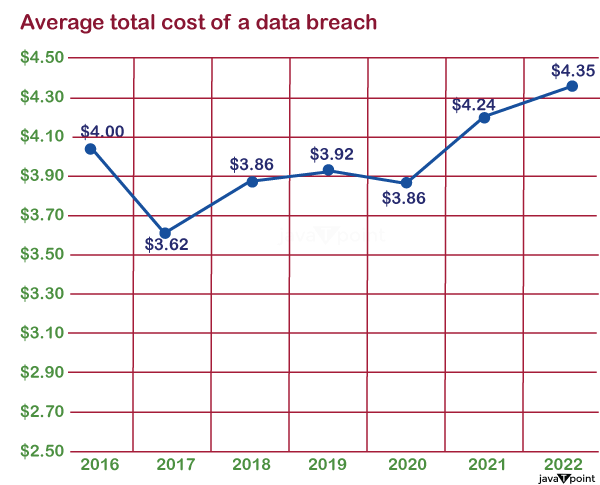
Each data breach results in severe business continuity costs. Businesses lose $4.35 million on average following a breach . In breaches when remote employment was a component, the average cost increased by $1 million. Cyber threat classificationsCyber-security counters three types of threats:
Some popular cybersecurity theats are listed below :Attempted Work-from-Home AttacksThe first major cyber trend for 2021 emerges in 2020. While WFH is not a new threat in 2018, it's just an issue of time until hackers target a large number of susceptible home networks simultaneously, resulting in a massive-scale incursion of critical systems and services. Everything is in order. The region under corporate assault has risen dramatically as more employees use their residence's internet connection for both personal and commercial functions. To address this issue, double the quantity of IAM with systems capable of proactively evaluating user behavior, resource needs, and corporate connectivity patterns allowing for rapid sign-in when it is safe to do so - and demanding further verification if possible concerns are detected. Frustrations with Brute ForceBrute-force attacks are also on the rise. These along with other cybersecurity improvements are being driven by attackers who see an opportunity for DDoS assaults to bring down corporate networks. DDoS attack efforts grew by 12% in the second half of 2020, with the most significant rise occurring with the use of a simple delivery of services mechanism (SSDP) with its simple network management mechanism (SNMP). By using botnet swarms, attackers were able to multiply IP inquiries and overload company networks, decreasing responses or even shutting off services. SNMP assaults are especially problematic since this protocol links and manages common corporate equipment such as broadband connections, printers, routers, switches, and servers. When SNMP functions are exploited, attackers are effectively beyond the limitations of firewalls, putting all enterprise services to risk. Frameworks without filesFileless ransom and other malware attacks will continue to plague organisations in 2021. These assaults are designed to escape detection and enter critical components by "existing off the soil" - that is, through utilizing authorized platforms or programs that are already present within the business's networks. Attackers can use this method to bypass traditional detection procedures such as checking for attachments that are malicious or cataloging the production of new files. Furthermore, using existing system tools minimises the need of malicious actors to design their own attack infrastructure. This minimizes the period of time required to create malware. In 2021, attackers were more likely to target businesses that provide services rather than individuals. They can then target downstream clients by leveraging their existing infrastructure. Older Cybersecurity Trends Continue to Be ImportantEven when attackers create new forms of threats, existing ones like ransomware, Trojans, and botnets continue to exist. To confront these well-known risks and emerge relatively undamaged, businesses must guarantee that their employees have the knowledge and resources they need to detect these assaults as soon as possible. This begins with training on typical compromise vectors like fraudulent email attachments and URLs. It also includes continual attempts to monitor email accounts, educate employees on security requirements, and automatically inform them if possible dangers are found. Phishing on the Front LinesObviously, the COVID-19 immunization is the most important news event of 2021. People want vaccination information on everything from the current state of the disease to when and where the vaccine is delivered and who is qualified to get it. This will influence cyber security advances in 2021. As a result, organizations should prepare for a rise in phishing efforts. These are highly dangerous since they quickly catch the reader's interest. Attacks that take use of this have already been identified. The United Kingdom's National Health Service recently issued a warning about fake vaccination appointment emails. IBM X-Force found a supply-side hack targeted at jeopardizing vaccine freezing. Trends in Cybersecurity threatsThis year's top cyber security developments are driven by modern organisations' ever-expanding digital presence .security and risk executives are at a crossroads as organizations' digital footprints grow and centralized cyber security control becomes outmoded. you can find new trends listed below; Expansion of the attack surfaceAt the moment, 60% of knowledge employees are distant, and a minimum of 18% will never return to their office. These changes in how we operate, along with increased usage of public the cloud, highly networked supply chains, and the utilization of cyber-physical systems, have exposed new and difficult attack "surfaces." As a result, organizations are more exposed to assault. To manage a broader collection of threats, Gartner suggests that security leaders explore beyond standard techniques to security monitoring, detection, and response. Identity system protectionIdentity systems are under constant attack. The improper use of passwords is increasingly a common approach for attackers to gain access to networks and achieve their objectives. In the Solar Winds hack, for example, attackers utilized privileged access from a supplier to penetrate the target network. Gartner defines identity detection and response to threats (ITDR) as a set of technologies and processes for defending identity systems. Over time, more unified solutions will emerge. The dangers of the digital supply chainAccording to Gartner, 45% of organizations worldwide would have faced assaults on their computer software supply chains by 2025, a threefold increase from 2021. Leaders in risk and security management must collaborate with other divisions to prioritize digital logistics risk and put demands on suppliers to exhibit best practices in security. Consolidation of vendorsSecurity products are becoming more similar. To make bundles more appealing, vendors are unifying security functions onto single platforms and providing pricing and licensing alternatives. While consolidation may pose new issues such as diminished bargaining leverage and potential singular points of failure, IDC sees it as a positive trend that will reduce complexity, lower costs, and enhance efficiency, ultimately leading to greater overall security. Mesh Cyber SecurityThe safety mesh is a current conceptual method for security architecture that allows the dispersed company to deploy and integrate protection to assets on-premises, in data center , or in the cloud. According to Gartner, organizations that use a safety mesh architecture would minimize the cost effectiveness of individual security events by 90% by 2024. Decisions that are distributedTo achieve digital business ambitions, executive executives want a quick and agile cyber security department. However, as more areas of the organisation get digitalized, the task has grown too large for a centralised CISO post. Leading organisations are establishing CISO offices to allow dispersed cyber judgement. The CISO with the centralised role will continue to create policy, but cybersecurity leaders will be distributed throughout the organisation to decentralise security choices. 
Above and beyond awarenessHuman error is a factor in the majority of data breaches, demonstrating that standard approaches to education on security awareness are unsuccessful. Progressive organisations are going beyond outmoded compliance-based awareness efforts and pursuing holistic behaviour and culture change programmes meant to in still more secure working practises. In a nutshell:
End-user securityEnd-user protection, frequently referred to as security for endpoints, is an important aspect of cyber security. After all, it is typically the end-user who unintentionally installs malware or another sort of cyber threat on their laptop, desktop, or mobile device. So, how can information security measures protect customers and systems? To begin, encryption methods are employed in cyber-security to encrypt communications, files, and other critical data. This protects information not just in transit, but additionally against theft or destruction. Furthermore, end-user antivirus software scans computers for malicious malware, restrictions it, and finally completely eliminates it from the machine. Security applications may even detect and remove hazardous code hidden in the master BIOS record (MBR), which is used to encrypt or delete data.. As cyber-security specialists find new dangers and strategies to tackle them, security programmes continue to create new defences. Employees must be taught on how to utilise end-user security software in order to get the most out of it. Importantly, keeping it operating and periodically upgrading it guarantees that it can defend users from the most recent cyber dangers. Cyber security advice - how to defend yourself against cyber attacksHere is our top cyber security recommendations:
ConclusionIn addition to proper security practises and training for maintaining your data safe, it may be worthwhile to use third-party software and solutions for further protection. It's a good idea, for example, to employ one of the best antivirus companies to assist further secure your site and check for possible dangers, in addition to a VPN to maintain your online activities private.
Next TopicImpact of IOT on Cyber Security
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










