SHA Algorithm in CryptographySHA IntroductionSecure Hashing Algorithm, or SHA. Data and certificates are hashed with SHA, a modified version of MD5. By using bitwise operations, modular additions, and compression functions, a hashing algorithm reduces the input data into a smaller form that is impossible to comprehend. Can hashing be cracked or decrypted, you may wonder? The main distinction between hashing and encryption is that hashing is one-way; once data has been hashed, the resultant hash digest cannot be decrypted unless a brute force assault is applied. See the illustration below to see how the SHA algorithm functions. SHA is designed to provide a different hash even if only one character in the message changes. As an illustration, consider combining the themes Heaven and Heaven Is Different. The only difference between a capital and tiny letter, though, is size. 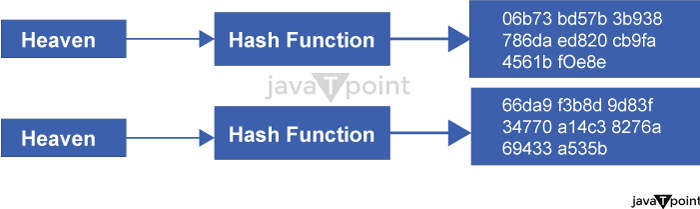
The first message is hashed using SHA-1 to get the hash digest "06b73bd57b3b938786daed820cb9fa4561bf0e8e". The hash digest for the second, analogous message will look like "66da9f3b8d9d83f34770a14c38276a69433a535b" if it is hashed with SHA-1. The avalanche effect is what is known for this. This phenomenon is crucial for cryptography since it implies that even the smallest alteration to the message being entered entirely alters the output. As a result, attackers won't be able to decipher what the hash digest initially said or determine whether the message was altered while in route and inform the message's recipient. SHAs can aid in identifying any modifications made to an original message. A user can determine whether even one letter has been altered by consulting the original hash digest since the hash digests will be entirely different. The fact that SHAs are deterministic is one of their key features. This implies that any machine or user may reproduce the hash digest if they know the hash algorithm that was used. Every SSL certificate on the Internet must have been hashed with the SHA-2 procedure because of the determinism of SHAs. Different Types of SHANumerous SHA variants are mentioned while discussing SHA forms. There are only two kinds of SHA-SHA-1 and SHA-2-but they go by several names, such as SHA-1, SHA-2, SHA-256, SHA-512, SHA-224, and SHA-384. The other higher numbers, such as SHA-256, are merely SHA-2 variants that include information on the bit lengths of SHA-2. The first secure hashing algorithm was SHA-1, which produced a 160-bit hash digest as a result of hashing. Can SHA-2 be cracked like SHA-1, one may wonder? Yes, it is the solution. SHA-1 is easier to brute force than SHA-2 because to the shorter length of the hash digest, however SHA-2 can also be done. Due to the limited amount of possible combinations that can be made with 160 bits, another problem with SHA-1 is that it can provide the same hash digest for two distinct values. All certificates must utilize SHA-2 since it provides each digest with a unique value under SHA-2. SHA-2 can generate hash digests with bit lengths ranging from 256 to 512, giving each one a fully unique result. When two values have the same hash digest, collisions happen. Because SHA-1 is prone to collisions, it is simpler for attackers to find two digests that match and reconstitute the original plaintext. Since 2016, SHA-2, which is far more secure than SHA-1, has been needed in all digital signatures and certificates. The most secure hash method is SHA-2 since common assaults like brute force attacks can take years or even decades to decrypt the hash digest. Why and How SHA is used?Secure Hashing Algorithms (SHAs), as was already noted, are used for a variety of purposes and must be included in all digital signatures and certificates for SSL/TLS connections. SHAs are also used by programs like IPSec, SSH, and S-MIME (Secure / Multipurpose Internet Mail Extensions). Additionally, passwords are hashed using SHAs so that the server only has to remember the hashes and not the actual passwords. As a result, if a database holding all the hashes were stolen, an attacker would not only lack direct access to all the plaintext passwords but would also need to figure out how to break the hashes in order to utilize the passwords. SHAs can also serve as markers for the consistency of a file. Now that we are aware of the purposes of SHAs, we must ask ourselves: why would anyone ever employ a Secure Hashing Algorithm? Their capacity to repel invaders is a frequent justification. Although some techniques, such as brute force assaults, can disclose the plaintext of the hash digests, SHAs make these strategies very challenging. A basic password may deter many attackers since a password encoded by a SHA-2 algorithm might take years or even decades to crack. The distinctness of each hash digest is another justification for using SHAs. The hash digest might be totally altered by changing just one word in a message if SHA-2 is used since there are likely to be few to no collisions. The Secure Hashing Algorithm cannot be broken by the attacker since there are few or no collisions, making it difficult to identify a pattern. These are only a few explanations for why SHA is employed so frequently. The Prospects for HashingSHA-2 is now the industry standard for hashing algorithms, although SHA-3 may eventually overtake it. The NIST, which also developed SHA-1 and SHA-2, produced SHA-3 in 2015; but, for a variety of reasons, it was not adopted as the industry standard. Since most businesses were transitioning from SHA-1 to SHA-2 at the time of SHA-3's introduction, it did not make sense to convert to SHA-3 immediately away while SHA-2 was still quite secure. Additionally, SHA-3 was perceived as being slower than SHA-2, albeit this is not entirely accurate. Although SHA-3 is slower on the software side than SHA-1 and SHA-2, it is substantially quicker on the hardware side and gets faster every year.
Next TopicWhat is AES
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









