Difference between Active attack and Passive attackThis article is going to be very interesting and important for readers that are interested in cyber security. In this article, we are going to discuss two major types of security attacks that are Active attack and Passive attack. Hope this article will be informative to you, and give you the sufficient information about Active attack, Passive attack, and their comparison. So, without any delay, let's start our topic. What is a Security attack?Security attacks jeopardize the system's security. These are the unauthorized or illegal actions that are taken against the government, corporate, or private IT assets in order to destroy, modify, or steal the sensitive data. They are further classified into active and passive attacks, in which the attacker gets unlawful access to the system's resources. Active attacksIn active attacks, the attacker intercepts the connection and efforts to modify the message's content. It is dangerous for integrity and availability of the message. Active attacks involve Masquerade, Modification of message, Repudiation, Replay, and Denial of service. The system resources can be changed due to active attacks. So, the damage done with active attacks can be harmful to the system and its resources. In the below image, we can see the process of active attacks. 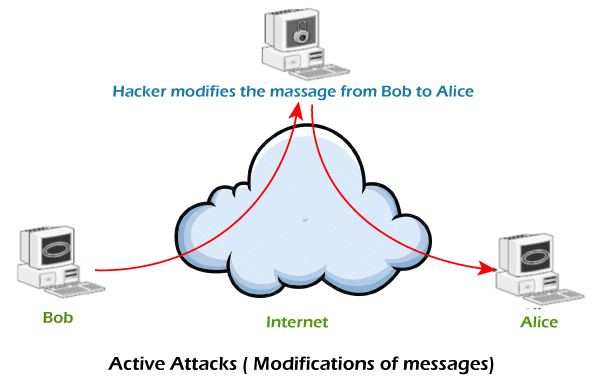
In active attacks, the victim gets notified about the attack. The implication of an active attack is typically difficult and requires more effort. Active attacks can be prevented by using some techniques. We can try the below-listed measures to prevent these attacks -
Passive attacksIn passive attacks, the attacker observes the messages, then copy and save them and can use it for malicious purposes. The attacker does not try to change the information or content he/she gathered. Although passive attacks do not harm the system, they can be a danger for the confidentiality of the message. In the below image, we can see the process of passive attacks. 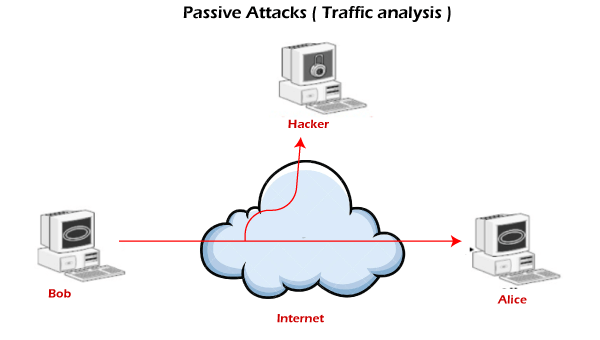
Unlike active attacks, in passive attacks, victims do not get informed about the attack. It is difficult to detect as there is no alteration in the message. Passive attacks can be prevented by using some encryption techniques. We can try the below-listed measures to prevent these attacks -
Active attack v/s Passive attack
Now, let's see the comparison chart between Active attack and Passive attack. We are comparing both security attacks on the basis of some characteristics.
Next TopicDifference between
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










