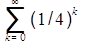|
33) A database of research articles in a journal uses the following schema. ( VOLUME , NUMBER , START PAGE , ENDPAGE , TITLE , YEAR , PRICE ) The primary key is (VOLUME , NUMBER , START PAGE , ENDPAGE ) and the following functional dependencies exist in the schema. (VOLUME , NUMBER , STARTPAGE , ENDPAGE ) → TITLE The database is redesigned to use the following schemas. (VOLUME , NUMBER , STARTPAGE , ENDPAGE , TITLE , PRICE ) Which is the weakest normal form that the new database satisfies, but the old one does not?
Answer: B Explanation: The Old relation schema design is in 1NF because it has functional dependency: Volume, Number → Year as a partial dependency so the original database design is in 1NF but not in 2NF. Now, the new relation schema design removes all partial dependencies, so it is in 2NF as well as in 3NF. Therefore, 2NF is the weakest normal form that the new database satisfies, but the old database does not. Hence option(B) is the right answer. 34) Which one of the following protocols is NOT used to resolve one form of address to another one?
Answer: C Explanation: A) DNS - It converts domains or hostname to IP address B) ARP - It converts IP to MAC address C) RARP - It converts MAC to IP address D) DHCP - It assigns IP dynamically. So, it doesn't resolve any addresses. Therefore, option (C) is the correct Answer. 35) Which of the following is/are example(s) of stateful application layer protocols? (i) HTTP
Answer: C Explanation: A Stateless Protocol doesn't maintain information about a transaction after a transaction is processed. There is no tight dependency between client and server. Example: HTTP A Stateful Protocol kept information about a transaction even after a transaction has been processed. There is a tight dependency between client and server. Example: FTP, POP3 Therefore option (C) is the right answer. 36) The coefficient of x12 in (x3 + x4 + x5 + x6 + • • • )3 is __________.
Answer: C Explanation: The coefficient of x12 is: The coefficient of x12 is: 1+ 3 + 6 = 10 37) Consider the recurrence relation a1 = 8, an = 6n2 + 2n + an-1. Let a99 = K × 104 . The value of K is __________.
Answer: B Explanation: an = 6n2 + 2n + an-1 So, for n = 99, Therefore option (B) is the correct answer. 38) A function f : N+ → N+ , defined on the set of positive integers N+, satisfies the following properties: f (n) = f (n/2) if n is even Let R = {i | ∃ j : f ( j) = i} be the set of distinct values that f takes. The maximum possible size of R is __________.
Answer: A Explanation: Assume: f(1) = a. Then, Hence the given function will have two values, i.e. a and b. All multiples of 5 will have value b and others will have value a. So the above function has two values only. Therefore option (A) is the right answer. 39) Consider the following experiment. Step 1. Flip a fair coin twice. The probability that the output of the experiment is Y is (up to two decimal places) __________.
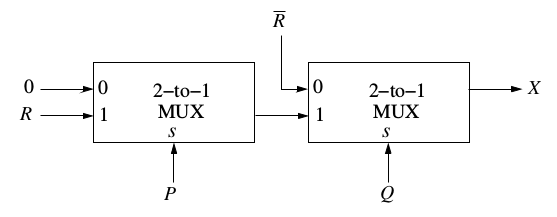
Answer: A Explanation: According to the question, = 1/4 = 1/4 / 1-1/4 (GP =a / (1-r)) Therefore option (A) is the correct answer. 40) Consider the two cascaded 2-to-1 multiplexers as shown in the figure.
The minimal sum of products form of the output X is
Answer: D Explanation: Solving first multiplexer (f1), we get GATE 2016 CS Set 1-1 GATE 2016 CS Set 1-2 GATE 2016 CS Set 1-3 GATE 2016 CS Set 1-4 GATE 2016 CS Set 1-6 GATE 2016 CS Set 1-7 GATE 2016 CS Set 1-8
Next TopicGATE 2016 CS Set 1-6
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share