Cryptosystem Project in JavaCryptosystem is responsible for encrypting the user's data and provide a secure mechanism to store it in a virtual drive. The virtual drive will be created by the system for the particular user for the very first while using the system. The system provides limited storage area where the data can be saved. As we can say that, it's a cloud storage medium where data can be accessed from any location. It also enables us to synchronize our desktop or laptop while using this cryptosystem. 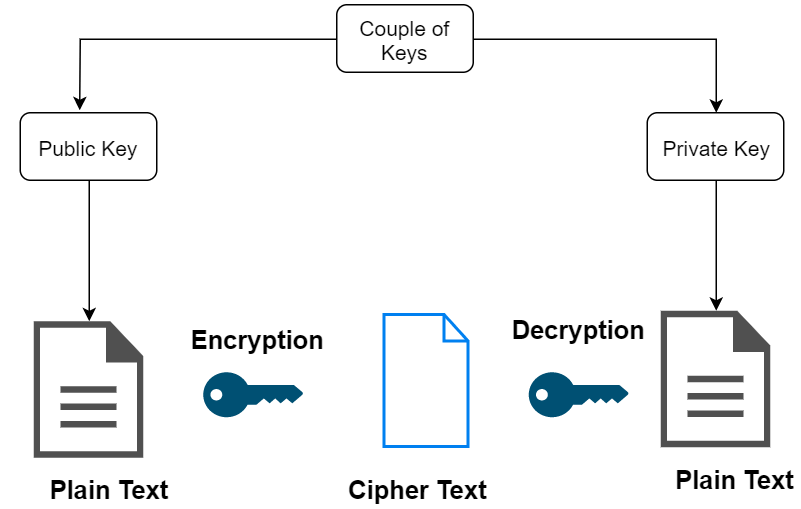
Cryptography PrimitivesCryptography primitives are nothing but the tools and techniques in Cryptography that can be selectively used to provide a set of desired security services
The Java Cryptography Architecture (JCA) is a set of APIs to implement concepts of modern cryptography such as digital signatures, message digests, certificates, encryption, key generation and secure random number generation, etc. By using JCA developers can build their applications by integrating security into them. To integrate security in our applications rather than depending on the complicated security algorithms we can easily call the respective APIs provided in JCA for required services. Java Cryptography Encrypting and Decrypting DataWe can encrypt and decrypt the data using the cipher class of the javax.crypto package. Follow the steps given below to decrypt using Java. Step 1: Create a KeyPairGenerator object The KeyPairGenerator class provides getInstance() method that accepts a String variable representing the required key-generating algorithm and returns a KeyPairGenerator object that generates keys. Create the KeyPairGenerator object using the getInstance() method as shown below. Step 2: Initialize the KeyPairGenerator object The KeyPairGenerator class provides a method named initialize(). It is used to generate key and pair. It accepts an integer value representing the key size. Initialize the KeyPairGenerator object created in the previous step using the initialize() method as shown below. Step 3: Generate the KeyPairGenerator We can generate the KeyPair using the generateKeyPair() method of the KeyPairGenerator class. Step 4: Get the public key We can get the public key from the generated KeyPair object using the getPublic() method as shown below. Step 5: Create a Cipher object The getInstance() method of the Cipher class accepts a String variable representing the required transformation and returns a Cipher object that implements the given transformation. Create the Cipher object using the getInstance() method as shown below. Step 6: Initialize the Cipher object The init() method of the Cipher class accepts two parameters. An integer parameter representing the operation mode (encrypt/decrypt) and Key object representing the public key. Step 7: Add data to the Cipher object The update() method of the Cipher class accepts a byte array representing the data to be encrypted and updates the current object with the data given. Update the initialized Cipher object by passing the data to the update() method in the form of byte array as shown below. Step 8: Encrypt the data The doFinal() method of the Cipher class completes the encryption operation. Therefore, finish the encryption using this method as shown below. Step 9: Initialize the Cipher object for decryption To decrypt the cipher encrypted in the previous steps we need to initialize it for decryption. Therefore, initialize the cipher object by passing the parameters Cipher.DECRYPT_MODE and PrivateKey object as shown below. Step 10: Decrypt the data Finally, Decrypt the encrypted text using the doFinal() method as shown below. Advantages of Asymmetric Cryptography
Disadvantages of Asymmetric Cryptography
Common Security ChallengesManaging keys is a hot issue, especially when dealing with access rights to the data, the legal ramifications of outsourcing, and how risks are mitigated. Common questions we hear: How do I protect my company? We have moved to the cloud, but who is the actual owner of the data? What protections do I have in the cloud? What happens if I have all my information, including my cryptographic keys in a certain cloud provider, and they get subpoenaed? What happens to the data if my organization gets subpoenaed? Other cloud and security considerations are single-source cloud provider or multi-cloud; how data is moved; and how organizations maintain control of the data while keeping it secure. Cryptosystem.java Output: Decrypted plaintext: This is a secret message. ConclusionAt the end of the day, organizations want to improve their data security. Many organizations have been taking a minimalist approach to their key management until recently. As organizations grow, many find it challenging to build out their cryptographic architecture to manage PKI, identity management, and data at rest. They must untwine some bad habits, particularly concerning key and certificate management, to build for today but also plan for tomorrow.
Next TopicFarthest from Zero Program in Java
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









