Web Server, Proxies and their role in Designing System
Introduction
The notion of web server proxies has evolved as a cornerstone in developing durable, preformat, and secures applications in the realms of current web development and system architecture. As the digital world gets more complex, the strategic deployment of web server proxies has gained popularity for optimizing resource usage, boosting security measures, and creating an effective bridge between clients and backend servers. In this exploration, we'll dig into the realm of web server proxies, shining light on their many varieties and exposing the critical role they play in defining today's systems.
Understanding Web Server Proxies' Importance
Web server proxies are the intermediary agents that sit between client devices and backend servers, directing requests and answers to their correct destinations. The basic idea behind these proxies is their capacity to intercept client requests, route them to appropriate servers, and send replies back to the clients. Importantly, this orchestration occurs invisibly, insulating end-users from the complexities and making the proxy's contribution visible.
Uncovering the Varieties: Web Server Proxies
Dive into the world of web server proxies to discover a variety of sorts, each adapted to certain needs and challenges:
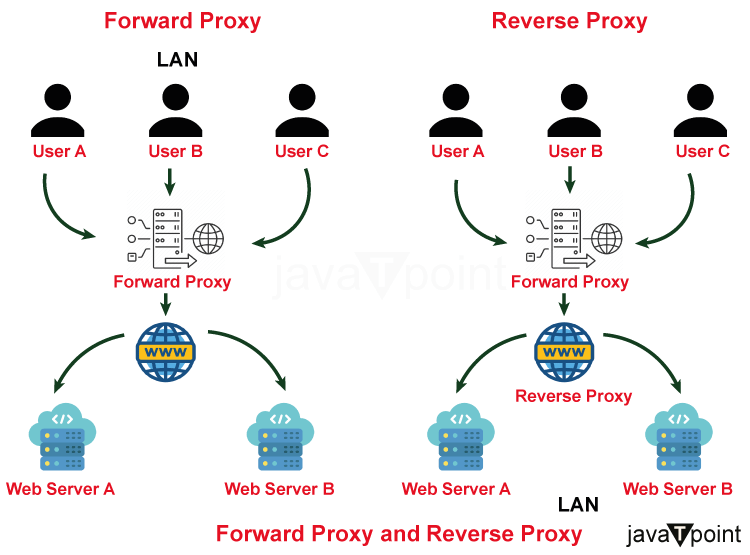
- Reverse Proxies: The reverse proxy, a gatekeeper who handles incoming client requests, is at the forefront. The reverse proxy is in charge of routing these requests among many backend servers. This load distribution not only minimizes server overload but also provides high availability by routing traffic to operational servers in the event of a breakdown. Furthermore, reverse proxies frequently have the ability to handle duties such as SSL termination, compression, and caching, relieving backend servers of these obligations.
- Forward Proxies: Forward proxies, on the other hand, swing towards the client side, functioning as guardians between client devices and the broad internet expanse. They serve as a gateway for outward traffic, ensuring adherence to security regulations, monitoring user activity, and facilitating content screening. Forward proxies decrease the need for repeated external requests, improving speed and overall efficiency.
- Load Balancers: Although not strictly proxies, load balancers work in tandem with reverse proxies to spread incoming client requests uniformly over numerous backend servers. This balanced distribution reduces the likelihood of server bottlenecks and supports optimal system performance. Load balancers absorb variable traffic loads and guarantee that no one server is overworked by using methods like round-robin, least connections, or weighted distribution.
Web Server Decoding
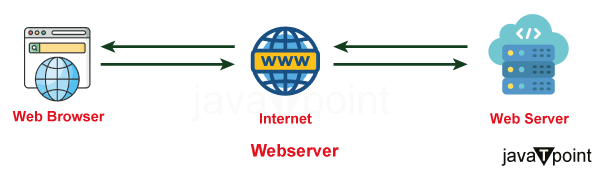
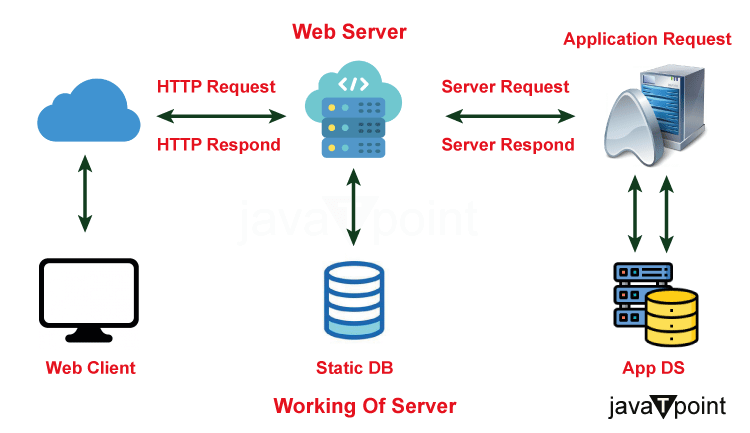
A web server is, at its core, specialized software that responds to client requests for online resources, which might be HTML pages, photos, videos, or other material. It receives incoming requests, processes them, and then delivers the required resources to the client's browser. The internet as we know it now is built on this seamless connection.
Web Server Features
To maintain a pleasant and responsive online experience, web servers wear several hats:
- Request Handling: A web server's primary responsibility is to manage incoming HTTP requests from clients, most notably web browsers. It parses these requests, identifies the resource sought, and prepares to provide it.
- Load Balancing: Multiple web servers can be installed behind a load balancer in high-traffic settings. To avoid overcrowding and to guarantee optimal resource use, the load balancer distributes incoming requests across various servers.
- Caching: To increase response times and minimize the demand on backend services, web servers might cache frequently visited material. For a brief period, cached material might comprise static files or even dynamic content.
- Security: Web servers contribute to security by imposing access rules, managing SSL/TLS encryption for secure communication (HTTPS), and defending against many forms of assaults such as DDoS and SQL injection.
- Monitoring and logging: Web servers create logs that offer information about server performance, user activity, faults, and security incidents. Monitoring these logs aids in the diagnosis of problems and the optimization of the system.
Types of web servers
There are various commonly used web servers for serving online content and applications. Here are some well-known web server examples:
- Apache HTTP Server (Apache): Apache is one of the most popular and well-known web servers. Because it is open-source and extremely adaptable, it may be used for a wide range of applications. Apache provides a variety of modules that may be added to enhance its capabilities, such as SSL/TLS, URL rewriting, and authentication.
- Nginx: Nginx is another well-known open-source web server that is well-known for its performance and scalability. In addition to providing static and dynamic content, it is frequently used as a reverse proxy and load balancer. Nginx is well-known for its ability to handle concurrent connections and is frequently used for high-traffic websites.
- Microsoft Internet Information Services (IIS): IIS is a Microsoft web server designed for Windows operating systems. It is strongly connected with Windows Server and includes capabilities like as ASP.NET application support, Windows authentication, and connectivity with other Microsoft technologies.
- LiteSpeed Web Server: LiteSpeed is a high-performance web server built for business use. It is well-known for its speed, security features, and capacity to efficiently manage high numbers of concurrent connections.
- Caddy: Caddy is a contemporary, open-source web server that prioritizes usability and automated HTTPS configuration using Let's Encrypt certificates. It's intended to make the process of putting up secure websites easier, with features like automated HTTPS, HTTP/2, and simple configuration.
The Role of Web Server Proxies
Web server proxies provide a slew of benefits that have a big impact on current system design:
- Scalability and Load Distribution: The strength of proxies, particularly reverse proxies and load balancers, resides in their capacity to distribute incoming requests over several servers. This orchestration prevents server overload, allowing systems to scale gracefully and adjust to variable demand.
- Caching and Fast Content Delivery: The caching capabilities of proxies, particularly forward proxies, provide speed to content delivery. Proxies speed up the user experience by storing frequently requested material.
- Increased Security and Privacy: Forward proxies serve as sentinels, bolstering security by acting as mediators between clients and the open internet. They mask client IP addresses, impose access limits, and filter out harmful information, forming a barrier against possible dangers.
- SSL Termination for Performance: SSL termination is handled by reverse proxies, relieving backend servers of the resource-intensive encryption and decryption operations. This enhancement boosts server speed while simplifies SSL certificate handling.
High Availability is ensured by the symbiotic relationship between reverse proxies and load balancers. When servers fail, these proxies automatically divert traffic to healthy alternatives, minimizing downtime and ensuring continuous operation.
Proxies serve as observatories, catching and logging incoming and outgoing communications. This single view enables administrators to spot bottlenecks, analyze security issues, and understand use trends.
Why proxies are useful?
Proxies are useful for a variety of reasons, including improved security and privacy, improved network speed, and easier resource management. Here are some of the main reasons why proxies are useful:
- Anonymity and security: Proxies can operate as a buffer between clients and servers, screening out harmful requests and assisting in the prevention of attacks such as Distributed Denial of Service (DDoS), Cross-Site Scripting (XSS), and SQL injection.
- Identity Concealment: Some proxies conceal clients' IP addresses, giving an additional degree of anonymity and privacy that might be advantageous when users want to use the internet without disclosing their genuine identities or locations.
- Access Control and Content Filtering: Proxies can filter out undesired or hazardous information before it reaches customers, safeguarding consumers from potentially malicious websites or viruses.
- Policy Enforcement: Proxies can implement access control policies, limiting access to specific websites or categories of material, which is especially beneficial in business or educational environments.
- Content Delivery and Caching: Caching proxies cache copies of frequently requested material locally, eliminating the need to fetch resources from remote servers. This results in faster user load times and less demand on origin servers.
- Reduced Bandwidth Consumption: By providing cached material, proxies can drastically reduce the amount of data carried over the network, optimizing bandwidth use and cutting expenses.
- High availability and load balancing: Load balancer proxies spread incoming requests over numerous backend servers, ensuring balanced load distribution and avoiding any single server from getting overburdened.
- Fault Tolerance: In the event of a server failure, load balancer proxies can redirect traffic to healthy servers, ensuring high availability while reducing downtime.
- Optimization of Network Performance: Proxies can compress online material before providing it to clients, lowering data transmission and improving page load speeds, particularly on sluggish connections. Proxies can translate between multiple network protocols, allowing clients and servers that use incompatible protocols to connect successfully.
- GSLB (Global Server Load Balancing): Geographical Redirection: GSLB proxies can route users to the closest server based on their geographical location, boosting performance and lowering latency.
- SSL Expiration: Reverse proxies can perform SSL/TLS encryption and decryption, offloading resource-intensive processes from backend servers and simplifying SSL certificate maintenance.
- Manipulation and Transformation of Content: Proxies may change or convert material on the fly, such as resizing pictures or adapting information for different devices (responsive design).
- Monitoring and logging of network traffic: Proxies can give complete logs and information about network traffic, enabling administrators to monitor use trends, identify problems, and optimize performance.
Advantages and disadvantages of proxy server
Depending on the context and use case, proxy servers provide a variety of benefits and drawbacks. Here's a rundown of the primary advantages and disadvantages:
Advantages:
- Privacy and Anonymity: Proxy servers can conceal the user's true IP address, offering an additional degree of anonymity and privacy. This is very beneficial for ensuring privacy and preventing internet monitoring.
- Content Filtering: Organizations can employ proxy servers to limit access to specified websites or content categories. This is frequently done to guarantee that staff or users follow corporate standards and that resources are not misused.
- Faster Access: Caching proxies cache copies of frequently requested sites locally. This shortens the time it takes to retrieve data from the internet, resulting in speedier load times for consumers.
- Bandwidth Savings: By caching and providing material locally, proxy servers can minimize the amount of bandwidth necessary for numerous users to access the same content, thereby saving money.
- Proxies can impose authentication protocols, requiring users to check in before gaining access to specified sites. This aids in limiting who has access to certain services.
- protection: Reverse proxy servers can serve as a buffer between the internet and internal servers, adding an extra layer of protection by concealing server IP addresses and aiding in the mitigation of certain types of assaults.
Disadvantages:
- Single Point of Failure: If a proxy server fails or has problems, it can impair internet access for all users that rely on it, potentially resulting in considerable downtime.
- Performance bottlenecks: If a proxy server is not correctly configured or does not have enough resources, it might create a performance bottleneck, slowing down rather than speeding up internet access.
- Complex Configuration: Setting up and configuring proxy servers can be difficult, necessitating technical knowledge. Incorrect setting might result in security flaws or operational difficulties.
- Limited Security: While proxy servers can provide security benefits, they can not replace specialized security solutions like as firewalls and intrusion detection systems.
- problems with logging and privacy: Some proxy servers track user activities, which might cause privacy problems. These logs may include sensitive information that might be abused if not properly maintained.
- Circumvention: While proxy servers might limit access to certain content, dedicated individuals may find ways to circumvent these limitations, possibly undermining the intended policy.
- Out dated Caches: Cached material may become outdated, resulting in users obtaining old or erroneous information if the proxy server does not update its cache on a regular basis.
proxy servers provide a variety of benefits such as privacy, content filtering, and security advances, but they also have possible drawbacks such as configuration complexity, performance concerns, and limits in full security coverage. The decision to employ a proxy server should be based on the organization's or individual's particular needs and goals.
How proxies are designed ?
A proxy must be designed with certain factors in mind to guarantee that it fulfills its intended duties properly. The design process might differ depending on the needs, use cases, and technology involved. Here's a high-level overview of the stages needed in creating a proxy:
- Determine the Use Case and Requirements: Recognize the proxy's function. Determine if the proxy is forward (client-side) or reverse (server-side). Determine the needs for security, speed, caching, load balancing, content filtering, and so forth.
- Select Proxy Type and Technology: Based on the use case, select the appropriate proxy type (e.g., HTTP, SOCKS, SSL, transparent). Select the appropriate technological stack and tools, such as Nginx, Apache, HAProxy, Squid, and so on.
- Architecture and Network Topology: Determine the network topology in which the proxy will be implemented. Consider if the setup is a single proxy or distributed. Determine the proxy's placement inside the network architecture.
- Proxy Server Configuration: Set the proxy server's authorized protocols, port numbers, logging, access control rules, security methods, and any other features needed (e.g., caching, compression).
- Load Balancing and Routing: Set up routing rules to disperse incoming traffic over many backend servers if the proxy is used for load balancing. Choose a load balance algorithm (round-robin, least connections, etc.).
- Security Measures: Use authentication (basic, token-based, OAuth), SSL/TLS encryption, IP whitelisting/blacklisting, and content filtering as needed.
- Caching Strategy: If caching is necessary, specify caching policies, expiration rules, and cache eviction techniques based on the content type. Choose whether material should be cached on the proxy or sent to backend servers.
- Performance Optimization: To maximize performance and decrease latency, configure options such as connection pooling, connection timeouts, and keep-alive techniques.
- Monitoring and Logging: Configure monitoring tools to monitor proxy performance, traffic trends, and possible problems. Set up logging to gather useful data for troubleshooting and analysis.
- Scalability and redundancy: Make the proxy scalable by taking into account aspects such as the number of users, traffic volume, and possible expansion. To provide high availability, use redundancy and failover techniques.
- Testing and Deployment: Before deploying the proxy to a production environment, thoroughly test it in a controlled environment. To discover and fix any flaws, do load testing, security testing, and usability testing.
- Documentation: Write detailed instructions for configuring, administering, and troubleshooting the proxy. Both administrators and users should have easy access to this documentation.
- Maintenance and updates: Monitor and maintain the proxy on a regular basis to ensure it continues to satisfy the criteria. Apply security updates, update settings, and make any necessary adjustments.
Conclusion
The integration of web servers and proxies in system design allows for the building of strong, scalable, and secure infrastructures. These components assist to the creation of efficient and dependable web-based services by spreading workloads, improving content delivery, strengthening security, and providing caching techniques. The particular design decisions are determined by the system's goals, needs, and technology.
|




 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










