What is a Magic Link?Magic links are URLs containing embedded tokens that allow users to log in without entering a password. These links are often delivered to the user's email account, but they can also be distributed over SMS as well as additional messaging systems such as WhatsApp. Magic link authentication, when used effectively, substantially enhances the user experience, lowers turnover caused by forgotten login credentials, and improves app conversions. Users recognize magic links because they have previously dealt with similar (albeit significantly unhappier) flows when they've reset their password. They also function similarly to single-use passwords (OTP), except that they are links rather than numerical PINs. Since magic links eliminate the challenges linked to passwords, they do introduce some new security risks. As a result, magic links are occasionally used in a multi-factor authorization (MFA) technique to boost security. What is a magic link with no password?A no-password magic link enables you to get in instantly using an email link. This procedure is similar to receiving a one-time password (OTP), except you may be required to actually input the OTP once redirected to the appropriate page and application. In the circumstance of anonymous magic links, all one has to do is act upon clicking on the link given by email, which will allow you to log in immediately. Benefits of magic linksBy adding the magic link function to your smartphone applications or email addresses, you are most likely attempting to make your app or site easier to use while also contributing to a robust security approach. Here are some of the reasons why you should use passwordless magic links. Perfect for infrequent login requirements: At the start of every user session, a password-free system magic link is issued to validate the user on a one-time basis. This form of magic link registration implementation is particularly suited for mobile apps or email account login processes requiring single or infrequent authentication, allowing easy access. Prevent password-based attacks: In today's world, data breaches, security breaches, and phishing are all on the rise. There has been a significant loss of required credentials, so magic link password security assures their safety by preventing security concerns involving passwords. How does magic link authentication work?This is what consumers see when they use magic link authentication:
The straightforwardness of the preceding procedures is most likely how the term "magic" developed. However, there are a couple more things going on behind the scenes. Here's how magic links operate in more detail:
If the preceding stages sound familiar, it's because they're quite similar to what occurs during the reset of password flows. Whereas password reset links direct users to a page where they may generate a new username, password magic links offer users access to resources. Many applications, like Medium and Slack, have utilized magic link authentication. 
Examples of how magic links can be usedThe Slack app is one of the most well-known examples of magic links. The magic link forms a component of the online login procedure and is promoted by a prominent "Send Magic Link" button.
Scenario in which a rapid and easy setup of accounts is desired: Password-based verification slows down the creation of accounts. You're going to need to force end users to develop complicated passwords as the necessity for ever more secure passwords grows because of the fast increase in password-based assaults. Magic links eliminate the need for that. Magic Links' user experience is unquestionably inadequate. To begin with, your users may never receive the magic link. The email may be considered spam by the user's email provider, requiring the user who received it to check their spam folders. There may be a delay while waiting to receive the link, in which case the user is simply left waiting and unable to finish their work. So, while magic links appear to be a simple way to create passwordless authentication, they are neither flawless nor totally safe. Magic linkages pose security risksMagic links are designed to make login quicker and more secure. However, each of the factors that make magic connections appealing for passwordless authentication has severe security implications: Some of you should always authenticate your usersThe magic link is a once-only login authentication. The user is now regarded as "trusted," and he or she will most likely not need to authenticate again. In today's dangerous environment, this is a recipe for disaster. Organizations should apply zero-trust ideas, which necessitate constant user verification, and place no faith in anyone. There's no need for the magic link when you're utilizing device authentication. There are authentication systems that do this and enable true passwordless authentication without requiring the user to leave the login screen. Though magic links are a significant step towards ultimately removing a username and password, there are other options available. There is no guarantee that the person who receives the magical connection is who they claim to be. If a user's email account has been compromised, a hacker may intercept the magic connection message and use it to obtain access. Magic links function so long as the token received matches what the web server expects. What is a more reliable and secure method of customer authentication?Since magic links appear to be an improved way to authenticate users without using passwords, there's a better approach for implementing passwordless authentication that genuinely safeguards your clients while giving an effortless user experience. Passwordless verification, device authorization, and risk-based authentication should all be integrated into a single, safe authentication platform. As a result, we developed our client's authentication solution. Our platform incorporates the zero-trust philosophy of "don't trust, always verify." Using invisible, passwordless MFA, our technology constantly confirms the user throughout an interaction while monitoring for over a dozen factors that may indicate difficulty. This enables you to safeguard your consumers without requiring them to go through any authentication procedures. You just need to authenticate a user twice with a magic link. Without actively watching these users for unusual behavior, you won't know if their device has been infected with malware until it's too late. Using magic links in your applicationMagic links are an excellent method to deliver an easy user experience for your clients without jeopardizing their account security. Is employing magic links the best option for authenticating users in your application? It most likely depends on what the application does. Magic connections may not be the best option if you work with confidential commercial or health care data. If you deal with customer apps in amusement and online retail, you're probably fine to go! Advantages and disadvantages of magic linksMagic connections provide several benefits in terms of customer service, account security, and technological backend enhancements. At the exact same time, magic linkages are not without flaws. There are various considerations you should make before adopting them. The following are the primary advantages of employing magic links:
Understanding the magical link disadvantages:
Tips for improving the effectiveness of your magical link emailsYou want to use magic links for authentication in your product. Here are a few pointers to help you create an excellent customer experience while minimizing risks: 1. Provide links that are only valid once. Allowing magic links to be used only once is one method for keeping them secure and effective. Configuring your magic links for one-time use prevents both authorized and unauthorized distribution. This is a wise practice in many situations, particularly when employing magic links to provide users access to sensitive or confidential information. 2. Implement two-factor authentication (MFA). We discussed how magic links have certain inherent flaws because they depend on the user's primary email address's security. If that address is hacked, hackers can easily steal single-factor magic links and acquire unauthorized access to the corresponding services and tools. Multi-factor authentication (MFA) significantly decreases these dangers by demanding extra confirmation that a person is who they say they are (in addition to email access). It adds a further level of protection to ensure that user logins remain secure. Even if the bad actors obtain access via the magic link, it is meaningless unless they additionally have access to the user's secondary form of identification (which may be text, fingerprinting, or any number of other techniques). If you're unsure where to begin using MFA, the WebAuthn architecture is a standards-based alternative worth exploring. 3. Configure link expiration dates. Another option to lessen the hazards connected with magic links is to establish expiration dates, which means that connections can remain valid for a period of time of your liking (1 hour is a frequent choice) before they deactivate automatically. If a user clicks an expired magic link, they'll usually be taken to a page where they may produce another one (or request that someone in management re-share availability for internal services like OneDrive). Expiration dates are thus relatively frictionless while preventing long-term accessibility if a link is stolen or shared. 
4. Include a meaningful, understandable subject line and "from" name. When someone decides to give themselves an encrypted link, they usually go straight to their email inbox to find it. If you send your magic links using an instant delivery service, your message will already be at the very top of their inbox. Still, you don't want consumers to have to guess what the email is about or who sent it. You wish it to be as unambiguous as feasible, and the subject tag and "From" name constitute two of the most effective methods for accomplishing this. 5. Continue to keep your emails simple. Magic link emails have a single goal: to induce recipients to sign in to the website or platform that produced the link. So, when writing the language for your magic link email model, avoid distracting readers with too much information or conflicting calls to action. Keep things simple, similar to your password-reset emails. This is not an area for promotion or upselling. Get straight to the point (and the reason is the magic link). The one exception is that it can be useful to include a statement regarding how to contact assistance if things aren't working as expected. Simply keep this message simple and place it underneath the magic link. 6. Do not allow message threading. Gmail and other email programmes have begun to group related communications into threads. If your magic links are dragged into threads, your users may become perplexed. They might end up hitting the initial magic link (which has now been deleted or expired) compared to the one you recently sent. Google offers two solutions for avoiding message threading: Use unique subject lines for each email; for example, you might dynamically insert the timestamp for the enchanted link search into the email's subject line. Choosing the Best Email Service for Magic Link SendingWhen you decide to create your own magic link authentication procedure, your sending email volume may increase dramatically, and your email reliability and punctuality will become increasingly important-so now is a good time to reconsider the company you use for transactional email. Consider the following while comparing services for sending magic links: 1. Speed It is critical that magic links be given as soon as possible. We've all waited about for far too long as account holders waiting for an email with password reset instructions to arrive, and it's not a good look for the firm we're attempting to conduct business with! 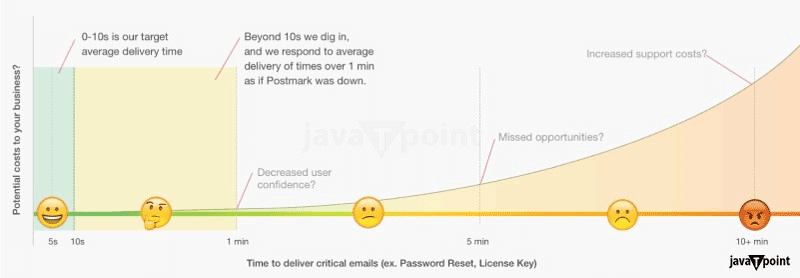
Postmark strives to deliver critical transactional emails in less than 10 seconds. On our status page, we also publish current time-to-inbox data. 2. Reliability Similarly, you require an email solution with consistent uptime and an established history of email deliverability. Customers will become irritated if your magic links just do not appear or are tagged as spam. Your supplier should also assist you in maintaining a good sender image so that your emails do not get blocked. A trademark, for example, will assist you in determining if an independent or common IP address will provide the optimum deliverability for your business. 3. Assistance with the guidelines, norms, and libraries you require Before you commit to a service, review the documentation to determine if it supports your favorite languages or frameworks for quick and easy email integration. You should also ensure that your email service supports the authentication procedures and standards you require, such as SPF. Postmark, for instance, makes it simple to apply SPF and gives useful tools to observe DMARC compliance. Before making a switch, be sure that you have access to what you require. 
How to Implement a Magic Link Flow in Your Application?Of course, if you want to create your own magic link procedure, the email is only one component. You must also take care of the following items:
Here's a more extensive walkthrough from Workos, complete with code samples. A portion of the hard work may already have been done according to the framework you're choosing to construct your app. Rails, for example, has some of the critical components required to make a magic link process function out of the box:
Do you want to implement a magic link process for authentication but don't want to put it together from scratch?We have a solution! Magic has developed a plug-and-play SDK that supports an assortment of passwordless login techniques, including SMS, MFA, WebAuthn, and others. It takes just a few lines of script to get started, and it's completely free! Magic is compatible with frameworks like Svelte and Next.js, as well as low-code platforms such as Webflow and WordPress. Furthermore, if you want to create a decentralized app that communicates with the most rapidly expanding platforms like Ethereum, Solana, and 18+ others, Magic's multichain compatibility is there for you. Using Magic Link Authentication, you can make your users' lives easier.Here, offer several key features to organizations seeking superior safety and management of identities for their personnel, one of which is passwordless authentication. Magic links can be used alongside robust identity administration, compliance verification of identity, and other authentication capabilities in the BlockID system. You get the following benefits from BlockID: Identity-Based Authentication: We bring biometrics and authentication together in a new "who you are" paradigm. Using credential triangulation and identity verification, BlockID identifies individuals rather than machines. Cloud-Native Architecture: Our cloud architecture is flexible and scalable, making it trivial to build applications utilizing our conventional API and SDK. Identity Verification: BlockID validates identity with more than ninety percent accuracy everywhere, at any time, and on any device. Privacy by Design: One of 1Kosmos' basic principles is to incorporate confidentiality into the construction of our ecosystem. In the distributed identity architecture, we protect personally identifying information, and protected data is restricted to use by the user. It is a private and authorized blockchain that secures personally identifiable information, encrypts online identities, and is only accessible by the user. The distributed qualities ensure that there are no vulnerable databases or honeypots for criminals to exploit. Interoperability: With its 50+ out-of-the-box connections or via API/SDK, BlockID can easily integrate with current infrastructure. SIM Binding: SMS validation, identity editing, and mobile phone authentication are all used by the BlockID programme to construct stable, robust, and secure connections. What are the challenges of employing magic links?Although magic links provide better security than passwords, they have some security flaws that must be addressed: The user's email account is linked to security. This introduces new security threats. Magic emails can be sent unsecured through mail servers and can be seen by staff at the user's email provider. Unattended devices also have easy access to user inboxes. Users have to safeguard their email addresses with multi-factor authentication to ensure the absolute security of magic emails. Link sharing is completely uncontrollable by administrators. Poor security behaviours, like weak passwords, expose vulnerabilities. There is no mechanism for administrators to see or restrict users from posting confidential connections with others. Attacks from the man in the-middle are possible. Hackers can intercept unsecured connections and grab the session tokens from a magic link if users do not access their emails across encrypted networks. ConclusionMagic links might not be the most dependable method of checking in, but they are undeniably a simple way for users to access their accounts. In today's fast-paced world, every type of validation must be done with extreme care, and a password-free system magic link is the ideal option. |
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










