How to Install Tor Browser in Ubuntu?Tor stands for The Onion Router. It is an open-source and free software to enable anonymous communication. It can manage internet traffic by a worldwide, free, volunteer overlay network composed of 7000+ relays to conceal the usage and location of a user from anyone implementing traffic analysis or network surveillance. Utilizing Tor makes it more complicated to trace the internet activity of a user. The intended use of Tor is to secure the personal privacy of its customers as well as their freedom and capability to confidentially communicate by IP address anonymity with Tor exit nodes. History of Tor BrowserOnion routing (Tor core principle) was integrated in mid-1990 by the US Naval Research Laboratory workers, computer scientists Michael G and mathematician Paul Syverson. Onion routing is operated by means of encryption in the communication protocol stack's application layer, nested like an onion layer. The Tor alpha version was developed by Nick Mathewson and Roger Dingledine and called the project, i.e., Onion Routing. It was announced on 20 September 2002. Various weaknesses of Tor have been discovered and exploited occasionally over its existence course. The Tor attacks are an active academy research area that is accepted by the Tor Project itself. Usage of Tor BrowserTor browser enables its users to browse the internet, anonymously send and chat instant messages, and use by a huge range of people for both illicit and licit goals. Tor has been used by law enforcement agencies, hacktivism groups, and criminal enterprises at cross goals, simultaneously sometimes; likewise, agencies in the US government mainly fund Tor and seek to corrupt it. Tor isn't meant to fully solve the problem of anonymity over the web. It is not designed to fully delete tracking but rather decrease the likelihood for several sites to data back and trace actions of the user. Also, Tor is used for several illegal activities. They can contain censorship circumvention or privacy protection, as well as malware distribution, drug sales, or child abuse content distribution. Operation of Tor BrowserTor aims to hide the online activities and identities of its users from traffic analysis and surveillance by isolating routing and identification. It is an onion routing implementation, which encrypts and bounces communications randomly from a relay network executed by volunteers across the globe. The onion routers apply encryption in a multi-layer way to guarantee perfect forward secrecy among relays. Hence, giving users anonymity inside a network location. This anonymity enhances the censorship-resistant content hosted by the onion service aspect of Tor. Furthermore, by keeping a few of the entry relays secret, users can avoid internet censorship that depends on blocking public relays of Tor. 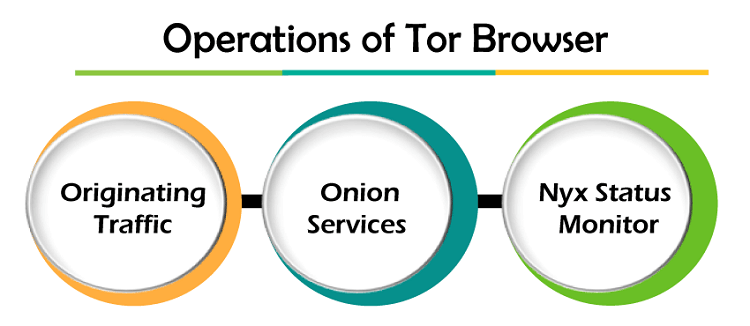
1. Originating trafficThe SOCKS-aware application of Tor users can be set up to manage their network traffic by the SOCKS interface of a Tor instance, which is listening on the 9050 or 9150 port of TCP at localhost. Periodically, Tor establishes virtual circuits by the Tor network from which it can onion-route that traffic to its target. The traffic is transferred from one router to another with the circuit once within a Tor network. Apart from almost every other anonymity network, the application independence of Tor sets it. It works at the TCP (Transmission Control Protocol) stream level. Software whose traffic is anonymized commonly with Tor includes World Wide Web browsing, instant messaging, and IRC (Internet Relay Chat). 2. Onion servicesAlso, Tor can give anonymity to several websites and servers. Servers set up to get inbound connections only from Tor are known as onion services (formerly called hidden services). Instead of revealing the IP address of a server, an onion service is used from its onion address by the Tor Browser. A Tor network knows these addresses by checking their corresponding introduction points and public keys through a distributed hash table inside the network. It can route data from and to onion services, those even hosted behind NAT (network address translators) or firewalls while preserving both party anonymity. Tor is essential to use these onion services. First, onion services were specified in 2003 and have been set up on the Tor network since 2004. Tor is decentralized by its design; no direct precise list of every onion service other than a database that can store the descriptors of the onion service. However, the catalog of several onion services is publicly called onion addresses. 3. Nyx status monitorFormerly, Nyx is known as ARM. It is a status monitor of the command line written for Tor in Python. This function offers real-time statistics for:
This project was started in the summer of 2009, and it has been a formal part of the Tor Project since 18 July 2010. It's a free application available with the GNU General Public License. Weaknesses of TorTor can't and doesn't try to protect against traffic monitoring at the Tor network boundaries like every current low-latency anonymity network. While Tor does offer protection from traffic analysis. It can't block traffic confirmation (also known as end-to-end correlation). 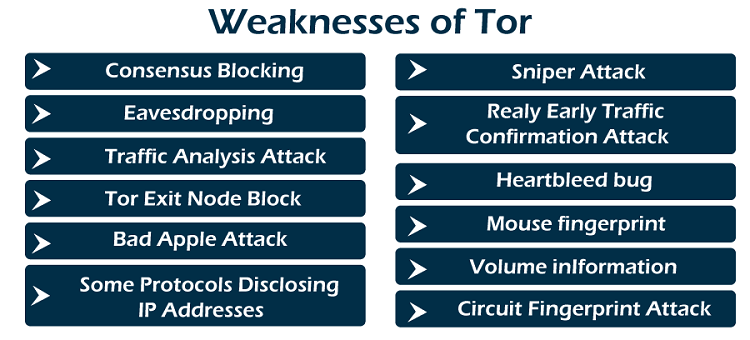
Consensus blocking Tor depends on a consensus mechanism to update its latest operating parameters periodically, like several decentralized systems, which are network parameters for Tor, like which node is bad/good relays, guards, exits, and how much traffic all can handle. The architecture of Tor to decide the consensus depends on some directory authority nodes voting on the latest network parameters. There are 10 directories coded into all Tor clients currently. The authority nodes vote each hour for updating the consensus, and every client downloads almost every latest consensus on the establishment. A network congestion attack, like a DDoS, can block the consensus nodes from negotiating and thus block voting for updating the consensus. Eavesdropping
Traffic analysis attack Two mechanisms of traffic analysis attack are available, active and passive. In the active traffic analysis mechanism, the attacker changes the flow packet timings according to a particular pattern and searches that pattern on another network side so the attacker can connect the flows on a single side to another network side and breach its anonymity. In the passive traffic analysis mechanism, the attacker extracts aspects from the traffic of a particular flow on a single side of the network and searches for those aspects on another network side. It is shown that there are many active traffic analysis mechanisms that are strong against like noise, although timing noise is included in the packets. Tor exit node block Internet site operators have the ability to block traffic to give decreased functionality or from Tor exit nodes for Tor users. For instance, it's not normally possible to change Wikipedia when utilizing Tor or an IP address that is also used by any Tor exit node. Bad apple attack With the Rocquencourt French Institute for Research in Computer Science and Automation, researchers documented an attack capable of displaying the BitTorrent user's IP addresses on the Tor network in March 2011. The "bad apple attack" takes the benefit of insecure applications and exploits the design of Tor used to connect the simultaneous use of any secure application with the Tor user IP address in question. An attack method relies on the control of hijacking tracker or exit node responses. Besides, a secondary attack method works according to a statistical exploitation part of distributed hash table tracking. Some protocols disclosing IP addresses From the French Institute for Research in Computer Science and Automation, researchers revealed that the Tor dissimulation method could be bypassed in BitTorrent by attackers controlling any Tor exit node. This study was planned by monitoring six different exit nodes for twenty-three days. Sniper attack Jansen defines a DDoS attack pointed at the Tor node application and defenses in opposition to that attack and many variants. This attack operates using a colluding server and client and filling the exit node queues until the node doesn't have memory. By attacking enough proportion of an exit node, an attacker can increase the target chances and corrupt the network with nodes managed by the attacker. Relay early traffic confirmation attack The Tor Project announced the "relay early traffic confirmation attack" security advisory in which the project recognized a relay group that attempted to de-anonymize onion service operators and users on 30 July 2014. The attacking directory node of the onion service modified the cell headers being relayed, identifying them as "relay early" or "relay" cells to encode extra information and transfer them back to the requesting operator or user. Heartbleed bug This OpenSSL bug disturbed the Tor network for many days in April 2014 while all private keys were re-established. The Tor Project suggested Tor onion service and relay operators invalidate and produce new keys after plotting OpenSSL. Mouse fingerprint In Barcelona, a security researcher represented laboratory techniques with time measurement by JavaScript at the 1-millisecond level, which could recognize and correlate a specific mouse movement of the users, offered the user has seen a similar "fingerprint" site with a regular browser and the Tor browser. The proof of concept accomplishes the "time measurement by JavaScript" problem, which had been a free ticket for ten months on the Tor project. Volume information A study represented "anonymization solutions defend only potentially against destination selection that may cause efficient surveillance" because they typically "don't cover up the volume information essential to implement destination selection". Circuit fingerprint attack The Agora administrators revealed that they were taking the website offline to a recently found security vulnerability in Tor in 2015. They didn't describe what the vulnerability was. However, Wired guessed it was the "Circuit Fingerprint Attack" illustrated at the Usenix security conference. Implementations of Tor BrowserThe primary Tor implementation is mainly written in C. 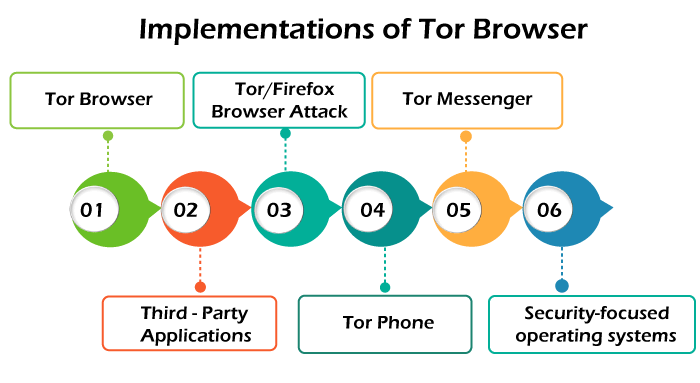
Tor BrowserIt is a web browser able to access the Tor network. The Tor browser was designed by Steven J. Murdoch and revealed in January 2008. It was composed of a changed Mozilla Firefox ESR browser, the Tor proxy, NoScript, TorLauncher, and TorButton. Users can use the Tor Browser from any removable media. It can work under Linux, Android, macOS, and Microsoft Windows. Tor/Firefox browser attackThe Dutch authority inspecting child pornography found a Tor onion service site IP address known as "Pedoboard" from the account of an unprotected administrator and offered it to the FBI. After a surveillance year, the FBI announced "Operation Torpedo" which outcome in the arrest of McGrath and permitted them to install their NIT (Network Investigative Technique) malware on the servers to retrieve information from the customers of the three onion service websites that McGrath managed. This technique, exploiting the vulnerability of a Tor/Firefox browser that had been patched and pointing users that had not upgraded, had a flash software pinging the IP address of a user back to an FBI server directly, resulting in disclosing at least 25 US customers and several customers from other countries. Tor MessengerThe Tor Project published Tor Messenger Beta on 29 October 2015. It is an instant messaging function based on Instantbird with OTR and Tor used and built-in by default. Like Adium and Pidgin, Tor Messenger supports several instant messaging protocols. Although it accomplishes it without depending on libpurple, working on every chat protocol in the memory-safe JavaScript language instead. Third-party applicationsTor support TorChat instant messenger, Bitmessage anonymous messaging system, and Vuze BitTorrent client. Users can share their files with Tor using OnionShare. The Guardian Project is developing an open-source and free suite of firmware and applications for the Android operating system to enhance mobile communication security. The applications contain the ChatSecure instant messaging client, ObscuraCam, ProxyMob Firefox add-on, Tor Browser mobile counterpart, Orfox, Orweb privacy-enhanced mobile browser, and Orbat Tor implementation. Onion Browser is a privacy-enhancing and open-source web browser for iOS. It uses Tor and is available on the iOS App Store. Its source code is present on GitHub. Brave supports Tor in the privacy-browsing mode of its desktop browser. Users can move to Tor-enabled browsing by pressing the hamburger menu on the browser. Tor PhoneMike Perry (Tor developer) announced a tor-enable smartphone prototype based on CopperheadOS in 2016. It was announced as a direction on mobile for tor. The project was known as "Mission Improbable". After that, Denial Micay (lead developer) was taken in the prototype. Security-focused operating systemsMany security-focused operating systems made or make massive use of Tor. They include Whonix, Tor-ramdisk, Tails, Subgraph, Qubes OS, Liberte Linux, Incognito, and Hardened Linux from Scratch. Installing Tor Browser on UbuntuNowadays, privacy is the highest concern. Tor browser is on top for those who want to keep their privacy and wish to endure anonymity on the Internet. Tor Browser assures our privacy by routing our traffic by the Tor network. In this article, we will discuss how we can install the Tor browser in the Ubuntu system. Step 1: Adding PPA Repository The Tor Browser's latest version is not available directly from the Linux Mint and Ubuntu repositories. We can download and install it on Linux Mint and Ubuntu with the help of the launcher script of the Tor browser. We will need a launcher script to guarantee the Tor browser installation. So, we need the following PPA repository for that purpose: 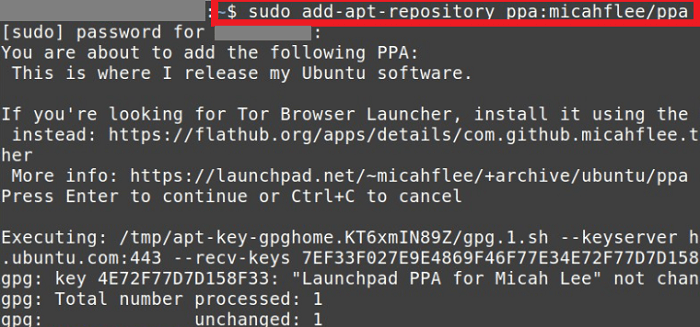
Step 2: Updating Repository Now, we will update our repository after adding PPA successfully: Step 3: Installing Tor Launcher We will install the Tor launcher with the help of the repository in this step: 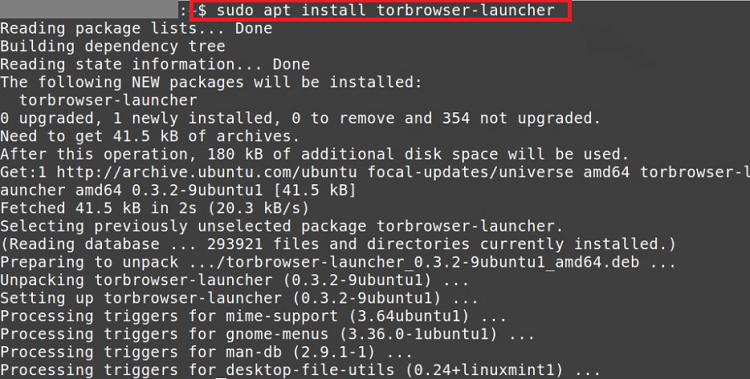
Step 4: Opening Tor Launcher We can either go to the application menu or the command line to open the Tor launcher once it is successfully downloaded and installed. We need to execute the below command to launch the Tor launcher using the command line: We need to press the application icon and find "Tor browser launcher" to launch it from the application menu. Step 5: Downloading in Installing Tor Browser-Related Dependencies We need to open our Tor browser launcher for downloading and installing Tor browser-related dependencies. Press the "Install Tor Browser" option, and it will get every related dependency automatically. How to uninstall Tor Browser?If you want to remove the Tor Browser at any point, we can execute the below command to do it: This command will successfully remove the Tor browser from our system.
Next TopicInstall Brave Browser Ubuntu
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










