Security TestingWhat is security testing?Security testing is an integral part of software testing, which is used to discover the weaknesses, risks, or threats in the software application and also help us to stop the nasty attack from the outsiders and make sure the security of our software applications. The primary objective of security testing is to find all the potential ambiguities and vulnerabilities of the application so that the software does not stop working. If we perform security testing, then it helps us to identify all the possible security threats and also help the programmer to fix those errors. It is a testing procedure, which is used to define that the data will be safe and also continue the working process of the software. Principle of Security testingHere, we will discuss the following aspects of security testing:
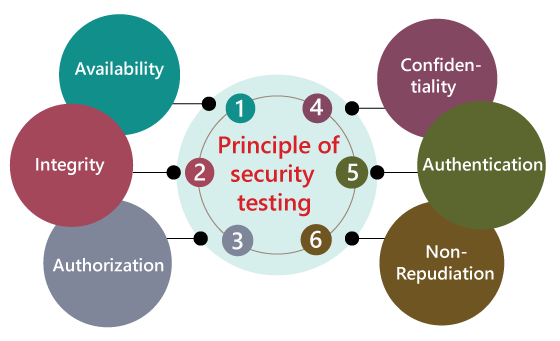
AvailabilityIn this, the data must be retained by an official person, and they also guarantee that the data and statement services will be ready to use whenever we need it. IntegrityIn this, we will secure those data which have been changed by the unofficial person. The primary objective of integrity is to permit the receiver to control the data that is given by the system.The integrity systems regularly use some of the similar fundamental approaches as confidentiality structures. Still, they generally include the data for the communication to create the source of an algorithmic check rather than encrypting all of the communication. And also verify that correct data is conveyed from one application to another. AuthorizationIt is the process of defining that a client is permitted to perform an action and also receive the services. The example of authorization is Access control. 
ConfidentialityIt is a security process that protracts the leak of the data from the outsider's because it is the only way where we can make sure the security of our data. AuthenticationThe authentication process comprises confirming the individuality of a person, tracing the source of a product that is necessary to allow access to the private information or the system. 
Non- repudiationIt is used as a reference to the digital security, and it a way of assurance that the sender of a message cannot disagree with having sent the message and that the recipient cannot repudiate having received the message. The non-repudiation is used to ensure that a conveyed message has been sent and received by the person who claims to have sent and received the message. Key Areas in Security TestingWhile performing the security testing on the web application, we need to concentrate on the following areas to test the application: 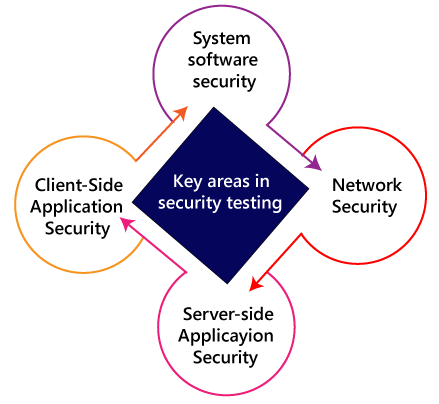
System software securityIn this, we will evaluate the vulnerabilities of the application based on different software such as Operating system, Database system, etc. Network securityIn this, we will check the weakness of the network structure, such as policies and resources. Server-side application securityWe will do the server-side application security to ensure that the server encryption and its tools are sufficient to protect the software from any disturbance. Client-side application securityIn this, we will make sure that any intruders cannot operate on any browser or any tool which is used by customers. Types of Security testingAs per Open Source Security Testing techniques, we have different types of security testing which as follows:
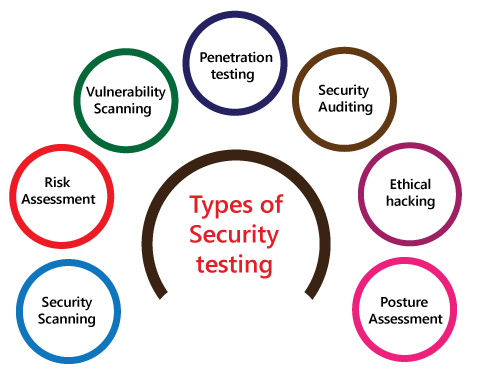
Security ScanningSecurity scanning can be done for both automation testing and manual testing. This scanning will be used to find the vulnerability or unwanted file modification in a web-based application, websites, network, or the file system. After that, it will deliver the results which help us to decrease those threats. Security scanning is needed for those systems, which depends on the structure they use. Risk AssessmentTo moderate the risk of an application, we will go for risk assessment. In this, we will explore the security risk, which can be detected in the association. The risk can be further divided into three parts, and those are high, medium, and low. The primary purpose of the risk assessment process is to assess the vulnerabilities and control the significant threat. Vulnerability ScanningIt is an application that is used to determine and generates a list of all the systems which contain the desktops, servers, laptops, virtual machines, printers, switches, and firewalls related to a network. The vulnerability scanning can be performed over the automated application and also identifies those software and systems which have acknowledged the security vulnerabilities. Penetration testingPenetration testing is a security implementation where a cyber-security professional tries to identify and exploit the weakness in the computer system. The primary objective of this testing is to simulate outbreaks and also finds the loophole in the system and similarly save from the intruders who can take the benefits. Security AuditingSecurity auditing is a structured method for evaluating the security measures of the organization. In this, we will do the inside review of the application and the control system for the security faults. Ethical hackingEthical hacking is used to discover the weakness in the system and also helps the organization to fix those security loopholes before the nasty hacker exposes them. The ethical hacking will help us to increase the security position of the association because sometimes the ethical hackers use the same tricks, tools, and techniques that nasty hackers will use, but with the approval of the official person. The objective of ethical hacking is to enhance security and to protect the systems from malicious users' attacks. Posture AssessmentIt is a combination of ethical hacking, risk assessments, and security scanning, which helps us to display the complete security posture of an organization. How we perform security testingThe security testing is needed to be done in the initial stages of the software development life cycle because if we perform security testing after the software execution stage and the deployment stage of the SDLC, it will cost us more. Now let us understand how we perform security testing parallel in each stage of the software development life cycle(SDLC). 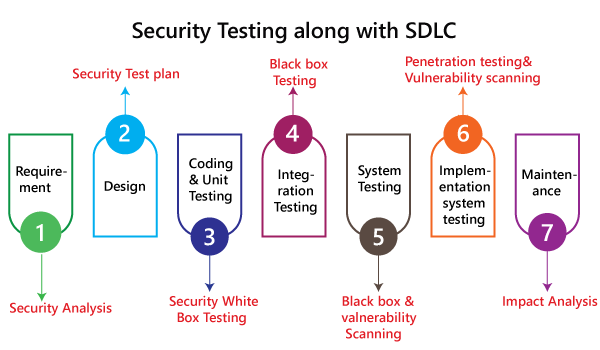
Step1 SDLC: Requirement stage Security Procedures: In the requirement phase of SDLC, we will do the security analysis of the business needs and also verify that which cases are manipulative and waste. Step2 SDLC: Design stage Security Procedures: In the design phase of SDLC, we will do the security testing for risk exploration of the design and also embraces the security tests at the development of the test plan. Step3 SDLC: Development or coding stage Security Procedures: In the coding phase of SDLC, we will perform the white box testing along with static and dynamic testing. Step4 SDLC: Testing (functional testing, integration testing, system testing) stage Security Procedures: In the testing phase of SDLC, we will do one round of vulnerability scanning along with black-box testing. Step 5 SDLC: Implementation stage Security Procedures: In the implementation phase of SDLC, we will perform vulnerability scanning again and also perform one round of penetration testing. Step 6 SDLC: Maintenance stage Security Procedures: In the Maintenance phase of SDLC, we will do the impact analysis of impact areas. And the test plan should contain the following:
Example of security testingGenerally, the type of security testing includes the problematic steps based on overthinking, but sometimes the simple tests will help us to uncover the most significant security threats. Let us see a sample example to understand how we do security testing on a web application:
Why security testing is essential for web applicationsAt present, web applications are growing day by day, and most of the web application is at risk. Here we are going to discuss some common weaknesses of the web application.
Client-side attacksThe client-side attack means that some illegitimate implementation of the external code occurs in the web application. And the data spoofing actions have occupied the place where the user believes that the particular data acting on the web application is valid, and it does not come from an external source. Note: Here, Spoofing is a trick to create duplicate websites or emails.AuthenticationIn this, the authentication will cover the outbreaks which aim to the web application methods of authenticating the user identity where the user account individualities will be stolen. The incomplete authentication will allow the attacker to access the functionality or sensitive data without performing the correct authentication. For example, the brute force attack, the primary purpose of brute force attack, is to gain access to a web application. Here, the invaders will attempt n-numbers of usernames and password repeatedly until it gets in because this is the most precise way to block brute-force attacks. After all, once they try all defined number of an incorrect password, the account will be locked automatically. AuthorizationThe authorization comes in the picture whenever some intruders are trying to retrieve the sensitive information from the web application illegally. For example, a perfect example of authorization is directory scanning. Here the directory scanning is the kind of outbreaks that deeds the defects into the webserver to achieve the illegal access to the folders and files which are not mentioned in the pubic area. And once the invaders succeed in getting access, they can download the delicate data and install the harmful software on the server. Command executionThe command execution is used when malicious attackers will control the web application. Logical attacksThe logical attacks are being used when the DoS (denial of service) outbreaks, avoid a web application from helping regular customer action and also restrict the application usage. Information disclosureThe information disclosures are used to show the sensitive data to the invaders, which means that it will cover bouts that planned to obtain precise information about the web application. Here the information leakage happens when a web application discloses the delicate data, like the error message or developer comments that might help the attacker for misusing the system. For example, the password is passing to the server, which means that the password should be encoded while being communicated over the network. Note: The web application needs more security regarding its access along with data security; that's why the web developer will make the application in such a way to protect the application from Brute Force Attacks, SQL Injections, Session Management, failure to Restrict URL Access and Cross-site scripting (XSS). And also, if the web application simplifies the remote access points, then it must be protected too. Here, Session management: It is used to check whether the cookies can be re-used in another computer system during the login stage. SQL injection: It is a code injection approach where the destructive SQL Statements are implanted into some queries, and it is implemented by the server. Cross-site scripting (XSS): This is the technique through which the user introduces client-side script or the HTML in the user-interface of a web application and those additions are visible to other users. Myths and Facts of Security testingHere, we will discuss the Myths and facts of security testing:
Security testing toolsWe have various security testing tools available in the market, which are as follows:
For more information about these tools, refer to the below link: https://www.javatpoint.com/security-testing-tools ConclusionFor an application or the software, it is necessary to perform security testing to verify that the sensitive information is still private. In software testing, the security testing is essential because it helps us to save our necessary data ultimately. In this, the test engineer will act as an invader and test the system or detect the security defects.
Next TopicAccessibility testing
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









