Wordlist crackingTo crack WPA or WPA2, we need to first capture the handshake from the target AP and second have a wordlist which contains a number of passwords that we are going to try. Now we've captured the handshake, and we have a wordlist ready to use. Now we can use aircrack-ng to crack the key for the target AP. The aircrack-ng will be going through the wordlist file, combine each password with the name of the target AP, and create a Pairwise Master Key(PMK) . This PMK is created by using an algorithm called PBKDF2. It is not like just combining the password and the BSSID. It is encrypted in certain way, and compare the PMK to the handshake. The password that was used is the password for the target AP if the PMK is valid. If the PMK wasn't valid, then aircrack-ng tries the next password. We will use aircrack-ng, the file name that contains the handshake, wep_handshake-01.cap, -w and the name of the wordlist, text.txt. The command is as follows: 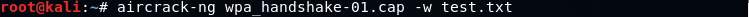
Now click Enter, and aircrack-ng is going to go through the list of the password. It will try all of the passwords, and will combine each password with the name of the target AP to create a PMK, then compare the PMK to the handshake. If the PMK is valid, then the password that was used to create the PMK is the password for the target AP. If the PMK is not valid, then it's just going to try the next password. In the following screenshot, we can see that the key was found: 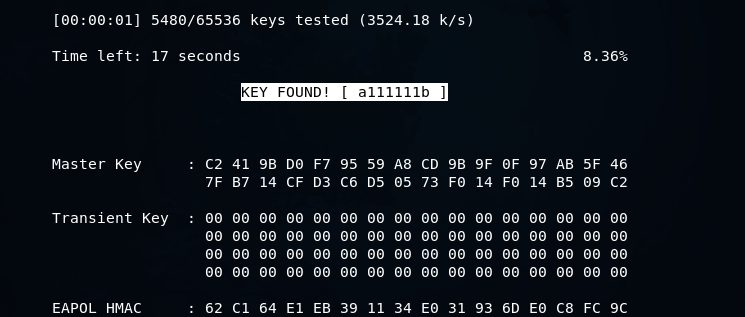
Next TopicSecuring Network from Attacks
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









