Overview of PayloadsOnce Veil is installed, we are going to look at its commands. The commands are straightforward as shown in the following screenshot. The exit allow us to exit the program, info is used to provide us the information about a specific tool, list is used to list the available tools, update is used to update Veil, use is used to enable the use of any tool, as shown in the given screenshot: 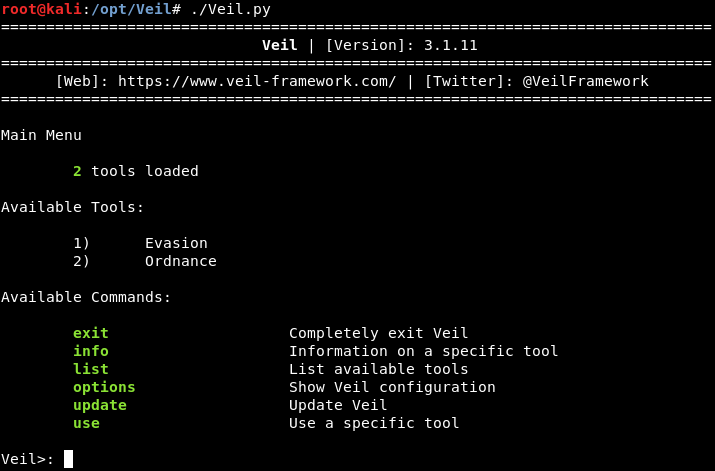
In the above screenshot, we can see that there are two types of tools that are used in the Veil:
The payload is a part of the code, that does what we want it to. In this case, it gives us a reverse connection, downloads and executes something on a target computer. Now we are using the use command to enable the use of any tool. We want to run Evasion, so we are going to run use 1 command. When Veil-Evasion has loaded, we should see something similar to the following command: 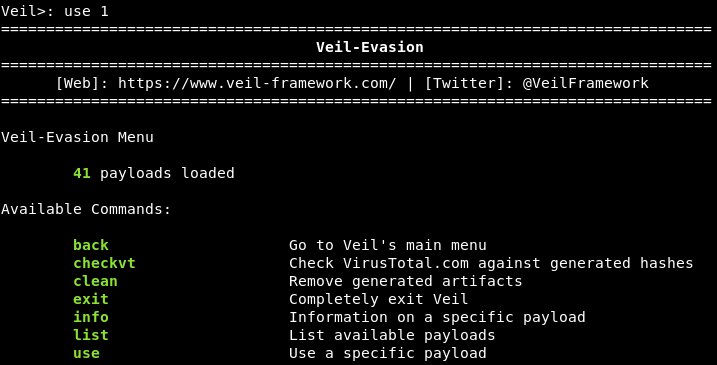
In the above screenshot, we can see that Veil gives us a list of commands that can run on this tool. We want to list all the available payloads, of which there are 41. In the following screenshot, we can see that each payload is divided into three parts, and we have highlighted the payloads we will be using which are 15) go/meterpreter/rev_https.py: 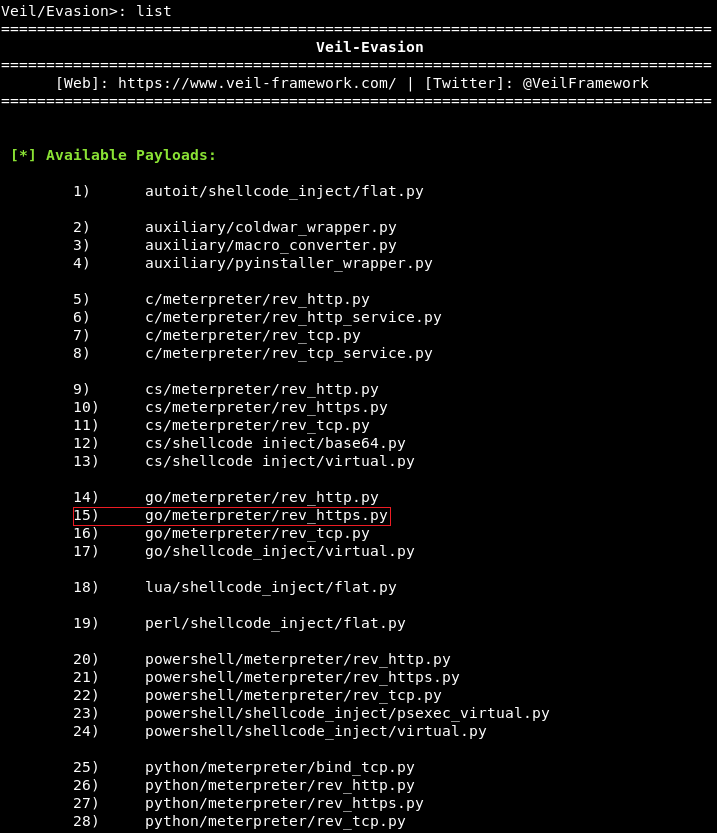
The first part of the payload's name is the programming language in which the payload will be wrapped. In the preceding screenshot, we can see the language used include CS, Python, GO, C, PowerShell, and Ruby. In this example, we are going to use the go language. The second part of the payload is the type of payload. In other words, the type of code that is going to be executed on the target network. In this example, we are going to use Meterpreter, which is a payload designed by Metasploit. Metasploit is a huge framework, and sometimes it is used for hacking. Meterpreter runs in memory, so it is difficult to detect, and it does not leave a large footprint. With Meterpreter, we can gain full access over a target computer. It allows us to navigate through the filesystem, install or download files, and much more. The third part of the payload's name is the method that's going to be used to establish its connection. In our example, that is rev_https. Where rev stands for reverse, and https is the protocol that will be used to establish the connection. In the preceding screenshot, there are a few examples of rev_tcp, which creates a reverse TCP connection. A reverse connection is where the target machine connects to the attacker's machine via a backdoor. This method bypass antivirus programs, because the connection is not directed at the target computer, but rather at the attacker instead. In our example, we are going to use a port 80 or 8080, that many websites use, so that the connection will appear as a harmless website connection.
Next TopicGenerating a Veil backdoor
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









