Dmitry Tool in Kali LinuxDmitry stands for DeepMagic Information Gathering Tool. Dmitry is a free and open-source tool that is available on GitHub. We used this tool for information gathering. Dmitry is a command-line tool. With the help of the Dmitry tool, we can gather information about the target, which we can then use for social engineering attacks. It can be used to collect a variety of useful information. Uses of Dmitry ToolThe following are the uses of the Dmitry Tool:
Flags of Dmitry ToolDmitry is a command-line tool. The Dmitry tool has a number of commands that can be used with different commands. Different flags are used with commands. The flags are listed below.
Installation of Dmitry ToolThe following steps are used to install the Dmitry tool: Step 1: First, we have to open our Kali Linux terminal and then Move to the Desktop Directory. 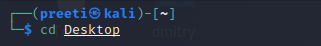
Step 2: Now, we have to create a new directory named dmitry. 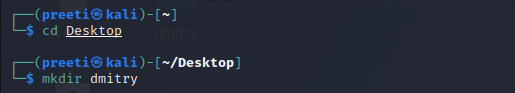
Step 3: We have already made the dmitry Directory. Now move into this directory, where we will find the Dmitry tool to be installed. 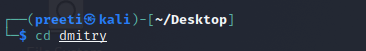
Step 4: Now, we can see that we are in a dmitry directory. The Dmitry tool must now be cloned and downloaded from GitHub. Use the following command to clone the tool. 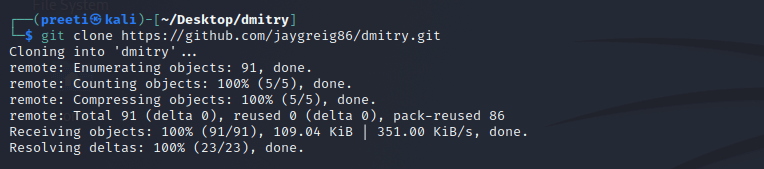
Step 5: The Dmitry tool has been successfully downloaded into our Kali Linux. We can now use the tool. Now run the following command to check the listing of the directory. 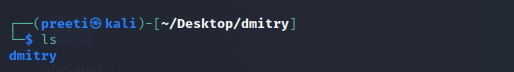
Step 6: Dmitry is a new directory that we can find here. Use the following command to move to this directory, and then use the following commands to list the contents. 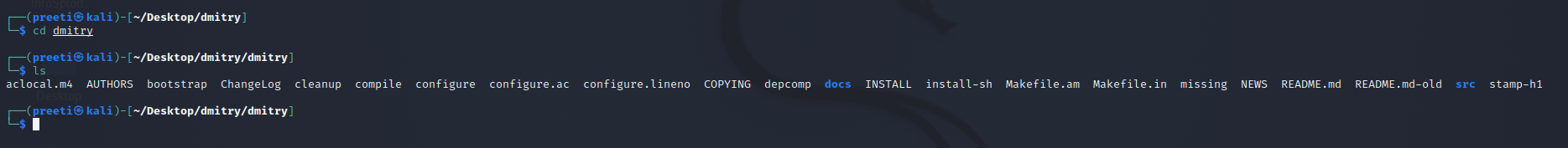
Step 7: The file has been downloaded into the directory; use the following command to install the directory; all of the dependencies will be downloaded as a result of this. 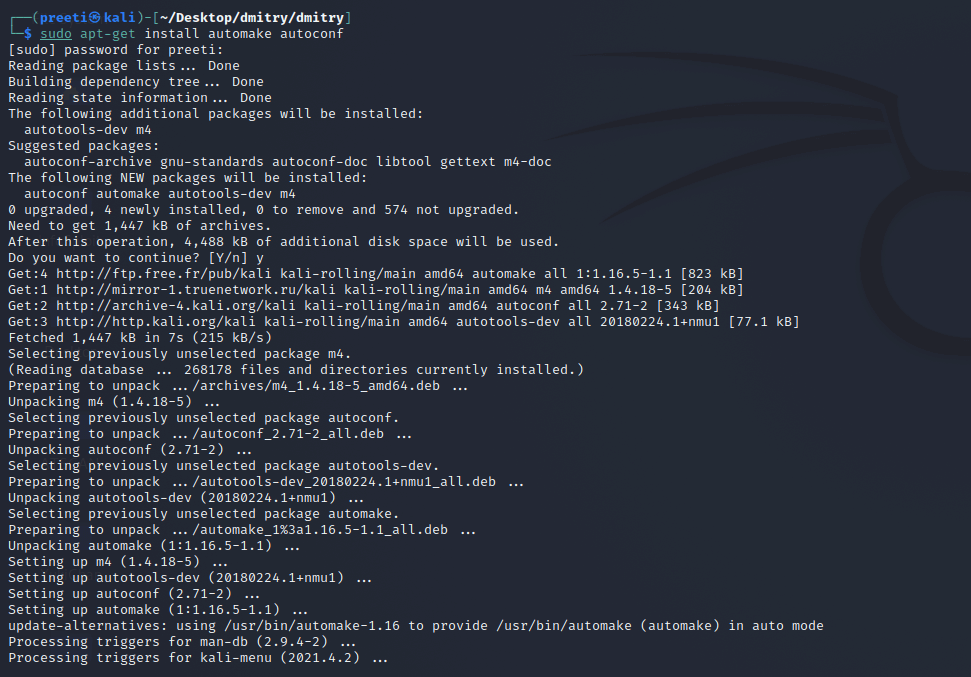
Step 8: After we have downloaded all of the dependencies, we need to give the permissions with the command below. 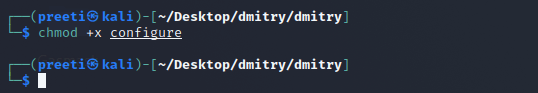
Step 9: The tool has been permitted for execution. It's time to initialize the configuration file using the following command. 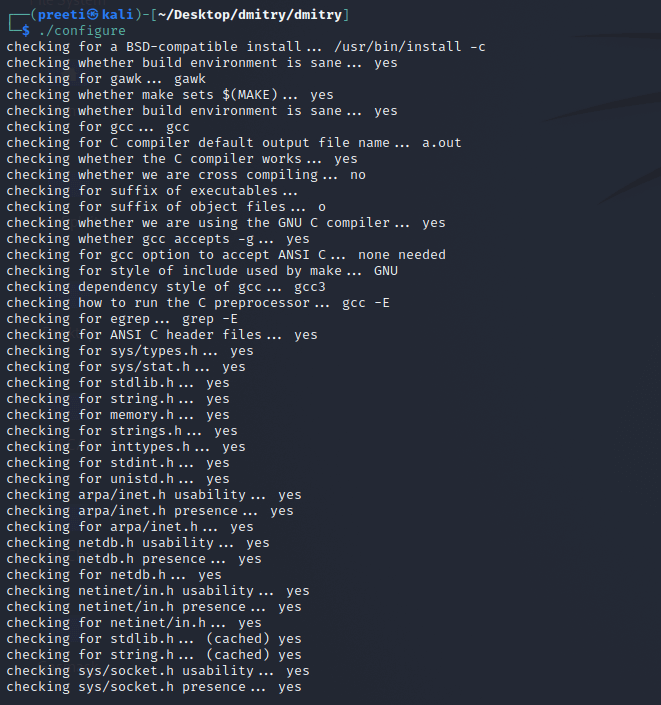
Step 10: Now, this is the time to make a configuration available for the tool so that we can run the command that follows. 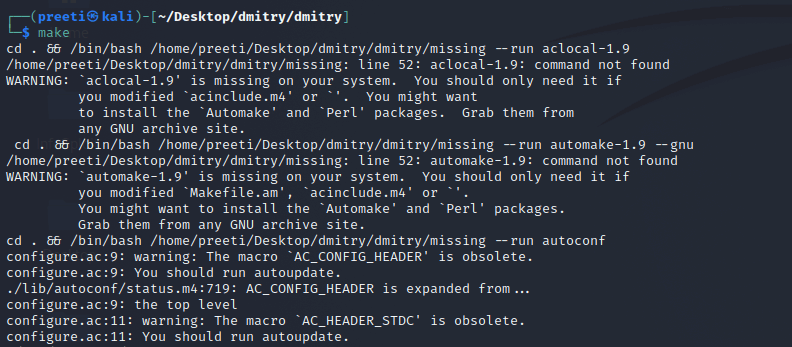
Step 11: Now, we can install the tool with the help of the following command. 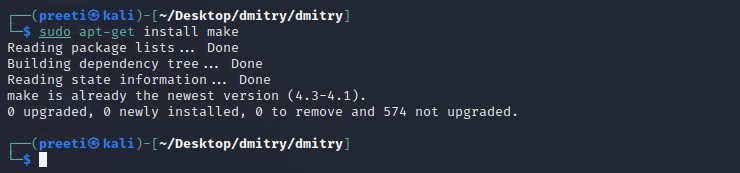
Step 12: Lastly, now that all of the dependencies and tool configuration have been completed, we can execute the tool with the help of the command below. 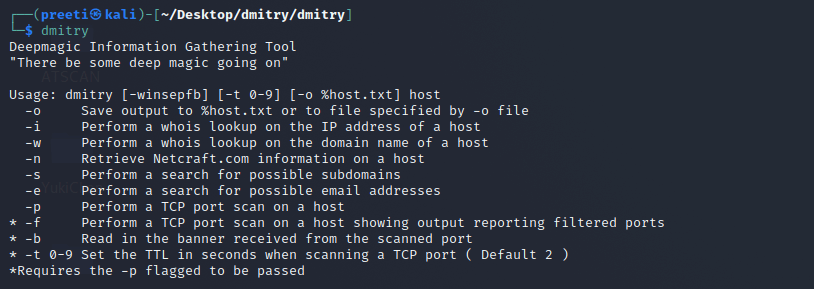
As we can see, the tool is currently in the running state, and several flags may be seen here. These flags can be used in conjunction with commands to set a target and obtain information about it. Now we will look at some instances of how to use the tool. The following are some examples. Run the Tool and Get the Information About Any TargetWe can run the tool and enter the following command to collect any basic information. 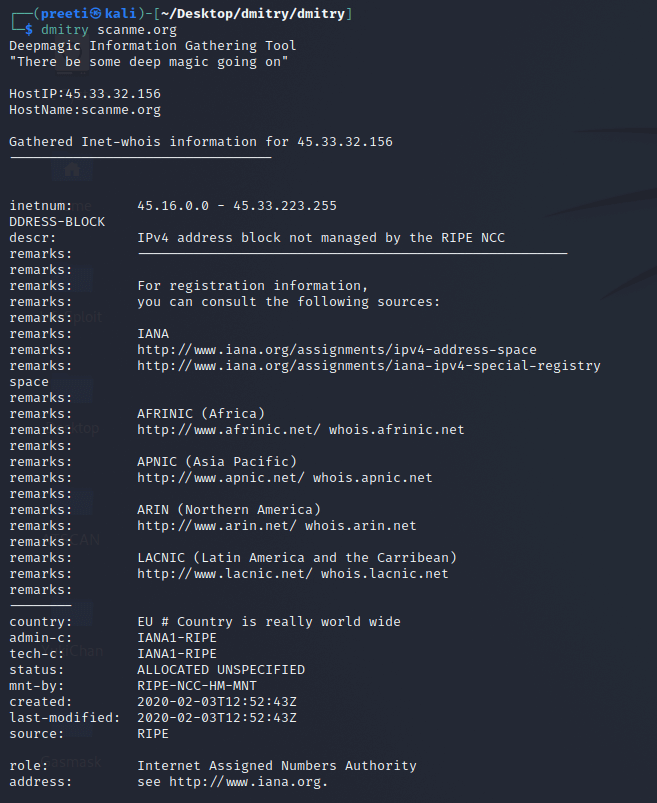
We can use any domain name here instead of scanme.org as our target. Run the Tool and Get Specific Information about Any Target With the help of a FlagRun the tool and type the following command with the flag for acquiring specified data. To gather information about ports, we use the -o flag. 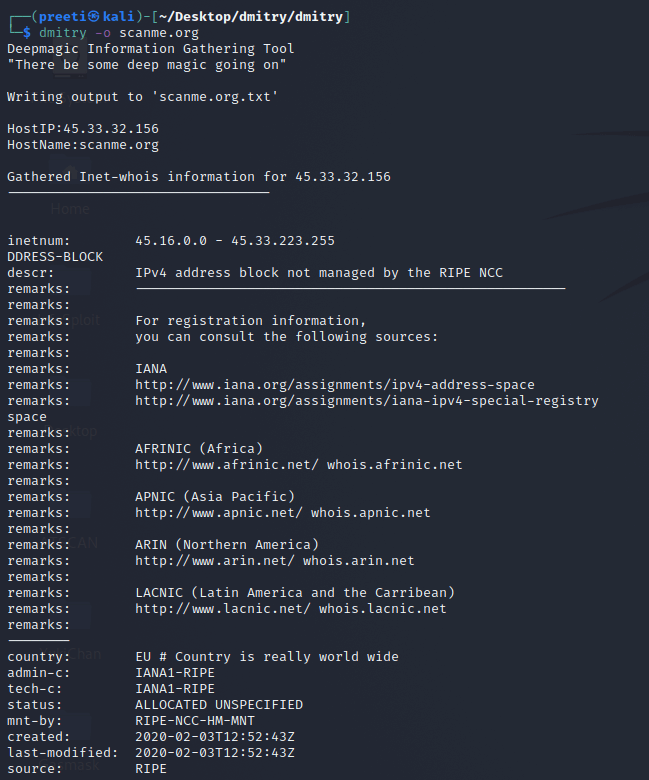
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









