TIDoS-Framework-Offensive Web Application Penetration Testing FrameworkWe must have used the Metasploit Framework for various attacks and information gathering as a penetration tester. TIDoS Framework is an open-source toolkit that is free to use, and it is similar to Metasploit Framework. This toolkit includes all of the most common web application tests, such as Target Scanning, Enumeration, and Vulnerability Assessment and Analysis. This toolkit comprises five main phases, subdivided into 4 sub-phases containing a total of 108 modules. The Reconnaissance Phase has its own 50 modules (including active and passive recon, and information disclosure modules). We have to provide the target domain and leave the rest to this tool. The TIDoS toolkit has full verbose out support, so we'll know what's going on. Features of TIDoS-FrameworkThe following are the features of TIDoS-Framework:
How TIDoS Works?The TIDoS-Framework is a group of a variety of modules. These modules are useful and have their own functionality. By executing the following command on the terminal, the system will execute the TIDoS-Framework script, enabling all the modules. 
After running the script, we should first configure the target domain host, go through the list of modules, and choose the one that will help us in the testing process. After selecting the module, select the applicable or associated option and begin the process. After a while, the tool will automatically collect the data and display it in the terminal. Reconnaissance and Open-Source IntelligenceReconnaissance is the first and most important phase in the penetration testing process. During this phase, all information about the target domain or person is gathered. OSINT (Open-Source Intelligence) is a term that refers to data obtained by this method that is publicly available through numerous sources such as Github, Facebook, and LinkedIn. These resources are open to the public and include a wealth of knowledge. Tidos can execute all of these scanning options automatically or manually by selecting the desired option. In the same way, the active reconnaissance scanning option comprises all the scanning techniques which need interaction with the target web application, such as pinging the target web server. Information Disclosure is the type that checks the target application for some sensitive kind of data such as mobile numbers, email addresses, credit card details, and so on. Scanning and EnumerationScanning and Enumeration is the process of directly or indirectly engaging with the target host to obtain further useful information such as port specifies, banner grabbing (OS information), server details, and firewall information. TIDoS tool can ping the target to obtain this information by hosting information, an encryption technique. Scanning can take several forms, including Network Scanning, Port Scanning, and Vulnerability Scanning. Vulnerability AnalysisVulnerability in a web application refers to security issues that expose sensitive information or have the potential to harm the organization or institution. The vulnerability must be identified and managed using all the procedures and methods. Vulnerabilities are categorized into several categories based on their severity. The TIDoS tool offers the ability or modules to scan the target domain vulnerabilities such as Cookie Injection, ClickJacking, XSS, SQL Injection, etc. For example, The TIDoS tool sends various malicious payloads to the target URL comprising of parameters if we want to test the application for XSS Vulnerability. If the server responds to those payloads, the target domain may be vulnerable. For example, if we want to test the application for XSS vulnerability, the TIDoS tool sends various malicious payloads to the target URL, including parameters. If the server responds to that payload, the target domain may be vulnerable. Active VS Passive ReconActive ReconWhen there is direct interaction with the target network host for gathering the information, this is referred to as active reconnaissance. Because there is direct communication, logs, or records are made in the target host to the target system, putting the hacker or attacker in danger because their identity may be revealed. Passive ReconThe term "passive reconnaissance" refers to a method of gathering information without interacting with the target. As a result, no traces or logs are created in the target client-side system. This phase collects information such as WHOIS Records, DNS Records, Reverse IP Data, etc. No requests to the target domain are made, during the data collection process. In this phase, the hacker's chances of being detected are reduced. The majority of the information is gathered using OSINT tools that are freely available on multiple platforms. How to Install TIDoS-Framework ToolThe following steps are used to install TIDoS-Framework Tool: Step 1: First, we have to use the following command to check whether Python Environment is Established or not. 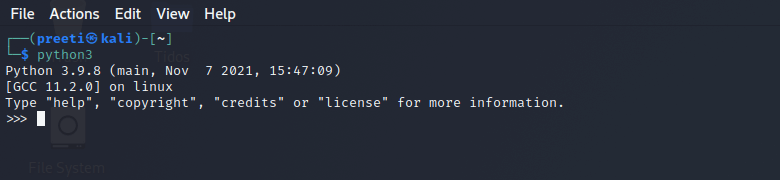
Step 2: Then, we have to open our Kali Linux Terminal and move to Desktop with the help of the following command. 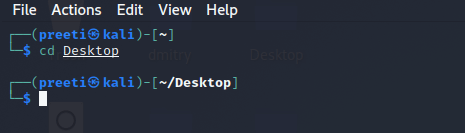
Step 3: Now, we are on Desktop, use the following command to create a new directory called Tidos. The installation of the Tidos tool will be completed in this directory. 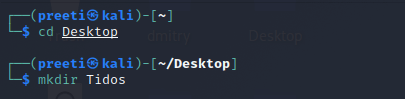
Step 4: Now, with the help of the following command, switch to the Tidos directory. 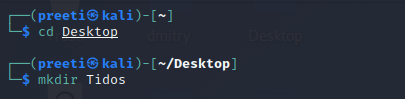
Step 5: Next, we need to install the tool. To use this tool, we must first clone it from Github. 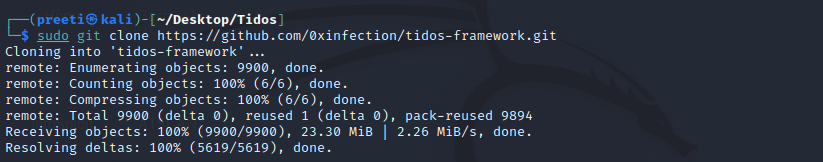
Step 6: The Tidos tool has been successfully downloaded. Using the following command, list the contents of the tool. 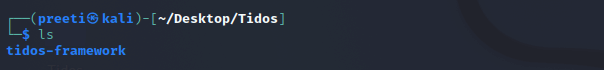
Step 7: Now, we can see that a new Tidos tool directory was created when we were installing the tool. Now use the following command in order to move to that directory. 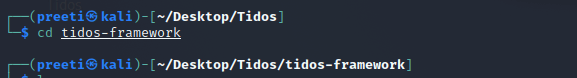
Step 8: Use the command below to find the tool's contents. 
Step 9: Use the following command to download the required packages for the usage of Tidos tool. 
Step 10: In order to open the Tidos tool's menu, run the tidconsole.py script using the following command. 
We have to type help in order to get the list of available modules of usages. 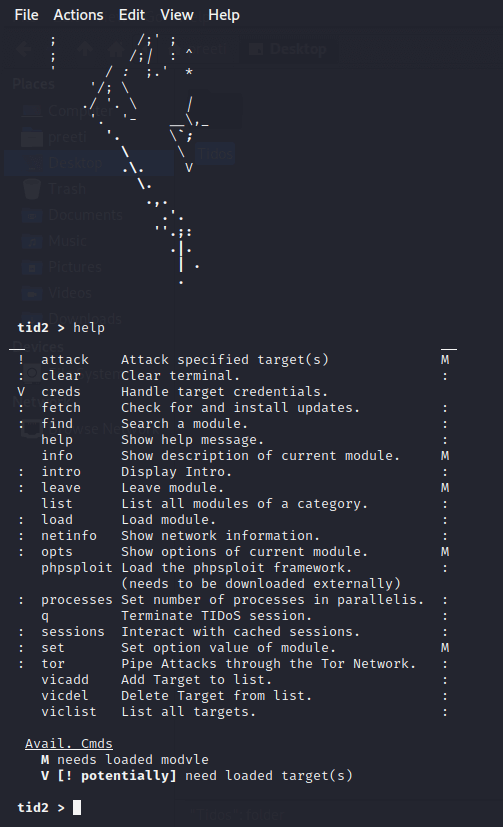
Working with TIDoS-Framework in Kali LinuxSetting Up Target DomainStep 1: First, we have to set our target domain in the toolkit. (vicadd) is the command we used to add the target domain URL for usage. 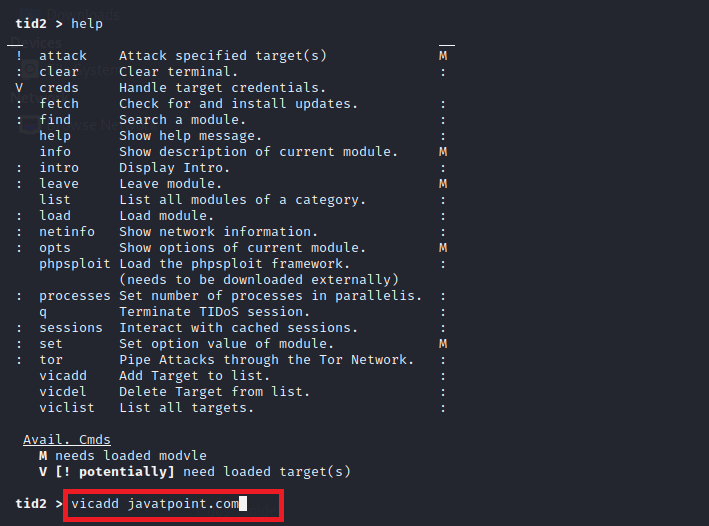
Step 2: We have added javatpoint.com as our target domain URL, which we can see in the below screenshot. After we setting up our target, we may use the toolkit's numerous modules. 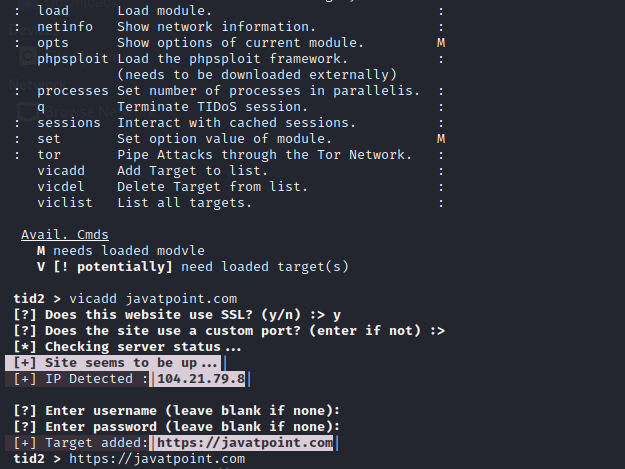
Display List of Available ModulesStep 1: The available modules offered by the TIDoS-Framework toolkit are listed in the screenshot below. This list command is used to display a list of modules. 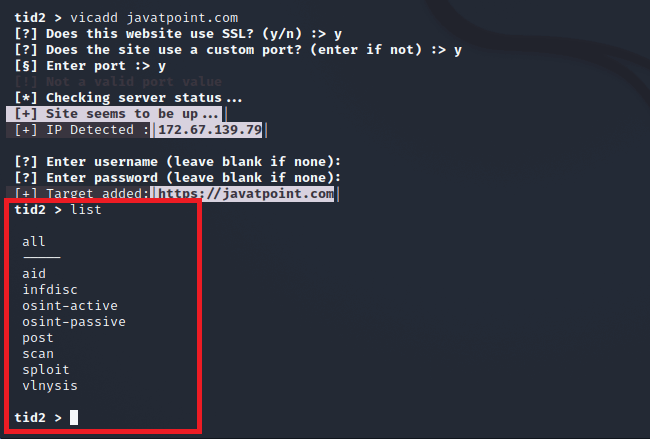
Next TopicFsociety Tool in Kali Linux
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









