Kali Linux CourseKali Linux is a Debian-based Linux distribution. It is a painstakingly operating system designed specifically for network analysts and vulnerability scanners. Due to the variety of tools that come with Kali, it has become an ethical hacker's favorite tool. Kali Linux, originally known as Backtrack, promotes itself as a more streamlined replacement with more testing-centric tools, as opposed to Backtrack, which featured a plethora of tools that all serve the same purpose, causing it to be bloated with unnecessary tools. This significantly simplifies ethical hacking with Kali Linux. Kali Linux is not inherently illegal. After all, it's only an operating system, it is a hacking tool, and it is illegal to use it specifically for hacking. It is acceptable if it is installed for practical purposes such as studying or teaching or used to strengthen your software or network. Installing any licensed and accessible operating system is not against the law. However, we have to be careful when using it. This list contains the Kali Linux courses that we can take online. Each of these courses has its own specialization, so that we can select one based on our priorities. In this article, we will learn about the Kali Linux courses. Here is a list of Kali Linux courses for beginners, and intermediate developers, programmers, system admins and IT professionals.
1. Kali Linux Tutorial For Beginners by Udemy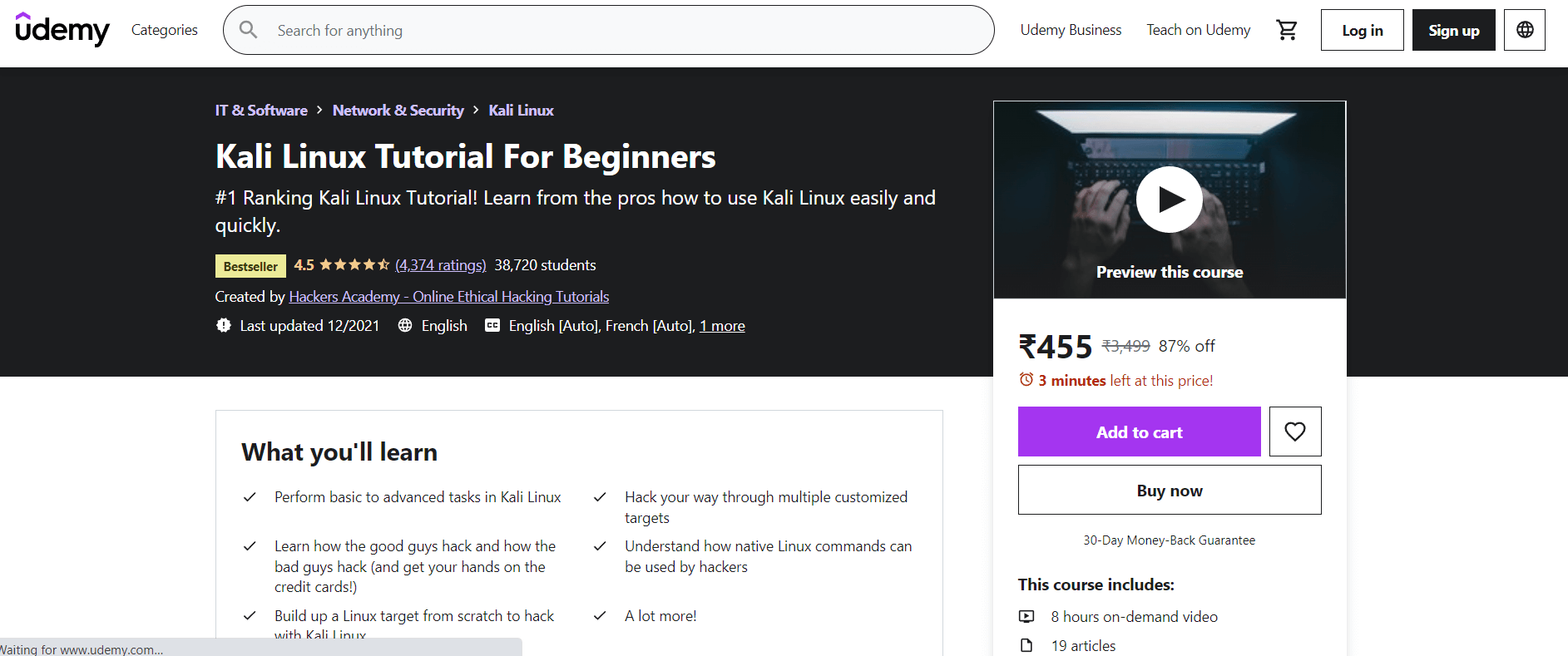
Those who are new to Kali Linux will benefit from this introductory course, which will teach us the basics of the operating system. In this program, we will learn how to use Kali Linux from the ground up, and we will become familiar with the basic tools and commands found not only in kali but also in most Linux systems. This course is divided into three parts: fundamentals, management, and, hacking. The first two chapters will introduce us to the fundamental concept of Kali Linux, while the third section will walk us through various key aspects of hacking. After completing this course, we will be able to use Kali Linux's advanced methods and techniques immediately. We will learn how to use common Linux functions like a hacker and build a Linux target from the ground up. We will also learn how to perform basic and complex tasks in Kali Linux and gain a basic understanding of the many concepts involved. Course Rating: 4.5 out of 5.0 (38,720 students) Duration: 8.5 Hours Certificate: Certificate of completion Key USPs:The following are the key USPs of this course:
To access this course, click on the following link https://www.udemy.com/course/kali-linux-tutorial-for-beginners/ 2. Kali Linux Hacking Lab for Beginners by Udemy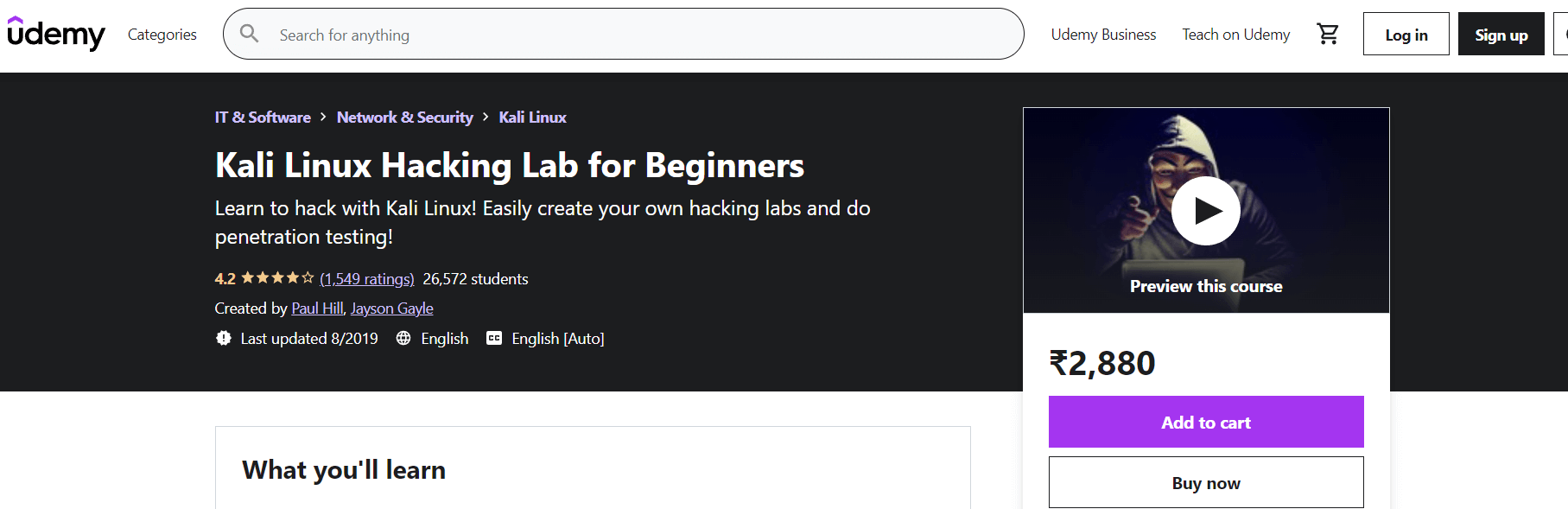
The purpose of this Kali Linux course is to teach us the fundamentals of hacking and to provide an introduction to becoming ethical hacker. The Kali Linux tutorial is intended for students who have no or little experience of hacking and penetration testing. With the help of this course, we will learn the theory of hacking and the practical side of ethical hacking. These Kali Linux tutorials will teach us how to set up our own virtual lab environment, similar to the one used in this course. This course also includes PDFs for each lecture to assist us in following along. If we follow the steps outlines in the lectures, we can replicate them in our won lab environment. If we are interested in Kali Linux hacking or ethical hacking, this is one of the best Kali Linux tutorials for us.
In this course, we will learn how to:
To access this course, click on the following link https://www.udemy.com/course/kali-linux-hacking/ 3. Hands-on Penetration Testing Labs 1.0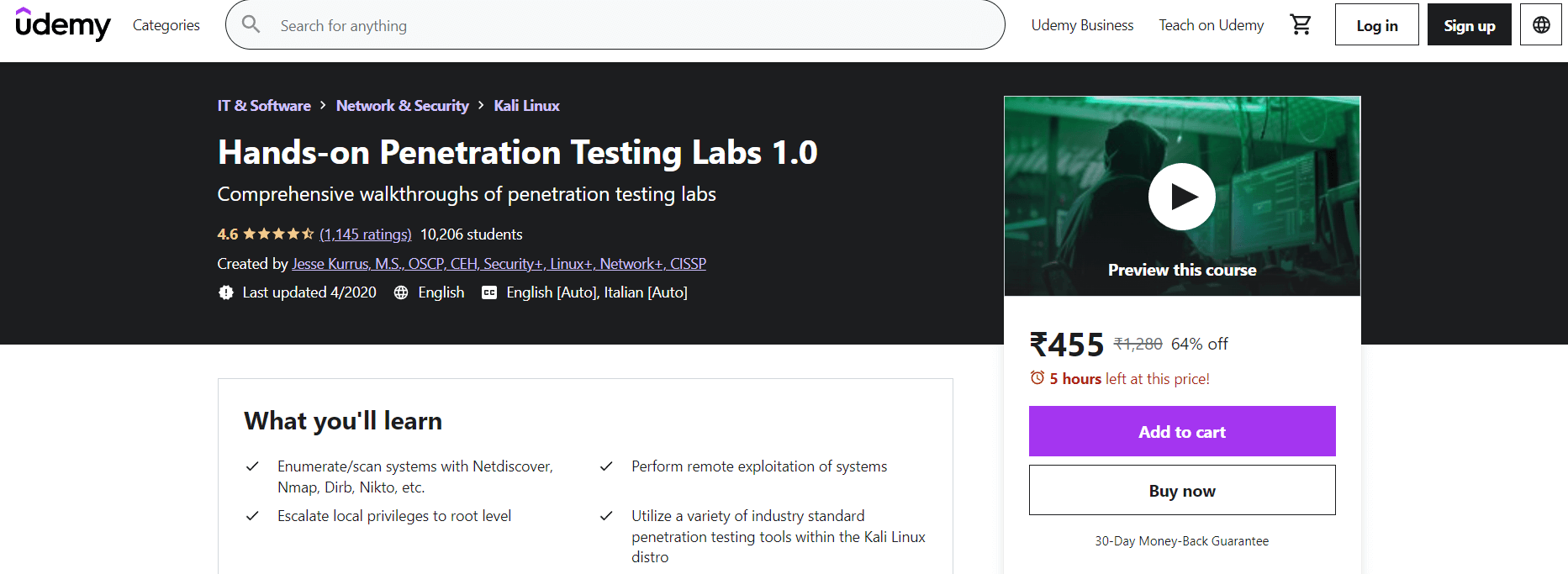
This course comprises hands-on technical labs where students hack a variety of intentionally vulnerable operating systems using industry-standard open-source technology. The course includes detailed instructions for setting up the labs (VMware Player, Kali Linux, Kioptrix, etc.). Enumeration, remote exploitation, buffer overflows, and privilege escalation are the main topics covered in this course. It will also show us how to effectively use tools like Dirb, Nmap, and enum4linux to comprise vulnerable systems by interpreting their output.
In this course, we will learn how to:
To access this course, click on the following link https://www.udemy.com/course/kali-linux-hands-on-penetration-testing-labs/ 4. Penetration Testing: Advanced Kali Linux
This course will teach us how to use Kali for advanced pen testing, such as stealth testing, privilege, tunneling, pivoting, and exfiltration. We will also learn how to use the basic toolset and extend Kali, integrating native exploits into the Metasploitable environment. Learn how to create and manage a variety of shells, including Python and C++, and how to collect and use credentials. The main focus of this course is on advanced exploit customization and gaining root access via a sustainable shell. It is intended to assist the learner in progressing as a professional pentester and learning key objectives required to pass the Offensive Security Certified Professional (OSCP) exam. All ethical hackers and pen testers, and general IT professionals, will find the training useful.
In this course, we will learn:
We can take this course on LinkedIn. To access this course, click on the following link https://www.classcentral.com/course/linkedin-learning-penetration-testing-advanced-kali-linux-30914 5. Kali Linux Web App Pentesting Labs by Udemy
This course focuses on the exploitation of vulnerable web applications. In this course, we will be building a lab environment using Kali Linux and various intentionally vulnerable web applications such as SQL injection labs, Beebox, WebGoat, and OWASP Juice shop. The course concentrates on the most common web application flaws and how to exploit them. We will be using the most recent edition of OWASP, OWASP 2017 top 10, as a framework for this learning approach. OWASP is an organization dedicated to improving web applications' security, and it is a crucial component for aspiring pentesters to understand. We will be covering OWASP 1-9 because 10 does not apply particularly to pentesting, and is attentive on the defensive side. The manual and automated methods of detecting and exploiting web application vulnerabilities are the main topics covered in this course. We'll learn how to use industry-standard tools like Nmap, Nikto, Sqlmap, and Burpsuite. The course begins with downloading, installing, and configuring the components required for comprehensive hands-on web application penetration testing in a lab environment.
In this course, we will learn how to:
To access this course, click on the following link: https://www.udemy.com/course/kali-linux-web-app-pentesting-labs/ 6. Penetration Testing and Ethical Hacking with Kali Linux
This course introduces ethical hackers and penetration testers to Kali Linux. This course teaches IT professionals, how to conduct a professional penetration test workflow using the Swiss Army Knife operating system Kali Linux and ethical hacking techniques.
In this course, we will learn:
To access this course, click on the following link https://www.pluralsight.com/courses/kali-linux-penetration-testing-ethical-hacking 7. The Complete Ethical Hacking Course 2.0 Python & Kali Linux
In this Kali Linux course, we will learn how to utilize Python to become an ethical hacker and how to execute network penetration testing with Kali Linux. The Course is divided into two sections, the first of which covers Python Basics and Advanced Training, and the second of which covers Penetration Testing using Python code. The course is intended for students at the beginning and intermediate levels of their website development and coding journeys. Penetration testers and ethical hackers have a bright future since they assist in the protection of company networks and the discovery of potential vulnerabilities inside them. On Udemy, we can enroll in The Complete Ethical Hacking Course 2.0: Python & Kali Linux Certificate Course.
In this course, we will learn how to:
To access this course, click on the following link https://www.udemy.com/course/penetration-testing-ethical-hacking-course-python-kali-linux/ 8. Learning Kali Linux
This course will provide a brief overview of Kali Linux for prospective ethical hackers. It demonstrates how to create a virtual testing environment, install Kali Linux, and set up toolsets for data collection; vulnerability assessment, password and hash cracking, and target exploitation. Business is exposed because they are interconnected, vulnerability testing helps companies in limiting their exposure to risk. This course will teach us about ethical hacking careers, tactics, and tools, one of the most competitive and in-demand IT security skills. On LinkedIn, we can take the Learning Kali Linux Certificate Course.
In this course, we will learn how to:
To access this course, click on the following link: https://www.linkedin.com/learning/learning-kali-linux-2 9. Ethical Hacking with Python, JavaScript, and Kali Linux
This course is more in-depth than the other, and we will perform real-world scenarios for attacking various targets. We will develop payloads (viruses) to investigate specific vulnerabilities, using the Python and JavaScript programming languages. We will learn how to penetrate networks using various tools and perform various operations such as MITM and stealing the network's data. Then we will study Python and use Tor to remain anonymous while creating a mac address changer with Python. Later, we will create the malware with Python, learn how to hack the browser with JavaScript, and learn web application penetration tools.
To access this course, click on the following link: https://www.udemy.com/course/ethical-hacking-with-python-javascript-and-kali-linux/ 10. Kali Linux - Backtrack Evolved
Kali Linux is Offensive Security's newest Linux distribution, which is specifically designed for network security audits and forensic investigations. It comes with hundreds of built-in tools for performing every aspect of a penetration test. This is one of the greatest Kali Linux courses available. It ensures that we have the skills and tools necessary to breach the security of enterprise networks and information systems.
To access this course, click on the following link: https://www.udemy.com/course/kali-linux-backtrack-evolved/ 11. Digital Forensics for Pentester- Hands-on | Udemy
In order to detect and track Black Hat Criminals, digital forensics is becoming increasingly vital in Cyber Security. It is necessary to remove Hacker's malicious backdoors/malware and trace them back to avoid possible future incidents. Kali Linux provides some of the most famous forensics tools to conduct formal forensics and investigations and perform professional-level forensics. It is the greatest Kali Linux digital forensics course available, and it will teach us all we need to know about forensics analysis of mobile devices and computers running the Kali Linux distribution. This course serves as a digital forensics' primer for pen-testers and cybersecurity professionals looking to broaden their expertise and add more tools and skills to their resumes. Anyone interested in a career in digital forensics should take this course. Understanding the difference between digital forensics and computer security is crucial. This course will include lessons and lab files that explain digital forensics techniques.
To access this course, click on the following link: https://www.udemy.com/course/digital-forensics-for-pentesters-hands-on-learning/ 12. Kali Linux Training for Users
If we can't find good resources for studying Kali Linux or getting training, this forum can help us cover all the elements of learning. This Kali training platform from Offensive Security offers all of the classes and training we will need to master ethical hacking and virtualization software. This course will teach us how to understand the internal components of penetration testing distribution Kali Linux, as well as how to build our own Kali Linux solutions like the Kali ISO of Doom, the Evil AP, and others. After finishing this course, we will be able to create optimized and customized Kali Linux Kernels and upload them to our distribution repository. This course teaches us how to use Kali Linux operating system and Kali Linux installations, as well as how to organize, configure, and pre-seed them. We will also learn how to create Kali appliances, such as the Doom Kali ISO, and how to create Kali packages and sources. To access this course, click on the following link: 13. Kali Linux Fundamentals by Cybrary
If we want to master the vocabulary, basic elements, and tools associated with Kali Linux, then this is the best course for us. This tutorial will teach us the basics of Kali Linux terminology and how to get and run a copy of Kali on our system, and other topics, such as browsing the interface, file system, and handy commands for getting a starter. The concepts were created by Robert Smith, the director of Corsica's Security Services. He will assist us in learning various Kali Linux principles throughout the course. The course will teach us how to use Kali Linux's tools and security testing tools, as well as basic troubleshooting resources and procedures. We will be able to execute basic distribution operations such as installation, troubleshooting, and navigation after completing this course. To access this course, click on the following link: https://niccs.cisa.gov/training/search/cybrary/kali-linux-fundamentals 14. Hacking and Patching by Coursera
This course will teach us how to use command injection flaws to hack web applications on our AWS Linux instance's website. We will learn how to utilize leverage LAMP services in order to find useful information on standard Linux systems and how to deposit and hide Trojans for later use. We will learn how to add authentication to these web apps using regular expressions. We will learn how to utilize input validation and replace generic system calls with unique function calls to avoid injection vulnerabilities. We will discover how to gain access to user profiles and passwords by exploiting SQL injection vulnerabilities in web programs. We will learn how to enhance them using input validation and SQL parameter binding. Coursera offers the course, and after successfully completing it, we will receive a certificate of completion. To access this course, click on the following link: https://www.coursera.org/learn/hacking-patching 15. Wi-Fi Hacking with Kali Linux
In this course, we will learn how to hack and protect several Wi-Fi security systems such as WEP, WPA, and WPA2. Throughout this Kali Linux online tutorial, we will learn about the history of Wi-Fi, its vulnerabilities, and how to build up a penetration testing environment. It is one of the greatest Kali Linux courses, and it will show us how to install and utilize Kali Linux in 4 distinct methods. We will also learn how to hack router admin panels using hydra, crack Wi-Fi passwords with a keylogger, change MAC addresses, etc., towards the end of this course. To access this course, click on the following link: https://www.udemy.com/course/wifi-hacking-with-kali-linux/
Next TopicPhishing Tools for Kali Linux
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









