Tor Browser Kali LinuxWhat is Tor Browser?The Tor (onion routing) browser is a web browser that is designed for anonymous web browsing and traffic analysis protection. Although Tor is typically linked with the darknet and criminal activity, it is also used by law enforcement officials, whistleblowers, reporters, whistleblowers, and regular security-conscious people for good purposes. The browser was developed by the US Navy to safeguard secret US government communications. While the government still uses Tor, it is now an open-source, multi-platform browser that the general public may use. Today, Tor is used by human rights activists and dissidents who want to keep their online activity hidden from authoritarian regimes, law enforcement, intelligence agencies, and criminals. Law enforcement agencies can trace Tor users using a variety of tactics and tools, especially if the sites they visit do not use end-to-end encryption (E2EE). Exit relays and encrypted tunnels are used by the browser to obscure user traffic within a network, but they leave endpoints more visible and have no effect beyond the network's limits. How Tor WorksOnion routing is a mechanism that the Tor browser uses to operate. The onion router is a peer-to-peer (P2P) overlay network that allows users to access the internet without revealing their identities. There are multiple layers of encryption used by Onion routing to hide the source and destination of information transferred over the network. It's created in such a way that no one can monitor or control online communication. When a user installs Tor, the browser communicates with Tor servers to deliver data to an exit node, which is where data leaves the network. This data is encrypted several times before being delivered to the next node; it becomes more difficult to trace the data back to its original source if we repeat the process. Tor does not track browsing history or store cookies, in addition to encryption. Levels of SecurityThere are three levels of security in the Tor browser, one of which is the default and two others. Each level provides a different level of protection, with the highest level providing the most protection.
Tor WeaknessesTor is more secure than most popular browsers, although it is not impenetrable to attacks. While Tor prevents traffic analysis, it does not prevent end-to-end correlation, which is the process of identifying the source and intent of an attack by combining many data points from a data stream. The following are some other Tor browser weaknesses: 1. Traffic Analysis Attack An intruder takes information and matches it to the opposite side of the network in a passive traffic analysis attack. The intruder alters packets in a pattern to analyze their influence on traffic in an active traffic analysis attack. 2. Bad Apple Attack In 2011, a documented attack revealed the exposure BitTorrent users' Internet Protocol (IP) addresses on the Tor browser. 3. Consensus Blocking The Tor exit relay is vulnerable to a type of attack that allows a malicious user to block consensus nodes from interacting for a short period of time. This issue is similar to a denial of service (DoS) attack that blocks users from accessing a website by flooding it with so many requests that the servers can't keep up. 4. Mouse Fingerprinting In 2016, a researcher revealed that they could monitor mouse fingerprinting by measuring time at the millisecond level. Third parties can use this strategy to identify individuals by recording their mouse movements on a certain website and comparing them to their mouse movements on the Tor browser against a standard browser. 5. Eavesdropping The Tor exit nodes are vulnerable to eavesdropping, because the traffic passing via the Tor exit nodes does not use E2EE. While this method does not reveal a user's identity directly, traffic interception can provide information about the source. 6. Relay Early Traffic Confirmation Attack After identifying a deanonymization effort on Tor users in 2014, the browser issued a security advisory. The bad actors altered the headers of cells and communicated back to the user. If the attack included the entry node, an attacker might capture the IP addresses using the attacking relays. 7. Sniper attack A sniper attack overwhelms exit nodes until they run out of memory, which is a sort of distributed DoS (DDoS) attack. The number of operational exit nodes can be reduced by an attacker, increasing the likelihood that users will use exit nodes controlled by the attacker. Who Uses Tor and WhyWhile Tor is best known for its illegal uses, most Internet users may have different, valid reasons for accessing the Internet through Tor. Let's see who uses Tor and why: 1. Illicit Organizations There are various criminals who use Tor to shield their online activity. 2. Government Agencies Government agencies use the Tor browser in order to protect their shared sensitive government information. 3. Private Individuals The Tor browser is beneficial to anyone who wants more online privacy and improved cybersecurity. Journalists, activists and anyone censored can use Tor to communicate online. 4. For-Profit Enterprises Tor-using businesses can benefit from greater data privacy and security. It comprises a number of websites that require special software. The Tor Browser and the Dark webThe Tor browser is the only browser that allows us to access the dark web. The dark web is made up of websites that are not easily located using a search engine and cannot be accessed using a standard web browser. It comprises a number of websites that require special software to access, such as forums and marketplaces. While everyone may access the internet, the dark web is a closed network where users do not reveal their true IP addresses. This makes it a safer area to do business on the internet, but it also makes it a hotbed for criminal activity. The dark web is used by the military, journalists, criminals, and politicians. The dark web was developed to allow people or groups to interact in an untraceable manner, in their opinion. Apart from its potential for illegal usage, the dark web has a number of legitimate uses, such as allowing whistleblowers to share information that they might not otherwise be able to reveal. With the help of the Tor browser, people can access the dark web. In contrast, many people associate the dark web with illegal activities. The Tor network has a variety of legitimate uses. These comprise communicating or browsing in nations that implement internet censorship. Is Tor Browser Legal?The use of Tor Browser is totally legal. On the other hand, Tor is either banned or blocked by national authorities in other nations. China has prohibited Tor and made it impossible for Tor traffic to pass through the Great Firewall. Iran, Russia, and Saudi Arabia, for example, are working hard to prevent citizens from using Tor. Venezuela has recently prohibited all Tor traffic. It's understandable why Tor is despised by a repressive regime. Journalists may easily report on corruption via this tool, and dissidents can organize against political repression. The freedom to communicate, publish, and read anonymously is a requirement for online freedom of expression and hence a requirement for democracy in today's world. Using and supporting Tor contributes to global freedom of expression. Users with advanced technical skills are invited to create a relay and denote bandwidth to the Tor network. How to Install Tor Browser on Kali LinuxTor browser is open-source, so we can install Tor in Kali Linux with a few steps and use it for our purposes. There are two methods for installing Tor in Kali Linux.
1. Install Tor Browser in Kali Linux Apt in TerminalFirst, we will learn how to install and run the Tor browser in Kali Linux using the terminal. The following steps are used to install Tor browser in Kali Linux: Step 1: In order to install the Tor browser in Kali Linux, first, we have to update the Kali Linux using the command below. 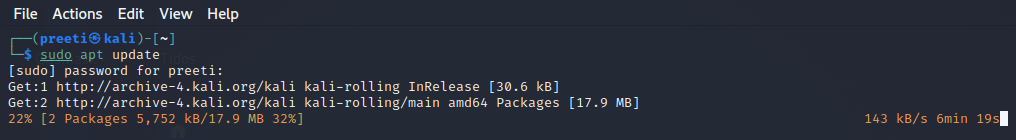
Step 2: Now, with the help of the following command, we will install the Tor browser. 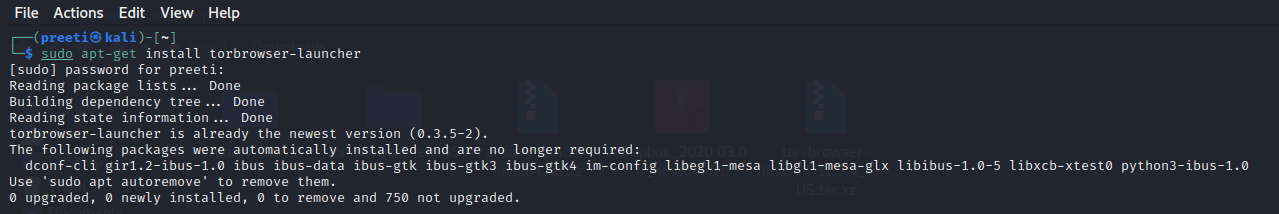
Our installation completes without any error. If we have any problems while using Tor Browser with Kali Linux, we can try the second method. Step 3: Now, we have installed the Tor Browser Launcher, we need to open the Tor Browser on Kali Linux. To do so, use the following command on the terminal: 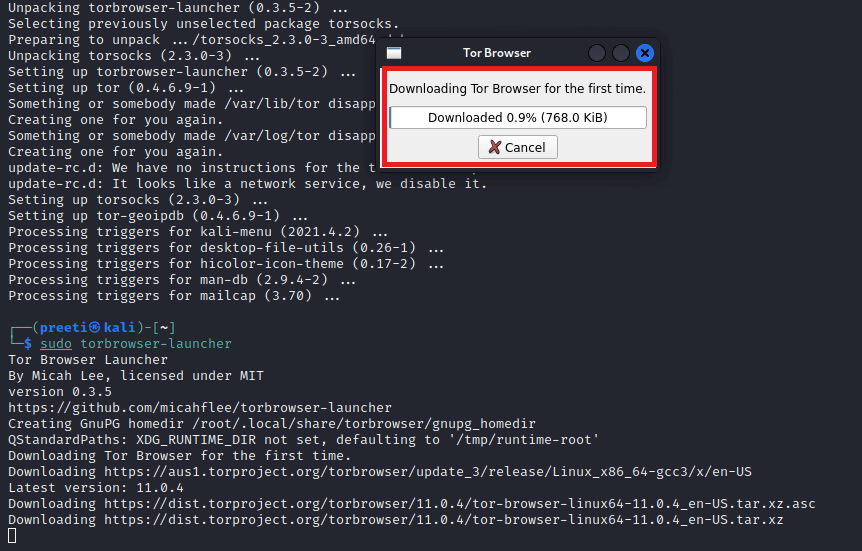
And we can search in the search bar as Tor, and we will get two alternatives for starting the Tor Browser. We'll see a new window appear on our computer after running the command or double-clicking the Tor Browser icon. Step 4: Next, we have to download the Tor browser. The first time we download the Tor browser, we will have to wait a while, depending on our internet speed. Step 5: Now, we have to connect to Tor. In order to connect to Tor network, we have to click on the "Connect", which will instantly connect us to the Tor network and allow us to utilize the Tor Browser under Kali Linux. 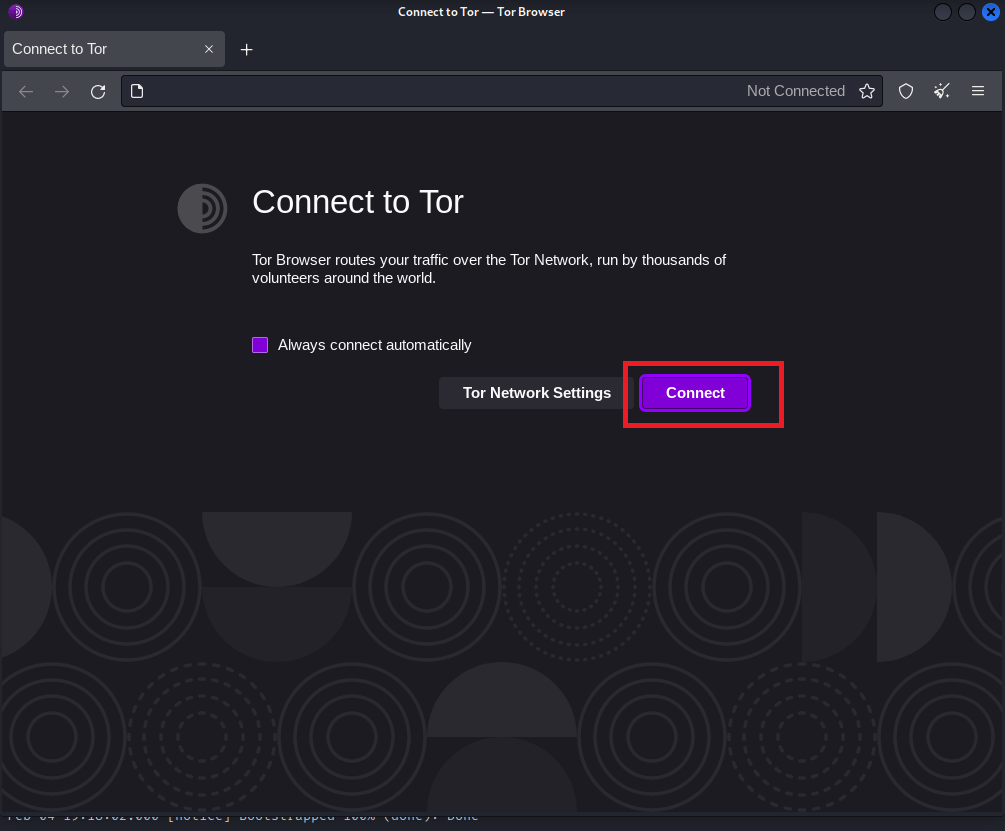
Step 6: Next, we can set the Network settings and utilize the proxy to connect to Tor in the Tor Network settings. If we are living or travelling in a country that censors Tor, we must manually setup the Tor Network using the options below. After that, we must click "Connect." Step 7: We have to wait while Tor Browser establishes a connection to the Tor network. Step 8: Now, Tor Browser is ready to use. And we can access the .onion website, as well as host our own website utilizing the Tor network. 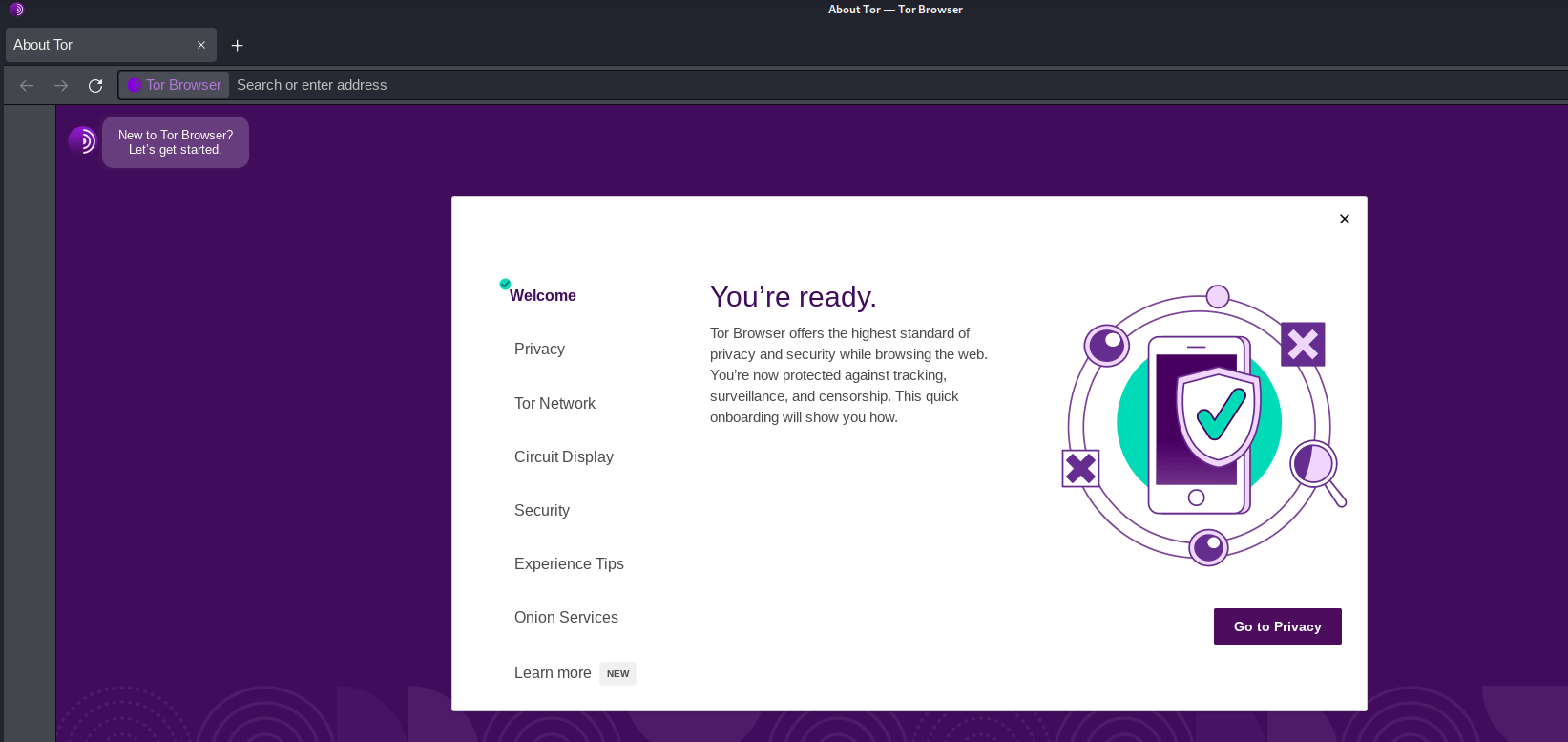
2. Download the Package and Run Tor Browser Manually in Kali LinuxThe following are the steps that we have to use in order to download the package and run the Tor browser manually in Kali Linux: Step 1: In order to download the package and run the Tor browser manually, we have to first visit the Tor Browser official website and download the most recent version of Tor Browser. We must select Download for Linux from the drop-down menu. 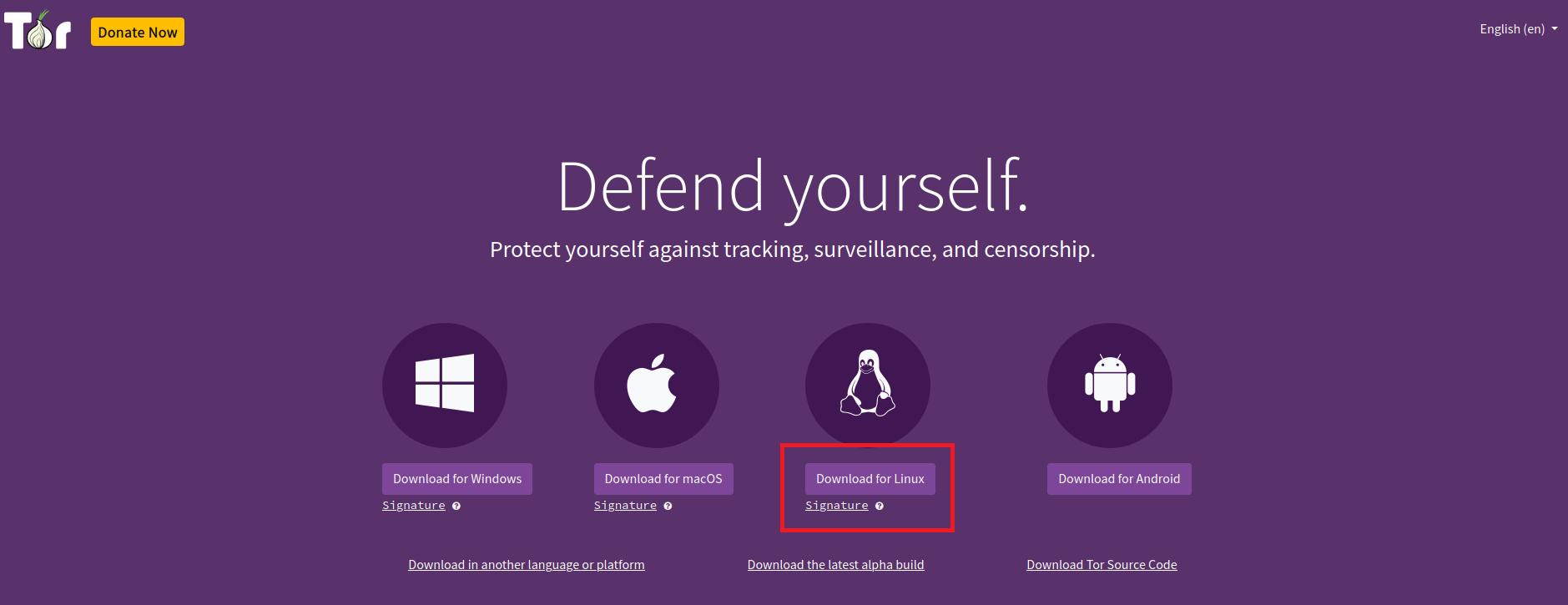
Step 2: Next, we need to save the tor-browser-linux.tar.xz. In our case, tor-browser-linux64-11.0.4_en-US.tar.xz. And then, we have to wait for downloading and then open the Download folder. 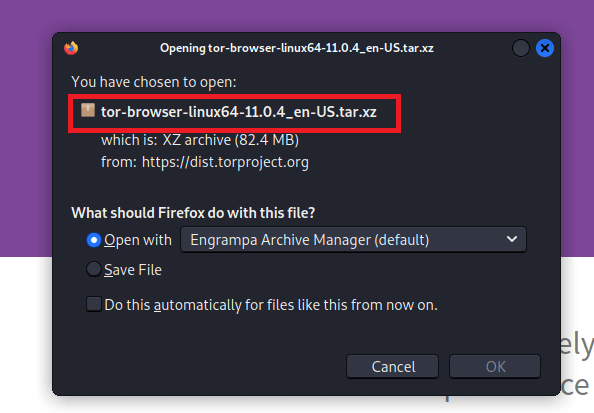
Step 3: Next, we need to unzip the downloaded tor-browser file with the help of the terminal or using Archive Manager. In this tutorial, we are using a command line. So, we will open the Kali Linux terminal and enter the following commands. 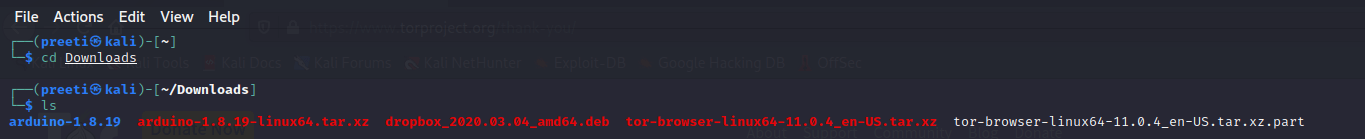
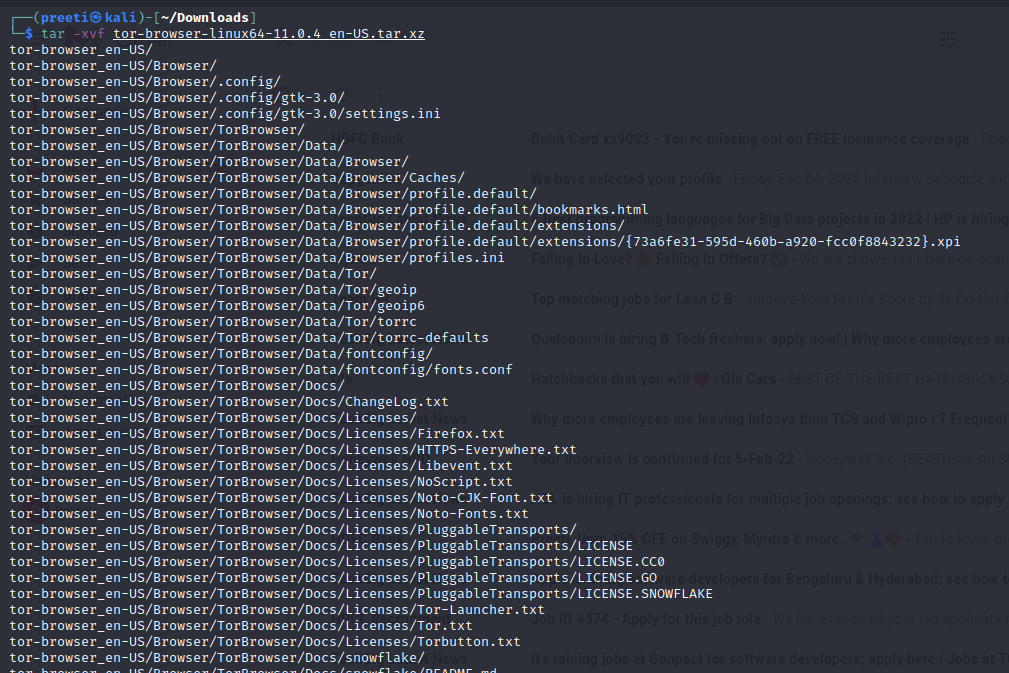
Step 4: Now, we can open the Tor Browser. To open the Tor Browser in Kali Linux, go to the extracted folder and double-click on the Tor Browser, or use the following command in the terminal. 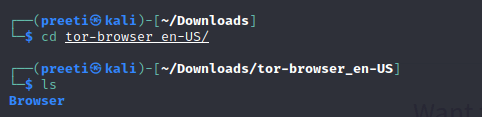
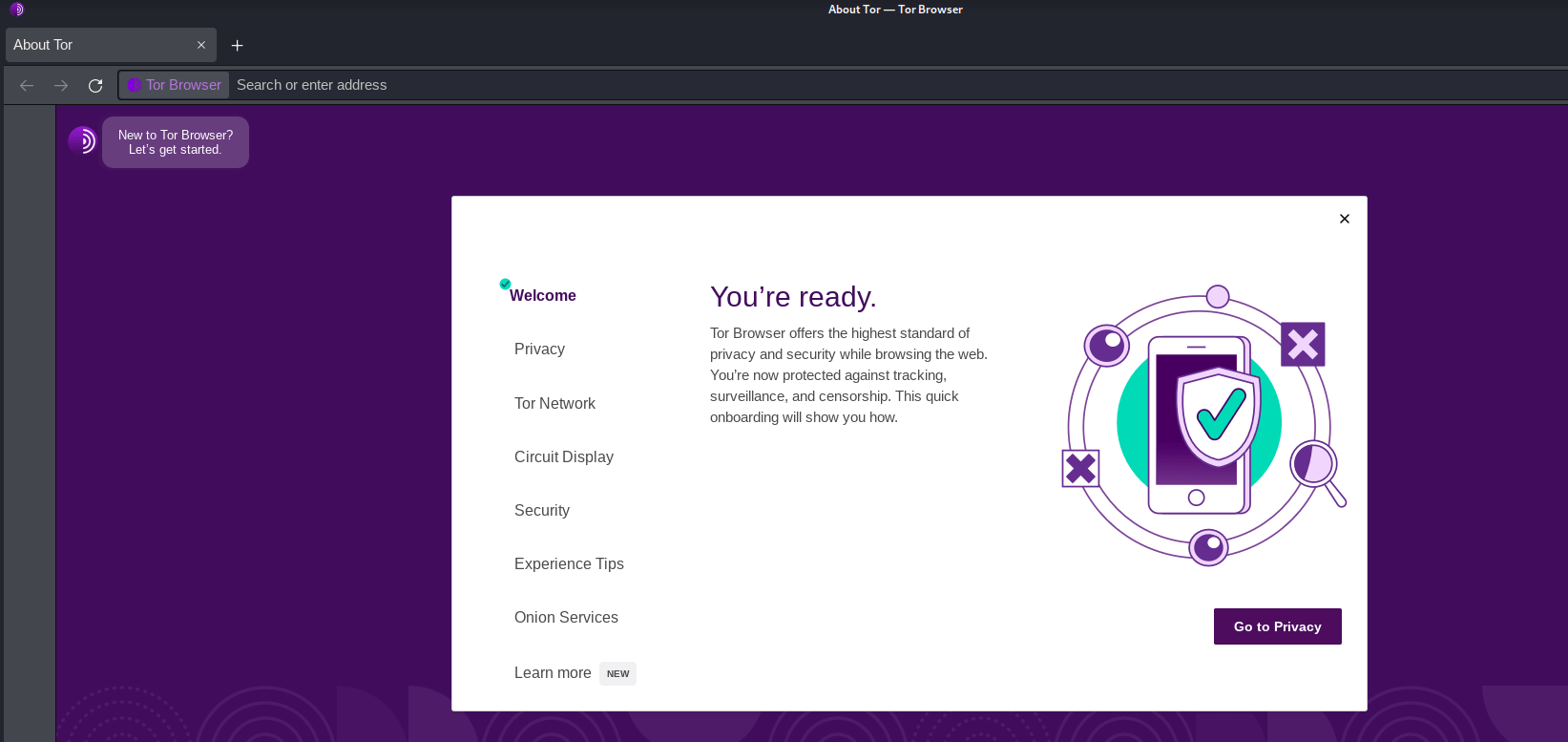
This is how we can use Kali Linux to install and run the Tor Browser and use the internet anonymously to safeguard our privacy.
Next Topic#
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









